Beruflich Dokumente
Kultur Dokumente
6 Ise 1 3 PVT Lab Guide
Hochgeladen von
alireza1023Originalbeschreibung:
Originaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
6 Ise 1 3 PVT Lab Guide
Hochgeladen von
alireza1023Copyright:
Verfügbare Formate
Lab Overview
Cisco ISE 1.3 Lab Guide
Developers and Lab Proctors
This lab was created by Secure Access and Mobility Technical Marketing teams, with main contributions
from Jason Kunst, Imran Bashir, and Hsing-Tsu Lai.
Lab Overview
This lab is designed to help attendees understanding how to deploy Cisco Identity Services Engine (ISE)
focusing on new key ISE 1.3 features such as Active Directory Multi-Join, ISE Internal Certificate
Services, and many Guest enhancements. In the lab the students will learn how configure ISE to connect
multiple AD domains, and use ISE internal CA to issue certificates for BYOD endpoints. The lab also
covers the new Guest UI available in ISE 1.3.
Lab participants should be able to complete the lab within the allotted time of 2 hours.
Lab Exercises
This lab guide includes the following exercises:
Lab Exercise 1 : Active Directory Multi-Join
Lab Exercise 2 : BYOD with Internal CA
Lab Exercise 3 : AnyConnect Unified Agent
Lab Exercise 4 : Guest Access Management
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 1 of 70
Product Overview: ISE
Product Overview: ISE
Cisco Identity Service Engine (ISE) is a context aware identity-based platform that gathers real-time
information from the network, users, and devices. ISE then uses this information to make proactive
governance decisions by enforcing policy across the network infrastructure utilizing built in standard
based controls. Cisco ISE offers:
Security: Secures your network by providing real-time visibility into and control over the users and
devices on your network.
Compliance: Enables effective corporate governance by creating consistent policy across an
infrastructure.
Efficiency: Helps increase IT and network staff productivity by automating traditionally labor-intensive
tasks and streamlining service delivery.
Enablement: Allows IT to support a range of new business initiatives, such as bring your own device
(BYOD), through policy-enabled services.
Lab Topology
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 2 of 70
Lab IP and VLANs
Lab IP and VLANs
Internal IP Addresses
Device
Name/Hostname
IP Address
Access Switch (3560CG)
3560CG.demo.local or 3560CG
10.1.100.1
Wireless LAN Controller
(virtual)
vwlc.demo.local
10.1.100.41
Wireless Access Point (varied)
ap.demo.local
10.1.90.x/24 (DHCP)
ASA (5505)
asa.demo.local
10.1.70.1
ISE Appliance
ise-1.demo.local
10.1.100.21
AD (AD/CS/DNS/DHCP)
ad.demo.local
10.1.100.10
mail.demo.local
10.1.100.40
Services
services.demo.local, ntp.demo.local
10.1.100.12
portal.demo.local, updates.demo.local
10.1.100.222
business.demo.local
10.1.100.223
it.demo.local
10.1.100.224
records.demo.local
10.1.100.225
Admin (Management) Client
admin.demo.local
10.1.100.6
(also FTP Server)
ftp.demo.local
Internal VLANs and IP Subnets
VLAN
VLAN Name
IP Subnet
Description
10
ACCESS
10.1.10.0/24
Authenticated users or access network using ACLs
20
MACHINE
10.1.20.0/24
Microsoft machine-authenticated devices (L3
segmentation)
50
GUEST
10.1.50.0/24
Network for authenticated and compliant guest users
90
AP
10.1.90.0/24
Wireless AP VLAN
99
LAB.LOCAL
10.1.99.0/24
AD domains lab.local and sam.lab.local
100
Management
10.1.100.0/24
Network services (AAA, AD, DNS, DHCP, etc.)
130
DB
10.1.130.0/24
Line-of-business Database servers
172
ISE.LOCAL
172.17.100.0/
24
AD domain ise.local
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 3 of 70
Connecting to Lab Devices
Accounts and Passwords
Access To
Account (username/password)
Access Switch (3560CG)
admin / ISEisC00L
Wireless LAN Controller (virtual)
admin /
ISEisC00L
ASA (5505)
admin /
ISEisC00L
ISE Appliances
admin /
ISEisC00L
AD (CS/DNS/DHCP/DHCP)
admin /
ISEisC00L
Services Servers
admin /
ISEisC00L
Admin (Management) Client
admin /
ISEisC00L
Connecting to Lab Devices
Note:
Note:
To access the lab, you must first connect to the Admin PC. The Admin PC provides a launching point for
access to all the other lab components
Admin PC access is through RDP, therefore you must have an RDP client installed on your computer
Connect to a POD
Step 1
Launch the Remote Desktop application on your system
a. Connect to you POD Admin PC using RDP.
b. Login as admin / ISEisC00L
Note: All lab configurations can be performed from the Admin client PC.
Connect to ESX Server Virtual Machines
During the lab exercises, you may need to access and manage the computers running as virtual
machines.
Step 1
From the Admin client PC, click the VMware vSphere Client icon on the taskbar
Step 2
Click OK when the VMware vSphere Client starts.
Step 3
You have the ability to power on, power off, or
open the console (view) these VMs. To do so,
place the mouse cursor over VM name in the
left-hand pane and right-click to select one of
these options:
a. To access the VM console, select Open Console from the drop-down.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 4 of 70
Connecting to Lab Devices
b. To login to a Windows VM, select Guest > Send Ctrl+Alt+del from the VM Console
menu:
Step 4
For this lab ensure that the following VMs are up and running:
p##-ad
p##-ise-1-13update
p##-mail
p##-services
p##-vWLC
p##-admin (might not be visible)
p##-w7pc-corp (should be Power-OFF)
p##-ws2012r2-lab.local
p##-ws2012r2-sam.lab.local
## refers to the pod number that you are assigned to. E.g., For POD 2, p##-ad would be p02-ad.
w7pc-guest may be powered on manually during the exercises.
Connect to Lab Device Command-Line Terminal
Step 1
To access the lab switches and ISE servers using SSH:
a. From the Admin client PC, locate the PUTTY shortcut on the taskbar. Click on the PuTTY
shortcut and it shows a list of devices and ISE servers.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 5 of 70
Pre-Lab Setup Instructions
b. Select the device that youd like to log into and double click on it.
c.
If prompted, click Yes to cache the server host key and to continue login.
d. Login using the credentials listed in the Accounts and Passwords table.
Pre-Lab Setup Instructions
Basic Connectivity Test
To perform a basic connectivity test for the primary lab devices, run the
pingtest.bat script from the Windows desktop of the Admin client PC.
Step 1
Step 2
Verify that ping succeeds for all devices tested by the script.
Controlling iPad via VNC Client
Below are some tips for controlling the iPad UI via VNC client which will be useful for the entire lab:
Home: (On PC/Mac with 2/3-button mouse) Right click once with a mouse. (On Mac with track
pad) Touch with two fingers on the Track Pad If Secondary Click is configured.
Mouse: Mouse pointer mimics touching the iPad screen with one finger.
Scrolling or dragging: Press and hold Left mouse button and move the mouse pointer to scroll
Keyboard: Move the pointer over any text box on the iPad, click once, and then begin using your
local keyboard for input.
Note: The tab key is not available on the iPads virtual keyboard so you will have to move the pointer to the text field you want to
input text, and click on it.
Note: When interacting with the iPad VNC session, US keyboard is preferred.
Note: US keyboard is needed for the RDP session too unless you have additional language packs installed to provide keyboard
mappings. This is only for the RDP sessions.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 6 of 70
Lab Exercise 1: Active Directory Multi-Join
Lab Exercise 1: Active Directory Multi-Join
Exercise Description
ISE customers often have users from several AD domains. The main reasons are:
Multi-Tenant: Service Providers -- to manage authentications for customers
Enterprise: Acquisition e.g. Company A buys Company B; Segmentation to separate
production from lab test instances or due to security concerns (e.g. PCI)
Before ISE 1.3, an ISE deployment may join to only one Microsoft Active Directory (AD) domain, and
requires two-way trusts to authenticate users located in other AD domains. Now an ISE 1.3 deployment
can join directly to multiple AD domains to authenticate users and computers in them. ISE 1.3 represents
each AD instance as an AD Join Point, each of which is essential the same as the AD identity store in
previous releases.
Exercise Objective
In this exercise, you are to explore new features implemented for ISE 1.3 Active Directory. You are to
Step 1
(Join Point #1) Join to a simple domain demo.local and check out new user interface
(Join Point #2) Add and join to the second domain sam.lab.local and experiment with
authentication domains
Create a simple Identity rewrite rule
Learn about the new Diagnostic Tools
Login to ISE admin web portal
a. Launch the Mozilla Firefox web browser. Enter the URL https://ise-1.demo.local
b. Login with username admin and password ISEisC00L
(Accept/Confirm any browser certificate warnings if present)
The ISE Dashboard should display. Navigate the interface using the multi-level menus.
Step 2
Step 3
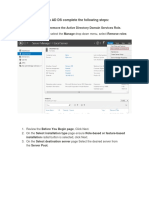
Access ISE Active Directory configuration page by navigating to Administration > Identity
Management > External Identity Sources and select Active Directory from the left-hand
pane.
Join ise-1 to demo.local (in a single-domain forest)
a. Click the hyperlink demoAD under the Joint Point Name column.
b. Tick the checkbox next to ISE node ise-1.demo.local and then click Join.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 7 of 70
Lab Exercise 1: Active Directory Multi-Join
c.
In Join Domain pop-up window, fill in
* AD User Name admin
* Password ISEisC00L
Specify Organization Unit OU=ISE,OU=HCC,DC=DEMO,DC=LOCAL
Note 1: To specify an organization unit is new in ISE 1.3 and it is optional in this step as admin is a domain admin user. When
employed, we may create the ISE computer object in a location other than the Microsoft AD default location, which is
CN=COMPUTERS,DC=DEMO,LOCAL.
Note 2: OU=ISE,OU=HCC is pre-created in this labs AD domain demo.local, to demonstrate this option.
d. Click OK to start the join operation.
e. A window Join Operation Status will pop up. Wait until the node status turns
Completed, and then click Close.
f.
The Connection tab shall show ad.demo.local as the domain controller and Default-FirstSite-Name as the site.
g. Click on the Groups tab to view the pre-defined groups.
h. In case of upgrade or renaming groups, also click Update SID Values to get the latest
group-to-SID mappings. Save when done.
Step 4
Join ise-1 to sam.lab.local (a child domain in a two-domain forest)
a. Click Active Directory from the left-hand pane to return to the main configuration page.
b. Click Add. In the Connection tab, fill in
* Join Point Name sam.lab.local
* Active Directory Domain sam.lab.local
Note: The Join Point Name is its ISE dictionary name for this external identity source and needs to be unique among all identity
sources. Although here we use the same name as its AD domain, they are not required to match.
c.
Submit when done.
d. Click Yes, when prompted after ISE Reloading page following the create,
Would you like to Join all ISE Nodes to the Active Directory Domain?
e. In Join Domain pop-up window, fill in
* AD User Name lisa
* Password ISEisC00L
Specify Organization Unit OU=theSimpsons,DC=SAM,DC=LAB,DC=LOCAL
Note: OU=theSimpsons is pre-created in sam.lab.local. lisa is not a domain admin user but granted Full Control permissions for
OU=theSimpsons through AD delegation of control, so she can create and delete the computer object for ise-1 in this OU.
Note: This AD is using the Microsoft default security policy, which allows any domain users to add workstations to domain. For
example, another domain user maggie can also join ise-1 to the AD domain with ise-1 computer account to be created at the
default location but NOT in this OU. Neither lisa or maggie can delete the ise-1s computer account at the default location.
f.
Click OK to start the join operation.
g. A window Join Operation Status will pop up. Wait until the node status turns
Completed, and then click Close.
h. The Connection tab shall show ws2012r2-2.sam.lab.local as the domain controller and
Default-First-Site-Name as the site.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 8 of 70
Lab Exercise 1: Active Directory Multi-Join
Step 5
Authentication Domains (a.k.a. Domain Whitelisting) in Join Point sam.lab.local
a. Click tab Authentication Domains to review the current settings. The checkbox Use
all Active Directory domains for authentication is shown as selected, which is the default.
The domain sam.lab.local is a child domain of lab.local. Both AD domains are shown with
a YES value for their Authenticate column so users from either domain can authenticate.
Step 6
Test Authentication Domains with default Use all AD domains for authentication in Join Point
sam.lab.local
a. Click back to tab Connection. Tick ise-1.demo.local and click Test User.
b. Test User Authentication with a user in lab.local (the parent domain). In Test User
Authentication Window, fill in
* Username
* Password
Authentication Type
Authentication Data
c.
homer
ISEisC00L
MS-RPC (drop-down)
Retrieve Groups
Retrieve Attributes
Click Test. The authentication result should be SUCCESS.
d. Click Close when done viewing the results.
Step 7
Test Authentication Domains with selected AD domain(s) sam.lab.local only
a. Click tab Authentication Domains.
b. Un-tick the option Use all Active Directory domains for authentication. Note that
Authenticate column turns from YES to NO for both domains.
c.
Select sam.lab.local and click Enable Selected to turn its Authenticate column to YES.
Then, Save.
d. Click tab Connection. Select ise-1.demo.local and click Test User.
e. Test User Authentication with a user in lab.local (the parent domain). In Test User
Authentication Window, fill in
* Username
* Password
Authentication Type
Authentication Data
f.
homer
ISEisC00L
MS-RPC (drop-down)
Retrieve Groups
Retrieve Attributes
Click Test. The authentication result should be FAILED.
g. Click Close when done viewing the results.
Step 8
Identity Rewrites manipulate identity names before searches in AD. Here exemplifies this
feature by Eduroam Realm Striping
Eduroam uses realm for routing the authentication requests so it needs the client supplicants to
send the outer identity in the form of username@realm. Certain 802.1X supplicants, such as
Windows native supplicants, are not configurable to use different identities for inner and outer
identities, so that the home RADIUS authentication server may receive the requests in that form
(username@realm). If the realm is not one of the authentication domains, a Join Point may be
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 9 of 70
Lab Exercise 1: Active Directory Multi-Join
configured either to strip it or to rewrite the identity to a UPN with an authentication domain
suffix.
a. Click tab Advanced Settings for the join point sam.lab.local.
Note: This is at Administration > Identity Sources > External Identity Sources. Select sam.lab.local under Active Directory in the left
pane.
b. Scroll down to the last section Identity Rewrite.
c.
