Beruflich Dokumente
Kultur Dokumente
SSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon Whitepaper
Hochgeladen von
GigamonOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
SSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon Whitepaper
Hochgeladen von
GigamonCopyright:
Verfügbare Formate
Whitepaper
SSL Decryption: Uncovering The New Infrastructure
Blind Spot
Since the mid-90s, users transacting on the internet have been
assured of security by the lock icon displayed on their browser
and URLs that begin with https. These indicate secure websites
that support the Secure Sockets Layer (SSL) internet protocol.
These SSL sessions protect sensitive information such as credit
card numbers and login credentials for e-mail, e-commerce,
voice-over-IP (VoIP), online banking, remote health, and other
critical services, from unauthorized or malicious parties.
Yet, the security stakes have been raised multiple fold with more
organizations adopting cloud computing. In a Cloud Security
Alliance survey1, 73% of respondents indicated that security
concerns held back cloud projects.
SSL Vulnerabilities
But high-profile vulnerabilities, such as the Heartbleed bug, which
exposes web server memory protected by the OpenSSL software
to theft, have stoked concerns and fuelled threats SSL was
supposed to curb.
Decisions concerning security of data in the cloud have also
shifted from the IT room to the boardroom for 61% of companies.
Indeed, top executives have seen the impact of high-profile data
breaches on not only company reputation and balance sheets but
also their jobs.
Encryption Primer
To ensure security in the cloud, SSL encrypts data in connections
between a web server and a browser. When one connects to
a secure website via a browser, data sent or received from the
remote web server is encrypted by a public key infrastructure (PKI).
In the PKI, a Certificate Authority (CA) issues a root certificate
an unsigned public key certificate or a signed certificate. The web
server has the public certificate or a public key. It also has sole
access to a private key.
Simply put, the public key is used to encrypt data while only the
private key is used to decrypt data. The public keys are visible at
the start of the transaction, but the administrator controls access
to the private keys.
Within SSL secure connections, a web browser uses root certificates
to verify identities and establish trust. The ITU-T X.509 standard
certificate, for example, includes a digital signature from a CA.
The Heartbleed bug, which has been present since 2011, is a
serious threat because OpenSSL is used by some 20% of the
worlds web servers. Such vulnerabilities enable cyber criminals
to gain access to keys and certificates and bypass SSL protection
based on encryption and signatures in the X.509 certificates.
Moreover, another trend spells trouble ahead. According to an
independent study by NSS Labs2, 25% to 35% of enterprise
traffic is currently being carried over encrypted connections,
of which a growing proportion are within SSL. That traffic segment
continues to grow every month. And hackers and cyber criminals
are increasingly using these SSL sessions to dodge network
security defenses.
These threat actors exploits stem from inline and out-of-band
security tools either lacking the ability to see inside the encrypted
sessions or end up with performance degradation of up to 80%
from processing SSL traffic.
Gaps in Tool Capabilities
Although inline devices such as application delivery controllers
and firewalls integrate SSL support, out-of-band monitoring
and security tools often do not have the ability to access
decrypted traffic.
1
Coles, Cameron. (2015, Jan. 12) CSA Survey: Security of Cloud Data Now a Board-Level Concern. Cloud Security Alliance Industry Blog. https://blog.cloudsecurityalliance.org/2015/01/12/csa-survey-securitycloud-data-now-board-level-concern/
2
Pirc, John W. (2013) Analyst Brief: SSL Performance Problems. NSS Labs. https://www.nsslabs.com/sites/default/files/public-report/files/SSL%20Performance%20Problems.pdf
2015 Gigamon. All rights reserved.
Whitepaper: SSL Decryption: Uncovering The New Infrastructure Blind Spot
But even inline technologies such as SSL proxies and application
load balancers that provide SSL decryption lack the scalability to
handle traffic from multiple TAPs across the network or to filter
and replicate decrypted traffic to multiple monitoring tools. With
limited extensibility, increasing SSL throughput often requires
hardware upgrades. In addition, these tools also lack visibility
functionality or traffic intelligence for non-encrypted traffic.
The situation will worsen as certificate authorities implement
longer keys such as 256-bit SSL encryption based on a 2048-bit
key which will increase the compute load for SSL decryption.
Furthermore, not knowing which applications are running over the
network hampers the ability to monitor application performance
and network usage patterns.
