Beruflich Dokumente
Kultur Dokumente
FSAE Troubleshoot
Hochgeladen von
Luis Gonzalez AlarconOriginalbeschreibung:
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
FSAE Troubleshoot
Hochgeladen von
Luis Gonzalez AlarconCopyright:
Verfügbare Formate
Technical Note : FSAE Troubleshooting Guide
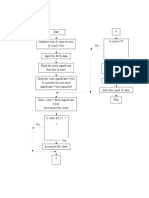
Note : this article is extracted from http://kb.fortinet.com/. This article provides troubleshooting steps that can be used when encountering FSAE problems. It is assumed the initial setup of FSAE has been completed. The FSAE installation guide can be found on http://docs.fortinet.com/ . The following chart shows an overview of the troubleshooting process : Note: "CA" in this article refers to the Collector agent.
Branch Point 1: Is the FortiGate unit connected to the collector agent ?
The first requirement is the connection from the FortiGate unit to the collector agent. The best way to verify the connectivity is by running the following CLI commands: diagnose debug enable diagnose debug authd fsae server-status If the collector agent is not connected, proceed to branch point 2. otherwise go to the "Group Check" section
Branch Point 2: Is the Collector Agent running ?
Opening the collector agent configuration interface displays the status of the collector agent service. You can also check by going to Administrative Tools > Services > Check the 'Fortinet Server Authentication Extention' Service. If the Collector agent is not running, go to section "Collector agent not running". Otherwise, proceed to section "Collector Agent running but not connected".
Section 1: Collector agent not running
Steps to follow : 1.1. - Check if the collector agent is using a domain administrator account : go to Administrative Tools > Services > Check the 'Fortinet Server Authentication Extention' Service. If it is not using a domain administrator account, please change the account. 1.2. - If another application is using the ports used by FSAE (ports 8000 and 8002 by default) the service will not start. This can be viewed in the collector agent logs. The related article "Troubleshooting Tip : Port conflict issues giving FSAE Collector Agent stopped message" provides additional information. 1.3. - Finally, checking the collector agent logs will show any other errors that are preventing the collector agent from starting.
Section 2: Collector Agent running but not connected
Steps description : 2.1 - A common problem is the password mismatch between the FortiGate and the collector agent. Reset the password between the two devices. The password is set on the main page on the Collector agent and on the FortiGate unit by going to User > Directory Service > Edit FSAE connector > Password. 2.2 - Another reason for the FortiGate unit not being able to connect to the collector agent is that a Firewall (host firewall or network firewall) is blocking the FSAE TCP port 8000. Make sure nothing is blocking the traffic between the FortiGate and the collector agent. 2.3 - A sniffer trace can be gathered on the FortiGate and the collector agent. The following command will start capturing traffic on the FortiGate : diagnose sniff packet any 'host <collector agent IP address> and port 8000' 4 2.4 - You can also check the FSAE process debug output on the FortiGate by using the commands: diagnose debug enable diagnose debug application authd 8256
Section 3: Group Check
Steps description : 3.1 - If you are not seeing the groups on the collector agent, check the collector agent groups using "group filter". Verify the groups configuration. 3.2 - Verify if the groups on the FortiGate unit and the collector agent are using the same mode. More on FSAE modes can be found in the article "FSAE Windows Directory Access Methods - Standard versus Advanced" (see the related articles section below) 3.3 - Proceed to branch point 3
Branch Point 3: Are you seeing logon events on the FortiGate unit ?
The FortiGate unit will need to see the logon event when the user logs in to his PC. You can check if the FortiGate unit is receiving logon events by running the commands: diagnose debug enable diagnose debug authd fsae list If you see ANY users logged in, proceed to branch point 4. Otherwise proceed to section "Not seeing logon events".
Section 4: Not seeing logon events
Steps description : 4.1 - Make sure the DC agent is installed on ALL domain controllers. If you have any problems pushing out the DC agent, you can refer to article "Troubleshooting FSAE DC agent installation problems" for more info (See related articles). To confirm that the DC agent is installed, you can refer to article "Where is DCagent service" in the related articles. 4.2 - If you have configured an LDAP server on the FSAE connector (on the FortiGate unit go to User > Directory Service > Edit FSAE connector > LDAP). You should try to disable it and running the commands from branch point 3 again. An incorrectly configured LDAP server is a common cause for not seeing the logon events on the FortiGate unit. 4.3 - If this does not resolve the issue, open a support ticket.
