Beruflich Dokumente
Kultur Dokumente
Guide To Obtaining BSC6900 Information
Hochgeladen von
Sunny HaqOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Guide To Obtaining BSC6900 Information
Hochgeladen von
Sunny HaqCopyright:
Verfügbare Formate
Guide to Obtaining BSC6900 Information
Confidentiality
Product Name
Confidentiality Level
BSC6900
INTERNAL
Product Version
Total 49 Pages
BSC6900 V900R011
Guide to Obtaining BSC6900 Information
Prepared by
BSC6900 Maintenance Team
Date
Reviewed by
Date
Approved by
Date
2010-12-01
Huawei Technologies Co., Ltd.
All Rights Reserved
2014-1-19
Huawei Confidential
Page 1 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Contents
1 Logging In to the BSC OMU..........................................................................................................6
1.1 Querying the OMU Directory Structure...................................................................................................................6
1.1 Querying the OMU Directory Structure...................................................................................................................6
1.2 Querying the Installation Directory of the Main Workspace of the OMU...............................................................7
1.2 Querying the Installation Directory of the Main Workspace of the OMU...............................................................7
1.3 Logging In to the OMU by Using the File Manager on the Web LMT....................................................................7
1.3 Logging In to the OMU by Using the File Manager on the Web LMT....................................................................7
1.4 Obtaining a Log by Using the FTP Client................................................................................................................7
1.4 Obtaining a Log by Using the FTP Client................................................................................................................7
2 Obtaining Common Information...................................................................................................9
2.1 Obtaining Data Configuration..................................................................................................................................9
2.1 Obtaining Data Configuration..................................................................................................................................9
2.2 Obtaining Alarm Information.................................................................................................................................10
2.2 Obtaining Alarm Information.................................................................................................................................10
2.3 Obtaining Operation Logs......................................................................................................................................12
2.3 Obtaining Operation Logs......................................................................................................................................12
2.4 Obtaining Debug Logs............................................................................................................................................13
2.4 Obtaining Debug Logs............................................................................................................................................13
2.5 Obtaining GCSR/GCHR/UCHR Logs...................................................................................................................14
2.5 Obtaining GCSR/GCHR/UCHR Logs...................................................................................................................14
2.6 Obtaining Single PS User Logs..............................................................................................................................15
2.6 Obtaining Single PS User Logs..............................................................................................................................15
2.7 Obtaining DSP Running Information.....................................................................................................................15
2.7 Obtaining DSP Running Information.....................................................................................................................15
2.8 Obtaining DSP Lastword Logs...............................................................................................................................15
2.8 Obtaining DSP Lastword Logs...............................................................................................................................15
2.9 Obtaining XPU Running Logs...............................................................................................................................15
2.9 Obtaining XPU Running Logs...............................................................................................................................15
2.10 Obtaining XPU Lastword Logs............................................................................................................................15
2.10 Obtaining XPU Lastword Logs............................................................................................................................15
2.11 Obtaining PMU Running Logs.............................................................................................................................16
2.11 Obtaining PMU Running Logs.............................................................................................................................16
2014-1-19
Huawei Confidential
Page 2 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.12 Obtaining Original Traffic Measurement Files.....................................................................................................16
2.12 Obtaining Original Traffic Measurement Files.....................................................................................................16
2.13 Obtaining Signaling Messages.............................................................................................................................16
2.13 Obtaining Signaling Messages.............................................................................................................................16
2.13.1 Tracing Signaling Messages over the A Interface..........................................................................................18
2.13.1 Tracing Signaling Messages over the A Interface..........................................................................................18
2.13.2 Tracing Signaling Messages over the CS Um Interface.................................................................................19
2.13.2 Tracing Signaling Messages over the CS Um Interface.................................................................................19
2.13.3 Tracing Signaling Messages over the PS Um Interface.................................................................................20
2.13.3 Tracing Signaling Messages over the PS Um Interface.................................................................................20
2.13.4 Tracing Signaling Messages over the Interface Between the BSC and CBC.................................................21
2.13.4 Tracing Signaling Messages over the Interface Between the BSC and CBC.................................................21
2.13.5 Tracing Signaling Messages over the Group Call Interface...........................................................................21
2.13.5 Tracing Signaling Messages over the Group Call Interface...........................................................................21
2.13.6 Tracing Signaling Messages over the Interface Between BSCs.....................................................................21
2.13.6 Tracing Signaling Messages over the Interface Between BSCs.....................................................................21
2.13.7 Tracing Signaling Messages over the CS Abis Interface................................................................................22
2.13.7 Tracing Signaling Messages over the CS Abis Interface................................................................................22
2.13.8 Tracing Signaling Messages over the PS Abis Interface................................................................................24
2.13.8 Tracing Signaling Messages over the PS Abis Interface................................................................................24
2.13.9 Tracing PTP Signaling Messages over the Gb Interface................................................................................25
2.13.9 Tracing PTP Signaling Messages over the Gb Interface................................................................................25
2.13.10 Tracing SIG Signaling Messages over the Gb Interface...............................................................................25
2.13.10 Tracing SIG Signaling Messages over the Gb Interface...............................................................................25
2.13.11 Tracing Signaling Messages of a Single CS User.........................................................................................26
2.13.11 Tracing Signaling Messages of a Single CS User.........................................................................................26
2.13.12 Tracing Signaling Messages of a Single PS User.........................................................................................27
2.13.12 Tracing Signaling Messages of a Single PS User.........................................................................................27
2.13.13 Tracing Signaling Messages over the CS Ater Interface..............................................................................28
2.13.13 Tracing Signaling Messages over the CS Ater Interface..............................................................................28
2.13.14 Tracing Signaling Messages over the Pb Interface.......................................................................................28
2.13.14 Tracing Signaling Messages over the Pb Interface.......................................................................................28
2.13.15 Tracing BTS Signaling Messages.................................................................................................................29
2.13.15 Tracing BTS Signaling Messages.................................................................................................................29
2.13.16 Tracing OS Messages...................................................................................................................................29
2.13.16 Tracing OS Messages...................................................................................................................................29
2.14 Querying Information About CS Cell Distribution..............................................................................................29
2.14 Querying Information About CS Cell Distribution..............................................................................................29
2.15 Obtaining the Channel Status...............................................................................................................................29
2.15 Obtaining the Channel Status...............................................................................................................................29
2.16 Collecting BSC Local Information.......................................................................................................................30
