Beruflich Dokumente
Kultur Dokumente
Improvement of Bit Rate Using M-Ary Chaotic Pulse Position Modulation
Hochgeladen von
vietbinhdinhOriginalbeschreibung:
Originaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Improvement of Bit Rate Using M-Ary Chaotic Pulse Position Modulation
Hochgeladen von
vietbinhdinhCopyright:
Verfügbare Formate
REV Journal on Electronics and Communications, Vol. 1, No.
3, July September, 2011 183
Regular Article
Improvement of Bit Rate Using M-ary Chaotic Pulse Position
Modulation
Nguyen Xuan Quyen, Vu Van Yem, Thang Manh Hoang
School of Electronics and Telecommunications, Hanoi University of Science and Technology, 1 Dai Co
Viet, Hanoi, Vietnam
Correspondence: Vu Van Yem, yemvv-fet@mail.hut.edu.vn
Manuscript communication: received 29 October 2011, revised 26 November 2011
Abstract Recent studies have pointed out that Chaotic Pulse Position Modulation (CPPM) is a very promising method for
improving privacy and security in chaos-based digital communication. Especially, CPPM provides better performance than
other chaotic modulation methods in noise- and distortion-affected environments. In this paper we present our development
of a robust method named M-ary CPPM which is based on the combination of the conventional CPPM and multi-symbol
modulation in order to improve the transmission bit rate. The M-ary CPPM signal has a pulse train format in which each
pulse is a symbol and the chaotically-varied inter-pulse time interval conveys the binary information of k bits (M = 2
k
).
The analysis and development of modulation and demodulation schemes are presented in detail. Theoretical evaluation of
Bit-Error-Rate (BER) performance in the presence of additive white Gaussian noise (AWGN) and the use of AWGN ltering
is also provided. The chaotic behavior of the M-ary CPPM is investigated with the variation of modulation parameters.
In order to verify the performance of the proposed schemes, numerical simulations were carried out in Simulink and
comparison between simulation and theoretical results is reported.
Keywords chaotic modulation, chaotic pulse position modulation, CPPM, M-ary modulation, chaos-based digital commu-
nication, ultra-wide band, tent map.
1 Introduction
In recent years, chaotic signals and chaotic systems
have been investigated in various research elds such as
physics, biology, chemistry, and engineering [1]. Chaos-
based digital communication has received signicant
attention [2] due to its potential in improving the
privacy and security of information [3]. Many chaos-
based modulation methods have been proposed us-
ing different modulation schemes [3, 4]. Due to their
type of demodulation, these schemes can be classied
as coherent or non-coherent detection. Each method
has its own advantages and disadvantages but most
of them use the chaotic carrier created by a chaotic
dynamical system to convey information, so they are
sensitive to distortion and noise that can strongly affect
the synchronization [57] and cause errors in recovering
information.
A robust modulation method called Chaotic Pulse
Position Modulation was proposed in [8, 9] to overcome
the major drawbacks mentioned above. Since binary
information is only modulated onto the inter-pulse
intervals, not the phase, frequency or amplitude of the
pulses, the impact of distortion and noise on the pulse
shape does not seriously affect the synchronization pro-
cess. In CPPM, only one bit is decoded at the moment of
a received pulse, that leads to low transmission rate. To
improve the bit rate, we propose a modied modulation
method which is the combination of the conventional
CPPM and multi-symbol modulation, named M-ary
CPPM. The proposed method uses each chaotically-
varied inter-pulse interval as a carrier to convey the
binary information of k bits, where each pulse is con-
sidered as a symbol. It means that a volume of k
bits is decoded for each instance of received pulses,
thus the bit rate will increase signicantly. Like the
CPPM method, the M-ary CPPM also performs well
in distortion- and noise-affected channels and achieves
high levels of information privacy as well as automatic
synchronization without the need of specic hand-
shaking protocols [10]. Especially, this method is effec-
tive for direct transmission of ultra-narrow and low-
power pulses and therefore suitable for ultra-wide band
(UWB) communication [11, 12].
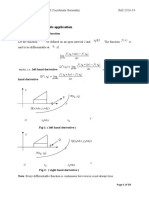
Tent map is a discrete-time and one-dimension non-
linear function with the piecewise-linear I/O charac-
teristic curve [13], used for generating chaotic values
which look like true random numbers [14]. In chaos-
based communications, the tent map is proposed for
application in chaotic modulation [15] with such ad-
vantages as the simplied calculation and the robust
regimes of chaos generation for rather broad ranges of
modulations parameters. Therefore, the utilization of
tent map for the M-ary CPPM is investigated with the
variation of modulation parameters. This is very impor-
tant for the design to guarantee the chaotic behavior of
the method.
1859-378X2011-0307 c 2011 REV
184 REV Journal on Electronics and Communications, Vol. 1, No. 3, July September, 2011
n
T
1 n
T
0
( )
M ary CPPM
S t
1 n
t
n
t
1
t
t
. . . . . .
A
Figure 1. M-ary CPPM signal.
n
T
1
( )
n
F T
0 t
( ) S t
1 n
t
n
t
. . .
d
m m m
. . .
0 1 1 M
A
Figure 2. Time interval T
n
with M symbols.
The rest of this paper is organized as follows. The
principle of the M-ary CPPM is described in Section 2.
Section 3 presents our analysis of the schemes for
modulator and demodulator in detail. In Section 4, BER
performance of the method is evaluated theoretically
based on a recursive algorithm. Section 5 investigates
the chaotic behavior of the M-ary CPPM with tent map.
In order to verify the performance of the proposed
schemes, a numerical simulation is implemented in
Simulink and its results in the time domain as well
as the resulted BER performance are presented in Sec-
tion 6. Finally, our conclusions are given in Section 7.
2 Description
In this section, we describe the principles of the M-ary
CPPM method. M-ary CPPM signal is considered as a
chaotic pulse train which is illustrated in Figure 1 and
can be expressed as follows:
S(t)
M-ary CPPM
=
n=0
A[u(t t
n
) u(t t
n
)], (1)
where u(t) is the unit-step function, A and are the
amplitude and width of the pulses, respectively. The n
th
pulse is generated at time t
n
= t
0
+
n
n=0
T
n
with T
n
being the time interval between the n-th and (n 1)-th
pulses. This interval is iteratively produced by a nonlin-
ear transformation F(T
n1
). By choosing a nonlinear
function F() with appropriate modulation parameters,
T
n
will vary in a chaotic way and has a random-like
behavior. The interval T
n
with M symbols is shown
in Figure 2.
In the M-ary CPPM modulator, the binary information
is modulated onto inter-pulse interval as follows:
T
n
= F(T
n1
) + d + mS
n
, (2)
where S
n
is the reference value of the n
th
symbol. The
source data is divided into k-bit groups which are then
mapped to equivalent symbols. The value of S
n
varies
COMPARATOR
CHAOTIC
THRESHOLD
GENERATOR
F(.)