Branch Point 4: Is the test user show up in the FSAE list ?
Focusing on a single test user will help for further troubleshooting. Information to collect about the "test" user : 1. 2. 3. 4. Account username of the user currently logged in. IP address of the test host. You can run 'ipconfig' to get the IP of the host. Host DNS name. You can run the command 'hostname' to get the host name. Logon server name: This is the domain controller that the host used to authenticate. You can get this info by running the command 'echo %logonserver%'.
Once all info about the test host are gathered, you can run the following commands on the FortiGate unit: diagnose debug enable diagnose debug authd fsae list If the user appears on the list, proceed to section "User in FSAE list", otherwise proceed to section "User not in FSAE list".
Section 5: User in FSAE list
Steps description : 5.1 - If the user is on the list but has an incorrect IP you will need to check the DNS settings on your DNS server. A common problem is with multi-homed hosts (i.e. hosts with more than one network interface). A multi-homed host may resolve host name to the IP address of one interface while send traffic out another. The FortiGate will receive traffic from the IP of the other interface and think the host is not authenticated. 5.2 - If the user does have the correct IP but not the correct groups you should disable group caching on the collector agent. More on group caching as well as how to disable this feature can be found on "New Feature in FSAE build 42 and later (Group caching)" (see related articles below). 5.3 - If the username, IP and groups are all correct but the user is still not able to access the Internet, the issue may be due to a Firewall Policy setting. Please check also the article "Only the first authenticated group allowed through policy" (see related articles below).
Section 6: User not in FSAE list
Steps description : 6.1 - Check the IP address of the host. If the IP is listed with the username of a service account, the service account is generating a logon event and is overriding the user's logon. A good article on this issue is "Windows application forces to log-off the current user on FSAE and access through the FortiGate is blocked" (see related articles below). 6.2 - If the user recently moved to a new group try disabling group caching. More on group caching as well as how to disable this feature can be found on "New Feature in FSAE build 42 and later (Group caching)" (see related articles below). 6.3 - Make sure the log level is set to "information". Start at the end of the file and search backwards for the IP of the test host. If not found search for the username of the test host. If still not found search for the hostname of the test host. If you found the host in any of the searches proceed to subsection A, otherwise proceed to subsection B. Subsection A: User found in collector agent logs Steps description : 6.A.1 Check if there are any DNS errors in the collector agent for the host name. These include the collector agent unable to resolve the host name at all or resolving to an incorrect IP. Either way you will need to check the DNS server. 6.A.2 If the collector agent logs show that the host timed out, the collector agent was not able to connect to the host on port 139 & 445 to verify the user. Please check also the related article "User status "Not Verified" on the collector agent " (See related articles below). 6.A.3 If all above have failed, please open a support ticket Subsection B: User not found in collector agent logs If the user is not in the collector agent logs, the logon event was probably not sent by the DC agent. Check which domain controller authenticated the host (run 'echo %logonserver%' on the host) and troubleshoot that domain controller Make sure the DC is installed on the domain controller. If it is not, install the DC agent (if you are having problems you can refer to article "Troubleshooting FSAE DC agent installation problems" in the related article section below). If the DC agent is installed, enable logging on the DC agent and check if there are any errors in the DC agent logs.