Choose Apply the Rewrite Rules Below to modify username.
d. Scroll down to see the built-in rules. Click the drop-down arrow next to the gears icon in
rule #4 if Indentity Matches [IDENTITY]@[DOMAIN]. And, select Duplicate above.
e. In the newly duplicated rule, update the rule as below:
If Identity Matches
f.
[IDENTITY]@demo.edu
rewrite as
[IDENTITY]
Click the button Try Rules
g. In the pop-up Test rewrite window, input maggie@demo.edu in the text box next to Test
Subject. It should result in maggie as the rewrite.
h. Click Close when done.
i.
Step 9
Click Save to persist the rewrite rules.
AD Diagnostic Tool is a new utility in ISE 1.3 AD to help determining any environment issues
related to the join points.
a. Click Active Directory from the left-hand pane to return to the main configuration page.
b. Click Advanced Tools and then select Diagnostics Tools from the drop-down menu.
c.
Click Run All Tests.
d. If Summary shows Failure(s), click the hyperlink See Details for warning/failed test
details. Then, click Close when done.
Note: The DNS failures are due to known defect CSCuq95531.
End of Exercise: You have successfully completed this exercise.
Proceed to next section.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 10 of 70
Lab Exercise 2: ISE 1.3 BYOD with Internal Certificate Authority
Lab Exercise 2: ISE 1.3 BYOD with Internal
Certificate Authority
Managing certificates for BYOD adds significant complexity and expense when using Microsoft Public
Key Infrastructure. ISE 1.3 introduces Internal Certificate Authority (CA), which is designed to simplify
BYOD deployments but works in concert with existing PKI infrastructure.
Internal CA provides a Single Management Console to manage endpoints and their certificates. For
example, deleting an endpoint in ISE will revoke the certificates associated with that endpoint.
Multiple deployment models are supported for the Internal CA, it supports stand alone and subordinate
deployments. Removes corporate PKI team from every BYOD interaction. In regards to the architecture,
Primary PAN (PPAN) may be Subordinate to an existing Root CA or may be Standalone Root CA.
All PSNs are Subordinate CAs to
PPAN
PSNs are SCEP Registration
Authorities (RAs)
Promotion of Standby PAN:
o Will not have any effect on
operation of the subordinate CAs.
o For Standby to become Root
CA must manually install the
Private/Public keys from PPAN.
This section is further divided for clarity
Lab Exercise 2.1: Configure ISE Internal CA for BYOD
Lab Exercise 2.2: Configure ISE for Single-SSID BYOD
Lab Exercise 2.3: Test and Verify Onboarding of Non-corporate iPad
Lab Exercise 2.1: Configure ISE Internal CA for BYOD
Exercise Description
This lab discusses Internal CA configuration for BYOD devices.
Exercise Objective
In this exercise, your goal is to configure the ISE 1.3 Internal CA. This includes completion of the
following tasks:
Step 1
Verify Internal Certificate Authority is running and is operational
Create a certificate template to provision BYOD devices.
Login to ISE @ https://ise-1.demo.local/admin/ with username admin and password ISEisC00L
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 11 of 70
Lab Exercise 2.2: Configure ISE for Single SSID BYOD
Step 2
Go to Administration > System > Certificates. Under Certificate Authority, select Internal
CA Settings and verify Internal CA is running.
Step 3
In the same page Administration > System > Certificates. Under Certificate Authority, click
Certificate Templates. ISE 1.3 preloaded with EAP_Authentication_Certificate_Template,
which could be used for BYOD. In this Lab we will create a new template to go through
certificate template creation process.
Step 4
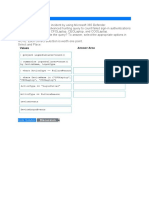
In Certificate Templates page, click Add, and fill-in with the following values
* Name
Description
Common Name (CN)
Organizational Unit (OU)
Organization (O)
City (L)
State (ST)
Country (C)
Subject Alternative Name (SAN)
Key Size
* SCEP RA Profile
Valid Period
internalCertBYOD
ISE internal cert template
$UserName$
MAC Address
2048
ISE Internal CA
730
Click Submit to save the changes.
Note: ISE 1.3 internal CA come with a default configuration and is already running when ISE is installed. Overall the administration
configuration experience is super easy to setup.
Lab Exercise 2.2: Configure ISE for Single SSID BYOD
Exercise Description
This exercise reviews ISE configurations for BYOD wireless deployment with one wireless SSID. You will
learn how to configure an ISE client provisioning policy rule that uses the internal CA as the PKI provider
for ISE native supplicant provisioning (NSP).
Exercise Objective
In this exercise your goal is to configure ISE for single SSID Wireless BYOD, which includes the
completion of the following tasks:
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 12 of 70
Lab Exercise 2.2: Configure ISE for Single SSID BYOD
Create Client Provisioning Policy to use ISE internal CA to issue BYOD endpoint
certificates.
Review the Certificate Authentication Profile and the Identity Source Sequence
Review the Authentication Policy to accept 802.1X authentication from wireless access
devices with EAP-TLS or PEAP/EAP-MSCHAPv2 protocols.
Review the Authorization Policy to allow registration as well as supplicant provisioning
and to grant full access to registered devices.
Step 1
If timed out, re-login to the ISE administration web portal at https://ise-1.demo.local using the
credentials admin / ISEisC00L
Step 2
Create Client Provisioning Policy for Native Supplicant Provisioning
a. Go to Policy > Client Provisioning and create a new rule, which will look like the
following:
Status
Rule Name
Identity
Groups
Apple iOS
Any
Operating
Systems
Apple iOS All
Other
Conditions
Results
iOS WPA2e TLS
You may add a new Native Supplicant Configuration/Wizard Profile in-line within the Results cell.
Create the native supplicant profile iOS WPA2 TLS in-line as shown below:
* Name
Description
* Operating System
* Connection Type
iOS WPA2e TLS
Apple iOS All
Wireless
* SSID ##-ISECOLD
Security WPA2 Enterprise
* Allowed Protocol TLS
Certificate Template internalCertBYOD
Note: SSID value is case-sensitive and needs to be exactly the same as the one defined in the WLC.
To avoid typos, copy the SSID name from the WLC and paste it on the ISE GUI. To find SSID for your POD, Go to admin PC,
launch a browser and login to WLC (https://vwlc.demo.local) with Username = admin and Password = ISEisC00L. Click WLANs and
then copy the name of the Secure SSID i.e. ##-ISECOLD (e.g. 02-ISECOLD for pod-02).
b. Click Save to persist the native supplicant profile. Save again to update to Client
Provisioning Policy.
You may skip the rest of this exercise and jump to Exercise 2.3, if already familiar with ISE BYOD from the previous ISE releases.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 13 of 70
Lab Exercise 2.2: Configure ISE for Single SSID BYOD
Step 3
Go to Administration > Identity Management > External Identity Sources > Certificate
Authentication Profile. Review
Preloaded_Certificate_Profile.
ISE 1.3 comes with this profile that has most
common settings, such as using Subject
Common Name as the User Name.
Step 4
Go to Administration > Identity Management > Identity Source Sequences.
Review Identity Source Sequence
DOT1X_ID_Sequence.
Note-1: When using this identity source
sequence in EAP-TLS authentications, it will
pick the certificate authentication profile. In
password-based authentications, it will use the
other identity sources in the authentication
search list.
Note-2: All_AD_Join_Points is new in ISE 1.3. It
is an AD scope that includes all AD join points.
Step 5
Go to Policy > Policy Elements > Results >
Authentication > Allowed Protocols. Review PEAPoTLS,
which allows only two protocols:
a. EAP-TLS
b. PEAP with inner method EAP-MS-CHAPv2
Step 6
Go to Policy > Policy Elements > Results > Authorization > Authorization Profiles. Review
two Authorization Profiles that are used in the Authorization Policy one for full network access
and the other for native supplicant provisioning.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 14 of 70
Lab Exercise 2.2: Configure ISE for Single SSID BYOD
a. Authorization Profile for allowing Full Network Access
Name
Description
Access Type
Common Tasks
Airespace ACL Name
Attributes Details
wlcFullAccess
-ACCESS_ACCEPT
PERMIT-ALL-TRAFFIC
Access Type = ACCESS_ACCEPT
Airespace-ACL-Name = PERMIT-ALL-TRAFFIC
b. Authorization Profile for allowing Supplicant Provisioning
Name
Step
5
Description
Access Type
Common Tasks
Web Redirection
(CWA,MDM,NSP,CPP)
wlcSupplicantProvisioning
-ACCESS_ACCEPT
Drop-down menu: Native Supplicant Provisioning
ACL: PERMIT-2-ISE-a-DNS
Value: BYOD Portal (default)
Attributes Details
Access Type = ACCESS_ACCEPT
cisco-av-pair = url-redirect-acl=PERMIT-2-ISE-a-DNS
cisco-av-pair = urlredirect=https://ip:port/guestportal/gateway?sessionIdValue&portal=&action=nsp
Step 7
Go to Policy > Policy Sets. Select wirelessDOT1X. Expand its Authentication Policy and
ensure that the authentication policy is configured as below. The modified are highlighted in
Yellow.
Enabled
Step 8
Name
Protocols
Identity Source
Options
Default Rule Allow Protocols PEAPoTLS and use DOT1X_ID_Sequence Reject
(if no match)
Reject
Drop
Next, expand the Authorization Policy to review two rules as shown below the Rule Name
Registered with ISE and EAP-TLS and Employee Personal Device.
Rule Name
Groups
Other Conditions
Registered
with
ISE
and
EAPAny
EndPoints:BYODRegistration
EQUALS
TLS
Yes
AND
Network Access:EapAuthentication
EQUALS EAP-TLS
AND
CERTIFICATE:Subject Alternative Name
EQUALS Radius:Calling-Station-ID
Employee_Personal_Device
Any
Network Access:EapAuthentication
EQUALS EAP-MSCHAPv2
Any
Default
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Permissions
wlcFullAccess
wlcSupplicantProvisioning
DenyAccess
Page 15 of 70
Lab Exercise 2.3: Test and Verify Onboarding of Non-corporate iPad
Lab Exercise 2.3: Test and Verify Onboarding of
Non-corporate iPad
Exercise Description
This exercise will onboard an Apple iPad to validate the policies configured previously.
Warning: The Apple iPad you will be using is controlled remotely using VNC over the USB port of the admin PC. Due to
configuration and limitations of remotely controlling an interactive device like the iPad in a lab environment please do not
deviate from the exercise steps. Any deviation may result in losing connectivity to the iPad, which will need physical / manual
resetting and prevent you from experiencing the full potential of the lab.
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Step 1
On-board the iPad with ISE internal CA issued certificate.
Review ISE Live Logs to monitor the process
Enable ##-ISECOLD in WLC.
a. Login to vWLC web portal @ https://vwlc.demo.local as admin / ISEisC00L
b. Menu WLANs and select WLAN ID 1 ##-ISECOLD, Enable Selected from the drop-down
next to Go, and hit Go.
Step 2
Double click on the batch file vnc-to-iPad on the admin-PCs Desktop to start a VNC session to
the iPad. The batch file will prompt you to press any key to continue. You will then see the VNC
Viewer pop up.
Step 3
On the iPad, navigate to Settings > General > Profiles. Remove any existing profiles, if
present.
Note: You might not see the Profiles menu option, when no profile installed on the iPad.
Step 4
Next on the iPad, go to Settings > Safari and hit Clear History as well as Clear Cookies and
Data.
Step 5
Go to Settings > Wi-Fi and slide the virtual switch to enable Wi-Fi. Select and connect to the
network ##-ISECOLD
a. Enter the username/password AD
credentials (employee1/ISEisC00L) and click
Join
b. Click to Accept the certificate
c.
Next click on the blue arrow of the connected network and verify the IP address assigned
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 16 of 70
Lab Exercise 2.3: Test and Verify Onboarding of Non-corporate iPad
Note: IP address for iPad might be different depending on the DHCP server in the POD, iPad might get an IP address from
10.1.10.x subnet which is OK.
Step 6
Now launch the mobile Safari app and access the website portal.demo.local.
If receiving a warning Cannot Verify Server Identity, click Continue and it will redirect to the
self-provisioning page.
This will take you to the ISE 1.3 BYOD Welcome Screen, which guides the end-user over a
series of steps to onboard the device and also keeps tracks of these steps with proper
numbering.
Click Start to proceed.
Next, enter Device Name and Description
Device Name
Description
Personal iPad
This is my iPad
Click Continue to proceed.
Step 3 prompts to Launch Apple Profile and Certificate
Installers Now. Click to proceed.
When prompted to install the root CA certificate that
signed the SSL server certificate of ISE, click
Install.
Accept any Warnings to complete this installation.
Step 7
It switches back to the self-provisioning page in
Safari. Shortly afterwards, the ISE Profile
Service pops up and prompts Install.
Click Install to start the Apple Over-The-Air
(OTA) enrollment process. This will automatically
generate the key, enroll the identity certificate,
and save the resulting signed Wi-Fi profile to the
iPad.
Note: If errors in installing the profile, do the following:
Verify a SCEP CA profile has been created (Administration > System > Certificates > Certificate Authority >
Internal/External CA Settings)
Verify the CA and RA certificates have been downloaded to the Certificate Store (Administration > System > Certificates >
Certificate Management > Trusted Certificates)
Check the console output of the iPad using the iPhone Configuration Utility (iPCU) from Apple, which is installed on the admin
PC (Start > All Programs > iPhone Configuration Utilities)
Step 8
Now entering portal.demo.local in the mobile Safari app should take you to the website.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 17 of 70
Lab Exercise 2.3: Test and Verify Onboarding of Non-corporate iPad
Step 9
Verifying Settings > General > Profiles shows two profiles are installed
Note: iOS WPA2e TLS is the name of the supplicant profile created in Step 2 of Exercise 2.2
Step 10
Go to Operations > Authentications. Check the live logs on ISE admin web portal to verify that
the correct authorization profiles were applied. Initially, the device is authorized for
wlcSupplicantProvisioning. Once the provision is done, the wlcFullAccess profile is applied.
Note: For debugging, enable DEBUG logging for relevant components -- client, guest, provisioning, SCEP, and OCSP.
(Admin>System>Logging>Debug Log > Conifg)
Step 11
Note:
Under Administration > System > Certificates > Certificate Management > Endpoint
Certificates, look at the certificate issued to the iPad
The certificate is shown as issued one the day before. This is by design to reduce issues (e.g. CSCui15922)
where endpoints may clock slightly earlier than the CA.