S+H COUNTER
UNIT
DELAY
RECTANGULAR
PULSE
GENERATOR
BINARY
DATA
SOURCE
M-ARY
SYMBOL
MAPPING
TIME DELAY
MODULTOR
M-ARY MODULATOR
C(t)
Reset
M-ARY CPPM
SIGNAL_OUT
Clock
C
n
F(C
n
)
S
n
k bits_IN
Figure 3. Scheme for the M-ary CPPM modulator.
from 0 to M1 with M being the number of symbols
(M = 2
k
). The parameter d is a constant time delay
that is inserted to guarantee the synchronization of
the system. The parameter m is the modulation depth
and it directly affects the bit error rate as well as the
optimization of the transmission speed.
In the M-ary CPPM demodulator, the parameters d,
m and F() are the same as in the modulator. Each re-
ceived pulse carries information of a symbol and guides
the synchronization process. When the synchronization
state of the system is maintained, suppose that the
demodulator receives the interval T
n1
correctly, it
easily computes S
n
by the following equation:
S
n
=
T
n
F(T
n1
) d
m
. (3)
From the value of S
n
, the n
th
symbol is found and re-
mapped to k bits, thus the binary data is recovered.
Similar to the CPPM, the M-ary CPPM method also
has a chaotic pulse train format, thus its system au-
tomatically acquires synchronization as in a CPPM-
based system. The demodulator only needs to correctly
detect two consecutive pulses in order to re-establish
the synchronization state.
3 Modulator and Demodulator
In this section, the operation of an M-ary CPPM-based
system is examined through the design and analysis of
the schemes for modulator and demodulator.
3.1 Modulator
The scheme for an M-ary CPPM modulator is shown
in Figure 3 and its signals are illustrated in Figure 4.
The Counter operates in free running mode to pro-
duce a linearly increasing value C(t) = Kt at its
output, where the time t is the duration from the reset
time and K is the count step (the difference value
between two consecutive samples). At the time t
n1
,
the counter is reset, i.e., C(t
n1
) = 0, and then it starts
to count immediately. The output signal C(t) is put
into a Comparator to compare with a threshold value
F(C
n1
) which is produced at the output of the Chaotic
Threshold Generator F(). Here, C
n1
is the output
N.X. Quyen et al.: Improvement of Bit Rate Using M-ary Chaotic Pulse Position Modulation 185
Amplitude
t 0
F(C
n-1
)
F(C
n
)
C
n-1
C
n
C(t)
K
0
0
Reset
Clock
0
t
t
t
M-ary CPPM
Signal _Out
T
n
K
d
1 n
t
n
t
'
n
t
n
t
1 n
t
n
mS
m m m
...
0 1 M-1
A
Figure 4. Chaotic signals of the M-ary CPPM modulator.
value of the counter which was acquired and saved
by a Sample and Hold (S+H) block from the previous
iteration before the reset time. When the output of
the counter C(t) reaches the threshold value F(C
n1
),
the output of the comparator triggers a Rectangular
Pulse Generator to produce a clock pulse at the time
t
n
= t
n1
+ F(C
n1
)/K. Then, this clock pulse triggers
a Binary Data Source to map a k-bit number to a new
symbol S
n
at the M-ary Symbol Mapping block. At the
Time Delay Modulator, depending on the input value
S
n
, the clock pulse will be delayed by a time duration
d + mS
n
. Therefore, the modulated pulse is generated
at the time t
n
= t
n
+d +mS
n
. After that, the modulated
pulse will trigger the S+H block and reset the counter.
A new iteration starts and the next symbol will be
modulated in the same way. The reset pulses are the
same pulses of the output M-ary CPPM signal. From
the above equations, the time interval between the n
th
and (n 1)
th
pulses is determined by
T
n
= t
n
t
n1
=
F(C
n1
)
K
+ d + mS
n
=
F(KT
n1
)
K
+ d + mS
n
(4)
With K, d and m being constants, Eq. (4) points out that
the time interval T
n
depends on the reference value
S
n
and the chaotic threshold F(KT
n1
).
3.2 Demodulator
The scheme and signals of the M-ary CPPM de-
modulator are shown in Figures 5 and 6, respectively.
The Counter, the Chaotic Threshold Generator F(),
the S+H and the Rectangular Pulse Generator blocks
are the same as in the modulator. At the input of
the demodulator, the M-ary CPPM signal is put into
a Threshold Detector. When this signal exceeds the
threshold value, a rectangular pulse is generated by the
SUBTRACTOR
CHAOTIC
THRESHOLD
GENERATOR
F(.)
S+H
1
COUNTER
UNIT
DELAY
1
SYMBOL
DETECTOR
M-ARY
SYMBOL
REMAPPING
M-ARY DETECTOR
C(t)
Reset
M-ARY CPPM SIGNAL_IN
F(Cn)
S+H
2
RECTANGULAR
PULSE
GENERATOR
UNIT
DELAY
1
THRESHOLD
DETECTOR
F(C
n-1
)
k bits_OUT
C
n
-F(C
n-1
)
Sn
C
n
y(t)
p(t)
Figure 5. Scheme of the M-ary CPPM Demodulator.
0
t
M-ary CPPM
Signal _In
T
n
Amplitude
0
S
n
n
t
1 n
t
n
t
1 n
t
t 0
F(C
n-1
)
F(C
n
)
C
n-1
C
n
C(t)
K
K
d
1 n
t
n
t
'
n
t
n
mS
m m m
...
0 1 M-1
C
n
-F(C
n-1
)
1
2
M-1
.
.
.
t
A
Figure 6. Chaotic signals of the M-ary CPPM demodulator.
Rectangular Pulse Generator. This pulse at rst triggers
the block S+H 2 to save the value F(C
n1
) from the
F() output, then triggers the block S+H 1 to store the
value of the counter C
n
at that time, and then resets
the counter. The two values saved by the S+H blocks
are put into a Subtractor to produce a difference value
at the output. From Eq. (4), it is determined by
C
n
F(C
n1
) = KT
n
F(C
n1
) = K(d + mS
n
). (5)
After that, the difference value is put into a Symbol
Detector to decode the reference value S
n
of the symbol
as follows:
S
n
=
C
n
F(C
n1
)
K
d
m
. (6)
Depending on the value S
n
, the n
th
symbol is identied
and k bits are recovered at the output of the M-ary
Symbol Re-mapping block.
4 Theoretical Evaluation of BER
Performance
An analytical method to evaluate the CPPM error prob-
ability was reported in [8], and it is used for estimating
the BER of the M-ary CPPM in this research. For
186 REV Journal on Electronics and Communications, Vol. 1, No. 3, July September, 2011
Detection duration
T1-bit=m
A
H
0
t
m/2 m/2
0" window 1" window
Figure 7. Detection windows of the Binary-CPPM.
simplicity, lets consider the input signal of the M-
ary CPPM demodulator, y(t), as the ltered signal of
the sum of the transmitted M-ary CPPM signal and
the AWGN. In the threshold detector, when the signal
y(t) exceeds a threshold value H, the rectangular pulse
generator is triggered to generate a rectangular pulse,
p(t), with an amplitude A at its output. This pulse will
be used to recover the original data bits. Firstly, we
consider a simple case with the Binary CPPM (M = 2).
