Beruflich Dokumente
Kultur Dokumente
How To Configure Port Security Cisco
Hochgeladen von
Celia KingOriginalbeschreibung:
Originaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
How To Configure Port Security Cisco
Hochgeladen von
Celia KingCopyright:
Verfügbare Formate
How to configure port security in Cisco switch
In this article we would perform following task
Configuring the IP address and subnet mask Setting the IP default gateway Enable telnet session for switch Enable Ethereal Channel Enable port security
To perform this activity download this lab topology and load in packet tracer or create your own topology as shown in figure Switch Port Security
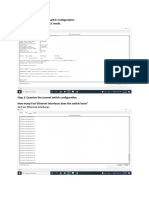
Configure IP address subnet mask and default gateway IP address and default gateway is used to configure switch remotely via telnet or SSH. Without this essential configurations you have connect with switch via console cable each time. That's very tedious as you have to go near to switch each time. Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#hostname S1
S1(config)#interface vlan 1 S1(config-if)#ip address 10.0.0.10 255.0.0.0 S1(config-if)#no shutdown %LINK-5-CHANGED: Interface Vlan1, changed state to up %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to up S1(config-if)#exit S1(config)#ip default-gateway 10.0.0.1 Enable Telnet and password protect the line You can secure a switch by using passwords to restrict various levels of access. Using passwords and assigning privilege levels are simple ways of providing both local and remote terminal access control in a network. Passwords can be established on individual lines, such as the console, and to the privileged EXEC (enable) mode. Passwords are case sensitive. By default There are five VTY ports on the switch, allowing five simultaneous Telnet sessions, noting that other Cisco devices might have more than five logical VTY ports. The five total VTY ports are numbered from 0 through 4 and are referred to all at once as line vty 0 4. S1(config)#line console 0 S1(config-line)#password vinita S1(config-line)#login S1(config-line)#exit S1(config)#line vty 0 4 S1(config-line)#password vinita S1(config-line)#login S1(config-line)#exit S1(config)# Enable Switch port security this feature set allows you (among several other options) to disable a port if more than one MAC address is detected as being connected to the port. This feature is commonly applied to ports that connect security-sensitive devices such as servers. You can use the port security feature to restrict input to an interface by limiting and identifying MAC addresses of the stations allowed to access the port.
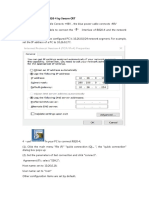
When you assign secure MAC addresses to a secure port, the port does not forward packets with source addresses outside the group of defined addresses. Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#hostname S2 S2(config)#interface fastEthernet 0/1 S2(config-if)#switchport mode access S2(config-if)#switchport port-security S2(config-if)#switchport port-security maximum 1 S2(config-if)#switchport port-security mac-address sticky S2(config-if)#switchport port-security violation shutdown S2(config-if)#exit S2(config)# You can verify port security.
Click on the red x button on the right hand portion of the PT window. This will allow you to delete a connection in the topology. Place the x over the connection between Server and S2 and click. The connection should disappear. Select the lightening bolt button on the bottom left-hand corner of the PT window to pull up connection types. Click the copper straight-through connection. Click the TestPC device and select the fastethernet port. Next, click on S2 and select port Fa0/1. From the command prompt of TestPC type the command ping 10.0.0.4. The ping should fail. On S3, enter the command show port-security interface fa0/1.
Port security is enabled, port-status is secure-shutdown, security violation count is 1.