More Troubleshooting Tips
Helpful WLC CLI commands:
Debugging client traffic
debug client <mac_address>
Debugging AAA authentication
debug aaa events enable
Debugging 802.1X events
debug dot1x events enable
Bypass captive portal
config network web-auth captive-bypass enable
End of Exercise: You have successfully completed this exercise.
Proceed to next section.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 18 of 70
Lab Exercise 3: AnyConnect Unified Agent
Lab Exercise 3: AnyConnect Unified Agent
Lab Exercise 3.1: Configure Client Provisioning Services
for Unified Agent
Exercise Description
AnyConnect ISE Posture, shown as a new System Scan tile, is replacing NAC agent for Windows
and OSX. This exercise covers how to configure policies to web-deploy AnyConnect from ISE.
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Complete general system settings to support Client Provisioning and Posture Services
Update Cisco conditions, OS, and AV/AS support chart
Add client posture agent software
Create and add AnyConect Agent profiles and configuration(s)
Define Client Provisioning Policy
The diagram highlights the key tasks covered in this exercise including System Settings,
Download of Dynamic Updates and CPP Packages, Agent Profiles and CPP Policy:
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 19 of 70
Lab Exercise 3.1: Configure Client Provisioning Services for Unified Agent
Lab Exercise Steps
Step 1
Access ISE admin web interface
a. Launching the Mozilla Firefox web browser on the admin client PC and entering in the
address field https://ise-1.demo.local
b. Login with username admin and password ISEisC00L
(Accept/Confirm any browser certificate warnings if present)
The ISE Home Dashboard page should display. Navigate the interface using the multi-level menus.
Step 2
Verify the ISE proxy configuration for software downloads.
Navigate to Administration > System > Settings and select Proxy from the left-hand pane.
Note:
(New) ISE 1.3 supports Basic Proxy authentication.
Proxy host server : port
Step 3
proxy-wsa.esl.cisco.com
80
Download pre-built posture checks for AV/AS and Microsoft Windows.
a. Click the icon to the left of Posture in the left-hand pane to expand the contents of the
Posture settings, and then click Updates. The Update Information in the bottom righthand pane displays the last time Posture updates took place.
b. Review and add a check mark to Automatically Check for updates starting from
initial delay as shown below:
Web
Update Feed URL:
Proxy Address:
Proxy Port:
https://www.cisco.com/web/secure/pmbu/posture-update.xml
proxy-wsa.esl.cisco.com
80
Automatically check for updates starting from initial delay every 24 hours
a. Click the Save button.
d. Click Update Now to run it immediate.
Note:
Step 4
You may proceed to next steps while the update is running.
Configure general settings for agent behavior:
a. Select General Settings from the left-hand pane under the Posture settings. Review the
default values for Remediation Timer, Network Transition Delay, and Default Posture
Status.
b. Check (enable) the checkbox to Automatically Close Login Success Screen After
and set time to 5 seconds.
c.
Posture Lease is new in ISE 1.3. It controls posture assessment at re-authentications.
For example, after disconnecting from network in the office to attend a conference, a user
needs not posture again when reconnecting at the conference room.
For this lab, we set the posture lease to 1 Day
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 20 of 70
Lab Exercise 3.1: Configure Client Provisioning Services for Unified Agent
Posture General Settings
Remediation Timer 6
Minutes
Network Transition Delay 3
Seconds
Default Posture Status Compliant
Seconds
Automatically Close Login Success 5
Screen After
Posture Lease
[ ] Perform posture assessment every time a user connects to the network
Days
1
Perform posture assessment every
d. Click Save.
Note:
Step 5
The posture agent profiles may be used to override these global settings.
Configure an Acceptable Use Policy for ISE Posture.
a. Select Acceptable Use Policy from the left-hand pane under the Posture settings.
b. Click Add. Enter the following values for the new AUP policy:
* Configuration Name
Configuration Description
Show AUP to Agent Users
( )
( )
AUP URL / AUP File
* Select User Identity Groups
c.
Step 6
aupAnyUser
Simple Acceptable Use Policy
[
Use URL for AUP message
Use file for AUP message
http://updates.demo.local/AUP.html (Case Sensitive)
Any
Click Submit when finished.
Download AnyConnect files.
a. Open a new tab in FireFox to https://tools.demo.local/cp/, and download the following
files by right-click and Save Link As to the Downloads folder.
i.
anyconnect-win-4.0.00048-k9.pkg
ii.
anyconnect-win-compliance-3.6.9492.2.pkg
iii.
anyconnect-VPN-disable.xml
iv.
anyconnect-NAM-EAP-FAST.xml
b. Back to ISE admin web UI, go to Policy > Policy Elements > Results and click the
icon to left of Client Provisioning to expand its contents.
c.
Select Resources in the left-hand pane.
d. From the right-hand pane, click Add then click Agent Resources from local Disk from
the drop-down list. Select Cisco Provided Packages from Category drop-down.
e. Browse to C:\Users\admin\Downloads\, select to open, Submit, and Confirm the
checksum for:
anyconnect-win-4.0.00048-k9.pkg
anyconnect-win-compliance-3.6.9492.2.pkg
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 21 of 70
Lab Exercise 3.1: Configure Client Provisioning Services for Unified Agent
CLIENT PROVISIONING FILE REFERENCE:
AnyConnectDesktopWindows: AnyConnect ISE Posture module for Windows.
AnyConnectDesktopOSX: AnyConnect ISE Posture module for OSX.
Compliance Module(s): AnyConnectComplianceModuleOSX, AnyConnectComplianceModuleWindows are
OPSWAT modules that provide updates to AV/AS vendor support for AC ISE Posture Agent.
AnyConnect ISE Posture Agent Profiles: Configuration files for AnyConnect ISE Posture
agent.
Step 7
Create an AnyConnect posture profile for Windows clients.
a. From the right-hand pane, click Add then select NAC or AnyConnect Posture Profile from
the drop-down list.
b. In ISE Posture Agent Profile Settings > New Profile, click on drop down arrow for Select a
Category and then select AnyConnect
c.
Enter the following values for the new Agent profile. When finished, click Submit.
ISE Posture Agent Profile Settings
The defaults should work for most cases. Changed items are highlighted. See ISE User
Guide, Release 1.3 for more info on Agent Profile Parameters and Applicable Values.
AnyConnect
* Name:
acPostureWinProfile
Description:
AnyConnect ISE Posture Profile for Windows clients
Agent Behavior
Parameter
Enable debug log
Operate on non-802.1X
wireless
Value
No
No
Notes
Description
Enables the debug log on the agent
Enables the agent to operate on non802.1X wireless networks.
Enable signature check
No
OSX: N/A
Log file size
Remediation timer
5 MB
4 mins
Enables signature checking of
executables before the agent will run
them.
The maximum agent log file size
The time the user has for remediation
before they will be tagged as noncompliant
The default is empty which
means use the global setting.
The default of global setting is 4.
IP Address Change
Parameter
Enable agent IP refresh
Value
Yes
Notes
Enables VLAN change detection
Description
Sets the Vlan change detection flag on
the server, to transmit the configured
dhcp release delay, and the dhcp renew
delay values from the server to the client.
VLAN detection interval
0 secs
0 means VLAN detection is
disabled
The interval at which the agent will check
for a VLAN change
Ping or ARP
Maximum timeout for ping
DHCP renew delay
DHCP release delay
Network transition delay
Ping
1 secs
1 secs
4 secs
3 secs
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
Ping timeout.
The default is empty which
means uses the global setting.
The default of global setting is 3.
11/17/2014 10:17:00 AM PST
The period for which the agent suspends
network monitoring so it can wait for a
planned IP change to happen
Page 22 of 70
Lab Exercise 3.1: Configure Client Provisioning Services for Unified Agent
Posture Protocol
Parameter
PRA retransmission time
Value
120 secs
Discovery host
biz.demo.local
* Server name rules
Step 8
Note:
Notes
Description
This is the agent retry period if there is a
Passive Reassessment communication
failure
The server that the agent should connect
to
need to be blank by default to
force admin to enter a value. "*"
means agent will connect to all
A list of wildcarded, comma-separated
names that defines the servers that the
agent can connect to. E.g. "*.cisco.com
Configure an AnyConnect VPN profile to hide the VPN tile in AnyConnect GUI.
We need a VPN profile in order not to show AnyConnect VPN module tile on the client machine.
Ref: CSCur22131: Discrepancy with VPN module appearing on client when it is de-selected
a. Click Add then click Agent Resources from local Disk from the drop-down list.
Category:
Type:
Name:
Description:
Customer Created Packages
AnyConnect Profile
acVPNdisableProfile
Profile to disable VPN tile.
b. Browse to C:\Users\admin\Downloads\
c.
Select anyconnect-VPN-disable.xml, downloaded in Step 7.
d. Click Submit to save changes. Confirm when prompted for Please confirm this
package's SHA1 hash matches : 7f7003bd2e53ab111aa55f63a0d737a373276501.
Step 9
Upload NAM profile to ISE.
a. Click Add then Agent Resources from local Disk from the drop-down list.
Category:
Type:
Name:
Description:
Customer Created Packages
AnyConnect Profile
acNAMProfile
Profile to Configure AnyConnect NAM for EAPFAST.
b. Browse to C:\Users\Admin\Downloads\
c.
Select anyconnect-NAM-EAP-FAST.xml
d. Click Submit to save changes. Confirm when prompted for Please confirm this
package's SHA1 hash matches : aae7e54819644d3219b7282a179133a184c1d3bd.
Step 10
Create an AnyConnect configuration profile for Windows clients.
a. From the right-hand pane, click Add then select AnyConnect Configuration from the
drop-down list.
b. Under AnyConnect Package, click on drop down arrow for Choose a Package and then
select AnyConnectDesktopWindows 4.0.48.0
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 23 of 70
Lab Exercise 3.1: Configure Client Provisioning Services for Unified Agent
c.
Enter the following values for the new Agent Configuration. When finished, click Submit
to save the changes.
* AnyConnect Package: AnyConnectDesktopWindows 4.0.48.0
* Configuration Name: acConfigWin
Description: An AnyConnect agent configuration for Windows
* Compliance Module Anyconnect-win-compliance-3.6.9492.2.pkg
AnyConnect Module Selection
ISE Posture
VPN
Network Access Manager
Web Security
ASA Posture
Start Before Logon
Diagnostic and Reporting Tool
Profile Selection
ISE Posture
VPN
Network Access Manager
Web Security
Customer Feedback
Step 11
acPostureWinProfile
acVPNdisableProfile
acNAMProfile
-
Define Client Provisioning Policy for Employees
a. Go to Policy > Client Provisioning.
b. Add a new rule, either insert above or below the existing policy, as
below, and then Save when done.
Rule Name
ID Groups
OS
Conditions
Results
Agent Configuration
Employee WinAll Any
Windows All demoAD.local:ExternalGroups
EQUALS demo.local/HCC/Groups/Employees Agent: acConfigWin
Note: Ensure you saved your Client Provisioning Policy!
End of Exercise: You have successfully completed this exercise.
Proceed to next section.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 24 of 70
Lab Exercise 3.2: Define Authorization Policy for Client Provisioning and Posture Compliance
Lab Exercise 3.2: Define Authorization Policy for Client
Provisioning and Posture Compliance
Exercise Description
This exercise includes modifications to an existing Authorization Policy to ensure that endpoints
that are not posture compliant are redirected to ISE client provisioning portal, and that only
posture compliant endpoints are granted privileged network access.
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Define a Downloadable ACL (dACL) that restricts network access for endpoints whose
compliance state is either Unknown or NonCompliant.
Review a URL Redirect ACL on the access switch to ensure that general http/https traffic
is redirected to the ISE Policy Service node while allowing access to remediation servers.
Define a new Authorization Profile that apply the quarantine dACL and Redirect ACL to
redirect endpoints to provisioning and posture services.
Add new rules to the Authorization Policy that leverage the new Authorization Profiles to
quarantine, assess posture, and remediate endpoints that are not posture compliant.
Update existing Authorization Policy rules such that privileged network access is based
on posture compliance.
The diagram highlights the key tasks covered in this exercise including Authorization Profiles,
their component dACLs, and Authorization Policy:
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 25 of 70
Lab Exercise 3.2: Define Authorization Policy for Client Provisioning and Posture Compliance
Lab Exercise Steps
Step 1
Access the admin interface of the ISE Administrative node.
a. Go to the Admin client PC and launch the Mozilla Firefox web browser. Enter the
following URL in the address field:
https://ise-1.demo.local
b. Login with username admin and password ISEisC00L
(Accept/Confirm any browser certificate warnings if present)
The ISE Home Dashboard page should display. Navigate the interface using the multi-level menus.
Step 2
Define a dACL that restricts network access for endpoints that are not posture compliant.
a. Go to Policy > Policy Elements > Results and click
double-click Authorization) to expand its contents.
icon to left of Authorization (or
a. Select Downloadable ACLs from the left-hand pane.
b. Click Add from the right-hand pane under DACL Management and enter the following
values for the new dACL:
Note:
Copy-and-paste the DACL content from https://tools.demo.local/cp/DACL_POSTURE_REMEDIATION.txt
* Name POSTURE_REMEDIATION
Description Permit access to posture and remediation services and deny all
other access. Permit general http and https for redirection only.
* DACL Content permit udp any any eq domain
permit icmp any any
permit tcp any host 10.1.100.21 eq 8443
permit tcp any host 10.1.100.21 eq 8905
permit udp any host 10.1.100.21 eq 8905
permit tcp any host 10.1.100.222 eq 80
The following describes the purpose of individual ACL entries:
Downloadable ACL Entry
permit udp any any eq domain
permit icmp any any
permit tcp any host 10.1.100.21 eq 8443
permit tcp any host 10.1.100.21 eq 8905
permit udp any host 10.1.100.21 eq 8905
permit tcp any host 10.1.100.222 eq 80
c.
Step 3
Description
Permit DNS for name resolution
Permit ICMP for initial troubleshooting
Permit CWA/CPP to ISE Policy Service node
Allow Agent discovery direct to Policy Service node
Allow Agent discovery and keep-alives
Explicit allow to remediation server
Click Submit when completed.