In Figure 7, the detection duration with the width m
is divided into the 0 window and the 1 window,
both have a same width, where m is the modulation
depth and is the fundamental sampling period of
the system. Assume that the demodulator maintains
the synchronization at all times. Bit error will occur
when the pulse p(t) falls into an unexpected window.
It means that the pulse p(t) of a transmitted bit 0
falls into the 1 window and vice versa. From [8], the
evaluation result of the BER is determined by
BER
Binary CPPM
= p
1
P
0/1
+ (1 p
1
)P
1/0
= p
1
_
1
_
1
2
_
1 +erf
_
h
_
E
b
/N
o
__
_ m
2
_
+ (1 p
1
)
_
_
1
2
_
1 +erf
_
h
_
E
b
/N
o
__
_ m
2
1
1
2
erfc
_
(1 h)
_
E
b
/N
o
_
_
,
(7)
where P
0/1
and P
1/0
are the error probabilities that a
0 is detected when an 1 is transmitted and vice
versa; p
1
is the proportion of 1 bits in the entire data
stream; and h =
H
A
. In the case that both p
1
and h are
equal to
1
2
, the expression for the BER can be written
in a shorter form as
BER
Binary CPPM
=
1
2
_
1 erf
_
1
2
_
E
b
/N
o
_
_
1
2
_
1 +erf
_
1
2
_
E
b
/N
o
___ m
2
1
_
.
(8)
Secondly, from the above results, we consider the gen-
eral case for BER evaluation of the M-ary CPPM (k bits)
with the detection duration illustrated in Figure 8. The
pulse p(t) can appear in the detection duration with
the width T
k-bit
= (M1)m. This duration is divided
into two windows having the same width of T
k-bit
/2.
In these, the left window contains symbols with the
0 prex and the right one contains symbols with the
Detection duration
Tk-bits=(M-1)m
A
H
0
t
T(k-1)-bits=(M-1)m/2
0" window 1" window
1xxxxxxxxxx
(k-1) bits
0xxxxxxxxxx
(k-1) bits
T(k-1)-bits=(M-1)m/2
Figure 8. Detection windows of the M-ary CPPM.
1 prex. Therefore, the error probability of the rst
detected bit, P
1st-bit
, is also the error probability of the
pulse in the detection duration T
k-bit
. From Eq. (8), we
have
P
1st-bit
=T
k-bit
=
1
2
_
1 erf
_
1
2
_
E
b
/N
o
_
_
1
2
_
1 +erf
_
1
2
_
E
b
/N
o
___
T
k-bit
2
1
_
_
.
(9)
In case the rst bit is recovered correctly, the M-ary
CPPM error probability is then the error probability
of recovering the rest (k 1) bits with the detection
duration of T
(k1)-bit
= (M 1)m/2. Therefore, the
M-ary CPPM error probability for transmitting a k-bit
sequence can be inferred from the following recursive
equation:
BER
M-ary CPPM
BER
k-bit
= P
1st-bit
+ (1 P
1st-bit
) BER
(k1)-bit
= P
T
k-bit
+ (1 P
T
k-bit
) BER
(k1)-bit
= BER
(k1)-bit
+P
T
k-bit
(1 BER
(k1)-bit
), (10)
with the initial equation being
BER
4-ary CPPM
BER
2-bit
= BER
1-bit
+P
T
2-bit
(1 BER
1-bit
), (11)
where BER
1-bit
BER
Binary CPPM
is determined by
Eq. (8), P
T
2-bit
is determined by Eq. (9) with the detection
duration T
2-bit
= 3m.
BER evaluation results of 2-, 4-, 8- and 16-ary CPPM
according to Eq. (10) and Eq. (11) are shown in Fig-
ure 13 (see the blue lines), in which the modulation
depth is chosen by m = 10.
5 M-ary CPPM with Tent Map
The conventional tent map is iteratively generated
through a transformation function F() : (0, 1) (0, 1)
as given by
x
n+1
= F(x
n
) = F
n
(x
0
)
=
_
ax
n
, 0 < x
n
0.5
a(1 x
n
), 0.5 < x
n
< 1
(12)
In this equation, n represents the number of iterations,
x
0
is the initial value, x
n
is the output value at the n-th
step, and parameter a controls the state of the map.
N.X. Quyen et al.: Improvement of Bit Rate Using M-ary Chaotic Pulse Position Modulation 187
Figure 9. Bifurcation diagram of the M-ary CPPM tent map with
variations of parameters a and (delta).
In the M-ary CPPM, the time interval between the n-
th and (n 1)-th pulses is expressed by Eq. (4) which
can be converted to the following:
T
n
=
F(KT
n1
)
K
+ d + mS
n
(13)
or
X
n
= F(X
n1
) + d
+ m
S
n
(14)
where X
n
= KT
n
, X
n1
= KT
n1
, d
= Kd, and m
=
Km. From Eq. (12) and Eq. (14), the tent map for the M-
ary CPPM, called the M-ary CPPM tent map, is derived
as
X
n+1
= F(X
n
)
=
_
aX
n
+ d
+ m
S
n
, 0 < X
n
0.5
a(1 X
n
) + d
+ m
S
n
, 0.5 < X
n
< 1
(15)
In the modulation process, the value of the symbol S
n+1
varies from 0 to M1, thus the value of the parameter
= d
+ m
S
n
varies from d
to d
+ m
(M 1). This
variation of makes the chaotic behavior of the M-
ary CPPM tent map dependent not only on the control
parameter a but also on the parameters d
, m
and M.
Figure 9 presents the bifurcation diagram of the M-ary
CPPM tent map, which clearly shows the dependence
of the chaotic behavior on the parameters a and . In
the gure, = 0 is the case of the conventional tent
map. The more the value of increases, the smaller the
chaotic area becomes, and when 0.5 the chaotic area
disappears. In practice, the parameters d
, m
and M
are determined rst based on design specications such
as bit rate and BER. After that, the control parameter
a is chosen to guarantee the chaotic behavior of the
system. For example, suppose we have a 4-ary CPPM
tent map (M = 4) with given parameters d
= 0.075 and
m
= 0.075, the maximum value of is then determined
by
max
= d
+ m
(M1) = 0.075 +0.075 3 = 0.3 (16)
0 10 20 30 40 50 60 70 80 90 100
0.2
0.4
0.6
0.8
1
n
X
n
+
1
=
F
(
X
n
)
0 10 20 30 40 50 60 70 80 90 100
0
1
2
3
n
S
n
0 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1
0
0.2
0.4
0.6
0.8
1
X
n
X
n
+
1
=
F
(
X
n
)
Sn=0
Sn=1
Sn=2
Sn=3
Attractor
(c)
(b)
(a)
Figure 10. The 4-ary CPPM tent map with parameters a = 1.3,
x
0
= 0.1, d
= 0.075, and m
= 0.075. (a) and (b): reference values
of the symbols and output values of the map, respectively, for 100
iterations; (c): attractor diagram with four xed points.