When SSL traffic is allowed to flow uninspected, this creates a
potential security loophole. Hence, analysts at Gartner believe
that more than half of the network attacks targeting enterprises
will use encrypted traffic to bypass controls in 2017, up from less
than 5% today.3
Harm will come from hackers and nefarious actors hiding threats,
such as the Zeus botnet, in SSL sessions that have been largely
considered safe.
This makes uncovering attacks hiding in threat sources like
SSL sessions an essential component of enterprise security.
Organizations must develop visibility into these sessions so
network security and analytics tools can monitor encrypted traffic
and detect threats hidden within them.
Why SSL Decryption
Organizations should analyze their architecture and environment
to determine the security risks due to uninspected encrypted
network traffic. As more of enterprise network traffic is
encrypted, organizations have to identify and seal gaps in
defense-in-depth effectiveness.
Without a traffic decryption plan, organizations will not be
able to see and stop malware activity that comes through
encrypted connections.
To alleviate critical blind spots created by encrypted traffic flowing
through the IT infrastructure, organizations need innovative
visibility solutions with the capability to decrypt SSL sessions at
high performance.
A traffic decryption strategy can bolster protection of endpoints
and DMZ servers from threats in outbound and inbound traffic.
SSL decryption can be applied to:
Malware detection It prevents malware from exploiting a host
using SSL transactions
Data loss prevention (DLP) It prevents confidential data
and files from being encrypted and leaked via malware or a
malicious insider using SSL connections
Application performance monitoring (APM) It enables proper
monitoring of data and allows business applications to use SSL
for authentication
Cloud services monitoring It helps to differentiate and
monitor secure services running in the cloud, including
web applications
Two types of traffic have to be decrypted so security tools can
examine them:
Inbound traffic from an external or remote client computer on
the internet to an internal server
Outbound traffic from an internal client computer to an external
server on the internet
Decrypting Inbound Traffic
When a client device accesses a web server in a data center via the
internet, an end-to-end, SSL-encrypted connection is established
between the devices browser and the web server.
If this link is invisible to network security tools deployed in the data
center, the traffic has to be decrypted using two steps:
1. Place a copy of the web servers private key on a decryptioncapable device
2. Store a copy of the data in the decryption-capable device
End-to-end data encryption must be maintained to prevent data theft
or leakage.
Decrypting Outbound Traffic
Decrypting outbound traffic requires a different approach. When
the server sends its certificate to a browser, the browser decides
whether or not it trusts the certificate based on a list of trusted CAs
loaded in the device.
DHoinne, Jeremy and Hils, Adam. Security Leaders Must Address Threats From Rising SSL Traffic. Gartner report, 9 Dec 2013.
2015 Gigamon. All rights reserved.
Whitepaper: SSL Decryption: Uncovering The New Infrastructure Blind Spot
However, cyber criminals can exploit decryption of outbound
traffic by setting up a decryption device as a CA with the ability to
sign certificates and configuring the browser to trust certificates
from the decryption device.
features are built into hardware to decrypt SSL sessions at high
performance. This serves the demand for deeper insight into
the critical blind spots to help expose hidden security threats or
network performance issues.
With the decryption device placed inline between users and
the internet, it is ready to intercept any request from users who
browse to an encrypted website and pretend to be the web
server. At the other end, the decryption device establishes its
own connection to the actual web server and controls requests
between the user and the server.
The GigaSMART Difference
Protecting Data Confidentiality
Many organizations and countries are required to meet strict
regulations to protect data privacy. While SSL decryption is
critical for security and performance analysis, capabilities must be
in place to prevent misuse of decrypted data.
SSL decryption can stop outbound malware connections or
leakage of sensitive information. But privacy-related laws,
regulations, and employee issues can derail an outbound web
traffic decryption project.
At the workplace, organizations have to manage employees
expectations of privacy on the corporate network or help
employees understand the importance of SSL decryption in
protecting the business. At the same time, existing privacy
and network usage policy has to be reviewed and updated, if
necessary, to facilitate SSL decryption.
Privacy Concerns
The critical task is to ensure that sensitive user data contained in
SSL traffic remains secure. For example, decrypted packets can
be sliced to remove irrelevant or private payload data, or fields
within the payload can be masked. By doing so, the monitoring
and security tools do not store, read, or analyze private data.