Define dACL for AD Login Access
Click Add from the right-hand pane under DACL Management and enter the following values for
the new dACL:
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 26 of 70
Lab Exercise 3.2: Define Authorization Policy for Client Provisioning and Posture Compliance
Note:
Copy-and-paste the DACL content from https://tools.demo.local/cp/DACL_AD_LOGIN_PROCESS.txt
* Name AD_LOGIN_ACCESS
Description Employee AD Access
* DACL Content permit udp any eq bootpc any eq bootps
permit udp any any eq domain
permit icmp any any
permit tcp any host 10.1.100.10 eq 88
permit udp any host 10.1.100.10 eq 88
permit udp any host 10.1.100.10 eq ntp
permit tcp any host 10.1.100.10 eq 135
permit udp any host 10.1.100.10 eq netbios-ns
permit tcp any host 10.1.100.10 eq 139
permit tcp any host 10.1.100.10 eq 389
permit udp any host 10.1.100.10 eq 389
permit tcp any host 10.1.100.10 eq 445
permit tcp any host 10.1.100.10 eq 636
permit udp any host 10.1.100.10 eq 636
permit tcp any host 10.1.100.10 eq 1025
permit tcp any host 10.1.100.10 eq 1026
Step 4
Review URL Redirect ACL on the access switch. An Authorization Profile will reference this ACL
and work in conjunction with the accompanying dACL applied to the switchport interface.
a. From the Admin client PC, use the desktop shortcut for the PuTTY
to launch a
terminal session to the c3560cg switch using the credentials admin / ISEisC00L.
b. Enter the following command at the access switch exec shell prompt to verify the
contents of the ACL:
3560CG# show ip access-lists ACL-AGENT-REDIRECT
Extended IP access list ACL-AGENT-REDIRECT
10 deny tcp any host 10.1.100.222 eq www
20 permit tcp any any eq www
Step 5
Define a new Authorization Profile PostureRemediation that leverages both the new dACL for
port access control and the URL Redirect ACL for traffic redirection.
a. Return to the ISE admin interface from the Admin client PC.
b. Click Authorization Profiles from the left-hand pane under Policy > Policy Elements >
Results > Authorization.
c.
Click Add from the right-hand pane and enter the values for the Authorization Profile as
shown below.
Name
Description
Access Type
DACL Name
Web Redirection
(CWA, MDM, NSP, CPP)
Posture Remediation
Permit access to posture and remediation services; redirect
traffic to client provisioning and posture services.
ACCESS_ACCEPT
POSTURE_REMEDIATION
Client Provisioning (Posture)
ACL: ACL-AGENT-REDIRECT
Value: Client Provisioning Portal (default)
d. The resultant Attribute Details should appear at the bottom of the page as the following:
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 27 of 70
Lab Exercise 3.2: Define Authorization Policy for Client Provisioning and Posture Compliance
Access Type = ACCESS_ACCEPT
DACL = POSTURE_REMEDIATION
cisco:cisco-av-pair=url-redirect-acl=ACL-AGENT-REDIRECT
cisco:cisco-av-pair=url-redirect =https://ip:port/portal/gateway?sessionId=SessionIdValue&portal=&action=cpp
e. Scroll to bottom of page and click Submit to apply your changes.
Step 6
Define a new Authorization Profile for Compliant Employees named Employee that allows
complete access.
a. From the left-hand pane under Policy > Policy Elements > Results > Authorization>
Authorization Profiles.
b. Click Add from the right-hand pane and enter the values for the Authorization Profile as
shown below.
Name
Description
Access Type
DACL Name
c.
Employee
Full Access
ACCESS_ACCEPT
PERMIT_ALL_TRAFFIC
The resultant Attribute Details should appear at the bottom of the page as the following:
Access Type = ACCESS_ACCEPT
DACL = PERMIT_ALL_TRAFFIC
d. Scroll to the bottom and click Submit to apply your changes.
Step 7
Define a new Authorization Profile for AD Login
a. Click Authorization Profiles from the left-hand pane under Policy > Policy Elements >
Results > Authorization.
b. Click Add from the right-hand pane and enter the values for the Authorization Profile as
shown below.
Name
Description
Access Type
DACL Name
c.
AD Login
Allow machine to login to AD through dot1.x
ACCESS_ACCEPT
AD_LOGIN_ACCESS
The resultant Attribute Details should appear at the bottom of the page as the following:
Access Type = ACCESS_ACCEPT
DACL = AD_LOGIN_ACCESS
d. Scroll to the bottom and click Submit to apply your changes.
Step 8
Update the Authorization Policy to support posture compliance.
a. Go to Policy > Policy Sets > Default
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 28 of 70
Lab Exercise 3.2: Define Authorization Policy for Client Provisioning and Posture Compliance
b. Update the existing Authorization Policy with the following values as highlighted using the
selector at the end of a rule entry to insert or duplicate rules above:
S
Rule Name
Groups
Other Conditions
Permissions
Domain Computer
Any
AD Login
Basic_Authenticated_Access Any
demoAD.local:ExternalGroups
EQUALS demo.local/Users/Domain Computers
demoAD.local:ExternalGroups
EQUALS demo.local/HCC/Groups/employees
AND
Session:PostureStatus EQUALS Compliant
demoAD.local:ExternalGroups
EQUALS demo.local/HCC/Groups/Employees
AND
Session:PostureStatus NOT EQUALS Compliant
Network_Access_Authentication_Passed
Employee Compliant
Any
Employee NonCompliant
Any
Default
DenyAccess
Any
c.
Employee
Posture Remediation
PermitAccess
Click Save to apply your changes.
End of Exercise: You have successfully completed this exercise.
Proceed to next section.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 29 of 70
Lab Exercise 3.3: Test and Monitor Client Provisioning Services for AnyConnect
Lab Exercise 3.3: Test and Monitor Client Provisioning
Services for AnyConnect
Exercise Description
This exercise validates the Client Provisioning and Authorization Policy configuration completed
in the previous lab exercises. Since no Posture Policy has been configured, all users should be
posture compliant. The AC ISE Posture Agent will be tested and monitored in this exercise. In
addition to AC ISE Posture Agent provisioning, this exercise will also validate agent policies such
as AUP, auto-closure of login success screens, and agent profile configuration.
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Login to the secured lab network from a Windows 7 PC client as an Employee via 802.1X
machine authentication and user authentication and verify NAC Agent provisioning.
Review ISE and switch logs to validate proper operation and application of the
Authorization Policy.
Lab Exercise Steps
Step 1
Power ON VM guest p##-w7pc-corp.
Step 2
Establish a terminal session with the access switch (10.1.100.1).
Step 3
Validate the session status of the switchport authorization after Windows login (802.1X User
authentication):
a. At the W7PC-corp VM console, send Ctrl+Alt+del and login to Windows domain.
To login to a Windows VM, select Guest > Send Ctrl+Alt+del from the VM Console
menu:
Login as user DEMO\employee1 / ISEisC00L. Issue show authentication sessions for
interface GigabitEthernet0/4. After successful 802.1X user authentication, the
Authorization Policy should match the Employee_NonCompliant rule (Authorization
Profile = Posture_Remedation). The output should appear similar to that shown below:
3560CG# sh auth sess int g0/4 details
3560CG(config-if)#do sh auth sess int G0/4 det
Interface: GigabitEthernet0/4
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 30 of 70
Lab Exercise 3.3: Test and Monitor Client Provisioning Services for AnyConnect
MAC Address:
IPv6 Address:
IPv4 Address:
User-Name:
Status:
Domain:
Oper host mode:
Oper control dir:
Session timeout:
Common Session ID:
Acct Session ID:
Handle:
Current Policy:
0050.5693.a76b
Unknown
10.1.10.201
DEMO\employee1
Authorized
DATA
multi-auth
both
N/A
0A0164010000001B0233334D
0x00000015
0x54000010
POLICY_Gi0/4
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecure
Server Policies:
ACS ACL: xACSACLx-IP-POSTURE_REMEDIATION-5464abc7
URL Redirect: https://ise1.demo.local:8443/portal/gateway?sessionId=0A0164010000001B0233334D&portal=528d2310276c-11e4-9866-005056bf01c9&action=cpp&token=a654130b16dfa0bcc928d989f42226a8
URL Redirect ACL: ACL-AGENT-REDIRECT
Runnable methods list:
Method
mab
dot1x
State
Not run
Authc Success
a. Verify that 802.1X user authentication (User-Name = DEMO\employee1) completed
successfully and that the dACL (ACS ACL) named POSTURE-REMEDIATION pushed to
the interface.
b. A named URL Redirect ACL = ACL-AGENT-REDIRECT has also been applied that
defines the traffic to be redirected to the link specified by URL Redirect. The redirect
URL must include the domain name of the ISE Policy Service node, reference to port
8443, the current session ID, and reference action to cpp (Client Provisioning Portal). If
any of these items are missing, then web authentication will fail.
Step 4
Validate Client Provisioning (aka Web-Deploy) for the AnyConnect.
a. From w7pc-corp, launch Firefox web browser and type in www.cisco.com. It will
immediately redirect to ISE client provisioning portal (CPP). (Accept/Confirm any browser
certificate warnings if present)
Note:
If receiving [ 500 ] Internal Error, please clear auth session on the switch while the user logged-in and try
again. Defect: CSCup20844
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 31 of 70
Lab Exercise 3.3: Test and Monitor Client Provisioning Services for AnyConnect
b. Click the Start button.
c.
After CPP takes ~ 10 seconds to detect any existing AnyConnect installation, it shows an
info page for the location to download and install AnyConnect.
d. Expand + This is my first time here and click the hyperlink and download AnyConnect
ISE Setup Assistant.
e. Double click to run the downloaded program. If prompted by Windows UAC, enter
credentials admin / ISEisC00L.
Note:
Admin privileges are required to install AnyConnect for the first time. Once installed, upgrades can occur
without escalated privileges. AnyConnect can also be distributed using an MSI installer package.
f.
AnyConnect ISE Network Setup Assistant window appears. Click Connect to start
running AnyConnect Downloader Click Yes to restart your computer now when
prompted.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 32 of 70
Lab Exercise 3.3: Test and Monitor Client Provisioning Services for AnyConnect
g. After reboot and re-login, AnyConnect shows an AUP.
h. Click Accept to agree to the AUP. The login success screen should display indicating
Full Network Access and automatically close after 2 seconds per the Agent profile
configuration.
i.
Step 5
The client should now have full network
access. To validate, open a web browser and
verify that access to www.cisco.com is
allowed.
Verify the session status of the switchport
authorization for a compliant Employee.
a. Repeat the show authentication sessions output for interface GigabitEthernet0/4. The
Authorization Policy should match the Employee rule (Authorization Profile = Employee)
and output should appear similar to that shown below:
3560CG#sh auth sess int g0/4 details
3560CG(config-if)#do sh
Interface:
MAC Address:
IPv6 Address:
IPv4 Address:
User-Name:
Status:
Domain:
Oper host mode:
Oper control dir:
Session timeout:
Common Session ID:
Acct Session ID:
Handle:
Current Policy:
auth sess int G0/4 det
GigabitEthernet0/4
0050.5693.a76b
Unknown
10.1.10.201
DEMO\employee1
Authorized
DATA
multi-auth
both
N/A
0A0164010000001B0233334D
0x00000015
0x54000010
POLICY_Gi0/4
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 33 of 70
Lab Exercise 3.3: Test and Monitor Client Provisioning Services for AnyConnect
Security Policy:
Security Status:
Server Policies:
ACS ACL:
Should Secure
Link Unsecure
xACSACLx-IP-PERMIT_ALL_TRAFFIC-4478ace7
Runnable methods list:
Method
State
mab
Not run
dot1x
Authc Success
b. In the above output, note that the dACL (ACS ACL) = PERMIT_ALL_TRAFFIC has been
successfully downloaded to the interface to grant the compliant Employee full network
access.
Step 6
Verify the authentication/authorization phases of the 802.1X Auth and Client Provisioning from
the ISE admin interface.
a. Go to Operations > Authentications. View the recent entries associated with the
Employee session by MAC Address, IP address, Interface, or Session ID. It may be help
to filter the log entries by entering a couple bytes of the Session ID or MAC address
(Calling Station ID) into the appropriate column header and hitting Enter. Click the circled
x in the field to clear the filter.
b. Referring to the sample log below, you should see entries similar to the following that
match the output received from the switch, where 1 is the lowest or first entry:
1.
Successful 802.1X machine authentication of the Domain Computer host/w7pc-corp.demo.local using
PEAP(EAP-MSCHAPv2); Authorization Profile named AD_Login applied.
2.
dACL named AD_LOGIN_ACCESS has been successfully downloaded.
3.
Successful 802.1X user authentication of the Domain User DEMO\employee1; Authorization Profile named
Posture_Remediation applied.
4.
dACL named POSTURE_REMEDIATION has been successfully downloaded.
5.
Successful authentication of host/w7pc-corp using EAP-FAST (EAP-MSCHAPv2) due to NAM installation.
6.
dACL named AD_LOGIN_ACCESS has been successfully downloaded.
7.
Successful machine authentication of host/w7pc-corp.demo.local using PEAP (EAP-MSCHAPv2) due to reboot.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 34 of 70
Lab Exercise 4: Guest Access Management
8.
Successful machine authentication of host/w7pc-corp using EAP-FAST (EAP-MSCHAPv2) due to reboot.
9.
Successful 802.1X user authentication of the Domain User employee1; Authorization Profile named
Posture_Remediation applied.
10. dACL named POSTURE_REMEDIATION has been successfully downloaded.
11. Posture reported compliant and dynamic authorization (CoA) succeeded for session based on posture status
change.
12. Authorization Profile named Employee applied; dACL PERMIT_ALL_TRAFFIC applied.
13. dACL named PERMIT_ALL_TRAFFIC has been successfully downloaded.
14. Session State is Started.
End of Exercise: You have successfully completed this exercise.
Proceed to next section.
Lab Exercise 4: Guest Access Management
Exercise Description
This exercise will show you how to setup and configure Guest Access Management with ISE 1.3.