Das könnte Ihnen auch gefallen
- Fortinet OT Value Proposition v1.4 - ESDokument59 SeitenFortinet OT Value Proposition v1.4 - ESLuis Gonzalez AlarconNoch keine Bewertungen
- Comandos FortigateDokument26 SeitenComandos FortigateLuis Gonzalez AlarconNoch keine Bewertungen
- Netlab Remote PC Guide Vol 3 ConfiguringDokument50 SeitenNetlab Remote PC Guide Vol 3 ConfiguringLuis Gonzalez AlarconNoch keine Bewertungen
- Joining Data From Multiple TablesDokument27 SeitenJoining Data From Multiple TablesLuis Gonzalez AlarconNoch keine Bewertungen
- Working With SubqueriesDokument27 SeitenWorking With SubqueriesLuis Gonzalez AlarconNoch keine Bewertungen
- Remote PC Guide Series - Volume 2a: Dell R710 BIOS and RAID ConfigurationDokument13 SeitenRemote PC Guide Series - Volume 2a: Dell R710 BIOS and RAID ConfigurationRwjdjNoch keine Bewertungen
- Modifying Data in TablesDokument35 SeitenModifying Data in TablesLuis Gonzalez AlarconNoch keine Bewertungen
- Querying and Filtering DataDokument32 SeitenQuerying and Filtering DataLuis Gonzalez AlarconNoch keine Bewertungen
- Configurando Supervisoras Redundantes 6000Dokument18 SeitenConfigurando Supervisoras Redundantes 6000Luis Gonzalez AlarconNoch keine Bewertungen
- Course 2778A: Writing Queries Using Microsoft® SQL Server® 2008 Transact-SQLDokument14 SeitenCourse 2778A: Writing Queries Using Microsoft® SQL Server® 2008 Transact-SQLLuis Gonzalez AlarconNoch keine Bewertungen
- Grouping and Summarizing DataDokument34 SeitenGrouping and Summarizing DataLuis Gonzalez AlarconNoch keine Bewertungen
- Convergencia Rapida y Ha en Redes Ruteadas Networkers 2007Dokument100 SeitenConvergencia Rapida y Ha en Redes Ruteadas Networkers 2007Luis Gonzalez AlarconNoch keine Bewertungen
- 6236A-En Implementing Maintaining MS SQLServer08 ReportingServices-TrainerWorkbookDokument462 Seiten6236A-En Implementing Maintaining MS SQLServer08 ReportingServices-TrainerWorkbookLuis Gonzalez AlarconNoch keine Bewertungen
- Module 1: Getting Started With Databases and Transact-SQL in SQL Server 2008Dokument37 SeitenModule 1: Getting Started With Databases and Transact-SQL in SQL Server 2008Luis Gonzalez AlarconNoch keine Bewertungen
- CEH v5 Module 14 SQL InjectionDokument52 SeitenCEH v5 Module 14 SQL InjectionLuis Gonzalez AlarconNoch keine Bewertungen
- VRRP for redundant network servicesDokument11 SeitenVRRP for redundant network servicesLuis Gonzalez AlarconNoch keine Bewertungen
- Iconografia Cisco 17-03-2010Dokument34 SeitenIconografia Cisco 17-03-2010HumbertoAcostaNoch keine Bewertungen
- Why Unified Communications and Why CiscoDokument4 SeitenWhy Unified Communications and Why CiscoLuis Gonzalez AlarconNoch keine Bewertungen
- 8 Steps To Secure and Harden Cisco RouterDokument6 Seiten8 Steps To Secure and Harden Cisco RouterchiweekokNoch keine Bewertungen
- VMware Vsphere 5.1 Install Configure Manage Lab ManualDokument152 SeitenVMware Vsphere 5.1 Install Configure Manage Lab Manualmisresearchsky100% (3)
- VMWare Vsphere Esxi Vcenter Server 5.1 Installation & Setup GuideDokument316 SeitenVMWare Vsphere Esxi Vcenter Server 5.1 Installation & Setup GuideVinod DhakaNoch keine Bewertungen
- May 14 13Dokument5 SeitenMay 14 13Luis Gonzalez AlarconNoch keine Bewertungen
- Enterprise QoS SRNDDokument328 SeitenEnterprise QoS SRNDjdenoyNoch keine Bewertungen
- VMWare Vsphere Esxi Vcenter Server 5.1 Installation & Setup GuideDokument316 SeitenVMWare Vsphere Esxi Vcenter Server 5.1 Installation & Setup GuideVinod DhakaNoch keine Bewertungen
- CCNP4 SLM v50Dokument344 SeitenCCNP4 SLM v50Adam MalikNoch keine Bewertungen