This simplifies the auditing process for organizations challenged
to maintain user privacy and comply with rigorous regulatory
compliance imposed by PCI-DSS, HIPAA, SOX, and the GLB Act.
Security Compliance
To maintain security compliance in cloud environments, proper
handling of private encryption keys is just as vital as data
protection and encryption. Whenever a user accesses a cloud
service or application, the public and private keys are used and
put at risk.
These challenges have driven Gigamon to introduce the industrys
first and only visibility solution with integrated SSL support.
Gigamons innovative GigaSMART traffic intelligence application
2015 Gigamon. All rights reserved.
Unlike what other visibility solutions offer, the GigaSMART
application delivers SSL decryption as a common service to
connected security and performance management tools so the
tools can function at full performance.
The offloading of SSL decryption also eliminates the need to
have multiple decryption licenses for multiple tools. After all, a
security appliance with integrated SSL decryption, for example,
does not benefit other tools, such as application performance
monitoring. Gigamon can supply decrypted traffic to multiple
tools simultaneously, maximizing the overall efficiency, security,
and performance of the infrastructure. An associated benefit
of this approach is that the private keys can now be securely
uploaded to just the visibility infrastructure instead of sharing it
with multiple tools.
It also delivers to IT and security administrators the right level of
visibility into traffic, including SSL-encrypted segments that are at
the heart of todays cloud infrastructures.
GigaSMART decrypts the packets and sends the traffic to multiple
out-of-band tools, including intrusion detection (IDS), data loss
prevention, and application performance monitoring for analysis.
High-performance Engine
Hardware accelerators drive the GigaSMART modules highperformance compute engines when handling SSL traffic.
Another key advantage is that SSL decryption is not limited
to specific ingress ports or where the GigaSMART engine is
located. The out-of-band Gigamon Visibility Fabric can deliver the
decrypted traffic by GigaSMART from the production network to
the tools required to monitor and manage IT infrastructure.
Any traffic received on any network port of the Gigamon visibility
nodes can be decrypted and sent to any tool port in the cluster.
This is an important attribute because not every node in the
cluster needs to have the SSL decryption capability. It also avoids
the need to unnecessarily install SSL decryption appliances at
various points in the infrastructure, saving cost and bringing
efficiency. The cluster provides the necessary reach of the
visibility infrastructure and SSL decryption can then be selectively
applied to any traffic that enters the visibility infrastructure.
Whitepaper: SSL Decryption: Uncovering The New Infrastructure Blind Spot
More GigaSMART modules can be added to the cluster to scale
SSL decryption throughput up, allowing inspection to grow as SSL
processing needs increase.
Privacy Measures
After traffic within the SSL session is decrypted, other GigaSMART
applications are available to modify, manipulate, transform, and
transport traffic from the network to connected management,
monitoring, and security tools. A combination of these applications
can be applied to different traffic profiles to maximize security.
For example, SSL traffic can be decrypted and then masked so
confidential information like passwords, financial accounts, or
medical data can be hidden in compliance with SOX, HIPAA, PCI
and other regulations.
Security Compliance
The key capabilities of Gigamons holistic platform-based approach
are designed to harness SSL decryption to solve visibility challenges.
The Steps to SSL Decryption
Tap the network and connect it to Gigamons
Visibility Fabric.
Select which flows to monitor and the GigaSMART
engine will identify the exchange of public keys at the
start of the transaction.
The private keys, which have been uploaded by the
administrator, are encrypted and stored under tight
password and role-based access controls.
GigaSMART then uses the private and public keys to
decrypt the SSL traffic.
The clear packets can be sent directly to your
monitoring tools or additional Flow Mapping and
GigaSMART operations can be applied.
With access to bidirectional traffic, Gigamons Visibility Fabric
observes the exchange of public keys at the start of a transaction.
Once the administrator loads the private keys, they are securely
stored on the system. These private server keys are encrypted
and protected by role-based access controls.
That means Gigamon only allows keys to be uploaded, changed
or deleted by users designated by the administrator. The keys are
encrypted using a special password, which is distinct from the
generic system admin password.