2.16 Collecting BSC Local Information.......................................................................................................................30
2014-1-19
Huawei Confidential
Page 3 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.17 Collecting Data by Using the NIC Tool................................................................................................................32
2.17 Collecting Data by Using the NIC Tool................................................................................................................32
2.17.1 Creating an NE...............................................................................................................................................33
2.17.1 Creating an NE...............................................................................................................................................33
2.17.2 Creating a Collection Task..............................................................................................................................35
2.17.2 Creating a Collection Task..............................................................................................................................35
2.17.3 Observing the Collection Results...................................................................................................................40
2.17.3 Observing the Collection Results...................................................................................................................40
3 Information Required for Common Network Problems...........................................................41
3.1 Problems About Board Resetting and Switchover.................................................................................................41
3.1 Problems About Board Resetting and Switchover.................................................................................................41
3.2 Problems About the A Interface Link.....................................................................................................................41
3.2 Problems About the A Interface Link.....................................................................................................................41
3.3 Problems About Transmission................................................................................................................................41
3.3 Problems About Transmission................................................................................................................................41
3.4 Problems About Calling..........................................................................................................................................41
3.4 Problems About Calling..........................................................................................................................................41
3.5 Problems About Voice............................................................................................................................................42
3.5 Problems About Voice............................................................................................................................................42
3.6 Problems About Channels......................................................................................................................................42
3.6 Problems About Channels......................................................................................................................................42
3.7 Problems about the LMT........................................................................................................................................42
3.7 Problems about the LMT........................................................................................................................................42
3.8 Problems About the OMU......................................................................................................................................42
3.8 Problems About the OMU......................................................................................................................................42
3.9 Problems About Traffic Measurement....................................................................................................................42
3.9 Problems About Traffic Measurement....................................................................................................................42
3.10 Problems About Alarms........................................................................................................................................42
3.10 Problems About Alarms........................................................................................................................................42
3.11 Problems About the Hardware..............................................................................................................................42
3.11 Problems About the Hardware..............................................................................................................................42
3.12 Problems About the BTS......................................................................................................................................43
3.12 Problems About the BTS......................................................................................................................................43
3.13 Problems About PS Channel Fault/Out-of-Synchronization................................................................................43
3.13 Problems About PS Channel Fault/Out-of-Synchronization................................................................................43
3.14 Problems About PS Resources.............................................................................................................................43
3.14 Problems About PS Resources.............................................................................................................................43
3.15 Problems About the PS Access Process................................................................................................................43
3.15 Problems About the PS Access Process................................................................................................................43
3.16 Problems About the Throughput (FTP Uploading/Downloading).......................................................................44
3.16 Problems About the Throughput (FTP Uploading/Downloading).......................................................................44
2014-1-19
Huawei Confidential
Page 4 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
3.17 Problems About PS Indexes.................................................................................................................................44
3.17 Problems About PS Indexes.................................................................................................................................44
3.18 Problems About PS Board Faults.........................................................................................................................44
3.18 Problems About PS Board Faults.........................................................................................................................44
3.19 Problems About the PS GB Interconnection........................................................................................................44
3.19 Problems About the PS GB Interconnection........................................................................................................44
3.20 Obtaining Location Information About a Configuration Problem.......................................................................44
3.20 Obtaining Location Information About a Configuration Problem.......................................................................44
3.21 Obtaining Location Information About a BTSOM Problem................................................................................44
3.21 Obtaining Location Information About a BTSOM Problem................................................................................44
3.22 Collecting Information About a Voice Problem...................................................................................................45
3.22 Collecting Information About a Voice Problem...................................................................................................45
3.23 Checking an IP Problem.......................................................................................................................................45
3.23 Checking an IP Problem.......................................................................................................................................45
3.24 Obtaining Location Information About a Web LMT Problem.............................................................................46
3.24 Obtaining Location Information About a Web LMT Problem.............................................................................46
3.25 List of Health Check Information After BSC Version Upgrade...........................................................................46
3.25 List of Health Check Information After BSC Version Upgrade...........................................................................46
3.26 List of Location Information About a Cell Problem.............................................................................................47
3.26 List of Location Information About a Cell Problem.............................................................................................47
3.27 List of Location Information About a Call Problem.............................................................................................47
3.27 List of Location Information About a Call Problem.............................................................................................47
4 Transferring Information.............................................................................................................49
2014-1-19
Huawei Confidential
Page 5 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Logging In to the BSC OMU
1.1 Querying the OMU Directory Structure
The following figure shows the OMU directory structure:
2014-1-19
Huawei Confidential
Page 6 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
1.2 Querying the Installation Directory of the Main
Workspace of the OMU
Run the LST OMUAREA command to query the workspace of the OMU and the current
running version.
1.3 Logging In to the OMU by Using the File Manager on the
Web LMT
The File Manager can display a maximum of 1,000 pieces of data. If the number of files in the directory
exceeds 1,000, some log files may not be displayed. Therefore, you must use other methods to obtain
required information.
1.4 Obtaining a Log by Using the FTP Client
2014-1-19
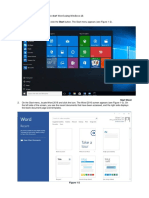
1.
Choose Start>All Programs>Huawei Local Maintenance Terminal > FTP Client to
start the FTP client tool.
2.
In the server connection area of the FTP client, enter the external virtual IP address of
the OMU, and an FTP user name and the password.
3.
Click Enter to connect the OMU. The Connect Information window displays the
connection status.
4.
After the connection succeeds, find the installation directory of the main workspace of
the OMU\ftp in the server list. The server list window displays all files in the directory.
Huawei Confidential
Page 7 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
5.