- Cisco Secure PIX Firewall Advanced Student Guide Version 2.1Dokument332 SeitenCisco Secure PIX Firewall Advanced Student Guide Version 2.1p.calimero5844100% (1)
- 2+IPT+Configuring Cisco CMEDokument84 Seiten2+IPT+Configuring Cisco CMELuis Gonzalez AlarconNoch keine Bewertungen
- FortiGate Troubleshooting GuideDokument16 SeitenFortiGate Troubleshooting GuideRocco D'SadeNoch keine Bewertungen
- En Switch v6 Ch04Dokument70 SeitenEn Switch v6 Ch04ignaciomatte2011Noch keine Bewertungen
- Shoe Dog: A Memoir by the Creator of NikeVon EverandShoe Dog: A Memoir by the Creator of NikeBewertung: 4.5 von 5 Sternen4.5/5 (537)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeVon EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeBewertung: 4 von 5 Sternen4/5 (5794)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceVon EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceBewertung: 4 von 5 Sternen4/5 (890)
- The Yellow House: A Memoir (2019 National Book Award Winner)Von EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Bewertung: 4 von 5 Sternen4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingVon EverandThe Little Book of Hygge: Danish Secrets to Happy LivingBewertung: 3.5 von 5 Sternen3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryVon EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryBewertung: 3.5 von 5 Sternen3.5/5 (231)
- Never Split the Difference: Negotiating As If Your Life Depended On ItVon EverandNever Split the Difference: Negotiating As If Your Life Depended On ItBewertung: 4.5 von 5 Sternen4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureVon EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureBewertung: 4.5 von 5 Sternen4.5/5 (474)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersVon EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersBewertung: 4.5 von 5 Sternen4.5/5 (344)
- Grit: The Power of Passion and PerseveranceVon EverandGrit: The Power of Passion and PerseveranceBewertung: 4 von 5 Sternen4/5 (587)
- On Fire: The (Burning) Case for a Green New DealVon EverandOn Fire: The (Burning) Case for a Green New DealBewertung: 4 von 5 Sternen4/5 (73)
- The Emperor of All Maladies: A Biography of CancerVon EverandThe Emperor of All Maladies: A Biography of CancerBewertung: 4.5 von 5 Sternen4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaVon EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaBewertung: 4.5 von 5 Sternen4.5/5 (265)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreVon EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreBewertung: 4 von 5 Sternen4/5 (1090)
- Team of Rivals: The Political Genius of Abraham LincolnVon EverandTeam of Rivals: The Political Genius of Abraham LincolnBewertung: 4.5 von 5 Sternen4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyVon EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyBewertung: 3.5 von 5 Sternen3.5/5 (2219)
- The Unwinding: An Inner History of the New AmericaVon EverandThe Unwinding: An Inner History of the New AmericaBewertung: 4 von 5 Sternen4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Von EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Bewertung: 4.5 von 5 Sternen4.5/5 (119)
- Her Body and Other Parties: StoriesVon EverandHer Body and Other Parties: StoriesBewertung: 4 von 5 Sternen4/5 (821)
- Siemens PLC s7 1200Dokument71 SeitenSiemens PLC s7 1200Mahadzir Bin Mat Rabi'Noch keine Bewertungen
- HCNA-Security-CBSN Constructing Basic Security Network TrainingDokument509 SeitenHCNA-Security-CBSN Constructing Basic Security Network Trainingmahmood291100% (1)
- Flow Chart:: Is Count 0?Dokument2 SeitenFlow Chart:: Is Count 0?KARTHINoch keine Bewertungen