3
2
Visibility Fabric
4
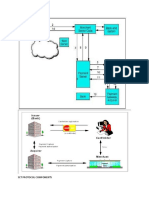
Steps to SSL Decryption and Active Visibility
Figure 1 shows the steps describing how SSL decryption is
carried out via GigaSMART technology:
In the final step, network managers can apply a combination of
GigaSMART operations or use Gigamons Flow Mapping technology
to finely filter and forward traffic to specific monitoring tools. The
latter is done through thousands of map rules or criteria based
on over 30 predefined Layer 2, Layer 3 and Layer 4 parameters
including IPv4/IPv6 addresses, application port numbers, VLAN IDs
and MAC addresses, as well as custom rules that match specific
bit sequences in the traffic streams. Additional filter criteria can be
set up based on user defined attributes or even based on content
inspection for specific patterns.
Leveraging GigaSMART traffic intelligence is also a key step
toward Gigamons Active Visibility for Multi-tiered Security
architecture. As part of the Gigamon Visibility Fabric, GigaSMART
technology extends the intelligence and value of the architecture
with expanded visibility; high-precision NetFlow-generated data
on traffic flows and usage patterns across systems; improved tool
performance; privacy protection; and easier regulatory compliance.
2015 Gigamon. All rights reserved.
The Steps to SSL Decryption
1. Tap the network and connect it to Gigamons
Figure
1: TheFabric.
steps to SSL decryption
Visibility
2. Select which flows to monitor and the
GigaSMART engine will identify the exchange
The architectures Fabric Manager centrally administers these
of public keys at the start of the transaction.
capabilities across the Visibility Fabric. Traffic bound for out-of-band
3. The private keys, which have been uploaded
monitoring
tools can benefit
from GigaSMART
by the administrator,
are encrypted
and storedintelligence
regardless
of where
it entered
the Visibility
Fabric.
under tight
password
and role-based
access
controls.
4. GigaSMART then uses the private and public
keys to decrypt the SSL traffic.
5. The clear packets can be sent directly to your
monitoring tools or additional Flow Mapping
and GigaSMART operations can be applied.
Whitepaper: SSL Decryption: Uncovering The New Infrastructure Blind Spot
REST API
Closed Loop Monitoring
Multi-tiered security
appliances
(inline or out-of-band)
GigaVUE-FM
NGFW
Core
switch
Spine
switch
Inline
Bypass
SSL
NetFlow
Decryption Generation
WAF
ANTI-MALWARE
Spine
switch
Visibility Fabric
Leaf
switch
IPS
Core
switch
Leaf
switch
VM
VM
GigaVUE-VM
HYPERVISOR
IDS
DLP
NETWORK FORENSICS
APT
Figure 2: Multi-tiered security supported by Gigamons Visibility Fabric architecture
Key Benefits for the Cloud
The growing adoption of cloud computing be it public, private,
or hybrid as an alternative deployment strategy for IT systems
disrupts traditional notions of data security.
Data center managers have typically secured the entire core
infrastructure and the perimeter. Cloud computing and mobility have
blurred that perimeter. Meanwhile, a dynamic cloud-based environment
calls for agile and efficient allocation of IT resources and investments.
For instance, security plans have to clearly distinguish between
sensitive and non-sensitive data and how to store and secure them.
But while cloud computing has radically changed the way IT
services are delivered and managed, the responsibility of securing
sensitive data and ensuring compliance to security regulations has
to remain with data owners.
In essence, the Gigamon Visibility Fabric, built on the GigaSMART
traffic intelligence engine and GigaVUE fabric nodes or servers,
delivers the very benefits that give data owners the visibility
and control to make sound security decisions while fulfilling
regulatory compliance.
Visibility into encrypted traffic facilitates malware detection,
intrusion detection, data loss prevention, and network forensics
while at the same time feeds traffic to application performance,
monitoring, and customer experience management tools.
Integrated SSL inspection in a multi-tiered security solution
exposes malware within SSL sessions, forwards traffic that
does not match known flows to GigaSMART for decryption,
and decrypts traffic from the cloud and/or remote sites.
2015 Gigamon. All rights reserved.
Improved tool performance from offloading SSL decryption
to the Visibility Fabric frees tool resources for packet analysis;
decryption has to be applied only once for all tools. This method
also increases secure management of private keys.
A wide array of GigaSMART applications enable IT organizations
to apply both Flow Mapping and SSL decryption; obscure
private data with packet slicing or masking; use Adaptive Packet
Filtering for L7-based packet forwarding; and more.
