Beruflich Dokumente
Kultur Dokumente
COMP 8531 Final Exam
Hochgeladen von
Minh-Ha LeCopyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
COMP 8531 Final Exam
Hochgeladen von
Minh-Ha LeCopyright:
Verfügbare Formate
COMP 8531 Final Exam
Harvey Le (A00811495) Instructor: Tejinder Randhawa Part 1 1. Enhanced Distributed Channel Access (EDCA) HCF Control Channel Access (HCCA) 2. HCCA is more suitable for real time applications because its an asynchronous real time scheduler 3. The 802.11b standard consists of a Distributed Coordination Function (DCF), which coordinated the usage of medium via the use of CSMA/SA Since multiple stations are connected and connections are full duplex, CSMA/CA should be employed in 802.11b 4. In 802.11b standard, SIFS is Short Inter Frame Spacing, which is the amount of time a station must wait before sending or starting to receive a RTS/ CTS or ACK, DIFS is Distributed IFS, which is the amount of time a station must wait before sense a clear radio before starting a new transmission sequence and PIFS is Point Coordination IFS, which is the DIFS for the access point in a special access method (Point Coordination Function) The reason for a packet to be transmitted after SIFS, DIFS or PIFS is that when the MAC receives a request for transmission, the medium is checked by the physical and virtual Carrier Sense mechanisms. If all of them indicate an idle medium, which is required, for a period of DIFS, SIFS or PIFS, then the transmissions are allowed to begin 5. RTS/CTS is employed because in a particular station, it will prevent that station from sending a data frame to another different station until the current handshake with the current station is completed Another reason for RTS/CTS to be employed is that it can minimize collision among hidden stations 6. The provisions exist in 802.11e for QoS support are DCF (Distributed Coordination Function) Part 2 1. In a Bluetooth piconet, a master is the one who controls the communication. Therefore, slaves are devices connected with the master 2. Up to 7 slaves are allowed for a master
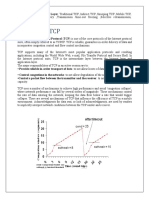
3. A Bluetooth piconet can allow up to 7 simultaneously active slave devices or 255 slave devices in parked mode 4. A master of a piconet can only be a slave for another master in another piconet, cannot be a master. Part 3 1. The time for the node to wait is d = l/R where l is the distance between that node and node V, R is the Part 4 1. An example for necessitating fast indexing schemes for LBS involving moving objects is that most moving objects are constantly changing their position and submitting request to a database, which can reduce system performance. Thus, fast indexing mechanisms are needed 2. The main advantage of IMORS over TPR tree is that the update cost is about 40% less Part 5 1. TCP was initially designed and implemented for wired networks. Thus, in wireless networks, whose one characteristic is congestions or noise, TCP performance reduces. When congestions and transmission errors occur, the link-layer mechanisms will recover the losses, which are caused by transmission errors, and the transport protocol will recover the losses that are caused by congestions 2. In TCP-DCR, the response to the duplicate acknowledgements is delayed by a short period (T). If the packet is recovered by link-level retransmission before the end of T, TCP-DCR will proceed as if the packet loss never occurred. However, if the packet is not recovered by the end of T, TCP-DCR will start the congestion recovery algorithms of fast retransmission and recovery. Part 6 1. TCP Friendly Rate Control (TFRC): The receiver measures the loss event rate and send this information back to the sender. The the sender uses the feedback messages to measure the round-trip time (RTT). The loss event rate and RTT are fed into TFRCs throughput equation, giving the acceptable transmit rate. Finally, the sender adjusts its transmit rate to match the calculated rate. Multiple TFRC (MULTFRC): This approach is to measure the round-trip time (RTT) and adjust the number of connections accordingly to utilize the wireless bandwidth efficiently and ensure fairness between applications.