Das könnte Ihnen auch gefallen
- How To Write A Technical ProposalDokument7 SeitenHow To Write A Technical ProposalMotasem AlMobayyed100% (1)
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationVon EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNoch keine Bewertungen
- q3 Basic CalculusDokument8 Seitenq3 Basic CalculusDon Aldrich SantosNoch keine Bewertungen
- Ajax CheatSheetDokument7 SeitenAjax CheatSheetdrypzNoch keine Bewertungen
- 6.5.1.1 Lab - Securing Layer 2 SwitchesDokument29 Seiten6.5.1.1 Lab - Securing Layer 2 Switchesxmaryta0% (2)
- Chapter 1 - Perspective DrawingDokument23 SeitenChapter 1 - Perspective DrawingChe Nora Che HassanNoch keine Bewertungen
- 2.3.3.4 Lab - Configuring A Switch Management Address - ILMDokument10 Seiten2.3.3.4 Lab - Configuring A Switch Management Address - ILMKevin KimNoch keine Bewertungen
- A Primer On A Good Instrument Grounding SystemDokument26 SeitenA Primer On A Good Instrument Grounding SystemwlmostiaNoch keine Bewertungen
- Library and Information ScienceDokument32 SeitenLibrary and Information Scienceneilesh300100% (2)
- GRE Prep ClubDokument3 SeitenGRE Prep ClubHarris IjazNoch keine Bewertungen
- How To Configure Cisco Switches - A Step by Step Guide - ComparitechDokument12 SeitenHow To Configure Cisco Switches - A Step by Step Guide - ComparitechAbcxyz XyzabcNoch keine Bewertungen
- Cisco Router Basic Network ConfigurationDokument42 SeitenCisco Router Basic Network ConfigurationMitraNoch keine Bewertungen
- Configuring Dell EMC Networking S5248F-On SwitchesDokument6 SeitenConfiguring Dell EMC Networking S5248F-On SwitchesthienvugcsNoch keine Bewertungen
- Easy Mikrotik HotSpot SetupDokument5 SeitenEasy Mikrotik HotSpot SetupBoy EloadNoch keine Bewertungen
- ESwitching Lab 5 5 2Dokument20 SeitenESwitching Lab 5 5 2Ninja NuggetNoch keine Bewertungen
- 2.3.3.5 Lab - Configuring A Switch Management AddressDokument8 Seiten2.3.3.5 Lab - Configuring A Switch Management AddressNicolas Bonina33% (3)
- Cisco Lab AnswersDokument20 SeitenCisco Lab AnswersNada Nader El-ibiary100% (1)
- Lab Cisco Packet TracerDokument17 SeitenLab Cisco Packet TracerPeter KaboreNoch keine Bewertungen
- Packet Tracer LABDokument38 SeitenPacket Tracer LABAsamiYamanakaNoch keine Bewertungen
- Switchport Port Security Explained With ExamplesDokument10 SeitenSwitchport Port Security Explained With ExamplesAyush UppalNoch keine Bewertungen
- Basic Command of Extreme SwitchDokument5 SeitenBasic Command of Extreme Switchykatiuska33% (3)
- Basic Config Guide For OCLAN Switch Ver 3 0Dokument11 SeitenBasic Config Guide For OCLAN Switch Ver 3 0anoop.ashu9376Noch keine Bewertungen
- SAP Data Migration - LTMOM - LSMW Vs LTMC S/4 HanaDokument10 SeitenSAP Data Migration - LTMOM - LSMW Vs LTMC S/4 HanaamferrazziNoch keine Bewertungen
- Lab3 - InstructorDokument10 SeitenLab3 - InstructorCelia King0% (1)
- Configure Switch Security: Addressing TableDokument5 SeitenConfigure Switch Security: Addressing TableguillcrNoch keine Bewertungen
- SwitchDokument6 SeitenSwitchAlex NeukomNoch keine Bewertungen
- SWITCHING CONFIGURATION BASICS Switch enDokument7 SeitenSWITCHING CONFIGURATION BASICS Switch enSINDA ZINE EL ABIDINENoch keine Bewertungen
- Technical Document Cisco 2960G, 2960S, and 2960X Configuration For Wheatnet-IpDokument6 SeitenTechnical Document Cisco 2960G, 2960S, and 2960X Configuration For Wheatnet-IpRaneesh RamesanNoch keine Bewertungen
- CNs-Lab 9-Cisco Switch ConfigurationDokument8 SeitenCNs-Lab 9-Cisco Switch ConfigurationHemin EssaNoch keine Bewertungen