Summary
The changing threat landscape, amid growing volumes, velocity,
and variety of data and evolving cloud-based infrastructure, are
forcing organizations to rethink their approach to security.
SSL has become a vital technology for cloud-based services. It
has a strong track record for encrypting and authenticating data
online but it might not be the silver bullet for cloud security.
It severely limits visibility for both performance and security
monitoring. The risk around the growing security threat posed by
uninspected SSL sessions increases the urgency for inspecting
SSL traffic.
The ultimate objective is to build trusted cloud services and SSL
connections. By supplying clear, decrypted SSL traffic to multiple
tools, Gigamon provides immediate value and return on investment
in capital expenditure, licensing fees, and management costs.
Whitepaper: SSL Decryption: Uncovering The New Infrastructure Blind Spot
Coupled with the full capabilities of Flow Mapping and GigaSMART
traffic intelligence, the Gigamon Visibility Fabric allows enterprises
to be much more efficient in security management and to view and
monitor the traffic that really matters.
About the Visibility Fabric
The Gigamon Visibility Fabric is a distributed system of nodes
that provides pervasive visibility across physical, virtual, and
future SDN production networks. The fabric delivers traffic from
the production network to inline or out-of-band tools required to
monitor and manage IT infrastructure such as security, application
and network performance, and user experience monitoring tools.
A Visibility Fabric is very different from a traditional network.
The Visibility Fabric taps into the production network (be it SDN or
traditional) or connects to the SPAN/mirror ports of the network
switches (white box or otherwise) to receive a copy of the traffic
traversing the production network. That traffic is then forwarded
to the tools based on the type of traffic that is relevant to the
tools. There is a fundamental difference between how network
switches and Visibility Fabric nodes forward traffic. Traffic within
the Visibility Fabric is forwarded based on the content that is
relevant to the tools.
both physical and virtual environments without affecting the
performance or stability of the production network. Through
patented technologies, centralized management and
a portfolio of high availability and high density fabric nodes,
network traffic is intelligently delivered to management,
monitoring and security systems. Gigamon solutions have been
deployed globally across enterprise, data centers and service
providers, including over half of the Fortune 100 and many
government and federal agencies.
For more information about the Gigamon Unified Visibility Fabric
visit: www.gigamon.com
Traditional network switches are highly optimized for addressbased forwarding where traffic is forwarded based on address
information in the headers of the packets. Within the Visibility
Fabric, traffic is forwarded based on the content of the packets,
as well as based on correlated traffic flows that straddle multiple
packets. And furthermore, those traffic streams may need to
be replicated within the Visibility Fabric so as to deliver them to
multiple sets of tools.
That packet replication is also based on the content of the packet,
as well as based on correlated traffic streams, so as to ensure
that just the relevant traffic is delivered to the tools. This makes
the Visibility Fabric a highly specialized function that is very
unique and different from traditional network switches. As we
look to the future, this specialized capability of the Visibility Fabric
will make it an integral but distinct component in ensuring the
successful deployment of SDN solutions.
About Gigamon
Gigamon provides an intelligent Unified Visibility Fabric to enable
the management of increasingly complex networks. Gigamon
technology empowers infrastructure architects, managers and
operators with pervasive visibility and control of traffic across
2015 Gigamon. All rights reserved. Gigamon and the Gigamon logo are trademarks of Gigamon in the United States and/or other
countries. Gigamon trademarks can be found at www.gigamon.com/legal-trademarks. All other trademarks are the trademarks of
their respective owners. Gigamon reserves the right to change, modify, transfer, or otherwise revise this publication without notice.