According to the file name, select the operation log file to be downloaded, and doubleclick the file to download the file to the LMT.
6.
After the file is downloaded, choose System>Quit on the FTP client or click
upper right corner of the window to quit from the FTP client.
at the
FTP user name and password
When the OMU is installed, the default user name is FtpUsr.
If you forget the password, you can run the MOD FTPPWD command to change the
password of the FTP user name to the designated one.
2014-1-19
Huawei Confidential
Page 8 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Obtaining Common Information
2.1 Obtaining Data Configuration
1.
Run the EXP CFGMML command to export the current configuration file.
2.
Run the EXP INNERCFGMML command to export the current configuration file
containing internal software parameters.
You can enter a path where the exported MML script is saved and a file name that the file is
saved as. If you enter no path or file name, the exported MML script is automatically saved in
the \\%INSTALLPATH%\mbsc\bam\version_a\ftp\export_cfgmml directory. In this case,
you only need to copy the file in the directory.
A configuration file is in a directory, for example,
\\10.161.100.174\mbsc\bam\version_a\ftp\export_cfgmml.
2014-1-19
Huawei Confidential
Page 9 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
When no file name is specified, a configuration file is named as follows:
For example, CFGMML-BSC0-20091202184237.zip
CFGMML BSC0 2009 12 02 18 42 37
.zip
CFGMML + BSC0 + Year + Month + Day + Hour +Minute + Second + File Suffix
2.2 Obtaining Alarm Information
1.
2014-1-19
Run the COL LOG command to obtain history alarms.
Huawei Confidential
Page 10 of 49
Guide to Obtaining BSC6900 Information
2.
2014-1-19
Confidentiality
Query history alarms by date on the WEB LMT.
Huawei Confidential
Page 11 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Save the alarms in a file in the .csv format.
2.3 Obtaining Operation Logs
Run the command shown in the following figure to obtain operation logs.
2014-1-19
Huawei Confidential
Page 12 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Time processing rules: If neither Start Time nor End Time is specified, logs recorded from the earliest
time to the latest time are exported by default. If Start Time is specified but End Time is not specified,
all logs recorded from the start time to the latest time are exported. If Start Time is not specified but
End Time is specified, logs recorded from the earliest time to the end time are exported.
The operation log file is saved in the ftp\operator_log directory of the main workspace of the OMU.
The saving path is displayed in the MML execution result window,
\\10.161.100.174\mbsc\bam\version_a\ftp\exp_log\MBSC-xxx-OLOG.csv.
2.4 Obtaining Debug Logs
The debug logs are in the DEBG file in a directory, for example,
\\10.161.100.174\mbsc\bam\common\fam\famlogfmt\.
Time when a debug log file is saved:
The time when the debug log file is saved is related to the number of logs in the directory
where the logs are saved. When the system is abnormal, a lot of logs are generated. When the
space is insufficient, new logs quickly overwrite the original logs. In the extreme case, only
two days of logs can be saved. Therefore, debug logs need to be backed up in time.
A debug log file is named as follows:
Format of the start time and end time:
BSC0000_[DEBG]00Log20101203102457_20101203113504.log.zip
20101203102457_20101203113504
2010 12 03 10 24 57 _ 2010 12 03 11 35 04
Year Month Day Hour Minute Second _ Year Month Day Hour Minute Second
When you obtain logs in this way, you need to obtain the logs of all subracks according to the file name.
Or you can collect logs through the WEB LMT.
Run the COL LOG command and select DEBUG_LOG from the LOG File Type dropdown list and specify a subrack No. (optional), start time (optional), and end time (optional).
2014-1-19
Huawei Confidential
Page 13 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Then run the LST LOGRSTINFO command to view the results, which are similar to the
following:
Start the file manager and obtain the required logs according to the execution results of the
LST LOGRSTINFO command.
You can obtain multiple types of logs in this way. You only need to select the specified log type from the
Log File Type drop-down list to obtain the required types of logs.
2.5 Obtaining GCSR/GCHR/UCHR Logs
The GCSR/GCHR/UCHR logs are in the GCSR/GCHR/UCHR file in a directory, for
example, \\10.161.100.174\mbsc\bam\common\fam\famlogfmt\.
The rules for naming a GCSR/GCHR/UCHR log file are the same as those for naming a
debug log file.
When you obtain logs in this way, you need to obtain the logs of all subracks according to the file name.
2014-1-19
Huawei Confidential
Page 14 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.6 Obtaining Single PS User Logs
The single PS user logs are in the GPSR file in a directory, for example,
\\10.161.100.174\mbsc\bam\common\fam\famlogfmt\.
The rules for naming a GPSR log file are the same as those for naming a debug log file.
2.7 Obtaining DSP Running Information
The directory is \\10.161.100.174\mbsc\bam\version_a\ftp\export_cfgmml, for example.
2.8 Obtaining DSP Lastword Logs
The DSP lastword logs are in the MDSP file in a directory, for example,
\\10.161.100.174\mbsc\bam\common\fam\famlogfmt\.
2.9 Obtaining XPU Running Logs
The XPU running logs are in a file in the .log format in a directory, for example,
\\10.141.122.244\mbsc\bam\common\fam\fad\.
2.10 Obtaining XPU Lastword Logs
The XPU lastword logs are in a file in the RESET_REASON_DEMAND_OF_MUX_*.log
format in a directory, for example, \\10.141.122.244\mbsc\bam\common\fam\fad\.
2014-1-19
Huawei Confidential
Page 15 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.11 Obtaining PMU Running Logs
2.12 Obtaining Original Traffic Measurement Files
The original traffic measurement files are in a directory, for example,
\\10.161.100.174\mbsc\bam\version_a\ftp\MeasResult.
An original traffic measurement file is named as follows:
The traffic measurement period of common original traffic measurement files is 60 minutes. The naming
of an original traffic measurement file, see the figure below.