From the bifurcation diagram, it is drawn that the con-
trol parameter a must be chosen such that 1 < a < 1.4
in order to obtain a chaotic behavior for the system.
Simulation results for the above-mentioned 4-ary
CPPM tent map in the rst 100 iterations with X
0
= 0.1
and a = 1.3 are shown in Figure 10. It is shown that the
output values of the map (Figure 10b) vary chaotically
but also convey the information of the symbol values
(presented in Figure 10a). Besides, the chaotic behavior
of the map is displayed by the attractor diagram in
Figure 10c that have four xed points (red markers)
corresponding to four values of the symbols.
6 Numerical Simulation And Results
In order to verify the performance of the presented M-
ary CPPM modulation and demodulation schemes, a
numerical simulation of the system with an AWGN
channel and without parameter mismatch is imple-
mented in Simulink. It means that a same set of values
for the modulation parameters is used in both modu-
lator and demodulator. Simulations are performed for
M = 2, 4, 8, and 16. The values of other modulation pa-
rameters are chosen as follows: K = 0.002/, d = 10,
m = 10, and T
0
= 50, with being the fundamental
sampling period of the system. From Eq. (14) and
Figure 9, the parameters of the M-ary CPPM tent map
188 REV Journal on Electronics and Communications, Vol. 1, No. 3, July September, 2011
Table I
Transmission Rate of 2, 4, 8, 16-ary CPPM System Per 10
6
Fundamental Sample Time
Number of Number of Number of
symbols M transmitted pulses transmitted bits
2 3749 3749
4 3387 6774
8 3328 9984
16 3284 13136
are then derived as:
X
0
= KT
0
= (
0.002
50) = 0.1
d
= Kd = (
0.002
10) = 0.02
m
= Km = (
0.002
10) = 0.02
Therefore,
max
(M = 2, 4, 8, 16) =
max
(M = 16)
= d
+m
(16 1) = 0.02 +0.02 15 = 0.32
(17)
Then, the value for a is selected as a = 1.3 to guarantee
the chaotic behavior of the simulated system for all four
cases of M (2, 4, 8, and 16).
6.1 Chaotic Signals in Time Domain
An 8-ary CPPM system with an AWGN channel
is simulated, in which E
b
/N
o
= 20 dB to ensure a
good transmission line. Simulated chaotic signals in the
8-ary CPPM modulator and demodulator, within the
duration from the starting time 0 to 5000, are shown
in Figure 11 and Figure 12, respectively. We can observe
that the time interval T
n
varies chaotically in the range
between 150 and 500. The widths of the reset, clock
and M-ary CPPM pulses are the same and equal to 20.
At each time instant, S
n
receives only one of the eight
values, 0, 1, 2, 3, 4, 5, 6 or 7, corresponding to one of
the eight symbols, 000, 001, 010, 011, 100, 101, 110 or
111, respectively.
When the synchronization state of the system is
maintained, the signals recovered by the demodulator
exactly match their corresponding signals in the mod-
ulator. It veries that the proposed schemes for the M-
ary CPPM method are suitable and feasible.
6.2 Improvement of Bit-Rate Performance
Table I compares simulation results of transmission
rates between the 2-, 4-, 8- and 16-ary CPPM schemes
with a time duration of 10
6
and E
b
/N
o
= 20 dB for
all simulations. These results show that the numbers of
transmitted pulses (i.e., the symbol rates) of the 4-, 8-
and 16-ary CPPM schemes are only slightly lower than
that of the binary CPPM scheme, but their numbers
of transmitted bits (i.e., the bit rates) are much higher
than the binary CPPM bit rate. That means a signi-
cant improvement in bit-rate performance of the M-ary
CPPM compared to the conventional CPPM. According
to these results, if the processing speed of modulator
Figure 11. Time-domain signals of the 8-ary modulator. (a): the
reference signal S
n
; (b): output of the counter C(t); (c) and (d): input
and output of the chaotic threshold generator F(), respectively; (e):
clock pulses (f): the output 8-ary CPPM signal.
Figure 12. Time-domain signals of the 8-ary demodulator. (a): the
input 8-ary CPPM signal; (b) and (c): outputs of the blocks S+H 2 and
S+H 1, respectively; (d): output signal from the counter; (e): recovered
signal S
n
.
and demodulator circuits is 1 MHz (10
6
pulses per
second), for example, then the corresponding bit rates
for M = 2, 4, 8, and 16 are 3.749 Kbps, 6.774 Kbps,
9.984 Kbps, and 13.136 Kbps, respectively.
N.X. Quyen et al.: Improvement of Bit Rate Using M-ary Chaotic Pulse Position Modulation 189
0 2 4 6 8 10 12 14 16
10
6
10
4
10
2
10
0
Eb/No (dB)
B
i
t
E
r
r
o
r
R
a
t
e
(
B
E
R
)
M=2 evaluation
M=4 evaluation
M=8 evaluation
M=16 evaluation
M=2 simulation
M=4 simulation
M=8 simulation
M=16 simulation
Figure 13. Theoretical vs. simulated BER results for the 2-, 4-, 8-,
and 16-ary CPPM systems.
6.3 BER Performance
The BER performance obtained from simulations of
the 2-, 4-, 8-, and 16-ary CPPM systems with a l-
tered AWGN channel is presented in Figure 13 (red
lines). This BER is calculated as the number of error
bits divided by the total number of transmitted bits
in a time duration of 10
8
. Similar to the theoretical
curves, there are only slight differences between the
simulation curves of the 2-, 4-, 8-, and 16-ary CPPM
systems. Besides, with a same value of the fraction
E
b
/N
o
, the simulation BER values are slightly higher
than their corresponding theoretical ones. It can be
explained that the cause of these differences is the loss
of synchronization leading to bit errors. In theoretical
evaluation, we suppose that the synchronization state
is maintained at all times, thus pulse errors leading to
bit errors can only occur due to noise and ltering.
However, in the simulations, the effects of noise and
ltering may cause not only pulse errors but also the
loss of synchronization which leads to bit errors.
It can be observed from simulation results that, when
the number of symbols, M, increases, the bit rate is im-
proved signicantly but the BER just slightly increases.
This is a great advantage of the proposed M-ary CPPM
method.