Part 7 1. An example of serializability: Lets consider we have 3 bank accounts (A, B, C). There are 2 transactions: first is to transfer 100 from A to B and second to to transfer 100 from A to C. A schedule that is considered serializable should be like this Transaction 1 will be done first Read (A, t) t = t - 100 Write (A, t) Read (B, t) t = t + 100 Write (B, t) Then transaction 2 starts Read (A, s) s = s - 100 Write (A, s) Read (C, s) s = s +100 Write (C, s) Those steps above must be done correctly, they are not allowed to overlap 2. The key issue relates to 2-tier replication, which allows user to run transactions locally and when user connects to server, those transactions will be re-executed at servers. The problem is user executes transactions without knowing other transactions are doing and this can lead to a huge number of transaction rejections
Das könnte Ihnen auch gefallen
- Enhanced Backoff Scheme in CSMA/CA For IEEE 802.11: Wen-Kuang Kuo and C.-C. Jay KuoDokument5 SeitenEnhanced Backoff Scheme in CSMA/CA For IEEE 802.11: Wen-Kuang Kuo and C.-C. Jay KuoKawthar HedNoch keine Bewertungen
- TCP vs UDP: Key Differences ExplainedDokument14 SeitenTCP vs UDP: Key Differences ExplainedShivam NarkhedeNoch keine Bewertungen
- Opnetwork03 WanDokument7 SeitenOpnetwork03 WanHán LaNoch keine Bewertungen
- QoS in 802.11Dokument11 SeitenQoS in 802.11abeera ilyasNoch keine Bewertungen
- Abstract Speaking of Wireless LAN, The General Thought Is AboutDokument7 SeitenAbstract Speaking of Wireless LAN, The General Thought Is AboutSivaguru GurusivaNoch keine Bewertungen
- مصطفى نتوورك PDFDokument9 Seitenمصطفى نتوورك PDFBassam AlmunagemNoch keine Bewertungen
- Transport Layer Provides Reliable Data TransferDokument22 SeitenTransport Layer Provides Reliable Data TransferAnantharaj ManojNoch keine Bewertungen
- Bi An Chi 1996Dokument5 SeitenBi An Chi 1996Rajesh ECNoch keine Bewertungen
- A Throughput Analysis of TCP in ADHOC NetworksDokument8 SeitenA Throughput Analysis of TCP in ADHOC NetworksCS & ITNoch keine Bewertungen
- Module 3Dokument79 SeitenModule 3udayNoch keine Bewertungen
- Network Management 001Dokument7 SeitenNetwork Management 001Gourav BansalNoch keine Bewertungen
- Enhanced Transaction TCP-Design and Implementation: 1.1 What Is T/TCP 1.2 Why T/TCPDokument10 SeitenEnhanced Transaction TCP-Design and Implementation: 1.1 What Is T/TCP 1.2 Why T/TCPJetesh DevgunNoch keine Bewertungen
- TCP Performance Over Satellite in Case of Multiple Sessions Per Links Using Efficient Flow Control and Real OSDokument8 SeitenTCP Performance Over Satellite in Case of Multiple Sessions Per Links Using Efficient Flow Control and Real OSPunya ShreeNoch keine Bewertungen
- TranskateDokument7 SeitenTranskateSeptian MuktiNoch keine Bewertungen
- UNIT 2 CNDokument35 SeitenUNIT 2 CNmsk.official321Noch keine Bewertungen
- Computer Networks Assignment QuestionsDokument8 SeitenComputer Networks Assignment Questionsmayank27jaitly100% (1)
- TCP IP Over Satellite - Yi ZhangDokument8 SeitenTCP IP Over Satellite - Yi ZhangAhmadHambaliNoch keine Bewertungen
- Unit 4 NotesDokument20 SeitenUnit 4 NotesUmapathi Pawar SNoch keine Bewertungen
- Mobile IP performance and optimizationsDokument8 SeitenMobile IP performance and optimizationsBintang Mandala PutraNoch keine Bewertungen