A date.start time+time zone-end time+time zone_period flag
Period calculation: End time start time = traffic measurement period
Period flag:
Traffic measurement in a normal period: EMS-NORMAL Traffic measurement in 30 or 60
minutes
A20100915.0300+0800-0400+0800_EMS-NORMAL.mrf.bz2
A20101126.1330+0800-1400+0800_EMS-NORMAL.mrf.bz2
Traffic measurement in a short period: EMS-SHORTPERIOD
15 minutes
traffic measurement in 1, 5 or
A20100811.0000+0100-0015+0100_EMS-SHORTPERIOD.mrf.zip
A20100811.0000+0100-0015+0100_EMS-SHORTPERIOD.mrf.zip
24-hour traffic measurement:
A20100916.0000+0800-0000+0800_EMS-1440.mrf.bz2
The information about logs, traffic measurements, and alarms in section 2.2 through 2.12 can be
obtained by running the COL LOG command. This method is simple and is not error-prone. You should
try to use this method to obtain logs, traffic measurements, and alarms.
2.13 Obtaining Signaling Messages
You can obtain various signaling messages by selecting various tracing tasks under GSM
2014-1-19
Huawei Confidential
Page 16 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
services in the Trace Navigation Tree of the Trace tab on the main interface of the LMT.
In the tracing of various signaling messages, you need to determine whether the trace mode is
Report or Save to OMU. The following describes the meanings and use of these two trace
modes.
In Report mode, the traced signaling messages are sent by the GBAM (or GOMU) to the
LMT. The LMT saves the signaling file is and meanwhile displays each traced signaling
message in the tracing window. In this case, you are recommended to select Save File. You
can specify a file name or use the default file name of the system. You are also recommended
to use the default file saving path of the system. If you do not select Save File, the system
asks you whether to save the file or not when you close the tracing window.
The Report trace mode helps you to view the traced signaling messages. If the connection
between the LMT and the GBAM (or GOMU) is interrupted, the tracing task is subsequently
terminated. Therefore, the Report trace mode is applicable to short-time attended tracing.
In Save to OMU mode, the traced signaling messages are saved on the GBAM (or GOMU),
but are not displayed in the tracing window on the LMT. In addition, you need to perform the
following operations to upload the signaling file on the GBAM (GOMU) to the LMT:
On the main interface of the LMT, click Trace to access the Trace tab and choose Trace
Navigation Tree>Trace to start trace file management.
Set query conditions in the Query Setting text box and click Query. From the query
results, select the trace file to be uploaded to the LMT.
Set the upload parameters in the Upload Setting area and click Upload to upload the
trace file.
View the upload directory on the LMT and check whether the required trace files are all
uploaded to the LMT.
The Save to OMU mode is independent of the normal connection between the LMT and the
GBAM (or GOMU), but the traced signaling messages cannot be displayed on the tracing
window. Therefore, the Save to OMU mode is applicable to long-time unattended tracing.
In a high-traffic scenario, you must not start too many tracing tasks. Otherwise, the response
of the LMT is low. The Save to OMU mode is recommended in the high-traffic scenario.
2014-1-19
Huawei Confidential
Page 17 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.13.1 Tracing Signaling Messages over the A Interface
This tracing task is used to trace signaling messages, including BSSAP messages, MTP3
messages, MTP2 messages, SCCP messages, SCTP messages, and M3UA messages, over the
A interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click A Interface Trace. In the A Interface
Trace dialog box, first set parameters under the Basic tab, and then set parameters under the
tab of the type of the signaling messages to be traced. After setting parameters, click OK. In
the message browsing window, you can view the traced message streams.
2014-1-19
Huawei Confidential
Page 18 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.13.2 Tracing Signaling Messages over the CS Um Interface
This tracing task is used to trace layer-3 signaling messages by carrier or cell over the CS Um
interface. When signaling messages over the Um interface are traced by cell, 16 cells are
supported at most.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Um Interface CS Trace. In the
displayed Um Interface CS Trace dialog box, set parameters and then click OK. In the
message browsing window, you can view the traced message streams.
2014-1-19
Huawei Confidential
Page 19 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.13.3 Tracing Signaling Messages over the PS Um Interface
This tracing task is used to trace signaling messages, including DUMMY messages, system
messages, paging messages, and data block messages, over the PS Um interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Um Interface PS Trace. In the displayed
Um Interface PS Trace dialog box, set parameters and then click OK. In the message
browsing window, you can view the traced message streams.
2014-1-19
Huawei Confidential
Page 20 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.13.4 Tracing Signaling Messages over the Interface Between the BSC
and CBC
This tracing task is used to trace the interface signaling messages between the BSC and the
(cell broadcast center (CBC).
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double-click BSC-CBC Interface Trace. In the
displayed BSC-CBC Interface Trace dialog box, set parameters and then click OK. In the
message browsing window, you can view the traced message streams.
2.13.5 Tracing Signaling Messages over the Group Call Interface
This tracing task is used to trace VGCS messages and VBS messages over the A/Abis/Um
standard interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double-click Group Call Trace. In the displayed
Group Call Trace dialog box, set parameters and then click OK. In the message browsing
window, you can view the traced message streams.
2.13.6 Tracing Signaling Messages over the Interface Between BSCs
This tracing task is used to trace signaling messages over the interface between BSCs.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double-click BSC Trace. In the displayed BSC Trace
dialog box, set parameters and then click OK. In the message browsing window, you can
view the traced message streams.
2014-1-19
Huawei Confidential
Page 21 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.13.7 Tracing Signaling Messages over the CS Abis Interface
This tracing task is used to trace signaling messages, including RSL messages, ESL messages,
EML messages, OML messages, and LAPD messages, over the CS Abis interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Abis Interface CS Trace. In the Abis
Interface CS Trace dialog box, first set parameters under the Basic tab, and then set
parameters under the tab of the type of the signaling messages to be traced. After setting
parameters, click OK. In the message browsing window, you can view the traced message
streams.
1.
2014-1-19
OML
Huawei Confidential
Page 22 of 49
Guide to Obtaining BSC6900 Information
2.