Cisco ISE Guest gives sponsors/employees/lobby ambassadors the ability to create a guest
account and send it to a guest. Guests can also create their own accounts and the additional
ability can be required for guests to get approval by a sponsor or person they are visiting. There
are three built-in types of guest portals: Hotspot, Self-Registered, and Sponsored. We will be
working with the first 2 use cases (hotspot and self-registered) in this lab. The self-registered
portal is essentially the same as sponsored (without the setting to allow self reg)
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Lab Exercise 4.1: Configure Authorization Profiles for Guest Hotspot and Self Registration
Lab Exercise 4.2: Configure Policy Sets for Guest Authentication and Authorization
Lab Exercise 4.3: Configure Hotspot with basic customization
Lab Exercise 4.4: Test the Hotspot Portal
Lab Exercise 4.5: Configure Settings for Self-Registered with Sponsor Approval
Lab Exercise 4.6: Test Self Registration Portal with Approval Flow
Lab Exercise 4.7: Configure Settings for Sponsored Access
Lab Exercise 4.8: Test Sponsored Guest Flow
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 35 of 70
Lab Exercise 4.1: Configure Authorization Profiles for Guest Hotspot and Self Registration
Lab Exercise 4.9: Work with Guest reporting
Lab Exercise 4.1: Configure Authorization
Profiles for Guest Hotspot and Self Registration
Exercise Description
In this Exercise you will setup the needed authorization profiles and policies to work with policy
sets for a hotspot and self-registration portals
Exercise Objective
In this exercise, your goal is to complete the following task:
Configure Authorization Profiles for Hotspot & Self-Registration policies
Step 1
Return to the ISE UI and login if needed
Step 2
Configure Authorization Profiles for Hotspot Redirect
a. Navigate to Policy Policy Elements Results
b. Expand Authorization
c.
Step 3
Click Authorization Profiles
Configure Authorization Profile for Hotspot Redirect
a. Click Add
* Name
Description
* Access Type
Common Tasks
Web Redirection
(CWA )
HotSpot Redirect
ACCESS_ACCEPT
Hot Spot
ACL: ACL-WEBAUTH-REDIRECT Value: Hotspot Guest Portal (default)
Note: The ACL is case-sensitive and should match exactly as defined in WLC.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 36 of 70
Lab Exercise 4.1: Configure Authorization Profiles for Guest Hotspot and Self Registration
b. Click Submit
Step 4
Configure Authorization Profile for Guest Redirect
a. Click Add
* Name
Description
* Access Type
Common Tasks
Web Redirection
(CWA )
Guest Redirect
ACCESS_ACCEPT
Centralized Web Auth
ACL: ACL-WEBAUTH-REDIRECT Value: Self-Registered Guest Portal (default)
Note: The ACL is case-sensitive and should match exactly as defined in WLC.
b. Click Submit
Step 5
Configure Authorization Profile for Guest Permit Access
a. Click Add
* Name Guest Permit
Description Internet Access for Guests
* Access Type ACCESS_ACCEPT
Common Tasks
Airespace ACL Name GUEST_ACL
Note: The ACL is case-sensitive and should match exactly as defined in WLC.
b. Click Submit
Note: You should have 3 new Authorization profiles after completing this task: HotSpot_Redirect, Guest_Redirect and GuestPermit
Authorization profiles for the basic portal setup has been completed. Lets now work with the Policy Sets.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 37 of 70
Lab Exercise 4.2: Configure Policy Sets for Guest Authentication and Authorization
Lab Exercise 4.2: Configure Policy Sets for
Guest Authentication and Authorization
Exercise Description
In this exercise you will setup the needed authorization profiles and policies using policy sets to
work with the hotspot and self-registration portals
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Step 1
Configure Policy Sets for Wireless_MAB
Configure Authentication Policies for Wireless_MAB
Configure Authorization Policies for Hotspot and Self Register Portal
Configure the Policy Set for Guest Access
a. Navigate to Policy Policy Sets
b. Click on the + and Create Above
c.
Click Edit on the far right to edit the Policy Name and Conditions
Attribute
Value
Name
Description
wirelessMAB
-
Select Attribute
Select Existing Condition from Library
Compound Condition
Wireless_MAB
d. Click Done
e. Expand the Authentication Policy
f.
Click Edit for the Default Rule
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 38 of 70
Lab Exercise 4.2: Configure Policy Sets for Guest Authentication and Authorization
g. Under Allowed Protocols
Select HostLookup
h. Select Identity Source
Internal Endpoints
i.
Select Continue for If
user not found
j.
Click Done
k.
l.
Collapse Authentication Policy
Expand Authorization Policy
Info for saving time: The following table and screenshot are how we are setting up the authorization policy for HotSpot and Guest
Access if you would like to attempt this without following the steps then please do, or continue on with the steps below the
screenshot. Remember after you enter your first rule above default you can use Duplicate above instead to save time. Dont forget
to click Save and then skip to Section 3.3.
Rule Name
Guest Internet Access
Guest Redirect
Identity Groups
Other Conditions
Any
Radius:Called-Station-ID ENDS_WITH guest
AND
NetworkAccess:UseCase EQUALS Guest Flow
Any
Radius:Called-Station-ID ENDS_WITH guest
Hotspot Internet Access
GuestEndpoints Radius:Called-Station-ID ENDS_WITH hotspot
Guest Permit
Hotspot Redirect
Any
Radius:Called-Station-ID ENDS_WITH hotspot
HotSpot Redirect
Default
Any
DenyAccess
Step 2
Permissions
Guest Permit
Guest Redirect
Configure Authorization Policy for Hotspot Redirection
a. Click arrow to the right of edit of Default Rule and insert a new rule above
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 39 of 70
Lab Exercise 4.2: Configure Policy Sets for Guest Authentication and Authorization
b. Enter Rule Name as Hotspot Redirect
c. Click the + next to Condition
d. Choose Condition Create new Condition
e. Select attribute Radius Called-Station-ID Ends With hotspot
Note: If you enter Calling-Station-ID then it wont work, be careful
f.
Under Permissions click + Select an item
Standard Hotspot Redirect
g. Click Done
Step 3
Configure Authorization Policy for Hotspot Internet Access
a. Click arrow to the right of Hotspot Redirect and duplicate above, change the values to the
following
Info for Saving time: Remember to use Duplicate above and then change what is needed instead of inserting new fresh policies
Attribute
Rule Name
Identity Group
Conditions
Permissions
Value
Hotspot Internet Access
Endpoint Identity Group GuestEndpoints
Radius: Called-Station-ID Ends with hotspot
Guest Permit
b. Click Done
Step 4
Configure Authorization Policy for Guest Redirect
a. Click arrow to the right of edit of HotSpotInternetAccess and duplicate above
Attribute
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
Value
11/17/2014 10:17:00 AM PST
Page 40 of 70
Lab Exercise 4.3: Configure Hotspot with basic customization
Attribute
Rule Name
Identity Group
Conditions
Permissions
Value
Guest Redirect
Any
Create New Condition Select Attribute
Radius Called-Station-ID Ends with guest
Standard Guest Redirect
b. Click Done
Configure Authorization Policy for Guest Permit
a. Click arrow to the right of edit of GuestRedirect and duplicate above
Step 5
Attribute
Rule Name
Identity Group
Value
Guest Internet Access
Any
Create New Condition Select Attribute
Radius Called-Station-ID Ends with guest
Conditions
Permissions
Add another attribute/value
NetworkAccess: UseCase EQUALS Guest Flow
Standard Guest Permit
b. Click done
Dont Forget to Click Submit
Hotspot and Guest Authentication/Authorization Setup has been completed. Lets now look at the Default Hotspot Portal.
The default settings are a good start. We will also go over some of the cool extras to go along with it.
Lab Exercise 4.3: Configure Hotspot with basic
customization
Exercise Description
In this Exercise you will configure the minimal settings plus a few minor customizations setting up
the hotspot portal. There are many options, features and functions for setting up and customizing
guest to play with later on your own
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Configure Hotspot Settings
Work with basic customization
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 41 of 70
Lab Exercise 4.3: Configure Hotspot with basic customization
Step 1 Click Guest Access Configure Guest Portals
Notice how the defaults portals indicate
they have been configured in an
authorization policy. It also explains
what each of the portals is used for.
This makes it easier to setup and
troubleshoot.
Step 2 Click on the Hotspot Guest Portal (default) and click Edit
Lets highlight some of the new settings that make hotspot operational. Note this is also known as DRW
(Device Registration Web Auth) and it is meant for simple registration of a device MAC address with a
splash page, optional AUP and other options.
Step 3 Navigate to the section under Portal Settings that shows the Endpoint Identity Groups and
Purging.
Step 4 Look at the following settings, Guest Endpoint and Purging, leave these default.
GuestEndpoints:
This Hotspot configuration by default will automatically take the MAC address from the MAB (MAC
authentication bypass) and place it into GuestEndpoints group. Remember in our authorization policy
that we based GuestInternet Access off GuestEndpoints as an identifier. This group could be changed so
that you have different Endpoint groups for different portals or types of access. Its also available in the
self registered and sponsor portal types. Dont change this group.
Purging:
Next notice the new purge policy. This will remove the device after it has been in the endpoint group for
30 days. The purge runs daily. This setting can be set as low as 1 day. There is no way to set it lower as
the purge runs as a process 1x a day. In ISE 1.2, DRW, required the endpoints to be manually purged
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 42 of 70
Lab Exercise 4.3: Configure Hotspot with basic customization
from the database when you wanted to remove access. There is a link to advanced purge policies where
you can purge
Step 5 Click on the little arrow next to Portal Settings to collapse this section.
Step 6 Under the Acceptable Use Policy (AUP) Page Settings notice Include an AUP is already
enabled - An AUP is not necessary but likely a customer would want one.
Step 7 Check the box to enter an access code of iseiscool An access code is used to protect the open
SSID from those outside of your business from getting Internet access. This can also be
configured for self registration and sponsor approval flows
Step 8 Notice on the right side of the screen the flow chart in real-time, if you change/add/remove a
component you see the changes immediately. Try toggling the checkbox Include An AUP off and
on and notice the difference
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 43 of 70
Lab Exercise 4.3: Configure Hotspot with basic customization
A new option in ISE 1.3 is the option to customize where the user is sent for a success. Configure
success page redirection to a static URL
Step 9 Scroll down to the section that says Authentication Success Settings
Step 10 Enter URL: http://www.cisco.com
Step 11 Scroll to the top of the page and Click Save
Step 12 Click on the Page Customization section at the top of the page
ISE 1.3 gives you basic customization built right into the product. It also makes it easier to
see what changes you are making in real-time. We wont go into detail of all of these but to
start you notice at the top of the page you can change things like the logos, banner and main
text elements. You can also choose from some built in color themes.
Step 13 Lets start by messing with the portal theme. Click on the pull down and pick the High Contrast
Theme. Notice how the Preview window in the bottom right of the screen shows the changes.
Step 14 Now click on the Tweaks button to see how you change the
colors a little more. Feel free to play around a little, click on
the Page Background Color. When done, click OK. To
tweak the button color equires advanced customization
using CSS and themes (e.g. jQuery Theme Roller, not
covered in this class). Now that you have played around with
the tweaks go back to the Portal Theme and change it back
to the Default Blue Theme
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 44 of 70
Lab Exercise 4.3: Configure Hotspot with basic customization
Step 15 Lets upload a logo and a banner
Step 16 On the workstation using Firefox and in a new tab, click on the bookmark for tools/guest.
Step 17 Click on the link for iseiscool-images.zip
Step 18 Check Save File and Click OK the file will be saved to C:\Users\admin\Downloads
Step 19 Click on the download arrow in the upper right of firefox to open the location it downloaded
Step 20 Right click on the package and choose the option to Extract All
Step 21 Use the default location C:\Users\admin\Downloads\iseiscool-images
Step 22 Click Next and OK to close window, close all tabs and explorer windows for the download
process
Step 23 Go back to ISE tab in Firefox
Step 24 Upload the banner and logo for mobile (iseiscool_logo_hotspot.png & iseiscool-banner.png) from
the location C:\Users\admin\Downloads\iseiscool-images
Note: Use the same logo for both mobile and desktop
Step 25 Remove the text for Banner title as it Is part of the logo (you may need to click in another place on
the page for the mobile preview to refresh)
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 45 of 70
Lab Exercise 4.4: Test the Hotspot Portal
Step 26 Below this main section where you can tweak the overall look and feel, you can also go into each
of the pages. Depending on your portal settings and portal type you will see different options on
the left hand side of the page. You can also tweak the text in the different areas on the page.
Step 27 After some basic customization is done check out the desktop preview (same as the portal test
URL at the top of the page) by clicking on the option in the bottom right of the mini preview.
Note:
You can test full flow without using a real client.
Step 28 Close the desktop preview
Step 29 Click Save at the top of the page
You have now completed setup of the Hotspot Portal. Next step is to try it out.
Lab Exercise 4.4: Test the Hotspot Portal
Exercise Description
In this Exercise you will work with the hotspot portal you configured
Exercise Objective
In this exercise, your goal is to complete the following task(s):
Step 1
Test the hotspot Portal
Enable SSIDs hotspot and guest in WLC
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 46 of 70
Lab Exercise 4.4: Test the Hotspot Portal
a. Login to vWLC web portal @ https://vwlc.demo.local as admin / ISEisC00L
b. Menu WLANs
c.
Select WLAN ID 1 ##-ISECOLD, Disable Selected from the drop-down next to Go, and
hit Go.
d. Select WLAN ID 2 ##-hotspot, Enable Selected from the drop-down next to Go, and hit
Go.
Step 2
Remove the iPad from ISE internal endpoints (as we registered it during the BYOD lab 2 and it
needs to be removed for this lab)
On ISE GUI go to Administration > Identity Management > Identities > endpoints
Select your iPad and Select Delete > Delete Selected
Step 3
Step 4
Step 5
From the workstation double click on the icon VNC-to-iPad on the desktop and press any key
to continue. The IPad screen will launch
If not already on the home screen, right click on the screen
Go to settings Wi-Fi
If Wi-Fi is disabled then turn it on and skip past the clean-up steps
Here are the steps to start with new session (clean-up)
a. On the iPad, navigate to Settings > General > Profiles. Remove any existing profiles, if
present.
Note: You might not see the Profiles menu option, when no profile installed on the iPad.
b. Next on the iPad, go to Settings > Safari and hit Clear History as well as Clear
Cookies and Data.
c. Forget any networks the device is automatically connecting to
d. Disable the Wi-Fi
e. On the Windows workstation, navigate to Admin Identity Management Identities
Endpoints and delete the iPad, you can delete anything in the list as there should only be
your iPad connected
f. Launch Firefox, go to vwlc, and login.
g. On the vWLC click on Monitor then Clients on the left side bar
h. Find your wireless session (there should only be one), click on the MAC address and
then click Remove in the upper right of the window
i. Go back to the iPad and enable the Wi-Fi
On the iPad from the list of wireless networks find the one that shows XX-hotspot, click to
connect to this
Step 7
Once youre connected to the hotspot (shows in the upper left of the iPad screen). Right click on
the iPad screen to show the home screen and then launch Safari.
Step 8
Using safari enter a site to visit, cnn.com, you will be redirected to the hotspot portal
Step 9
Enter the passcode iseiscool and click accept
Step 10 You are redirected to a success page and then can choose your original site.