3300 Olcott Street, Santa Clara, CA 95054 USA | +1 (408) 831-4000 | www.gigamon.com
3165-01 05/15
Das könnte Ihnen auch gefallen
- BlueCoat Decrypting SSLDokument15 SeitenBlueCoat Decrypting SSLRichardNoch keine Bewertungen
- E-Commerce Security Best PracticesDokument19 SeitenE-Commerce Security Best PracticesNess Wadia College of Coomerce PuneNoch keine Bewertungen
- Best Practices DecryptionDokument5 SeitenBest Practices DecryptionPartha DashNoch keine Bewertungen
- SSL LocksmithDokument2 SeitenSSL LocksmithStopSpyingOnMeNoch keine Bewertungen
- Encrypted Threat Protection: White PaperDokument7 SeitenEncrypted Threat Protection: White PaperswsloanNoch keine Bewertungen
- Decrypting SSL/TLS Traffic For Hidden Threats Detection: Conference PaperDokument5 SeitenDecrypting SSL/TLS Traffic For Hidden Threats Detection: Conference Paperlai khoiNoch keine Bewertungen
- Securosis SecurityPrivacyEncryptedNetwork FINALDokument20 SeitenSecurosis SecurityPrivacyEncryptedNetwork FINALmk7777Noch keine Bewertungen
- Best Practices For Securing Your Enterprise:: 10 Things You Need To KnowDokument10 SeitenBest Practices For Securing Your Enterprise:: 10 Things You Need To KnowShubham GuptaNoch keine Bewertungen
- Choosing A Cloud ProviderDokument9 SeitenChoosing A Cloud ProviderGabriel GiraldoNoch keine Bewertungen
- Choosing A Cloud Hosting Provider With ConfidenceDokument6 SeitenChoosing A Cloud Hosting Provider With ConfidencenaoexisteNoch keine Bewertungen
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerVon EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerNoch keine Bewertungen
- Symantec SSL Visibility Appliance: Data SheetDokument6 SeitenSymantec SSL Visibility Appliance: Data SheetDebojit GoswamiNoch keine Bewertungen
- Decryption Why Where and HowDokument6 SeitenDecryption Why Where and HowfanvantanNoch keine Bewertungen
- Security ProtocolsDokument4 SeitenSecurity Protocolsapi-3701346Noch keine Bewertungen
- SWOT AnalysisDokument2 SeitenSWOT AnalysisMian Muhammad OmairNoch keine Bewertungen
- SSL Offloading Relieves Server CPU LoadDokument2 SeitenSSL Offloading Relieves Server CPU Loadsyed_engrNoch keine Bewertungen
- Tackling SSL Vulnerabilities For Secure Online Transactions: E-GuideDokument13 SeitenTackling SSL Vulnerabilities For Secure Online Transactions: E-GuidewormingNoch keine Bewertungen
- Decrypt SSL and SSH TrafficDokument5 SeitenDecrypt SSL and SSH TrafficMinh Luan PhamNoch keine Bewertungen
- Security in e - CommerceDokument4 SeitenSecurity in e - CommerceAlex T BinoyNoch keine Bewertungen
- The Top Five Myths of Website SecurityDokument7 SeitenThe Top Five Myths of Website SecurityMiguel Angel MolineroNoch keine Bewertungen
- How secure are online payment systemsDokument7 SeitenHow secure are online payment systemsso guptaNoch keine Bewertungen
- Research Paper Topics in Network SecurityDokument5 SeitenResearch Paper Topics in Network Securityp1zajywigyd2100% (1)
- Mitigating Security Risks: at The Network'S EdgeDokument16 SeitenMitigating Security Risks: at The Network'S EdgeHéctor AndradeNoch keine Bewertungen
- Network Security Research Papers PDFDokument4 SeitenNetwork Security Research Papers PDFm1dyhuh1jud2100% (1)
- Analyzing Forget SSL Certificates in The Wild PDFDokument15 SeitenAnalyzing Forget SSL Certificates in The Wild PDFblob mlNoch keine Bewertungen
- Cloud Security ChallengesDokument10 SeitenCloud Security ChallengesAtul BarveNoch keine Bewertungen
- An SSL Decryption 4035Dokument4 SeitenAn SSL Decryption 4035Tryphon Tso-hunterNoch keine Bewertungen
- E Commerce Security Literature ReviewDokument6 SeitenE Commerce Security Literature Reviewea219sww100% (2)
- Endpoint Security (Ch10)Dokument15 SeitenEndpoint Security (Ch10)Areej OmarNoch keine Bewertungen