- 2.2.4.9 Packet Tracer - Configuring Switch Port Security Instructions - IGDokument7 Seiten2.2.4.9 Packet Tracer - Configuring Switch Port Security Instructions - IGJefferOrtizGonzalezNoch keine Bewertungen
- Lab2 - Configuring A Switch Management Address: TopologyDokument8 SeitenLab2 - Configuring A Switch Management Address: Topologymabrouka gmidenNoch keine Bewertungen
- Basic Switch/Router Configuration & Security (Ref Chapter 9 - ICND1)Dokument26 SeitenBasic Switch/Router Configuration & Security (Ref Chapter 9 - ICND1)Kevin SleightNoch keine Bewertungen
- Lab 7-1 Configuring Switches For IP Telephony Support: Learning ObjectivesDokument22 SeitenLab 7-1 Configuring Switches For IP Telephony Support: Learning Objectivesvishal tatwadeNoch keine Bewertungen
- 2.3.3.4 Lab - Configuring A Switch Management AddressDokument9 Seiten2.3.3.4 Lab - Configuring A Switch Management AddressIchwan Habibie20% (5)
- (Router Name) (Encrypted Privileged Exec Password)Dokument7 Seiten(Router Name) (Encrypted Privileged Exec Password)Mouhamad BazziNoch keine Bewertungen
- Cisco 1-And 2-Port T1/E1 Multiflex Voice/WAN Interface Cards For The Cisco 1721 RouterDokument24 SeitenCisco 1-And 2-Port T1/E1 Multiflex Voice/WAN Interface Cards For The Cisco 1721 Routerluiscastillo7Noch keine Bewertungen
- Lab Switching RouterDokument31 SeitenLab Switching RouteremersonNoch keine Bewertungen
- CCNP3 Lab 4 1 enDokument10 SeitenCCNP3 Lab 4 1 enmanucvNoch keine Bewertungen
- Task 1: Verify The Default Switch Configuration Step 1: Enter Privileged EXEC ModeDokument20 SeitenTask 1: Verify The Default Switch Configuration Step 1: Enter Privileged EXEC ModeAdnan YousafNoch keine Bewertungen
- DocumentoDokument33 SeitenDocumentoMaria AlvaradoNoch keine Bewertungen
- How To Configure VLAN, STP, DTP Step by Step Guide?Dokument9 SeitenHow To Configure VLAN, STP, DTP Step by Step Guide?sivachandran kaliappanNoch keine Bewertungen
- Port SecDokument8 SeitenPort SecNocvato MalioNoch keine Bewertungen
- CCNA Configuring Switch InterfacesDokument7 SeitenCCNA Configuring Switch InterfacesMin Min ZawNoch keine Bewertungen
- Topic 7D. Lab - Basic Configuration of A CISCO SwitchDokument5 SeitenTopic 7D. Lab - Basic Configuration of A CISCO SwitchsimonnjauNoch keine Bewertungen
- CN Lab ManualDokument64 SeitenCN Lab Manualprateekshekhawat395Noch keine Bewertungen
- Lab 4-1 Configuring Expanded Switched NetworksDokument13 SeitenLab 4-1 Configuring Expanded Switched NetworksTONGUINONoch keine Bewertungen
- TelnetDokument18 SeitenTelnetDebadutta NayakNoch keine Bewertungen
- Configuring A Terminal Comm ServerDokument7 SeitenConfiguring A Terminal Comm Serverbingo2kNoch keine Bewertungen
- Configuracion de Un SwitchDokument6 SeitenConfiguracion de Un SwitchwillyNoch keine Bewertungen
- Lab 5Dokument12 SeitenLab 5Tomas Rodriguez RamirezNoch keine Bewertungen
- CN Lab FileDokument59 SeitenCN Lab Filens7410501Noch keine Bewertungen
- Lecture 37 Prot SecurityDokument10 SeitenLecture 37 Prot Securitykamilbaba2241Noch keine Bewertungen
- CCN Lab ManualDokument28 SeitenCCN Lab ManualMuhammad Usman NasirNoch keine Bewertungen
- Commands For Ccna 3 4 LabDokument8 SeitenCommands For Ccna 3 4 LabibrarzamanNoch keine Bewertungen
- CISCO Basic CommandsDokument2 SeitenCISCO Basic CommandsGit EtcNoch keine Bewertungen
- 2.2.4.11 Lab - Configuring Switch Security Features - ScribdDokument9 Seiten2.2.4.11 Lab - Configuring Switch Security Features - ScribdstevehrccNoch keine Bewertungen
- PT Activity 4.4.1: Basic VTP Configuration: Topology DiagramDokument8 SeitenPT Activity 4.4.1: Basic VTP Configuration: Topology Diagramangel_of_love31290Noch keine Bewertungen