2014-1-19
Confidentiality
RSL
Huawei Confidential
Page 23 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.13.8 Tracing Signaling Messages over the PS Abis Interface
This tracing task is used to trace signaling messages by carrier or cell over the PS Abis
interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Abis Interface PS Trace. In the
displayed Abis Interface PS Trace dialog box, set parameters and then click OK. In the
message browsing window, you can view the traced message streams.
2014-1-19
Huawei Confidential
Page 24 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.13.9 Tracing PTP Signaling Messages over the Gb Interface
This tracing task is used to trace PTP signaling messages by cell or NSEI+BVCI over the Gb
interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Gb Interface PTP Trace. In the
displayed Gb Interface PTP Trace dialog box, set parameters and then click OK. In the
message browsing window, you can view the traced message streams.
2.13.10 Tracing SIG Signaling Messages over the Gb Interface
This tracing task is used to trace SIG signaling messages by NSEI over the Gb interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Gb Interface SIG Trace. In the
displayed Gb Interface SIG Trace dialog box, set parameters and then click OK. In the
message browsing window, you can view the traced message streams.
2014-1-19
Huawei Confidential
Page 25 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.13.11 Tracing Signaling Messages of a Single CS User
This tracing task is used to trace signaling messages of a specified user over the A/Abis/Um
standard interface. You can specify the user by IMSI, IMEI, TMSI, MSISDN, CELLID, or
channel. The task provides a way of identifying signaling messages of different users by call
number. This provides an effective means of locating problems. In the Single User CS Trace
dialog box, you can select CDT Mode to trace internal signaling messages to locate signaling
problems more accurately.
The signaling messages of all users in a maximum of 16 cells can be traced and the signaling
messages of a single user are identified by the call number.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Single User CS Trace. In the displayed
Single User CS Trace dialog box, set parameters and then click OK. In the message
browsing window, you can view the traced message streams.
2014-1-19
Huawei Confidential
Page 26 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
When you select MSISDN from the Trace Object Symbol Type drop-down list, the
MSISDN is the number of the peer end.
1.
(Recommended) If the signaling messages of the calling user are traced, the MSISDN is
the called number, namely, the number dialed by the user. For example, if the user dials
12345, the MSISDN is 12345.
2.
If the signaling messages of the called user are traced, the MSISDN is the calling
number, namely, the number presented on the called MS. For example, if the number
presented on the called MS is 54321, the MSISDN is 54321.
When you select TMSI or IMSI from the Trace Object Symbol Type drop-down list, you
need to confirm the reallocation policy on the MSC side.
1.
If an MS originates a TMSI call, you can start TMSI tracing.
2.
If an MS originates an IMSI call, you can start IMSI tracing.
When you select IMEI from the Trace Object Symbol Type drop-down list, you need to
confirm whether the function of obtaining the IMEI is enabled on the MSC side.
2.13.12 Tracing Signaling Messages of a Single PS User
This tracing task is used to trace messages of a specified user over the Gb/Abis/Um standard
interface, internal messages, or Um data block messages. You can specify the user by IMSI or
TLLI.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Single User PS Trace. In the displayed
Single User PS Trace dialog box, set parameters and then click OK. In the message browsing
window, you can view the traced message streams.
2014-1-19
Huawei Confidential
Page 27 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
You can select Trace Um Datablock Message only when the trace interface type is Um
interface.
When you select IMSI from the Trace Object Symbol Type drop-down list, you need to
confirm the reallocation policy on the MSC side. If an MS originates an IMSI call, you can
start IMSI tracing.
When select TLLI from the Trace Object Symbol Type drop-down list, you first need to run
the DSP MSCONTEXT command to view the TLLI value of the MS during a PS service.
The TLLI of the MS may be reallocated during the PS service. In this case, you can query the
new TLLI and continue to trace.
2.13.13 Tracing Signaling Messages over the CS Ater Interface
This tracing task is used to trace signaling messages over the CS Ater interface. When the TC
subrack is remotely deployed, the interface between the BM subrack and the TC subrack is
Ater interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Ater Interface CS Trace. In the
displayed Ater Interface CS Trace dialog box, set parameters and then click OK. In the
message browsing window, you can view the traced message streams.
2.13.14 Tracing Signaling Messages over the Pb Interface
This tracing task is used to trace signaling messages over the Pb interface.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click Pb Interface Trace. In the displayed Pb
Interface Trace dialog box, first set parameters under the Basic tab, and then set parameters
2014-1-19
Huawei Confidential
Page 28 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
under the tab of the type of the signaling messages to be traced. After setting parameters, click
OK. In the message browsing window, you can view the traced message streams.
2.13.15 Tracing BTS Signaling Messages
This tracing task is used to trace BTS signaling messages.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>GSM Services and double click BTS Signaling Trace. In the BTS
Signaling Trace dialog box, first set parameters under the Basic tab, and then set parameters
under the tab of the type of the signaling messages to be traced. After setting parameters, click
OK. In the message browsing window, you can view the traced message streams.
2.13.16 Tracing OS Messages
This tracing task is used to trace the messages received and sent between the switching
module of the OMU and a module of a board, or between modules of a board. Not only all
received and sent messages between two different modules, but also all received and sent
messages of a module (namely, messages a module sends to itself) can be traced.
On the main interface of the LMT, click Trace to access the Trace tab. In the trace navigation
tree, choose Trace>Device Commissioning and double click OS. In the displayed OS Trace
dialog box, set parameters and then click OK. In the message browsing window, you can
view the traced message streams.
2.14 Querying Information About CS Cell Distribution
On the MML interface, run the DSP PSCELL: IDXTYPE=BYBSC command to query the
information about the cell distribution of the whole BSC.
Save the query result to the specified file.
The settings of the command are as follows:
2.15 Obtaining the Channel Status
Method 1: In the device navigation tree, click Monitor Channel Status on the BTS to be
queried.
2014-1-19
Huawei Confidential
Page 29 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Method 2: Run the DSP CHNSTAT MML command.
2.16 Collecting BSC Local Information
2014-1-19
1.
Log in to the LMT and choose Device Maintenance>BSC Maintenance. There is a
Collect BSC Local Information option, as shown in the figure below.
2.