7 Conclusions
The paper has presented our development of the M-
ary Chaotic Pulse Position Modulation technique aimed
at improving the bit rate in secure communication
systems. The proposed schemes for the modulator and
demodulator of the system are designed and evaluated
using both theoretical evaluation and numerical simu-
lation in terms of time-domain signals and BER perfor-
mance. In addition, the M-ary CPPM tent map is in-
vestigated considering the variation of the modulation
parameters versus the chaotic behavior of the system.
It can be seen from presented results that the M-ary
CPPM not only inherits valuable features of the CPPM-
based methods such as strong security and privacy due
to its chaotic behavior, good performance in noise- and
distortion-affected environments; but can also achieve a
much higher bit rate with only a slightly different BER
performance as compared to the conventional CPPM.
This is the most important point to make the M-ary
CPPM become a strong candidate for applications of
chaos-based digital communication, especially in UWB
and high security-required systems.
Acknowledgment
This work is carried out in the framework of the re-
search project No.102.992010.17 supported by the Viet-
nams National Foundation for Science and Technology
Development (NAFOSTED). The authors would like to
thank the NAFOSTED for supporting this work.
References
[1] S. H. Strogatz, Nonlinear Dynamics And Chaos: With Ap-
plications To Physics, Biology, Chemistry, And Engineering.
Westview Press, 2001.
[2] M. P. Kennedy and G. Kolumbn, Special issue on
"noncoherent chaotic communications", IEEE Transac-
tions on Circuits and Systems I: Fundamental Theory and
Applications, vol. 47, no. 12, pp. 16611662, Dec. 2000.
[3] P. Stavroulakis, Ed., Chaos Applications in Telecommunica-
tions. CRC Press, 2005.
[4] W. M. Tam, F. C. M. Lau, and C. K. Tse, Digital Com-
munications with Chaos: Multiple Access Techniques and
Performance. Elsevier Science, 2006.
[5] L. M. Pecora and T. L. Carroll, Synchronization in
chaotic systems, Physical Review Letters, vol. 64, no. 8,
pp. 821824, Feb. 1990.
[6] N. F. Rulkov and L. S. Tsimring, Synchronization meth-
ods for communication with chaos over band-limited
channels, International Journal of Circuit Theory and Ap-
plications, vol. 27, no. 6, pp. 555567, Nov./Dec. 1999.
[7] C.-C. Chen and K. Yao, Numerical evaluation of error
probabilities of self-synchronizing chaotic communica-
tions, IEEE Communications Letters, vol. 4, no. 2, pp. 37
39, Feb. 2000.
[8] N. F. Rulkov, M. M. Sushchik, L. S. Tsimring, and A. R.
Volkovskii, Digital communication using chaotic-pulse-
position modulation, IEEE Transactions on Circuits and
Systems I: Fundamental Theory and Applications, vol. 48,
no. 12, pp. 14361444, Dec. 2001.
[9] J. Sushchik, M., N. Rulkov, L. Larson, L. Tsimrin,
H. Abarbanel, K. Yao, and A. Volkovskii, Chaotic pulse
position modulation: A robust method of communicat-
ing with chaos, IEEE Communications Letters, vol. 4,
no. 4, pp. 128130, Apr. 2000.
[10] H. Torikai, T. Saito, and W. Schwarz, Synchronization
via multiplex pulse trains, IEEE Transactions on Cir-
cuits and Systems I: Fundamental Theory and Applications,
vol. 46, no. 9, pp. 10721085, Sep. 1999.
[11] Y. Kim and et al., Chaotic UWB System, IEEE Std. 802.15-
05-0132-03-004a, Mar. 2005.
[12] P. Chiang and C. Hu, Chaotic pulse-position base-
band modulation for an ultra-wideband transceiver in
CMOS, IEEE Transactions on Circuits and Systems II:
Express Briefs, vol. 57, no. 8, pp. 642646, Aug. 2010.
[13] J. T. Bean and P. J. Langlois, A current mode analog
circuit for tent maps using piecewise linear functions,
in Proc. IEEE International Symp. Circuits and Systems
(ISCAS94), vol. 6, London, UK, 30 May 2 June 1994,
pp. 125128.
190 REV Journal on Electronics and Communications, Vol. 1, No. 3, July September, 2011
[14] T. Addabbo, M. Alioto, A. Fort, S. Rocchi, and V. Vig-
noli, The digital tent map: Performance analysis and
optimized design as a low-complexity source of pseu-
dorandom bits, IEEE Transactions on Instrumentation and
Measurement, vol. 55, no. 5, pp. 14511458, Oct. 2006.
[15] H. Ruan, E. E. Yaz, T. Zhai, and Y. I. Yaz, A generaliza-
tion of tent map and its use in EKF based chaotic param-
eter modulation/demodulation, in Proc. 43rd IEEE Conf
Decision and Control, vol. 2, 14-17 Dec. 2004, pp. 2071
2075.
Nguyen Xuan Quyen was born in Nghe An,
Viet Nam in 1983. He received the Diploma of
Engineer and Master degree from the School
of Electronics and Telecommunications (SET),
Hanoi University of Science and Technology
(HUST) in 2006 and 2008, respectively. From
2007 to 2011, he was a lecturer at the Depart-
ment of Telecommunication Systems of SET-
HUST. Currently, he is working toward PhD
degree at Institute for Smart System Technolo-
gies, Alpen-Adria University in Klagenfurt,
Austria. His main research interests are microwave circuits, ultra wide
band communications and chaos-based digital communications.
Vu Van Yem was born in 1975 in Hai
Phong, Vietnam. He received the Ph.D. degree
in communications from the Department of
Electronics and Communications, TELECOM
ParisTech (formerly ENST Paris) France in
2005. From 2006 to 2007, he was a postdoc-
toral researcher at the Department of Hyper-
frequencies and Semiconductor, Institute of
Electronics, Microelectronics and Nanotech-
nology (IEMN), France. He has been quali-
ed to be named as Associate Professor since
November, 2009. Currently, he is the head of the department of
telecommunication systems, school of electronics and telecommunica-
tions, Hanoi University of Science and Technology, Vietnam. His areas
of expertise are microwave engineering, antenna, chaos-based digital
communications as well as wireless communication and localization
systems.
Thang Manh Hoang received the B.S. and
M.S. degrees in Electronics and Telecommuni-
cations from Hanoi University of Science and
Technology in 1998 and in 2001, respectively.
During 1998-2004, he had stayed with Fac-
ulty of Electronics and Telecommunications,
Hanoi University of Science and Technology.
He received a PhD degree in Information
and Control Engineering in 2007 at Nagaoka
University of Technology, Japan. Now, he is
a lecturer at Department of Electronics and
Computer Engineering, School of Electronics and Telecommunica-
tions, Hanoi University of Science and Technology, Hanoi, Vietnam.
He is an Executive Member of IEEE Vietnam Section and of Korea
Information and Communications Society (KICS), a member of IEEE,
IEEE Circuits and Systems Society (CAS), IEEE Communications
Society (ComSoc), Korea Information and Communications Society
(KICS), Radio Electronics Vietnam (REV).