- 26.1.3 Lab - Configure Protections For Passwords and Terminal Lines - ILMDokument20 Seiten26.1.3 Lab - Configure Protections For Passwords and Terminal Lines - ILMAndrei Petru PârvNoch keine Bewertungen
- 3.2.2.4 LabDokument7 Seiten3.2.2.4 LabSamuelAbateSimmonsNoch keine Bewertungen
- Module 1 - Basic Device ConfigurationDokument51 SeitenModule 1 - Basic Device ConfigurationfayNoch keine Bewertungen
- Interface Configuration en Cisco SwitchesDokument34 SeitenInterface Configuration en Cisco SwitchesnethursNoch keine Bewertungen
- VnPro - 9. Starting A SwitchDokument37 SeitenVnPro - 9. Starting A SwitchTrần Hà MyNoch keine Bewertungen
- Lab 3.10.2 Use Network Inspector To Observe STP Behavior: ObjectiveDokument12 SeitenLab 3.10.2 Use Network Inspector To Observe STP Behavior: ObjectiveKishore Reddy KandiNoch keine Bewertungen
- Configure Protections For Passwords and Terminal LinesDokument10 SeitenConfigure Protections For Passwords and Terminal Linescesar javierNoch keine Bewertungen
- Topic 7A. Configuring A CISCO IOS SwitchDokument20 SeitenTopic 7A. Configuring A CISCO IOS SwitchsimonnjauNoch keine Bewertungen
- Cis188 8 ConvergedNetworks Part2Dokument103 SeitenCis188 8 ConvergedNetworks Part2agaver2Noch keine Bewertungen
- SwitchDokument13 SeitenSwitchma7522nigamNoch keine Bewertungen
- First How To Login R820-4 by Secure CRTDokument5 SeitenFirst How To Login R820-4 by Secure CRTHaris YiztNoch keine Bewertungen
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksVon EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNoch keine Bewertungen
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkVon EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNoch keine Bewertungen
- Ipv 6Dokument9 SeitenIpv 6Celia KingNoch keine Bewertungen
- Sba D3Dokument5 SeitenSba D3Celia KingNoch keine Bewertungen
- Lab4 - InstructorDokument5 SeitenLab4 - InstructorCelia KingNoch keine Bewertungen
- Ipv6 GraphicDokument6 SeitenIpv6 GraphicCelia KingNoch keine Bewertungen
- D3 - Ospf - Acl - Oct 31Dokument4 SeitenD3 - Ospf - Acl - Oct 31Celia KingNoch keine Bewertungen
- 03 CidrDokument20 Seiten03 CidrCelia KingNoch keine Bewertungen
- Lab 1 - Ipv6Dokument2 SeitenLab 1 - Ipv6Celia KingNoch keine Bewertungen
- Lab 2 - Ipv6 - EigrpDokument2 SeitenLab 2 - Ipv6 - EigrpCelia KingNoch keine Bewertungen
- IPv6 Static RoutesDokument16 SeitenIPv6 Static RoutesCelia KingNoch keine Bewertungen
- Ipv6 - Lab4Dokument3 SeitenIpv6 - Lab4Celia KingNoch keine Bewertungen
- CCNA Discovery 2 Practice Final Incorrect SolutionsDokument2 SeitenCCNA Discovery 2 Practice Final Incorrect SolutionsCelia KingNoch keine Bewertungen
- Ipv 6Dokument9 SeitenIpv 6Celia KingNoch keine Bewertungen
- IPv6 Static RoutesDokument16 SeitenIPv6 Static RoutesCelia KingNoch keine Bewertungen
- CCNA Discovery 4 Working at A Small To Medium Business or ISP Student Lab ManualDokument117 SeitenCCNA Discovery 4 Working at A Small To Medium Business or ISP Student Lab Manualdaltons_au100% (3)
- VirtualDJ 7 - Audio Setup GuideDokument29 SeitenVirtualDJ 7 - Audio Setup GuideLek ChongNoch keine Bewertungen
- VirtualDJ 7 - Getting Started PDFDokument11 SeitenVirtualDJ 7 - Getting Started PDFSanthia MoralesNoch keine Bewertungen
- Class B Magic NumberDokument3 SeitenClass B Magic NumberthecirclemasterNoch keine Bewertungen
- Crosswalk For CCNA 2 Labs and ActivitiesDokument56 SeitenCrosswalk For CCNA 2 Labs and Activitiesnobvisal0% (1)