- NWC203c PE23Dokument4 SeitenNWC203c PE23hayhe2910Noch keine Bewertungen
- Turning Hidden Nodes Into Helper Nodes in IEEE 802.11 Wireless LAN NetworksDokument12 SeitenTurning Hidden Nodes Into Helper Nodes in IEEE 802.11 Wireless LAN NetworksphdmadhuNoch keine Bewertungen
- Datocom AnswersDokument11 SeitenDatocom AnswersHalefom DestaNoch keine Bewertungen
- Data Link QuestionDokument7 SeitenData Link QuestionAhmed Aziz SultanNoch keine Bewertungen
- Lecture 11Dokument17 SeitenLecture 11تُحف العقولNoch keine Bewertungen
- Indirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerDokument12 SeitenIndirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerMukesh91% (220)
- Dynamic Contention Window For Quality of Service in IEEE 802.11 NetworksDokument5 SeitenDynamic Contention Window For Quality of Service in IEEE 802.11 NetworksLiyang ChangNoch keine Bewertungen
- Flow Control Methods for Data NetworksDokument7 SeitenFlow Control Methods for Data NetworksBassam AlmunagemNoch keine Bewertungen
- Priority TX in 802 - 11Dokument19 SeitenPriority TX in 802 - 11Manuel ChawNoch keine Bewertungen
- Mobile TCPDokument7 SeitenMobile TCPTUSHARNoch keine Bewertungen
- A Comparison of Techniques For Improving TCP Performance Over Wireless LinksDokument4 SeitenA Comparison of Techniques For Improving TCP Performance Over Wireless LinksMuthu Vijay DeepakNoch keine Bewertungen
- Methods To Improve TCP Throughput in Wireless Networks With High Delay VariabilityDokument5 SeitenMethods To Improve TCP Throughput in Wireless Networks With High Delay Variabilityamitkumargarg88Noch keine Bewertungen
- Digital Flow ControlDokument7 SeitenDigital Flow Controlyash patelNoch keine Bewertungen
- LIMITED AND DIRECTED IPv4 BROADCAST ADDRESSESDokument3 SeitenLIMITED AND DIRECTED IPv4 BROADCAST ADDRESSESGiuseppe FerrariNoch keine Bewertungen
- Cs601 Unit VDokument20 SeitenCs601 Unit VRekha RahangdaleNoch keine Bewertungen
- TCP Performance Enhancement Over UMTS Network With RNC FeedbackDokument6 SeitenTCP Performance Enhancement Over UMTS Network With RNC FeedbackumtsrfNoch keine Bewertungen
- Transport Layer STDDokument8 SeitenTransport Layer STDMd Habibur RahmanNoch keine Bewertungen
- MODEL HOME WORK --- 3: CSMA/CA AdvantagesDokument6 SeitenMODEL HOME WORK --- 3: CSMA/CA AdvantagesKritesh ThakurNoch keine Bewertungen
- Computer Networks FundamentalDokument7 SeitenComputer Networks FundamentalThomas Kofi AnnanNoch keine Bewertungen
- Unit 5 Final NotesDokument20 SeitenUnit 5 Final Notesappsectesting3Noch keine Bewertungen
- MC Unit 4Dokument28 SeitenMC Unit 4Naveenkumar TariNoch keine Bewertungen
- TCP TraficDokument82 SeitenTCP TraficAdv Antony JudeNoch keine Bewertungen
- 4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDokument16 Seiten4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDr. Sashi Kanth Reddy ANoch keine Bewertungen
- Performance Anomaly of 802.11b: Martin Heusse, Franck Rousseau, Gilles Berger-Sabbatel, Andrzej DudaDokument8 SeitenPerformance Anomaly of 802.11b: Martin Heusse, Franck Rousseau, Gilles Berger-Sabbatel, Andrzej DudaTanvir AhmedNoch keine Bewertungen
- Part 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersDokument6 SeitenPart 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersKani MozhiNoch keine Bewertungen