Step 11 Enter cnn.com
Step 12 Navigate to Operation Authentications and look at the sessions that came through.
Step 6
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 47 of 70
Lab Exercise 4.5: Configure Settings for Self-Registration with sponsor approval flow
a. When you first come in MAB from hotspot SSID redirects to hotspot
b. After AUP acceptance, the device is authorized by GuestEndpoints Group on a separate
line.
Step 13 Cleanup the iPad connection before continuing on with self-registration
a. Close the browser tab on the iPad
b. Right click to go to home screen
c. Forget the hotspot network on the iPad, make sure its not connecting to another network,
if it is also forget such network.
d. Turn Wi-Fi off
e. Navigate to Admin Identity Management Identities Endpoints and delete the
iPad, you can delete anything in the list as there should only be your iPad connected
HOTSPOT COMPLETE! You have now completed setup and testing of the Hotspot Portal. Next lets look into
Self-Registration with Sponsor Approval
Lab Exercise 4.5: Configure Settings for SelfRegistration with sponsor approval flow
Exercise Description
In this Exercise you will configure the minimum settings to allow you to use the self-registered
flow with sponsor approval
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Configure Guest Settings
Configure Sponsor Groups
Configure Self Registration Portal
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 48 of 70
Lab Exercise 4.5: Configure Settings for Self-Registration with sponsor approval flow
Step 1 Setup Guest settings to work for Self Registration
a.
b.
c.
d.
e.
f.
g.
h.
i.
Navigate to Guest Access Settings
Expand Guest Email Settings
Click on link to configure SMTP server mail.demo.local
Close the external page
Verify Enable email notifications to guests
Verify sponsor@demo.local as the Default From email address
Switch to use Send notifications from sponsors email address (if sponsored)
Click Save
Expand Guest Locations and SSIDs
Important Info: This setting is needed as the default comes as San Jose, the workstation is using time zone as UTC so we need to
add in a location of UTC for it to create an account with a valid start time. This is instead of having to choose from a LONG list of
time zones as in prior ISE releases
j.
k.
l.
Note:
Enter a Location Name as UTC
and Time zone as UTC
Click Add
Click Save
If you see a UI WAP Error please log out of ISE and log back in
Step 2 (Use Internet Explorer if Firefox doesnt work) Setup AD sponsor group in All_Accounts
a. Navigate to Guest Access Configure
b. Click on Sponsor Groups ALL_ACCOUNTS Edit
c. Click the Members button and move Domain Users over to the Selected User Groups
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 49 of 70
Lab Exercise 4.5: Configure Settings for Self-Registration with sponsor approval flow
d. Click OK
Note: If those steps dont work with Firefox: use Internet Explorer
Step 3 (Use Internet Explorer if Firefox doesnt work) Configure Guest Locations for this sponsor
a. Under Select the locations that guests will be visiting Choose UTC
Critical Info: Its important to setup the location where your user(s) are located, otherwise when the account is created it will be
using San Jose by default but the browser of the sponsor (workstation) is set to use UTC time. The account wont be active until
many hours later since it was created using SJC time. This is critical when setting up guest to create the locations your sponsors
will be using for visiting guests. Our admin machine is in UTC time so the guest accounts needs to be created per UTC time in order
for the account to be active
If you have trouble viewing this try setting it using Internet Explorer or log-out and then log back in.
Step 4 (Use Internet Explorer if Firefox doesnt work) Allow the Sponsor to send SMS (text messages)
for notifying guest of their credentials
a. Scroll down to the section that says Sponsor Can
b. Check the box that says Send SMS notifications with Guest Credentials
Step 5 (Use Internet Explorer if Firefox doesnt work) Now scroll to the top of the page and click Save
Step 6 Click Close
(Return to use Firefox) Configure Self Registration Portal
Click on Guest Portals Self-Registered Guest Portal (default)
Click Edit
Collapse the following areas as we are not changing them from the defaults for this lab: Portal
Settings, Login Page Settings
Step 11 Under Self-Registration Page Settings
Step 12 Under Guests can choose from these locations to set their time zone: Pick UTC time.
Step 7
Step 8
Step 9
Step 10
Critical Note: This was discussed before
Take a quick note of the SMS Service Provider, information
Note we are using a global provider to cover any mobile number since the lab participants could be from anywhere in the world. We
are using click-a-tell as the provider and their account covers lots of countries and service providers:
https://www.clickatell.com/pricing-and-coverage/standard-coverage/
Like the locations if you only have 1 choice it wont be displayed. There are other built in providers, these are examples of free
providers in the U.S. you can configure other providers if needed. Free providers would be listed for a guest to choose from so that
the site being visited doesnt have to pay for the texting. A global default would be used as a paid server to choose in case their
provider is not in the list. There are also new options to use SMTP and HTTP API SMS providers which opens up ISE capabilities to
be able to work with many more providers. ISE 1.2 was resitrcted to SMTP based and was severely limited in its customization so
could only work with a select few. Read more in the admin guide.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 50 of 70
Lab Exercise 4.5: Configure Settings for Self-Registration with sponsor approval flow
Step 13 Check the box to the right of Person being visited so that the field is required when doing self-
registration. This will require a guest to enter an email address of employee they are visiting.
Info only: There is currently no way in ISE to verify the person being visited email or name. This could be done with advanced
customization by integrating with an external LDAP for the lookups.
Require self-registered guests to be approved
a. Email approval request to: person being visited
Step 14 Check the box to
Info only: If choosing sponsor email addresses listed below, it could be the email of a sponsor or a group of sponsors
Step 15 After registration submission, direct guest to - Login page with instructions about how to
obtain login credentials
Step 16 Check both Email and SMS notifications are checked under Send credential notification upon
approval using:
Important Info: This could also be the email of a sponsor or a group of sponsors System behavior for email and SMS notifications:
There is no way to currently give a guest the ability to choose email or SMS as an option to choose for notification. If you check both
then they will both be required. If you choose Email then the guest will be required to enter an email address and only email
notification will work (even though the user enters their phone number). The same will hold true if you check SMS, they must enter a
phone number and email notification wont work even though they entered an email. For this demo we are showcasing both.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 51 of 70
Lab Exercise 4.6: Test the self registration with approval flow
Step 17 Scroll to the top of the page and click Save
Step 18 Now access Portal Page Customization
Step 19 Click on Self-Registration
Step 20 Scroll to the section: Login page
Change the text from:
An email or an SMS message has been sent to you containing your sign on credentials.
To:
After the person you are visiting approves your account, you will be notified by email or text the
credentials needed to login
Step 21 Click Save and Close.
You have now completed setup of Self-registration with sponsor approval setup
Lab Exercise 4.6: Test the self registration with
approval flow
Exercise Description
In this Exercise you will test the steps needed to do self registration with sponsor approval
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Access the guest portal
Create an account
Sponsor approves the account
Guest receives notifications
Guest access portal and gets access
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 52 of 70
Lab Exercise 4.6: Test the self registration with approval flow
Step 1
Enable SSID guest in WLC
a. Login to vWLC web portal @ https://vwlc.demo.local as admin / ISEisC00L
b. Menu WLANs
c.
Select WLAN ID 2 ##-hotspot, Disable Selected from the drop-down next to Go, and hit
Go.
d. Select WLAN ID 3 ##-guest, Enable Selected from the drop-down next to Go, and hit Go.
Step 2
Step 3
Step 4
Step 5
From the workstation double click on the icon VNC-to-iPad on the desktop and press any key
to continue. The IPad screen will launch
If not already on the home screen, right click on the screen
Go to Settings Wi-Fi
If Wi-Fi is disabled then turn it on and skip pass the clean up steps below
Here are the steps to start with new session on iPad (clean-up)
a. On the iPad, navigate to Settings > General > Profiles. Remove any existing profiles, if
present.
Note: You might not see the Profiles menu option, when no profile installed on the iPad.
b. Next on the iPad, go to Settings > Safari and hit Clear History as well as Clear
Cookies and Data.
c. Forget any networks the device is automatically connecting to
d. Disable the Wi-Fi
e. On the Windows workstation, navigate to Admin Identity Management Identities
Endpoints and delete the iPad, you can delete anything in the list as there should only be
your iPad connected
f. Launch Firefox, go to vwlc, and login.
g. On the vWLC click on Monitor then Clients on the left side bar
h. Find your wireless session (there should only be one), click on the MAC address and
then click Remove in the upper right of the window
i. Go back to the iPad and enable the Wi-Fi
Step 6
Step 7
Step 8
On the iPad from the list of wireless networks find the one that shows XX-guest, click to connect
to this
Once youre connected to the hotspot (shows in the upper left of the iPad screen). Right click on
the iPad screen to show the desktop and then launch Safari.
Using safari enter a site to visit, cnn.com, you will be redirected to the guest portal
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 53 of 70
Lab Exercise 4.6: Test the self registration with approval flow
Step 9
Click on Dont have an account
Step 10
Create a guest account using the following info (at a minimum these are basic to show the flow):
Attribute
Username
Value
iseiscool
Email address*
guest@demo.local
Phone number*
12025550133
Description
(new) This could be anything the user chooses.
To receive email notification of credentials once
account is approved, this must be entered as it is.
Enter your phone number with country code and
without the 00, e.g. US is 1, NL is 31. If you dont
want to receive a text then enter a bogus number,
12025550133
In this chosen time zone to express from and to
time of the guest account validity.
Location*
UTC
Person being
visited(email)*
sponsor@demo.local flow to allow an employee to receive an email
(new) This is a new field will work in the approval
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
where they can go and approve their visiting guest.
11/17/2014 10:17:00 AM PST
Page 54 of 70
Lab Exercise 4.6: Test the self registration with approval flow
Step 11
Click Register
Defect Note: A message will be shown: Youre notified you will be sent the credentials via email and text. There is a bug currently
that says instead you have been sent credentials when youre waiting for credentials
Step 12
You are redirected to the login page with instructions on how to connect. This message as
customized says once approved you will be sent the credentials.
Step 13
Step 14
Approve the account.
From the admin-PCs Firefox, click the bookmark mail.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 55 of 70
Lab Exercise 4.6: Test the self registration with approval flow
Step 15
Login to squirrel mail using sponsor/ISEisC00L
Info only: The email says there is a guest approval request. This can be customized (changing logo, text, color, font with HTML).
You can also add a message that will link directly to the sponsor portal for easy access to the person approving the request.
Step 16
Sign-out of the webmail client, you will need to later login as another user.
In absence of a hyperlink to the sponsor portal, on the Firefox browser, click on the sponsor
shortcut to sponsor.demo.local
Step 18 Login to the sponsor portal as sponsor/ISEisC00L
Step 17
Step 19
Navigate to Pending
accounts
Step 20
Select the user and Click
Approve
Step 21
Enter the email address of the sponsor here as sponsor@demo.local
Info only: This is the only way to set the sponsors email address in the system. This email is used to receive a copy of the requests
when notifying a user of their credentials. It will be saved the first time its entered. The employ (person visiting) would enter their
email address here.
Step 22
Step 23
Step 24
Step 25
Step 26
Step 27
Step 28
Step 29
Get your credentials and login
Open up web browser to mail.demo.local and login as guest/ISEisC00L
Click on the email or SMS and take down the username and password
Return to the iPad VNC safari screen
Login with the credentials iseiscool/xxxxx
Click through AUP and success screens
On final page type in your original URL again
Navigate to Operation Authentications and look at the sessions that came through.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 56 of 70
Lab Exercise 4.7: Configure Settings for Sponsored Access
a. When you first come in MAB with SSID of guest is redirected to self registration portal
b. After login you are authorized on Guest Flow to Permit Access
Warning: If you see a message, Maximum Devices Reached, then please follow the steps below to clean up the iPad connection,
this was caused because the endpoint is already in the store after BYOD and you didnt delete it after you ran through the hotspot.
Step 30
Now clean up your endpoint and connection
a. Close the tab on the browser
b. Right click on the screen
c. Go to settings Wi-Fi
d. Forget the guest network
e. Disable Wi-Fi
f. Navigate to Admin Identity Management Identities Endpoints and delete the
iPad, you can delete anything in the list as there should only be your iPad connected
g. Remove the wireless session from the controller Monitor Clients
Note: If you ran through the cleanup after getting the Maximum device limit reached then you can do the following to try it again.
1. Enable WIFI
2. Open Safari and try to get to cnn.com
3. Enter the necessary credentials to login again
You have now completed setup of Self-registration with sponsor approval flow
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 57 of 70
Lab Exercise 4.7: Configure Settings for Sponsored Access
Lab Exercise 4.7: Configure Settings for
Sponsored Access
Exercise Description
In this Exercise you will go through the steps needed to setup a portal to manage accounts as a
Sponsor for Guests and a portal for these guests to access the network
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Configure additional Guest Settings
Setup Sponsored Guest Portal
Work with guest types
Update Sponsor Group settings
Configure the default sponsor portal
Configure additional Guest Settings
Step 1 Using Firefox, Login to ISE @ https://ise-1.demo.local/admin/ (or use bookmark) with username
admin and password ISEisC00L
Step 2 Navigate to Guest Access Settings
Step 3 Setup some custom fields to be used for your contractors that Sponsors can use when
creating an account:
a. Expand Custom Fields
b. Enter the following information per table clicking Add after each entry:
Custom Field Name Data type Tip text
Badge #
Number
Enter Badge #
Manager
String
Enter Manager
c.
Dont forget to Click Save.
Step 4 Setup a Guest SSID variable used for information purposes when notifying guests on what
network they should be connecting to
a. Expand Guest Locations and SSIDs
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 58 of 70
Lab Exercise 4.7: Configure Settings for Sponsored Access
b.
Under Guest SSIDs add in ##-guest where ## is your pod #.
Example: pod2 would be entered as 02-guest
c.
Dont forget to Click Save.
Setup Sponsored Guest Portal
Step 5 Navigate to Guest Access Configure Guest Portals
Step 6 Edit the Sponsored Guest portal (default)
Step 7 Under Portal Settings
Employees using this portal as guests inherit login options from: We will use the
default, Contractor
Step 8 Collapse all setting areas under you get to Post-Login Banner page
Step 9 Under Post-login banner page settings uncheck Include a Post-Login Banner page.
Notice how the flow chart changed on the right
Note: This will remove one of the pages that the user is required to click through, it could be used to post
coupons, advertisements, announcements, etc so that there is a screen available before redirecting to
an Original URL or static page, otherwise this can be done on the success page
Step 10 Click Save at the top of the page
Note: There really isnt much to a Sponsored Guest portal, thats it, with a tweak to make the flow shorter. You can
customize this portal just like any other Guest Portal with same customization and branding.