- The Purpose of This Sim Is StraightforwardDokument2 SeitenThe Purpose of This Sim Is StraightforwardCelia KingNoch keine Bewertungen
- CCNA Discovery 4 Working at A Small To Medium Business or ISP Student Lab ManualDokument117 SeitenCCNA Discovery 4 Working at A Small To Medium Business or ISP Student Lab Manualdaltons_au100% (3)
- Lab 9.4.2 Correcting RIPv2 Routing ProblemsDokument13 SeitenLab 9.4.2 Correcting RIPv2 Routing ProblemsCelia KingNoch keine Bewertungen
- William Dafoe PoemDokument1 SeiteWilliam Dafoe PoemCelia KingNoch keine Bewertungen
- Discovery 1 Chapter 3 NotesDokument1 SeiteDiscovery 1 Chapter 3 NotesCelia KingNoch keine Bewertungen
- TV Show ListDokument1 SeiteTV Show ListCelia KingNoch keine Bewertungen
- D2 SBA StudentDokument9 SeitenD2 SBA Studentcyber_koNoch keine Bewertungen
- OSI Model For Cisco NetworkingDokument1 SeiteOSI Model For Cisco NetworkingCelia KingNoch keine Bewertungen
- Basic Cisco OS CommandsDokument5 SeitenBasic Cisco OS CommandsCelia KingNoch keine Bewertungen
- Packet Tracer 9.6.5.5 - Router CommandsDokument7 SeitenPacket Tracer 9.6.5.5 - Router CommandsCelia KingNoch keine Bewertungen
- C++11 Is A Version of The Standard For The ProgrammingDokument56 SeitenC++11 Is A Version of The Standard For The ProgrammingYvzNoch keine Bewertungen
- Dcit 26 ReviewerDokument8 SeitenDcit 26 ReviewerHunter KurusakiNoch keine Bewertungen
- Power Electronics Homework SolutionsDokument5 SeitenPower Electronics Homework Solutionsafnabzdmfiefxr100% (1)
- Man Inst Mru 5 r9Dokument148 SeitenMan Inst Mru 5 r9Miguel Martinez100% (1)
- CH 1Dokument24 SeitenCH 1Chew Ting LiangNoch keine Bewertungen
- Pioneer HDD/DVD Recorder DVR-550H-SDokument142 SeitenPioneer HDD/DVD Recorder DVR-550H-SdesNoch keine Bewertungen
- Skybox Security Best Practices Migrating Next-Gen Firewalls EN PDFDokument3 SeitenSkybox Security Best Practices Migrating Next-Gen Firewalls EN PDFsysdhanabalNoch keine Bewertungen
- Acer Iconia Tab A500 Service ManualDokument199 SeitenAcer Iconia Tab A500 Service Manualpsy1100de4751Noch keine Bewertungen
- VHDL Code For Updown CNTDokument3 SeitenVHDL Code For Updown CNTmeaow88100% (2)
- Lifting Points Brochure E1Dokument108 SeitenLifting Points Brochure E1tintucinbNoch keine Bewertungen
- 16BIT0056 - Implementing Two Stacks PDFDokument4 Seiten16BIT0056 - Implementing Two Stacks PDFSai Ganesh ReddyNoch keine Bewertungen
- BRO ASD535-532-531 en PDFDokument6 SeitenBRO ASD535-532-531 en PDFArman Ul NasarNoch keine Bewertungen
- Jurnal Internasional XiaomiDokument16 SeitenJurnal Internasional Xiaomipoppy hidayahNoch keine Bewertungen
- Personal IdentificationDokument15 SeitenPersonal IdentificationMASLA ZAINORNoch keine Bewertungen
- 001-65209 AN65209 Getting Started With FX2LPDokument27 Seiten001-65209 AN65209 Getting Started With FX2LPanacer55Noch keine Bewertungen
- Handwritten Text Recognition Using Deep LearningDokument13 SeitenHandwritten Text Recognition Using Deep LearningHarini MurugananthamNoch keine Bewertungen
- CivicrmDokument361 SeitenCivicrmmandohNoch keine Bewertungen
- Introduction To VLSI Design EEE 416: Dr. Mohammad Al HakimDokument23 SeitenIntroduction To VLSI Design EEE 416: Dr. Mohammad Al HakimMizanur Rahman SujanNoch keine Bewertungen
- Special Documentation Proline Promass 500 FOUNDATION FieldbusDokument52 SeitenSpecial Documentation Proline Promass 500 FOUNDATION Fieldbuspaula marambioNoch keine Bewertungen
- TWIDO-TWD LCAE 40DRF DocumentDokument8 SeitenTWIDO-TWD LCAE 40DRF DocumentA MNoch keine Bewertungen
- 200 Questions OMR Sheet 1Dokument1 Seite200 Questions OMR Sheet 1donNoch keine Bewertungen