- Unit 4Dokument18 SeitenUnit 4Manasa PNoch keine Bewertungen
- Transport Layer Protocols For Ad-Hoc NetworksDokument29 SeitenTransport Layer Protocols For Ad-Hoc NetworksShachi P GowdaNoch keine Bewertungen
- TCP/IP Protocols ExplainedDokument8 SeitenTCP/IP Protocols Explainedkavas26Noch keine Bewertungen
- Data and Computer CommunicationsDokument66 SeitenData and Computer CommunicationsHarsh VivekNoch keine Bewertungen
- Approaches To Support Real Time TrafficDokument4 SeitenApproaches To Support Real Time TrafficJason HouseNoch keine Bewertungen
- WifiDokument29 SeitenWifiSreedevi BalasubramanianNoch keine Bewertungen
- Transport Layer Challenges By: Talha Mudassar 015 Fahad Nabi 63 Rashid Mehmood 96Dokument6 SeitenTransport Layer Challenges By: Talha Mudassar 015 Fahad Nabi 63 Rashid Mehmood 96Noman AliNoch keine Bewertungen
- Performance Modelling HARQ LTEDokument6 SeitenPerformance Modelling HARQ LTEtrainingmomentNoch keine Bewertungen
- TCP Over AtmDokument19 SeitenTCP Over AtmAnonymous Ie0oEXP2eNoch keine Bewertungen
- Overview of IEEE 802.11 WLANDokument18 SeitenOverview of IEEE 802.11 WLANmanai raghavNoch keine Bewertungen
- Overview of IEEE 802.11 WLANDokument19 SeitenOverview of IEEE 802.11 WLANmanai raghavNoch keine Bewertungen
- NS simulation implementing Large Window over TCP SACKDokument5 SeitenNS simulation implementing Large Window over TCP SACKElizabeth FlowersNoch keine Bewertungen
- LTE Signaling: Troubleshooting and Performance MeasurementVon EverandLTE Signaling: Troubleshooting and Performance MeasurementNoch keine Bewertungen
- CCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesVon EverandCCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesNoch keine Bewertungen
- Introduction to Internet & Web Technology: Internet & Web TechnologyVon EverandIntroduction to Internet & Web Technology: Internet & Web TechnologyNoch keine Bewertungen
- DIGITAL MEDIA PIRACY DEBATEDokument12 SeitenDIGITAL MEDIA PIRACY DEBATEMinh-Ha LeNoch keine Bewertungen
- Cruise Control System Software DevelopmentDokument14 SeitenCruise Control System Software DevelopmentMinh-Ha LeNoch keine Bewertungen
- The Cost of Media PiracyDokument11 SeitenThe Cost of Media PiracyMinh-Ha LeNoch keine Bewertungen
- Lecture 1 - IntroductionDokument77 SeitenLecture 1 - IntroductionMinh-Ha LeNoch keine Bewertungen
- MODULE 2A - Practical Research 1 (STEM) : Name: Grade Level/Section: Subject TeacherDokument6 SeitenMODULE 2A - Practical Research 1 (STEM) : Name: Grade Level/Section: Subject Teacheryhajj jamesNoch keine Bewertungen
- CICS TuninngDokument53 SeitenCICS TuninngMrLouisCypherNoch keine Bewertungen
- BPC 4 EUM PS Project VersionDokument37 SeitenBPC 4 EUM PS Project VersionsherubdNoch keine Bewertungen
- Introduction to SQLDokument74 SeitenIntroduction to SQLGaurav GuptaNoch keine Bewertungen
- STS Third Party Protocols SupportDokument51 SeitenSTS Third Party Protocols Supportkobikon100% (1)
- FIFA Mod Manager Log20211017 - 001Dokument5 SeitenFIFA Mod Manager Log20211017 - 001Felipe CortesNoch keine Bewertungen
- Expl WAN Chapter 1 Intro WANsDokument82 SeitenExpl WAN Chapter 1 Intro WANsLeo LaguiNoch keine Bewertungen
- ADO Excel CodesDokument13 SeitenADO Excel CodesSayed DarwishNoch keine Bewertungen