Double-click Collect BSC Local Information. The Time Setting dialog box is
displayed.
Huawei Confidential
Page 30 of 49
Guide to Obtaining BSC6900 Information
3.
Confidentiality
In the Time Setting dialog box, set the time segment during which the location
information needs to be obtained.
If All Time is selected, the LMT reads the duration from the configuration file. By default, the duration
of All Time is 30 days.
4.
According to the fault type, select the type of the fault whose information needs to be
collected from the Fault List pane in the Set Basic Information area. The
corresponding file in the File Type List is automatically selected. You can continue to
select the files that are not selected but need to be collected.
You can select the BTS whose information needs to be collected in the Site Type pane only when BTS
Fault is selected from the Fault List pane.
2014-1-19
5.
Choose Start>All Programs>Huawei Local Maintenance Terminal>FTP Server to
start the FTP server. After the FTP server is started, the task bar status is shown in the
figure below.
6.
Set FTP server parameters in the Upload Setting area, and click Execute to collect BSC
local information. The collected information is saved on the OMU. The files and
directories are shown in the File Name column in the figure below. The Progress list
displays the collection progress, and the Result tab displays the collected files, as shown
in the figure below.
Huawei Confidential
Page 31 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
The FTP server IP field is set to the IP address of the computer on which the FTP server is
started, and the Upload path field is set to the path where the uploaded files are saved on the
computer. By default, the FTP user name and FTP password fields are both set to admin.
The Subrack No. field in the Upload Setting area is valid only when Universal Debug Log File
is selected in the File Type List pane. By default, the files of all subracks are uploaded.
7.
After the execution, click Upload to upload the collected files from the OMU to the FTP
server. You can obtain the collected files in the folder that the upload path points to.
8.
To delete all collected files from the OMU, click Delete Files.
2.17 Collecting Data by Using the NIC Tool
The following only describes how to use the NIC tool to collect data. For NIC installation, NE
installation at the adaptation layer, and FTP server configuration, download relevant documents from the
website at http://support.huawei.com.
2014-1-19
1.
Task management: Used to create a collection task (select a collection scenario, NEs
whose information needs to be collected, collection duration)
2.
Scenario management: Used to customize a collection scenario (optional, applicable to
the case where a SOP collection scenario is not available)
3.
NE management: Used to create or delete an NE (here only NE creation is described)
4.
Upload management: Used to create an upload task to automatically upload data to the
FTP server (the SOP does not need to concern this function)
Huawei Confidential
Page 32 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.17.1 Creating an NE
The following describes only how to manually create an NE.
Open the NIC toolkit to access the Network Information Collection interface.
Choose NE Management>NE Information Maintenance.
Select an NE type, for example, BSC6900 GSM.
Configure NE collection information.
2014-1-19
Huawei Confidential
Page 33 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Description of the previous parameters for the BSC6900 GSM:
Network element name and Network element IP: Name and IP address of the NE to be. The
network element name or the network element IP can uniquely identify an NE, and no
repeated network element name or network element IP is allowed.
User type: Type of the user used for logging in to the BSC6900GSM, including domain user
and local user. When you select a domain user to create an NE, the NE must be under the
management of the M2000.
BAM user name and BAM password: Domain user name and password or local user name
and password used for logging in to a BSC6900GSM NE through the Web LMT.
OMU FTP port, OMU FTP user name, and OMU FTP password: Port number (default:
21), user name (default: Guest or FtpUsr), and password (default: Guest or FtpUsr) of the
FTP server on the current BSC6900GSM
Click Apply. If "Create the network element successfully" is displayed, the NE is created.
2014-1-19
Huawei Confidential
Page 34 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.17.2 Creating a Collection Task
Choose Task Management>Create Task>Based on Customize Collection Item.
This document describes only the most flexible Based on Customize Collection Item. For the other
three task creation scenarios, see the Help document of the NIC.
Enter a task name and select a product type and a task execution type.
2014-1-19
Huawei Confidential
Page 35 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Task Name: Name of a collection task used for patrol inspection or SOP. A task name can
contain case-insensitive letters A through Z, digits 0 through 9, and underline _, but cannot
contain space or other characters. A task name cannot begin with a digit or contain more than
27 characters. You are recommended to follow these rules to name a collection task.
Task Execution Type: You are recommended to select Instant. If you select Scheduled, you
need to set the task execution time.
Click Next to set the collection time.
Data collection time range: Set this field as required.
Data collection method: If you select Whole day, the actual data collection time range is the
range specified by the Data collection time range field. If you select Time period, data is
collected in the time period of each day within the range specified by the Data collection
time range field.
2014-1-19
Huawei Confidential
Page 36 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Click Next to select NEs. Select the NEs whose information needs to be collected from the
Optional NEs drop-down list. Click
to move an NE to or click
move all NEs to the Selected NE drop-down list, as shown in the figure below.
2014-1-19
Huawei Confidential
to
Page 37 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
The NE display modes include display by topology and display by NE type.
You can press and hold the Ctrl key to select multiple NEs at one time. You can click
move an NE whose information needs to be collected from the Selected NEs drop-down list to the
Optional NEs drop-down list. Or you can click
Optional NEs drop-down list.
to
to move all selected NEs to the
Click Next.
Select collection items. In this step, you can flexibly select the BSC traffic measurement file,
the BSC configuration file, various BSC logs, measurement reports, and other desired
information as required.
If you select Save as New Scenario, you can save the current NE type and collection items as a new
scenario after entering a scenario name, a scenario group, and scenario remarks. For description of the
parameters such as Scenario Name, Scenario Group, and Scenario Description, see the parameter
description in Creating a Scenario.
Click Next.
Set the detailed parameters about the collection items, as shown in the figure below. If a
collection item does not involve detailed parameters, you can skip this step.
Click Next.
Enter additional information such as the name and email box of the information collector and
click Next.
2014-1-19
Huawei Confidential
Page 38 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
After confirming the collected information, click Finish to start the collection task.
2014-1-19
Huawei Confidential
Page 39 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
2.17.3 Observing the Collection Results
During a collection, do not shut down the FTP service of the tool. Otherwise, the collection fails.