Work with Guest Types
Step 11 Navigate to Guest Access Configure Guest Types
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 59 of 70
Lab Exercise 4.7: Configure Settings for Sponsored Access
Note:
Guest Types are used with the credentialed guest portals such as Self-Registration and Sponsored. Under
self-registration with sponsor approval we used the default Contractor type that allows access for 90 days by
default. For Self-Registration without approval a nice default is Daily guest type as it only has 1-day access.
For sponsored we will look at the Contractor type options.
Step 12 Select Contractor and then Edit
Step 13 Select Custom Fields
a. Choose the upper left checkbox to select them all
b.
c.
Click OK
Set all of these to be required, we will use them later when creating an account and
see how they are reported
Step 14 Navigate to Login Options section and look at some of these settings, these are new or
options that have changed since release 1.2:
a. Max simultaneous logins This has been updated to allow a configurable option,
prior to ISE 1.3 the setting only allowed 1 or infinite amount of devices to be
connected with a single username
b. Store device information in endpoint identity group For hotspot this is
configured in the portal settings, for credentialed portals i ts set per GuestType, this
can also be used to separate your endpoint group purge policies, hotspot might
require acceptance of the AUP daily, self registered users could be required to login
1x a week, and sponsored guests (like contractors) might only ne ed to login and
accept an AUP every month. The basic purge policy for this endpoint is set right
below this setting.
c. Allow Guests to bypass the Guest Portal Prior to 1.3 this was known as
ActivatedGuest, when using this option the guest is not required t o be redirect to a
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 60 of 70
Lab Exercise 4.7: Configure Settings for Sponsored Access
login or AUP portal and can be used with more secure options (802.1X and VPN
access)
Step 15 Lastly lets look at Sponsor Groups. This is basic but a new way of working with groups, if
you are a sponsor and part of any of these groups then you can use this Guest Type
Step 16 At the top of the Contractor Guest Type Page, click Save and Close
Setup the default Sponsor Portal
Step 17 Navigate to Sponsor Portals Sponsor Portal (default) and click Edit
Note:
Up until this point you have been working with the Guest Portals. The Sponsor Portals are configurable the same
way. Settings and Customization are the same and allow for a consistent experience. Here to save time and since
you already went through basic customization we will setup only what is needed (and a few nice options) to make this
flow work
Step 18 Under portal settings lets look at a few options
a. Certificates (NEW FEATURE IN 1.3) each portal can have its own certificate, the
certificate is tied to specific combination of Allowed interface and https port,
product documentation has a paragraph explain this and some examples on
combinations
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 61 of 70
Lab Exercise 4.7: Configure Settings for Sponsored Access
b.
Note:
FQDN (ENHANCED IN 1.3) In ISE 1.2 you could put in the FQDN or hostname of
your sponsor portal so you can access with sponsor or sponsor.demo.local, in ISE
1.3 it has been enhanced to allow both options. You can also have multiple sponsor
portals access using different names for different business entities and customized
with its own branding. Example: city fire dept vs. city police dept
NOTE : In this lab you may try to access using just sponsor in the address bar but make sure your Firefox proxy
settings are setup with no proxy for sponsor if you would like to try it out. Otherwise the bookmark in firefox or going
to sponsor.demo.local will work fine.
c.
SSIDs available to sponsors: (NEW IN 1.3) This gives the sponsor the ability to
choose from a list of guest networks a user would connect to. This field is used in
notifications to those guests when notified via email/sms/print. Will show this used
later on. Choose the SSID you configured before, example 02-guest
Step 19 Click Save at the top of the page
Step 20 Now access Portal Page Customization
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 62 of 70
Lab Exercise 4.7: Configure Settings for Sponsored Access
Step 21 Collapse Portal Access
Step 22 Under Create Accounts, Click on Create Account for Known Guest
a. Click on settings above the preview pane
b. Uncheck the following options:
o
o
o
Note:
Company
Person Being Visited
Reason for Visit
The Custom Fields already associated with this guest type. Please do not
select again here.
Step 23 Collapse Create Accounts
Step 24 Under Notify Guests, click on Email Notification
a. Modify the template to include the SSID
b.
c.
Note:
variable
In the email introduction text editor insert text on the second line:
Welcome to the ISE training lab, the wireless network you will connect to is:
$ui_ssid$
Click on insert variable SSID
The variable icon X could be blocked by the preview pane if your browser screen is not wide enough.
Step 25 Click on SMS notification
a. Put in the following message: Please connect to the network: $ui_ssid$
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 63 of 70
Lab Exercise 4.8: Test Sponsored Guest Flow
Step 26 At the top of the page, Click Save
You have now completed setup of the Sponsored Guest Flow.
Lab Exercise 4.8: Test Sponsored Guest Flow
Exercise Description
In this Exercise you will go through the Sponsored Guest Flow first as an administrator creating
an account and then as a guest using those credentials to access the network.
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Preview the Managed Accounts option
Create a Known Guest Account using the Sponsor Portal
Receive customized notifications via email and SMS
Preview the Managed Accounts Option
Step 1 Navigate to Guest Access Manage Accounts
Step 2 At the top of the page click on Managed Accounts
The managed account option is a quick easy way to see all the accounts and perform
Sponsor Actions. The admin account is auto-authenticated and not part of any Sponsor
Group. It has permissions to do everything and see everything, accept if the guest changes
their password they wont be able to see it (just like any other sponsor). If the Sponsor
Portal Session terminates for any reason, the admin will have to go back to the Admin UI to
get back in or login with a valid Sponsor Account. Their admin creds will not get them back
in unless it is part of a sponsor group. This was just a preview and we will be using the
sponsor portal to do our work.
Create a Known Account using the Sponsor Portal
Step 3 Click on the Firefox bookmark to access the sponsor portal, here you are using the FQDN to
access this portal
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 64 of 70
Lab Exercise 4.8: Test Sponsored Guest Flow
Step 4 Login as sponsor / ISEisC00L
Step 5 Create a Known Account using the info from the table below
Attribute
First Name &
Last Name
Value
Your first and last
name
Email address
guest@demo.local
Phone number
Description
Please enter your first and last name
Mandatory: To receive email notification of
credentials, guest@demo.local
Mandatory: Enter your phone number with
country code, e.g. US is 1. If you dont want to
receive a text then enter a bogus number,
12025550133
12025550133
Badge #
Manager
Group tag
A badge number like:
123
Enter a manager
name: Mickey Mouse
EBC
Mandatory: This is to show using custom fields,
will be also showcased later using Guest Reporting
Mandatory: This is to show using custom fields,
will be also showcased later using Guest Reporting
Mandatory: This is for a sponsor to group guest
accounts for a specific function. Lets say the EBC
(Executive Briefing Center) at Cisco tags with EBC,
this way they can later sort on EBC Guests for
reporting purposes
Step 6 Click Create
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 65 of 70
Lab Exercise 4.8: Test Sponsored Guest Flow
Step 7 At the bottom of the Account Information screen, click notify
Step 8 Select both SMS and Email options (optionally you can copy yourself as the sponsor using
Copy ME checkbox)
Step 9 Enter the email address of the sponsor, sponsor@demo.local
Note:
This is the ONLY way a sponsor can add or change their email address to receive notifications for sponsor approval
or to be copied on a guests credentials when being created
Step 10 Click OK to send the notifications
Step 11 After the account is created and the user notified you can search on the group tag, Type EBC in
the search window
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 66 of 70
Lab Exercise 4.8: Test Sponsored Guest Flow
Receive customized notifications via email and SMS
Step 12 Check out the notifications you received
a.
SMS receipt: If you put in your cell phone number you should see a text with all the info
(including the SSID to connect to)
b.
Email receipt:
i. In Firefox open a new browser tab and click on the mail bookmark
ii. Login as guest / ISEisC00L
iii. Notice the customized test also shown here for the SSID variable
Note:
We wont be logging into the portal you created, as you are familiar with how this works after using the Self
Registration Portal Flow. The only difference with this flow is that youre using credentials created by a Sponsor. This
lab was to show you the needed pieces to get this particular flow configured and working.
You have now completed test of the Sponsored Guest Flow.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 67 of 70
Lab Exercise 4.9: Work with Guest Reporting
Lab Exercise 4.9: Work with Guest Reporting
Exercise Description
In this Exercise you will go through the new Guest Reports available. ISE 1.3 introduces fixes and
new reports to cover all the needed options for guest reporting including custom fields and guest
activity reporting.
Exercise Objective
In this exercise, your goal is to complete the following tasks:
Familiarize ISE 1.3 Guest reports.
Step 1 Navigate to Operations Reports
Step 2 Expand Guest Access Reports
There are several options for reports, click through each of them to understand what they are used for
and run the report to see the results if you like:
AUP Acceptance Status shows you information on what devices and/or users accepted AUPs
on what portals, this is an AUP for all guest portals (including Sponsor)
Sponsor Login and Audit shows sponsor activity such as logins and anything the added or
modified for guest accounts
Step 3 Click on Sponsor Login and Audit
Lets modify the columns seen so that we can work with the Optional
Data Field:
Step 4 Setup per the screenshot below:
a.
Unchecking MAC & IP Address, Operation
b.
Checking Optional Data
c.
Once complete, click Close
d.
Now click on the optional data and see it expanded in a larger box
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 68 of 70
Lab Exercise 4.9: Work with Guest Reporting
e.
Next try setting up a filter on this information:
i. Click Filters
ii. Select Optional Data
iii. Click OK
iv. Type in Mickey Mouse to find all
guests (contractors) with that hiring
manager.
v. Click Run
f.
I messed with the account a few times so there are multiple entries shown in my
example:
My Devices Login and Audit for BYOD devices shows user activity in the My Devices
portal
Master Guest Report - The Master Guest report combines data from various Guest Access
reports into a single view enabling you to export data from different reporting sources. This
report collects all guest activity and provides details about the web sites that guest users visit.
In this setup we dont track what sites the user is going to however here is a sample. There
are requirements for the firewall to send syslog information to ISE M&T node for inclusion in
this report, please refer to the product documentation for more information.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 69 of 70
Lab Exercise 4.9: Work with Guest Reporting
Guest Accounting - The Guest Accounting report is a subset of the RADIUS Accounting
report. All users assigned to Guest identity groups appear in this report
End of Exercise: You have successfully completed this exercise.
End of Lab: Congratulations! You have successfully completed the lab. Please let your
proctor know you finished and provide any feedback to help improve the lab experience.