- Security in Cloud ComputingDokument30 SeitenSecurity in Cloud Computingtoon townNoch keine Bewertungen
- Report 1Dokument15 SeitenReport 1ycat440211813Noch keine Bewertungen
- Ixia-SV-WP-Role of Active SSL DecryptionDokument7 SeitenIxia-SV-WP-Role of Active SSL Decryptionliuyq7809Noch keine Bewertungen
- RGPV NotesDokument90 SeitenRGPV NotesIslamic India100% (1)
- Unit 4 - Cloud Computing - WWW - Rgpvnotes.in PDFDokument13 SeitenUnit 4 - Cloud Computing - WWW - Rgpvnotes.in PDFprince keshriNoch keine Bewertungen
- Chapter 4Dokument12 SeitenChapter 4jetowi8867Noch keine Bewertungen
- SSL Visibility Appliance enDokument4 SeitenSSL Visibility Appliance enDebojit GoswamiNoch keine Bewertungen
- EC II CH 3 4Dokument15 SeitenEC II CH 3 4Ness Wadia College of Coomerce PuneNoch keine Bewertungen
- The Five Myths of Web Application Security: Jeremiah Grossman, Cto and Co-Founder Whitehat Security, Inc. May 2005Dokument6 SeitenThe Five Myths of Web Application Security: Jeremiah Grossman, Cto and Co-Founder Whitehat Security, Inc. May 2005David Deka ThedarknessprinceNoch keine Bewertungen
- Document 4Dokument2 SeitenDocument 4Last SummerNoch keine Bewertungen
- SSL y Protocolos de SeguridadDokument12 SeitenSSL y Protocolos de Seguridadfrida ortizNoch keine Bewertungen
- CHAP - V (Cloud Computing)Dokument34 SeitenCHAP - V (Cloud Computing)baharNoch keine Bewertungen
- Bcs Ds BlueCoat Encrypted TAP en v1dDokument2 SeitenBcs Ds BlueCoat Encrypted TAP en v1dNancy DrewerNoch keine Bewertungen
- Why SSL Certificate Management Is Critical WhitepaperDokument9 SeitenWhy SSL Certificate Management Is Critical Whitepapercharanmann9165Noch keine Bewertungen
- Cryptography and Cloud SecurityDokument2 SeitenCryptography and Cloud SecurityAbdourahmane KaneNoch keine Bewertungen
- Firewall Features Overview PDFDokument5 SeitenFirewall Features Overview PDFElliott longNoch keine Bewertungen
- Network Security WorkDokument5 SeitenNetwork Security WorkjasperNoch keine Bewertungen
- Cloud Security and Its InfrastructureDokument22 SeitenCloud Security and Its InfrastructureRahul saini100% (1)
- Introduction To Sockets Layer: SecureDokument12 SeitenIntroduction To Sockets Layer: SecurePankaj MalviyaNoch keine Bewertungen
- Unit 6: Network Security and Public Key Infrastructure: Saujanya Raj Shrestha 017BSCIT041Dokument31 SeitenUnit 6: Network Security and Public Key Infrastructure: Saujanya Raj Shrestha 017BSCIT041Saujanya ShresthaNoch keine Bewertungen
- State of Encrypted AttacksDokument20 SeitenState of Encrypted AttacksShatten WeltNoch keine Bewertungen
- Diploma in Applied Network and Cloud Technology DNCT703 Network and Cloud SecurityDokument17 SeitenDiploma in Applied Network and Cloud Technology DNCT703 Network and Cloud SecurityAnchal SinghNoch keine Bewertungen
- Internet Security As Part of The Overall Security PlanDokument5 SeitenInternet Security As Part of The Overall Security PlanArvind Kumar SharmaNoch keine Bewertungen
- Cloud Computing 5Dokument5 SeitenCloud Computing 5serdal bilginNoch keine Bewertungen
- IOT PapersDokument25 SeitenIOT Papers18-QADEER AHMADNoch keine Bewertungen
- CCNAv 7Dokument134 SeitenCCNAv 7Jose ScottNoch keine Bewertungen
- Decryption Best PracticesDokument14 SeitenDecryption Best Practicesalways_redNoch keine Bewertungen
- Network Security Unit 4Dokument32 SeitenNetwork Security Unit 4Satyam PandeyNoch keine Bewertungen
- Secure Socket Layer (SSL) : Divey Gupta Sunny Gajjar B.Tech-IV Computer Engg. NIT-SuratDokument22 SeitenSecure Socket Layer (SSL) : Divey Gupta Sunny Gajjar B.Tech-IV Computer Engg. NIT-SuratSunny Kishorbhai GajjarNoch keine Bewertungen