Concern whether a collection configuration failure exists. If collection configuration fails, the NE
analysis also fails.
During a collection, you can view the progress of the whole collection task together with the
completion progress and running information of each NE.
The data collection result is saved in the NIC installation directory\NIC\var\nic\task ID
path.
2014-1-19
The task ID, similar to 10002, 10003, 10004, and so on, is generated at random by the system.
According to the collection task name in a task ID folder, you can determine whether the task ID
folder contains a created collection task.
Huawei Confidential
Page 40 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Information Required for Common Network
Problems
3.1 Problems About Board Resetting and Switchover
To analyze the problems about board resetting and switchover, you need to obtain the alarm
files, BSC lastword log files, debug log files, operation log files, and text log files, and the
BSC configuration data file.
The path of the text log file is OMU installation directory/mbsc/bam/common/fam/famlog.
3.2 Problems About the A Interface Link
TDM transmission mode: To analyze a problem about the A interface link, you need to obtain
the alarm files, SCCP signal trace files, MTP3 signal trace files, MTP2 signal trace files, BSC
configuration data file, debug log files, operation log files, and text log files.
IP transmission mode: To analyze a problem about the A interface link, you need to obtain the
alarm files, SCCP signal trace files, M3UA signal trace files, SCTP signal trace files, BSC
configuration data file, debug log files, operation log files, and text log files.
3.3 Problems About Transmission
To analyze a problem about transmission, you need to obtain the alarm files, SCCP signal
trace files, MTP3 signal trace files, MTP2 signal trace files, BSC configuration data files,
debug log files, operation log files, and text log files.
3.4 Problems About Calling
To analyze a problem about calling, you need to obtain the A interface BSSAP trace files,
Abis interface RSL trace files, single user trace files, traffic measurement result files, GCHR
and UCHR log files, debug log files, GCSR log files, operation log files, text log files, BSC
configuration data file, DT files, type and software version of the MS encountered with the
2014-1-19
Huawei Confidential
Page 41 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
problem, and manufacturer, software version number, and interconnection planning data of
the MSC.
3.5 Problems About Voice
To analyze a problem about voice, you need to obtain the test call records, traffic
measurement result files, GCHR log files, debug log files, BTS log files, alarm files, speech
codec call logs, DSP debug logs, DSP lastword logs, and recording files.
3.6 Problems About Channels
To analyze a problem about channels, you need to obtain a snapshot about the channel status
query result, OML trace files, RSL trace files, LAPD trace files, internal messages traced
from the BTSCP to the CECHM, BSC configuration data file, GCHR log files, debug log
files, operation log files, text log files, channel related alarm files, and channel related traffic
measurement result files.
3.7 Problems about the LMT
To analyze a problem about the LMT, you need to obtain the LMT frontward/backward log
files, operation log files, and BSC configuration data file.
3.8 Problems About the OMU
To analyze a problem about the OMU, you need to obtain the OMU log files, operation log
files, and history alarm files.
3.9 Problems About Traffic Measurement
To analyze a problem about traffic measurement, you need to obtain the OMU log files,
operation log files, history alarm files, traffic measurement result files, subsystem result files,
active measurement task files, standby measurement task files, and information about
performance switches.
3.10 Problems About Alarms
To analyze a problem about an alarm, you need to obtain the OMU log files, operation log
files, history alarm files, history fault alarm files, and configuration information of the alarm
system.
3.11 Problems About the Hardware
To analyze a problem about the hardware, you need to obtain the bar code of a board
2014-1-19
Huawei Confidential
Page 42 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
(including the bar codes of subboards), lastwords, *.hrdlog, dotting log files, text log files,
fault log files, operation log files, and OMU logs (bootp logs and ftp logs).
3.12 Problems About the BTS
To analyze a problem about the BTS, you need to obtain the BTS log files, BSC configuration
data file, BTS software version, and OML messages.
3.13 Problems About PS Channel Fault/Out-ofSynchronization
To analyze a problem about a PS channel fault/out-of-synchronization, you need to obtain the
debug log files, operation log files, PS Um interface message trace files, PS Abis interface
message trace files, OML interface trace files, PS basic MML query results, G_Abis traffic
measurements, alarm information, and a snapshot of channel monitoring.
3.14 Problems About PS Resources
To analyze a problem about PS resources, you need to obtain the PS Um interface message
trace files, SIG message trace files, PTP message trace files, PS basic MML query results,
debug log files, operation log files, BSC configuration data file, traffic measurements related
to Abis timeslot release application/PDCH/DSP resources/ GB NS/GB LLC PDU, and alarm
information.
3.15 Problems About the PS Access Process
To analyze a problem about the PS access process, you need to obtain the following
information:
2014-1-19
Configuration file when the problem happens
Alarm file when the problem happens
Cell distribution information queried by an MML command when the problem happens
Debug logs of all subracks within two hours after the problem happens
Single PS user logs of all subracks within one day after the problem happens
PS Um message trace file/GB PTP message trace file in the cell with a problem or top
problems within one-hour traffic measurement period
Original traffic measurement files within the time period of message tracing, with the
measurement period of 60 minutes
If the problem happens only to a particular MS, trace the messages of a single PS user.
Huawei Confidential
Page 43 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
3.16 Problems About the Throughput (FTP
Uploading/Downloading)
To analyze a problem about the throughput, you need to obtain the PS Um interface message
trace files, SIG message trace files, PTP message trace files, PS CDT single user trace files,
PS Abis interface message trace files, BSC configuration file, trace files (TEMS logs,
including CDS log, probe log, and QXDM log) on the MS side, captured ETHERAL packets
(on the GB side and the MS side), captured SCU packets, and alarm information.
3.17 Problems About PS Indexes
To analyze a problem about a PS index, you need to obtain the PS Um interface message trace
files, SIG message trace files, PTP message trace files, PS CDT single user trace files, single
user log files, indexes related to a PS problem, and alarm information.