Das könnte Ihnen auch gefallen
- Characteristic List & DefinitionsDokument5 SeitenCharacteristic List & Definitionstabithapang89% (116)
- Week 1 DLL - General MathematicsDokument5 SeitenWeek 1 DLL - General Mathematicsanon_838476361Noch keine Bewertungen
- Arc Flash Protection Calculations and GuidelinesDokument46 SeitenArc Flash Protection Calculations and GuidelinesRPantel100% (2)
- MIMO Channel Estimation Using The LS and MMSE Algorithm: Mohammed Ali Mohammed MOQBEL, Wangdong, Al-Marhabi Zaid AliDokument10 SeitenMIMO Channel Estimation Using The LS and MMSE Algorithm: Mohammed Ali Mohammed MOQBEL, Wangdong, Al-Marhabi Zaid AliKoustab MaityNoch keine Bewertungen
- Pilot Optimization and Channel Estimation For Multiuser Massive MIMO SystemsDokument6 SeitenPilot Optimization and Channel Estimation For Multiuser Massive MIMO SystemsQuả Ớt Leo-neeNoch keine Bewertungen
- E1106-12 Método de Prueba Estándar para La Calibración Primaria de Sensores de Emisión Acústica1Dokument13 SeitenE1106-12 Método de Prueba Estándar para La Calibración Primaria de Sensores de Emisión Acústica1fredy lopezNoch keine Bewertungen
- Transmitter and ReceiverDokument28 SeitenTransmitter and ReceiverVinod NayyarNoch keine Bewertungen
- Performance of Diversity Combining Techniques For Antenna ArraysDokument4 SeitenPerformance of Diversity Combining Techniques For Antenna ArraysTushar SaxenaNoch keine Bewertungen
- BLAST System: Different Decoders With Different Antennas: Pargat Singh Sidhu, Amit Grover, Neeti GroverDokument6 SeitenBLAST System: Different Decoders With Different Antennas: Pargat Singh Sidhu, Amit Grover, Neeti GroverIOSRJEN : hard copy, certificates, Call for Papers 2013, publishing of journalNoch keine Bewertungen
- Survey of MMSE Channel Equalizers: University of Illinois at ChicagoDokument7 SeitenSurvey of MMSE Channel Equalizers: University of Illinois at Chicagoamjc16Noch keine Bewertungen
- IJCER (WWW - Ijceronline.com) International Journal of Computational Engineering ResearchDokument6 SeitenIJCER (WWW - Ijceronline.com) International Journal of Computational Engineering ResearchInternational Journal of computational Engineering research (IJCER)Noch keine Bewertungen
- ICI CANCELLATION TECHNIQUES FOR OFDM SYSTEMSDokument6 SeitenICI CANCELLATION TECHNIQUES FOR OFDM SYSTEMSjavicho2006Noch keine Bewertungen
- Assignments-Assignment 4 PDFDokument4 SeitenAssignments-Assignment 4 PDFniki098Noch keine Bewertungen
- Possible Topic For TOEFL Ibt Speaking Task 1Dokument9 SeitenPossible Topic For TOEFL Ibt Speaking Task 1vietbinhdinhNoch keine Bewertungen
- Digital Modulation I August09Dokument14 SeitenDigital Modulation I August09gzb012Noch keine Bewertungen
- Coding and Modulation Techniques Enabling Multi-Tb/s Optical EthernetDokument2 SeitenCoding and Modulation Techniques Enabling Multi-Tb/s Optical EthernetAnthony WellsNoch keine Bewertungen
- Digital Equalization of Chromatic Dispersion and Polarization Mode DispersionDokument11 SeitenDigital Equalization of Chromatic Dispersion and Polarization Mode DispersionAliAzarniaNoch keine Bewertungen
- Analysis of A New Hybrid Clipping-SLM PAPR Reduction TechniqueDokument4 SeitenAnalysis of A New Hybrid Clipping-SLM PAPR Reduction TechniqueDr-Eng Imad A. ShaheenNoch keine Bewertungen
- Performance Comparisons Between Greedy and Lagrange Algorithms in Adaptive MIMO MC-CDMA SystemsDokument5 SeitenPerformance Comparisons Between Greedy and Lagrange Algorithms in Adaptive MIMO MC-CDMA SystemsFirman Nico ChandraNoch keine Bewertungen
- Performance Analysis of MIMO-OFDM Systems On Nakagami-M Fading ChannelsDokument5 SeitenPerformance Analysis of MIMO-OFDM Systems On Nakagami-M Fading ChannelsmnoppNoch keine Bewertungen
- CPM DemodulationDokument3 SeitenCPM Demodulationakkarthik0072933Noch keine Bewertungen
- PrintPN Sequence Generation & SimulationDokument4 SeitenPrintPN Sequence Generation & SimulationkuzhaloliNoch keine Bewertungen
- Comparison of ModulationDokument6 SeitenComparison of ModulationrakshitharaviNoch keine Bewertungen
- Detection of CPFSK Signals Using Per Survivor ProcessingDokument5 SeitenDetection of CPFSK Signals Using Per Survivor Processingradga1977Noch keine Bewertungen
- An Elaborate Frequency Offset Estimation For Ofdm SystemsDokument9 SeitenAn Elaborate Frequency Offset Estimation For Ofdm SystemswoodksdNoch keine Bewertungen
- VLC Communication B-10Dokument10 SeitenVLC Communication B-10Pavan KumarNoch keine Bewertungen
- Adaptive Coded Modulation With Receive Antenna Diversity and Imperfect Channel Knowledge at Receiver and TransmitterDokument7 SeitenAdaptive Coded Modulation With Receive Antenna Diversity and Imperfect Channel Knowledge at Receiver and TransmitterMatthew Luis Llano LoveraNoch keine Bewertungen
- MMSE Pre-Filtering Techniques For TDD MC-CDMA Downlink TransmissionsDokument5 SeitenMMSE Pre-Filtering Techniques For TDD MC-CDMA Downlink TransmissionsSurya AnilKumarNoch keine Bewertungen
- Optimal Modulation and Coding For Spatial Multiplexing Under Flat Fading ChannelDokument4 SeitenOptimal Modulation and Coding For Spatial Multiplexing Under Flat Fading ChannelIOSRJEN : hard copy, certificates, Call for Papers 2013, publishing of journalNoch keine Bewertungen
- Mabruk Jour Adaptive Full PaperDokument19 SeitenMabruk Jour Adaptive Full PapermgheryaniNoch keine Bewertungen
- Department of E.C.E.: Digital Communications Lab ManualDokument29 SeitenDepartment of E.C.E.: Digital Communications Lab Manualమొక్కపాటి మాధవిNoch keine Bewertungen
- TG10 2Dokument5 SeitenTG10 2m0hmdNoch keine Bewertungen