- Enc 1102 Reflective EssayDokument4 SeitenEnc 1102 Reflective Essayapi-607105333Noch keine Bewertungen
- CIS Module 2 Classic Data CenterDokument100 SeitenCIS Module 2 Classic Data CenterberrezegNoch keine Bewertungen
- A Review of Artificial Intelligence Methods For Engineering Prognostics and Health Management With Implementation GuidelinesDokument51 SeitenA Review of Artificial Intelligence Methods For Engineering Prognostics and Health Management With Implementation Guidelinesmarwa jmaiNoch keine Bewertungen
- Chapter 13 Managing The Systems Development Life CycleDokument36 SeitenChapter 13 Managing The Systems Development Life Cyclekristine mediavilloNoch keine Bewertungen
- Chapter 1 KsfeDokument5 SeitenChapter 1 Ksfeanon_360578830Noch keine Bewertungen
- Savable Data Page - Its Configuration, Usage & ExecutionDokument20 SeitenSavable Data Page - Its Configuration, Usage & ExecutionsurmanpaNoch keine Bewertungen
- Crystals PDFDokument164 SeitenCrystals PDFJoydip JoydipNoch keine Bewertungen
- Class Presentation BtreeDokument15 SeitenClass Presentation BtreeVipin BhagatNoch keine Bewertungen
- Social Networking and Analyzing DataDokument6 SeitenSocial Networking and Analyzing Dataapi-326620154Noch keine Bewertungen
- Customer Satisfaction Regarding Nivea Products - 211210 - 151844Dokument70 SeitenCustomer Satisfaction Regarding Nivea Products - 211210 - 151844HaniyaNoch keine Bewertungen
- Time Dependent Processing in A Parallel Pipeline ArchitectureDokument8 SeitenTime Dependent Processing in A Parallel Pipeline ArchitectureSnakeNRNoch keine Bewertungen
- Sync 2000Dokument2 SeitenSync 2000osto72Noch keine Bewertungen
- DDN GRIDScaler ProductFamily Datasheet v13Dokument2 SeitenDDN GRIDScaler ProductFamily Datasheet v13Cleime CorderoNoch keine Bewertungen
- Performance Tuning: Eliminate Source and Target Database BottlenecksDokument11 SeitenPerformance Tuning: Eliminate Source and Target Database BottlenecksSannat ChouguleNoch keine Bewertungen
- Chapter 1Dokument40 SeitenChapter 1Andrea AtonducanNoch keine Bewertungen
- Arne & Jeffress 2014 Sampling and Analysis For Public Reporting of Portable X-Ray Fluorescence Data Under The 2012 Edition of The JORC CodeDokument8 SeitenArne & Jeffress 2014 Sampling and Analysis For Public Reporting of Portable X-Ray Fluorescence Data Under The 2012 Edition of The JORC CodenagitankaNoch keine Bewertungen
- Transaction: Controlling Concurrent BehaviorDokument63 SeitenTransaction: Controlling Concurrent BehaviorPhan Chi BaoNoch keine Bewertungen
- Database For SQLCommandDokument1 SeiteDatabase For SQLCommandDevansh PandeyNoch keine Bewertungen
- Acfrogdtvu6zlyfry8-Jlk3gvpwxqgfxoqhrqzvdwvnipoybrtyke4bifddfinh7o Ec Aclwenwpg6qtny6cx-Huxzfiacj2es6inejvwwasbchocfup2 3fadm7uq0-4ziqvujkqwuxrykaqgDokument36 SeitenAcfrogdtvu6zlyfry8-Jlk3gvpwxqgfxoqhrqzvdwvnipoybrtyke4bifddfinh7o Ec Aclwenwpg6qtny6cx-Huxzfiacj2es6inejvwwasbchocfup2 3fadm7uq0-4ziqvujkqwuxrykaqg314 Madhu ChaityaNoch keine Bewertungen
- Cambridge IGCSE™: Global Perspectives 0457/11 May/June 2022Dokument20 SeitenCambridge IGCSE™: Global Perspectives 0457/11 May/June 2022Akoh Nixon AkohNoch keine Bewertungen
- Fujifilm LTO Ultrium SeminarDokument46 SeitenFujifilm LTO Ultrium SeminarLeandro MussoNoch keine Bewertungen
- CH 42Dokument86 SeitenCH 42arcamax74Noch keine Bewertungen