- Meraki Datasheet Ms125 Series enDokument7 SeitenMeraki Datasheet Ms125 Series enblackmamba etti jeanNoch keine Bewertungen
- NMB RT 8200wDokument2 SeitenNMB RT 8200wSergio Diaz PereiraNoch keine Bewertungen
- Dhi-Nvr4108/4116Hs-8P-4Ks2: 8/16 Channel Compact 1U 8poe 4K&H.265 Lite Network Video RecorderDokument3 SeitenDhi-Nvr4108/4116Hs-8P-4Ks2: 8/16 Channel Compact 1U 8poe 4K&H.265 Lite Network Video RecorderJimmy Andres Arias TrujilloNoch keine Bewertungen
- 7.4.3.4 Packet Tracer - Configuring Basic EIGRP With IPv6 Routing Instructions IG PDFDokument3 Seiten7.4.3.4 Packet Tracer - Configuring Basic EIGRP With IPv6 Routing Instructions IG PDFJESUSCAMPONoch keine Bewertungen
- ISA Server Introduction & InstallationDokument22 SeitenISA Server Introduction & InstallationAjmal IqbalNoch keine Bewertungen
- Design of A Data LoggerDokument62 SeitenDesign of A Data LoggerMuhammad Simjee100% (5)
- Asus Ts300 E7 Ps4 ServerDokument1 SeiteAsus Ts300 E7 Ps4 ServerMuhammad Imran RosadinNoch keine Bewertungen
- Void DocumentationDokument170 SeitenVoid Documentationrqn5gzvkfdNoch keine Bewertungen
- High Availability Configuration Guide, Cisco IOS XE Gibraltar 16.10.x (Catalyst 9500 Switches)Dokument54 SeitenHigh Availability Configuration Guide, Cisco IOS XE Gibraltar 16.10.x (Catalyst 9500 Switches)brunocpscNoch keine Bewertungen
- TL-SG3216 V2 DatasheetDokument5 SeitenTL-SG3216 V2 DatasheetMiguel Angel Gutierrez PerezNoch keine Bewertungen
- TEA - LTE 2.2.3 - GA Release Notes: System RequirementsDokument4 SeitenTEA - LTE 2.2.3 - GA Release Notes: System Requirementsmau_mmx5738Noch keine Bewertungen
- Creating and Restoring Wetlands: From Theory To Practice by Christopher Craft Read Ebook in FB2, DJV, AZW, DOCXDokument2 SeitenCreating and Restoring Wetlands: From Theory To Practice by Christopher Craft Read Ebook in FB2, DJV, AZW, DOCXliwegobNoch keine Bewertungen
- CCNA1 FINAL EXAMDokument64 SeitenCCNA1 FINAL EXAMsamiNoch keine Bewertungen
- TMC420 Backup Utility: Operating InstructionsDokument20 SeitenTMC420 Backup Utility: Operating InstructionsJhon Parker DimitrinskyNoch keine Bewertungen
- JumpDokument4 SeitenJumpAko C SeanNoch keine Bewertungen
- HackingDokument6 SeitenHackingapi-379098611100% (1)
- Computer Maintenance Checklist For Software and HardwareDokument3 SeitenComputer Maintenance Checklist For Software and HardwareKarthikNoch keine Bewertungen
- Parallel + Distrubuted ProgDokument35 SeitenParallel + Distrubuted Prog4444alisaNoch keine Bewertungen
- Prior Art On Lauri Valjakka US8495167Dokument32 SeitenPrior Art On Lauri Valjakka US8495167Jennifer M GallagherNoch keine Bewertungen
- PHC-D08 - USB Driver Installation Manual (En)Dokument34 SeitenPHC-D08 - USB Driver Installation Manual (En)Mallikharjuna OfficialNoch keine Bewertungen
- Veritas Netbackup For Db2 Administrator'S Guide: Unix and LinuxDokument144 SeitenVeritas Netbackup For Db2 Administrator'S Guide: Unix and LinuxsergeNoch keine Bewertungen
- Iatest 2-CS8493-oS-IT - SET2Dokument2 SeitenIatest 2-CS8493-oS-IT - SET2Ms.Sangeetha Priya IT DepartNoch keine Bewertungen
- HP Officejet Pro X476dw Multifunction PrinterDokument4 SeitenHP Officejet Pro X476dw Multifunction PrinterDaniel MartinsNoch keine Bewertungen
- CodaDokument25 SeitenCodamourya_chandraNoch keine Bewertungen
- Veeam PN 2 1 User GuideDokument137 SeitenVeeam PN 2 1 User GuideMohamed TarsafiNoch keine Bewertungen
- Workstation Heat, Sound, and Power Usage: Lenovo ThinkStation C30 vs. Dell Precision T5600Dokument14 SeitenWorkstation Heat, Sound, and Power Usage: Lenovo ThinkStation C30 vs. Dell Precision T5600Principled TechnologiesNoch keine Bewertungen