ISE_1.3_PVT_Lab_Guide_2014-11-14.docx
11/17/2014 10:17:00 AM PST
Page 70 of 70
Das könnte Ihnen auch gefallen
- SCCM Short Notes PDFDokument29 SeitenSCCM Short Notes PDFJunaid Irfan100% (2)
- Ise Lab Guide For 9-11th WorkshopDokument237 SeitenIse Lab Guide For 9-11th WorkshopKamalNoch keine Bewertungen
- ISE Pre ATP Lab Guide CombinedDokument407 SeitenISE Pre ATP Lab Guide CombinedMajnu SmNoch keine Bewertungen
- Lab Guide ISE 1 2 UpdateDokument87 SeitenLab Guide ISE 1 2 Updatejuliushasan250% (2)
- Wireless LabDokument38 SeitenWireless Labseema gopalanNoch keine Bewertungen
- Cisco DNA Starter KitDokument14 SeitenCisco DNA Starter KitElvis de LeónNoch keine Bewertungen
- Multi-Domain-SDA-ACI-Lab GuideDokument41 SeitenMulti-Domain-SDA-ACI-Lab Guidesantoshkumar salawadgiNoch keine Bewertungen
- 7 Lab Guide Wireless Controller 8 1 FeaturesDokument65 Seiten7 Lab Guide Wireless Controller 8 1 Featuresalireza10230% (1)
- Add Certificates To Cisco Sd-Wan Lab (Version 18.4.4) : 1) VmanageDokument21 SeitenAdd Certificates To Cisco Sd-Wan Lab (Version 18.4.4) : 1) VmanageNarender GargNoch keine Bewertungen
- Netbackup 8.0 Blueprint CatalogDokument58 SeitenNetbackup 8.0 Blueprint Catalogalireza1023Noch keine Bewertungen
- Active Directory Migration ChecklistDokument5 SeitenActive Directory Migration ChecklistChinni SNoch keine Bewertungen
- Lab Guide Ise 1 2 Byod MDMDokument55 SeitenLab Guide Ise 1 2 Byod MDMjuliushasan2100% (2)
- Lab Guide ISE 1 2 ProfilingDokument39 SeitenLab Guide ISE 1 2 Profilingjuliushasan2Noch keine Bewertungen
- Ts Sgfw-Asa Lab Guide 2013-09-13Dokument42 SeitenTs Sgfw-Asa Lab Guide 2013-09-13juanibanez10Noch keine Bewertungen
- ISE Lab For Guest ServicesDokument38 SeitenISE Lab For Guest Serviceszohebsarwar82Noch keine Bewertungen
- Iser Lab For BYODDokument25 SeitenIser Lab For BYODzohebsarwar82Noch keine Bewertungen
- Cisco Video Solution Lab Guide PDFDokument52 SeitenCisco Video Solution Lab Guide PDFRoberto Rios Mendez0% (1)
- Lab 7: 802.1X: Wireless NetworksDokument13 SeitenLab 7: 802.1X: Wireless NetworksJosel ArevaloNoch keine Bewertungen
- ISE 1.3 GuideDokument54 SeitenISE 1.3 GuideSunny JamNoch keine Bewertungen
- Firepower NGFW Labpdf PDFDokument119 SeitenFirepower NGFW Labpdf PDFvelramsenNoch keine Bewertungen
- Firewall 7.2 Basic Lab v3.2 220729-FinalDokument118 SeitenFirewall 7.2 Basic Lab v3.2 220729-FinalEddy StoicaNoch keine Bewertungen
- Ise Catalyst SwitchingDokument19 SeitenIse Catalyst SwitchingbakacpasaNoch keine Bewertungen
- SECURE10LGDokument150 SeitenSECURE10LGAzzafirNoch keine Bewertungen
- Fast Lane Ise FL SISE30 LG308Dokument333 SeitenFast Lane Ise FL SISE30 LG308Chang ChenNoch keine Bewertungen
- D2 T1 S5 ACI Multisite TroubleshootingDokument54 SeitenD2 T1 S5 ACI Multisite TroubleshootingTariro Tariro TariroNoch keine Bewertungen
- Lab05 - Configuring ASA Basic Settings and Firewall Using CLIDokument26 SeitenLab05 - Configuring ASA Basic Settings and Firewall Using CLIAdrián ChóezNoch keine Bewertungen
- BRKEWN-2670 Best Practices For Configuring Cisco Wireless LAN Controllers PDFDokument97 SeitenBRKEWN-2670 Best Practices For Configuring Cisco Wireless LAN Controllers PDFNeoNoch keine Bewertungen
- Step by Step Guide To Build A Cisco Wireless Infrastructure Using Cisco WLC 5500Dokument21 SeitenStep by Step Guide To Build A Cisco Wireless Infrastructure Using Cisco WLC 5500Renzo Mejia VeliNoch keine Bewertungen
- Identity Based Networking Services (IBNS) 2.0 - New Style 802.1X and MoreDokument68 SeitenIdentity Based Networking Services (IBNS) 2.0 - New Style 802.1X and MoreWilliam NogueiraNoch keine Bewertungen
- Lab Guide Training v2.0 PDFDokument36 SeitenLab Guide Training v2.0 PDFabijith13Noch keine Bewertungen
- Lab2 Cciesecv4 QuestionsetDokument47 SeitenLab2 Cciesecv4 QuestionsetPhạm Quốc BảoNoch keine Bewertungen
- CCIE SP v3.0 Sample Lab Part - 1 of 7Dokument37 SeitenCCIE SP v3.0 Sample Lab Part - 1 of 7Sơn ĐàoNoch keine Bewertungen
- Quick Configs - CCIE Notes PDFDokument215 SeitenQuick Configs - CCIE Notes PDFNoah AzpiriNoch keine Bewertungen
- Cisco TAC Entry Training - 12 - Open Shortest Path First (OSPF) PDFDokument54 SeitenCisco TAC Entry Training - 12 - Open Shortest Path First (OSPF) PDFFerasHamdanNoch keine Bewertungen
- Deploying+Cisco+SD Access+ (ENSDA) + +4Dokument76 SeitenDeploying+Cisco+SD Access+ (ENSDA) + +4Hamed GhabiNoch keine Bewertungen
- Khawar Butt CCIE Security v3 0Dokument191 SeitenKhawar Butt CCIE Security v3 0kamleg100% (1)
- Network Maintenance Tasks and Best Practices: CCNP TSHOOT: Maintaining and Troubleshooting IP NetworksDokument35 SeitenNetwork Maintenance Tasks and Best Practices: CCNP TSHOOT: Maintaining and Troubleshooting IP NetworksAustin SpillerNoch keine Bewertungen
- Ise Wired Access Depl Guide-V01Dokument113 SeitenIse Wired Access Depl Guide-V01Gustavo ScNoch keine Bewertungen
- Cisco SDWAN Solution OverviewDokument68 SeitenCisco SDWAN Solution Overviewshashwat tiwariNoch keine Bewertungen
- Catalyst 9k Troubleshooting - DGTL BRKARC 3190Dokument77 SeitenCatalyst 9k Troubleshooting - DGTL BRKARC 3190Test TestNoch keine Bewertungen
- Cisco Ios DMVPN: February 2008Dokument46 SeitenCisco Ios DMVPN: February 2008hadi_khan100% (1)
- Enterprise Networks TAC Workshop Day 1 SD-WAN Troubleshooting WorkbookDokument29 SeitenEnterprise Networks TAC Workshop Day 1 SD-WAN Troubleshooting Workbookg100% (1)
- Configure OSPF and EIGRP for ACME HQ and NY OfficeDokument33 SeitenConfigure OSPF and EIGRP for ACME HQ and NY Officeblck bxNoch keine Bewertungen
- Chapter 6 Lab 6-2, Using The AS - PATH Attribute: TopologyDokument8 SeitenChapter 6 Lab 6-2, Using The AS - PATH Attribute: TopologyMeliko ianNoch keine Bewertungen
- BRKRST 2096Dokument137 SeitenBRKRST 2096Binh NguyenNoch keine Bewertungen
- Advanced ISE Labs PDFDokument66 SeitenAdvanced ISE Labs PDFcoolboyasif100% (1)
- F5 BIG-IP Local Traffic Manager Service Insertion With Cisco Application Centric InfrastructureDokument56 SeitenF5 BIG-IP Local Traffic Manager Service Insertion With Cisco Application Centric InfrastructureSurath KumarNoch keine Bewertungen
- CCSE Class SlidesDokument313 SeitenCCSE Class SlidesphamvanhaNoch keine Bewertungen
- Brkaci 2102Dokument121 SeitenBrkaci 2102ivnnpcNoch keine Bewertungen
- Viptela Control Plane Setup PDFDokument29 SeitenViptela Control Plane Setup PDFFederacion Hip Hop DominicanaNoch keine Bewertungen
- Infoblox 1050 1550 1552 UserGuideDokument54 SeitenInfoblox 1050 1550 1552 UserGuidekranston100% (1)
- 9.3.1.1 Packet Tracer - Configuring ASA Basic Settings and Firewall Using CLIDokument7 Seiten9.3.1.1 Packet Tracer - Configuring ASA Basic Settings and Firewall Using CLIJunNoch keine Bewertungen
- LABDCT 2001 (Guide) Nexus.7000Dokument44 SeitenLABDCT 2001 (Guide) Nexus.7000kds20850Noch keine Bewertungen
- Troubleshooting Campus Networks: Practical Analysis of Cisco and LAN ProtocolsVon EverandTroubleshooting Campus Networks: Practical Analysis of Cisco and LAN ProtocolsBewertung: 4 von 5 Sternen4/5 (1)
- Cisco Certified Security Professional A Complete Guide - 2020 EditionVon EverandCisco Certified Security Professional A Complete Guide - 2020 EditionNoch keine Bewertungen
- Cisco Unified Communications Manager 8: Expert Administration CookbookVon EverandCisco Unified Communications Manager 8: Expert Administration CookbookNoch keine Bewertungen
- Cisco Certified Design Professional A Complete Guide - 2020 EditionVon EverandCisco Certified Design Professional A Complete Guide - 2020 EditionNoch keine Bewertungen
- Demoting A Domain Controller Server 2012 Step by StepDokument10 SeitenDemoting A Domain Controller Server 2012 Step by Stepalireza1023Noch keine Bewertungen
- Veritas Netbackup 8.0 Blueprint AIRDokument40 SeitenVeritas Netbackup 8.0 Blueprint AIRalireza1023Noch keine Bewertungen
- bd58610b-f919-496c-b41c-935ce24078feDokument21 Seitenbd58610b-f919-496c-b41c-935ce24078fealireza1023Noch keine Bewertungen
- Symantec Netbackup SOWDokument10 SeitenSymantec Netbackup SOWalireza1023Noch keine Bewertungen
- Veritas Netbackup 8.0 Blueprint Active DirectoryDokument31 SeitenVeritas Netbackup 8.0 Blueprint Active Directoryalireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint ExchangeDokument36 SeitenNetbackup 8.0 Blueprint Exchangealireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint OpsCenterDokument59 SeitenNetbackup 8.0 Blueprint OpsCenteralireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint Replication DirectorDokument74 SeitenNetbackup 8.0 Blueprint Replication Directoralireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint OracleDokument100 SeitenNetbackup 8.0 Blueprint Oraclealireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint Enterprise VaultDokument39 SeitenNetbackup 8.0 Blueprint Enterprise Vaultalireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint IRVDokument54 SeitenNetbackup 8.0 Blueprint IRValireza1023Noch keine Bewertungen
- Veritas Netbackup 8.0 Blueprint Accelerator For NDMPDokument27 SeitenVeritas Netbackup 8.0 Blueprint Accelerator For NDMPalireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint NDMPDokument42 SeitenNetbackup 8.0 Blueprint NDMPalireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint Hyper-VDokument51 SeitenNetbackup 8.0 Blueprint Hyper-Valireza1023Noch keine Bewertungen
- Netbackup 8.0 Blueprint Copilot OracleDokument49 SeitenNetbackup 8.0 Blueprint Copilot Oraclealireza1023Noch keine Bewertungen
- 01 Gartner - Magic Quad - Endpoint Protection Platforms 1-2018Dokument40 Seiten01 Gartner - Magic Quad - Endpoint Protection Platforms 1-2018Alejandro SanchezNoch keine Bewertungen
- Veritas Netbackup 8.0 Blueprint BMRDokument45 SeitenVeritas Netbackup 8.0 Blueprint BMRalireza1023Noch keine Bewertungen
- FOS Password Recovery NotesDokument24 SeitenFOS Password Recovery NotesSudheer ChNoch keine Bewertungen
- Vrealize Operations Service Discovery Management Pack - 2.0 - 2Dokument32 SeitenVrealize Operations Service Discovery Management Pack - 2.0 - 2alireza1023Noch keine Bewertungen
- PDFDokument121 SeitenPDFKarma_2006Noch keine Bewertungen
- Veritas Netbackup 8.0 Blueprint AcceleratorDokument29 SeitenVeritas Netbackup 8.0 Blueprint Acceleratoralireza1023Noch keine Bewertungen
- Us Meetings GSG 6.12Dokument4 SeitenUs Meetings GSG 6.12anghockbinNoch keine Bewertungen
- Cisco VCS Release Note X8 7 3Dokument13 SeitenCisco VCS Release Note X8 7 3alireza1023Noch keine Bewertungen
- Firewall Security Manager 6.6.8 Release Notes DraftDokument3 SeitenFirewall Security Manager 6.6.8 Release Notes Draftalireza1023Noch keine Bewertungen
- Netwrix Auditor Installation Configuration GuideDokument182 SeitenNetwrix Auditor Installation Configuration GuideMushtaqNoch keine Bewertungen
- Zoom Tutorial PP TDokument25 SeitenZoom Tutorial PP TShreyanRayNoch keine Bewertungen
- Top 10 Help DeskDokument4 SeitenTop 10 Help Deskalireza1023Noch keine Bewertungen
- System Center 2012 R2 SlidesDokument48 SeitenSystem Center 2012 R2 Slidesalireza1023Noch keine Bewertungen
- System Center 2016 Whats New WhitepaperDokument12 SeitenSystem Center 2016 Whats New Whitepaperalireza1023Noch keine Bewertungen
- AD FS Knowledge Transfer-V2.0Dokument56 SeitenAD FS Knowledge Transfer-V2.0cherifNoch keine Bewertungen
- Tesda Css Ncii Reviewer Coc1 Coc2 and Coc3Dokument2 SeitenTesda Css Ncii Reviewer Coc1 Coc2 and Coc3Be Nj65% (17)
- ISE TACACS+ Configuration Guide For Cisco NX-OS Based Network DevicesDokument16 SeitenISE TACACS+ Configuration Guide For Cisco NX-OS Based Network DevicesShirley Diossana GarayNoch keine Bewertungen
- FSMO Roles GuideDokument6 SeitenFSMO Roles GuideArjan Op 't HofNoch keine Bewertungen
- 70 533Dokument88 Seiten70 533WiNgeneAbr100% (1)
- ONTAP 90 Network Management Guide PDFDokument155 SeitenONTAP 90 Network Management Guide PDFJoy MukherjeeNoch keine Bewertungen
- ESRS IP Release Notes 2.18Dokument18 SeitenESRS IP Release Notes 2.18bolilla2Noch keine Bewertungen
- Andrew Wytwyckyj December 2008 CVDokument2 SeitenAndrew Wytwyckyj December 2008 CVAndrew Wytwyckyj100% (2)
- Leverage Multi Factor Authentication Server On Your PremisesDokument111 SeitenLeverage Multi Factor Authentication Server On Your PremisesanditzaskcNoch keine Bewertungen
- Exam TopicsDokument56 SeitenExam Topicstestertmu testerNoch keine Bewertungen
- 6426B: Configuring and Troubleshooting Identity and Access Solutions With Windows Server 2008 Active DirectoryDokument36 Seiten6426B: Configuring and Troubleshooting Identity and Access Solutions With Windows Server 2008 Active DirectorySmRodolfo PlUrrutiaNoch keine Bewertungen
- Fred Conover - PDF RésuméDokument2 SeitenFred Conover - PDF RésuméfredconoverNoch keine Bewertungen
- Sophoslabs Ransomware Behavior ReportDokument29 SeitenSophoslabs Ransomware Behavior ReportSaurabh SharmaNoch keine Bewertungen
- Troubleshooting Kerberos ErrorsDokument64 SeitenTroubleshooting Kerberos ErrorsShaziNoch keine Bewertungen
- FarCry CMS: Product FeaturesDokument16 SeitenFarCry CMS: Product FeaturesfullasagoogNoch keine Bewertungen
- ISE-SlidesDokument26 SeitenISE-SlidesElaouni AbdessamadNoch keine Bewertungen
- Microsoft - SC-300.v2021-09-20.q37: Leave A ReplyDokument32 SeitenMicrosoft - SC-300.v2021-09-20.q37: Leave A ReplyJavier Alonso SanzNoch keine Bewertungen
- Windows System Administrator Sample Resume PDFDokument3 SeitenWindows System Administrator Sample Resume PDFRavi Kumar Patnana0% (1)
- ODC Servers Requirement V 0.3 UpdatedDokument10 SeitenODC Servers Requirement V 0.3 Updatedakmalyezdani512Noch keine Bewertungen
- MongoDB Security Architecture WP PDFDokument18 SeitenMongoDB Security Architecture WP PDFjamesNoch keine Bewertungen
- h17240 WP Isilon Onefs Nfs Design Considerations BP PDFDokument38 Seitenh17240 WP Isilon Onefs Nfs Design Considerations BP PDFyazidNoch keine Bewertungen
- Troubleshooting PDFDokument991 SeitenTroubleshooting PDFMark BrownNoch keine Bewertungen
- User Attributes - Inside Active DirectoryDokument3 SeitenUser Attributes - Inside Active DirectorykgrchandranNoch keine Bewertungen
- Kyocera P3055dn Network AuthenticationDokument11 SeitenKyocera P3055dn Network Authenticationzaheer100% (1)
- 2279B Mod11lb PDFDokument14 Seiten2279B Mod11lb PDFJosé MarquesNoch keine Bewertungen
- Navneet ResumeDokument4 SeitenNavneet Resumenavneet.singh.gambhirNoch keine Bewertungen
- Pricing OverviewDokument126 SeitenPricing OverviewClaudio PazNoch keine Bewertungen
- IT program rubric for outcomesDokument7 SeitenIT program rubric for outcomesNoel IV T. BorromeoNoch keine Bewertungen