- Simulink-Based Simulation of Quadrature Amplitude Modulation (QAM) SystemDokument8 SeitenSimulink-Based Simulation of Quadrature Amplitude Modulation (QAM) SystemVeronica HansonNoch keine Bewertungen
- Performance Comparison of Wavelet Packet Modulation and OFDM Over Multipath Wireless Channel With Narrowband InterferenceDokument4 SeitenPerformance Comparison of Wavelet Packet Modulation and OFDM Over Multipath Wireless Channel With Narrowband Interferencesachin10dulkarNoch keine Bewertungen
- PSK Demodulation (Part 1)Dokument10 SeitenPSK Demodulation (Part 1)particlereddyNoch keine Bewertungen
- Poc Unit 3Dokument26 SeitenPoc Unit 3aashishscribdNoch keine Bewertungen
- On Opportunistic Power Control For MIMO-OFDM Systems: Norbert Reider G Abor FodorDokument6 SeitenOn Opportunistic Power Control For MIMO-OFDM Systems: Norbert Reider G Abor FodorMujeeb AbdullahNoch keine Bewertungen
- Improving MIMO Spectral Efficiency in 4G Macro-Cellular NetworksDokument6 SeitenImproving MIMO Spectral Efficiency in 4G Macro-Cellular Networksወንድሙ ዘገዬNoch keine Bewertungen
- High SNR Analysis For MIMO Broadcast Channels: Dirty Paper Coding vs. Linear PrecodingDokument33 SeitenHigh SNR Analysis For MIMO Broadcast Channels: Dirty Paper Coding vs. Linear Precodingkumaar1943Noch keine Bewertungen
- Coverage Optimization in Single Frequency Networks Using Simulated AnnealingDokument4 SeitenCoverage Optimization in Single Frequency Networks Using Simulated AnnealingJose Roberto Gonzales QuitoNoch keine Bewertungen
- On The Linear Representation of GMSK ModulationDokument14 SeitenOn The Linear Representation of GMSK ModulationIvanoNoch keine Bewertungen
- Adaptive MIMO Channel Estimation Using Sparse Variable Step-Size NLMS AlgorithmsDokument5 SeitenAdaptive MIMO Channel Estimation Using Sparse Variable Step-Size NLMS AlgorithmsManohar ReddyNoch keine Bewertungen
- Davide Cescato, Moritz Borgmann, Helmut Bölcskei, Jan Hansen, and Andreas BurgDokument5 SeitenDavide Cescato, Moritz Borgmann, Helmut Bölcskei, Jan Hansen, and Andreas BurgKhurram ShahzadNoch keine Bewertungen
- 5.0 Objectives:: MODULE-4&5 Sampling and QuantizationDokument19 Seiten5.0 Objectives:: MODULE-4&5 Sampling and QuantizationthasuplysmNoch keine Bewertungen
- Spatial Pulse Position Modulation For Optical CommunicationsDokument7 SeitenSpatial Pulse Position Modulation For Optical CommunicationsbelalassabiNoch keine Bewertungen
- Accurate Characterization of TWTA Distortion in Multicarrier Operation by Means of A Correlation-Based MethodDokument8 SeitenAccurate Characterization of TWTA Distortion in Multicarrier Operation by Means of A Correlation-Based MethodnaranjitoNoch keine Bewertungen
- 10 1 1 149Dokument5 Seiten10 1 1 149suspended22Noch keine Bewertungen
- Topic:: M-Ary PSK & M-Ary QAMDokument33 SeitenTopic:: M-Ary PSK & M-Ary QAMGita PatilNoch keine Bewertungen
- On Timing Offset and Frequency Offset Estimation in LTE UplinkDokument10 SeitenOn Timing Offset and Frequency Offset Estimation in LTE UplinkAjay SharmaNoch keine Bewertungen
- Analysis of Performance for MIMO Wireless Optical Comms SystemDokument18 SeitenAnalysis of Performance for MIMO Wireless Optical Comms SystemDITI SAI NAGA MAHESHNoch keine Bewertungen
- Micro Coded Transmitter DesignDokument14 SeitenMicro Coded Transmitter DesignJay SinghNoch keine Bewertungen
- M M M M M: M-Ary Orthogonal Modulation For Multi-Carrier Spread-Spectrum Uplink TransmissionDokument5 SeitenM M M M M: M-Ary Orthogonal Modulation For Multi-Carrier Spread-Spectrum Uplink TransmissionRahul KoshtaNoch keine Bewertungen
- Reduced Complexity Data-Aided and Code-Aided Frequency Offset Estimation For Flat-Fading MIMO ChannelsDokument10 SeitenReduced Complexity Data-Aided and Code-Aided Frequency Offset Estimation For Flat-Fading MIMO ChannelsSandeep SunkariNoch keine Bewertungen
- Lab1 Pulse Modulation FACETDokument5 SeitenLab1 Pulse Modulation FACETNabil Hilman Jaafar100% (1)
- A New Technique For Progressive ECG Transmission Using Discrete Radon TransformDokument6 SeitenA New Technique For Progressive ECG Transmission Using Discrete Radon TransformSanjana GaneshNoch keine Bewertungen
- Multiuser MIMO Downlink Transmission With BEM-based Limited Feedback Over Doubly Selective ChannelsDokument13 SeitenMultiuser MIMO Downlink Transmission With BEM-based Limited Feedback Over Doubly Selective ChannelsNguyen JustinNoch keine Bewertungen
- MIMO HSDPA Throughput Measurement Results in An Urban ScenarioDokument6 SeitenMIMO HSDPA Throughput Measurement Results in An Urban ScenarioAna Sofia FernandesNoch keine Bewertungen
- A14 Exp-3Dokument25 SeitenA14 Exp-3Chandra Sekhar KanuruNoch keine Bewertungen
- Large Margin Multi Channel Analog To Digital Conversion With Applications To Neural ProsthesisDokument8 SeitenLarge Margin Multi Channel Analog To Digital Conversion With Applications To Neural ProsthesisAdrian PostavaruNoch keine Bewertungen
- Volume4number5paper420 413Dokument6 SeitenVolume4number5paper420 413Ubiquitous Computing and Communication JournalNoch keine Bewertungen
- Overspread Digital Transmission Over Wireless Linear Time-Varying MIMO SystemsDokument13 SeitenOverspread Digital Transmission Over Wireless Linear Time-Varying MIMO SystemsRaghavendra Prasad ReddyNoch keine Bewertungen
- Ofdm Channel Estimation by Singular Value Decomposition: Abstract - A New Approach To Low-Complexity ChanDokument5 SeitenOfdm Channel Estimation by Singular Value Decomposition: Abstract - A New Approach To Low-Complexity ChanAlexandro PendosilioNoch keine Bewertungen