- 615adcd8c83b9292ed1f83ac_The_essential-guide-to-secure-web-gatewayDokument9 Seiten615adcd8c83b9292ed1f83ac_The_essential-guide-to-secure-web-gatewaylakbabi1035Noch keine Bewertungen
- ATARC AIDA Guidebook - FINAL KDokument3 SeitenATARC AIDA Guidebook - FINAL KdfgluntNoch keine Bewertungen
- Nine Metadata Use Cases: Data-Driven Decisions Using Metadata - GigamonDokument8 SeitenNine Metadata Use Cases: Data-Driven Decisions Using Metadata - GigamonGigamonNoch keine Bewertungen
- Alfa Banking Group Enhances Network Performance Monitoring - Gigamon Case StudyDokument3 SeitenAlfa Banking Group Enhances Network Performance Monitoring - Gigamon Case StudyGigamonNoch keine Bewertungen
- How Subscriber-Aware Traffic Processing Yielded Big Savings For US Wireless Provider - Gigamon Case StudyDokument3 SeitenHow Subscriber-Aware Traffic Processing Yielded Big Savings For US Wireless Provider - Gigamon Case StudyGigamonNoch keine Bewertungen
- High Density Passive Fiber Optical TAPs From Gigamon - G-TAP M Series Data SheetDokument3 SeitenHigh Density Passive Fiber Optical TAPs From Gigamon - G-TAP M Series Data SheetGigamonNoch keine Bewertungen
- Active Visibility Solutions For Multi-Tiered Security - Gigamon Network IntelligenceDokument5 SeitenActive Visibility Solutions For Multi-Tiered Security - Gigamon Network IntelligenceGigamonNoch keine Bewertungen
- Securing The Software Defined Data Center (SDDC) - Gigamon & RSA Joint Solution BriefDokument2 SeitenSecuring The Software Defined Data Center (SDDC) - Gigamon & RSA Joint Solution BriefGigamonNoch keine Bewertungen
- Software-Defined Visibility (SDV) - The New Paradigm For IT - Gigamon WhitepaperDokument8 SeitenSoftware-Defined Visibility (SDV) - The New Paradigm For IT - Gigamon WhitepaperGigamonNoch keine Bewertungen
- Adaptive Packet Filtering - Gigamon TechnologyDokument3 SeitenAdaptive Packet Filtering - Gigamon TechnologyGigamonNoch keine Bewertungen
- Application Session Filtering Technology - Feature Brief by GigamonDokument3 SeitenApplication Session Filtering Technology - Feature Brief by GigamonGigamonNoch keine Bewertungen
- Edge Traffic Aggregation Node - GigaVUE TA Series Product BriefDokument1 SeiteEdge Traffic Aggregation Node - GigaVUE TA Series Product BriefGigamonNoch keine Bewertungen
- 40GB BiDirectional Passive TAP From Gigamon - G-TAP Product BriefDokument2 Seiten40GB BiDirectional Passive TAP From Gigamon - G-TAP Product BriefGigamonNoch keine Bewertungen
- Visibility Fabric Management With Software Defined Visibility - GigaVUE FM Product BriefDokument2 SeitenVisibility Fabric Management With Software Defined Visibility - GigaVUE FM Product BriefGigamonNoch keine Bewertungen
- Gigamon Enables Your Organization Become More Agile, Secure and Cost EffectiveDokument13 SeitenGigamon Enables Your Organization Become More Agile, Secure and Cost EffectiveGigamonNoch keine Bewertungen
- Advanced Network Traffic Intelligence With GigaSmart - Product BriefDokument2 SeitenAdvanced Network Traffic Intelligence With GigaSmart - Product BriefGigamonNoch keine Bewertungen
- Unified Network Visibility Fabric From Gigamon - Solution BriefDokument3 SeitenUnified Network Visibility Fabric From Gigamon - Solution BriefGigamonNoch keine Bewertungen
- Network Visibility Operating System Software - GigaVUE-OS Product BriefDokument1 SeiteNetwork Visibility Operating System Software - GigaVUE-OS Product BriefGigamonNoch keine Bewertungen
- The Need For Active Visibility: Download WhitepaperDokument3 SeitenThe Need For Active Visibility: Download WhitepaperGigamonNoch keine Bewertungen
- Gigamon Gives You More Visibility Into Your Virtualized Data CentersDokument2 SeitenGigamon Gives You More Visibility Into Your Virtualized Data CentersGigamonNoch keine Bewertungen