- Spline and Spline Wavelet Methods with Applications to Signal and Image Processing: Volume III: Selected TopicsVon EverandSpline and Spline Wavelet Methods with Applications to Signal and Image Processing: Volume III: Selected TopicsNoch keine Bewertungen
- Fundamentals of Electronics 3: Discrete-time Signals and Systems, and Quantized Level SystemsVon EverandFundamentals of Electronics 3: Discrete-time Signals and Systems, and Quantized Level SystemsNoch keine Bewertungen
- Image Super-Resolution Via Sparse RepresentationDokument13 SeitenImage Super-Resolution Via Sparse RepresentationvietbinhdinhNoch keine Bewertungen
- Cao2013 Miccai 0Dokument8 SeitenCao2013 Miccai 0marcniethammerNoch keine Bewertungen
- Lecture07 UmlDokument44 SeitenLecture07 Uml007wasrNoch keine Bewertungen
- Gaussian Mixture Models and EMDokument23 SeitenGaussian Mixture Models and EMvietbinhdinhNoch keine Bewertungen
- An Example of A Simulation 2d Ising Model With C++ PDFDokument10 SeitenAn Example of A Simulation 2d Ising Model With C++ PDFFrans Madah WauNoch keine Bewertungen
- Multivariate Normal DistributionDokument4 SeitenMultivariate Normal DistributionvietbinhdinhNoch keine Bewertungen
- Ising Model 1 PDFDokument22 SeitenIsing Model 1 PDFvietbinhdinh100% (1)
- EdgesDokument6 SeitenEdgesvietbinhdinhNoch keine Bewertungen
- DownloadDokument4 SeitenDownloadvietbinhdinhNoch keine Bewertungen
- WifiDokument1 SeiteWifivietbinhdinhNoch keine Bewertungen
- HowtouseGui sinMatLabDokument10 SeitenHowtouseGui sinMatLabvietbinhdinhNoch keine Bewertungen
- Real TOEFL iBT Speaking Test Questions From March 2005 Up To NowDokument6 SeitenReal TOEFL iBT Speaking Test Questions From March 2005 Up To NowvietbinhdinhNoch keine Bewertungen
- Barron's Gives Good Hints About How To Structure The Essay: BooksDokument3 SeitenBarron's Gives Good Hints About How To Structure The Essay: BooksvietbinhdinhNoch keine Bewertungen
- List of 1000 Most Common Words in EnglishDokument5 SeitenList of 1000 Most Common Words in EnglishvietbinhdinhNoch keine Bewertungen
- User 0000Dokument1 SeiteUser 0000vietbinhdinhNoch keine Bewertungen
- CMakeDokument18 SeitenCMakevietbinhdinhNoch keine Bewertungen
- Barron's Gives Good Hints About How To Structure The Essay: BooksDokument3 SeitenBarron's Gives Good Hints About How To Structure The Essay: BooksvietbinhdinhNoch keine Bewertungen
- CMake ListsDokument4 SeitenCMake ListsvietbinhdinhNoch keine Bewertungen
- Intro OGLDokument39 SeitenIntro OGLvietbinhdinhNoch keine Bewertungen
- CMake ListsDokument4 SeitenCMake ListsvietbinhdinhNoch keine Bewertungen
- Geo 5 User Guide enDokument1.431 SeitenGeo 5 User Guide enShahab KhaledNoch keine Bewertungen
- Chapter 3.4Dokument9 SeitenChapter 3.4Jhon Barzola PalominoNoch keine Bewertungen
- Notes 8Dokument45 SeitenNotes 8---Noch keine Bewertungen
- Tolerance Intervals For Any Data (Nonparametric)Dokument9 SeitenTolerance Intervals For Any Data (Nonparametric)scjofyWFawlroa2r06YFVabfbajNoch keine Bewertungen
- Cucconi TestDokument2 SeitenCucconi Testdev414Noch keine Bewertungen
- Mathematics for Business Students Worksheet No. 7 SolutionDokument6 SeitenMathematics for Business Students Worksheet No. 7 Solutionahmed wahshaNoch keine Bewertungen
- Documents - MX - Ps Work BooksolutionDokument39 SeitenDocuments - MX - Ps Work BooksolutionHaziq MansorNoch keine Bewertungen
- Chapter 2Dokument19 SeitenChapter 2TearlëşşSufíåñNoch keine Bewertungen
- DirectX Factor - Exploring Filters in XAudio2Dokument8 SeitenDirectX Factor - Exploring Filters in XAudio2Dorothy SaikiaNoch keine Bewertungen
- Chapter 3 2D Simulations GuideDokument23 SeitenChapter 3 2D Simulations GuideTran Van TienNoch keine Bewertungen
- Comp Neuro Syl Lab Us 2018Dokument3 SeitenComp Neuro Syl Lab Us 2018Andrej IlićNoch keine Bewertungen
- LectureDokument35 SeitenLectureSuvin NambiarNoch keine Bewertungen
- m2 Chapter 01 Introduction To MLDokument31 Seitenm2 Chapter 01 Introduction To MLHariom PandeyNoch keine Bewertungen
- BINOMIAL ML KhannaDokument5 SeitenBINOMIAL ML KhannaPavitra KukadiyaNoch keine Bewertungen
- ME 406 The Logistic Map: 1. IntroductionDokument32 SeitenME 406 The Logistic Map: 1. IntroductionsustrasNoch keine Bewertungen
- WME01 01 Rms 20200305 PDFDokument16 SeitenWME01 01 Rms 20200305 PDFAhmad BatranNoch keine Bewertungen
- What You Need From Analysis: Appendix ADokument31 SeitenWhat You Need From Analysis: Appendix ACarlos BifiNoch keine Bewertungen
- 02page SageDokument140 Seiten02page SageSergio MontesNoch keine Bewertungen
- Physics Gutka - Allen's 2021 Side BookDokument192 SeitenPhysics Gutka - Allen's 2021 Side BookDhyey PatelNoch keine Bewertungen
- Application of Machine Learning Techniques in Project ManagementDokument11 SeitenApplication of Machine Learning Techniques in Project ManagementRoderick PerezNoch keine Bewertungen
- Circle the correct math answers quizDokument10 SeitenCircle the correct math answers quizShukri AidahNoch keine Bewertungen
- 2.8 Index of Refraction LabDokument4 Seiten2.8 Index of Refraction LabsashaNoch keine Bewertungen
- ZTEC Instruments ZT - 4610-f - Dig Storage Scopes - Data Sheet PDFDokument16 SeitenZTEC Instruments ZT - 4610-f - Dig Storage Scopes - Data Sheet PDFchaparalNoch keine Bewertungen
- ცდომილებათა თეორიის ელემენტები - 1, თსუ, 2003Dokument3 Seitenცდომილებათა თეორიის ელემენტები - 1, თსუ, 2003Marina MenteshashviliNoch keine Bewertungen
- Name: - Date: - ScoreDokument2 SeitenName: - Date: - ScoreJoshua Escobar100% (1)
- Presentation McqsDokument2 SeitenPresentation McqsEngr Mujahid Iqbal100% (1)