3.18 Problems About PS Board Faults
To analyze a problem about a PS board fault, you need to obtain the BSC lastword log files,
debug log files, operation log files, running log files, BSC configuration data file, and alarm
information.
3.19 Problems About the PS GB Interconnection
To analyze a problem about the PS GB interconnection, you need to obtain the query results
of MML commands (DSP BC, DSP NSVC, DSP SIGBVC, and DSP PTP BVC), debug log
files, operation log files, data configuration, alarms, FR loopback detection result, and the
networking structure of the feedback GB.
3.20 Obtaining Location Information About a Configuration
Problem
Col l ecti ng
Locati on I nformati on About BSC Confi gurati on Probl ems. docx
3.21 Obtaining Location Information About a BTSOM
Problem
Col l ecti ng
Locati on I nformati on About a BTSOM Probl em. docx
2014-1-19
Huawei Confidential
Page 44 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
3.22 Collecting Information About a Voice Problem
1.
Automatically record
Enter the ADD CALLRESRECORD command in the MML interface to add recording
data for a single user, for example, mobile user whose MSISDN is 13988080012.
ADD CALLRESRECORD: RECINDEX=0, USERIDTYPE=BYMSISDN,
MSISDN="13988080012", RECORDTYPE=TC;
Path of the recording data: \mbsc\bam\version_a(or version_b)\bin\fam\tc_file
If the version of the workspace of the OMU is version_a, the path of the recording data is
\mbsc\bam\version_a\bin\fam\tc_file. If the version is version_b, the path is
\mbsc\bam\version_b\bin\fam\tc_file.
For the method of obtaining the recording data, see sections about the methods of
obtaining logs.
2.
Obtain the DSP debug log file and DSP lastword log file in the
\mbsc\bam\common\fam\famlogfmt path.
The log file name is BSC0000_[DEBG]00Log20090730193820.log or
BSC0000_[DEBG]11Log20090730162635_20090730185100.log.zip.
The DSP lastword log file name is BSC0000_[MDSP]11Log20090730104125.log or
BSC0000_[MDSP]11Log20090729104009_20090730104125.log.zip.
You can obtain the DSP debug log file and the DSP lastword log file by running the
COL LOG command or collecting the BSC local information.
3.23 Checking an IP Problem
Run the PING IP command on the MML maintenance terminal to observe whether the
destination IP address can be pinged successfully.
2014-1-19
Huawei Confidential
Page 45 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Set the subrack No., slot No., destination IP address, source IP address for the specified board,
and run the PING IP command. If the destination IP address can be pinged successfully, a
link is established successfully. If the destination IP address cannot be pinged, check the
configurations of the router connected to the BSC.
3.24 Obtaining Location Information About a Web LMT
Problem
Col l ecti ng Web
LMT Logs. docx
3.25 List of Health Check Information After BSC Version
Upgrade
PS concerned information list after upgrade:
2014-1-19
1.
Original traffic measurement files in a period of 60 minutes within three days after
upgrade
2.
Configuration file
3.
All alarm files after upgrade
4.
Cell distribution information queried by an MML command
5.
Debug logs of all subracks within two hours before information collection
6.
All single PS user logs after upgrade
7.
DSP running information after upgrade
8.
All DSP lastwords after upgrade
Huawei Confidential
Page 46 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
The attachment below lists information that needs to be obtained for the health check of the
whole BSC.
Gui de to
I nformati on Col l ecti on Before and After BSC6900 Upgrade. doc
3.26 List of Location Information About a Cell Problem
1.
Configuration file when the problem happens
2.
Alarm file when the problem happens
3.
Cell distribution information queried by an MML command when the problem happens
4.
GB PTP message trace file and GB SIG message trace file of the cell that is abnormal
5.
If necessary (after a confirmation with the R&D department), run the RST PSCELL
command on the MML interface. The feedback information includes the GB PTP
message trace file, GB SIG message trace file, and operation log file of the abnormal cell
within the operation time.
6.
Operation logs from 10 days before the problem happens to the information collection
day, including the logs of all operations performed by field engineers on the abnormal
cell
7.
Debug logs of all subracks within two hours after the problem happens and logs of all
subracks when field engineers performs operations on the abnormal cell
3.27 List of Location Information About a Call Problem
1.
Configuration file when the problem happens
2.
Alarm file when the problem happens
3.
Cell distribution information queried by an MML command when the problem happens
4.
Debug logs of all subracks within two hours after the problem happens
5.
Single PS user logs of all subracks within one day after the problem happens
6.
PS Um message trace file/GB PTP message trace file in the cell with a problem or top
problems within one-hour traffic measurement period
7.
Original traffic measurement files within the time period of message tracing, with the
measurement period of 60 minutes
8.
If the problem happens only to a particular MS, trace the messages of a single PS user.
3.28 famlog
File in folder \bam\common\fam\famlog
The explanation of the file's name:
XXXX_$$Log**.logXXXX
"$$" means the subrack no.
"**" means the time.
For example, "BSC0000_01Log20101217000040_20101217041538.log.zip" means that the subrack no is 1,
and the time is between 20101217000040 and 20101217041538
Now, please collect the log that the subrack no is 0, and time start from 20110330(Include the
2014-1-19
Huawei Confidential
Page 47 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
20110330).
if the logs's size is too big, please upload them to the ftp web.
2014-1-19
Huawei Confidential
Page 48 of 49
Guide to Obtaining BSC6900 Information
Confidentiality
Transferring Information
After you obtain the information on site, if the amount of information is large, use the
following common FTP account to transfer the information to the FTP server and notify the
R&D engineers of it in time:
ftp.huawei.com
Upload information to the internal network or external network of Huawei, but download information
only from the internal network.
2014-1-19
Huawei Confidential
Page 49 of 49
Das könnte Ihnen auch gefallen
- Temario Curso AriesoGEO LTEDokument4 SeitenTemario Curso AriesoGEO LTEeduardo2307Noch keine Bewertungen
- Mobility Management in Connected Mode (ERAN3.0 - 07)Dokument359 SeitenMobility Management in Connected Mode (ERAN3.0 - 07)Sergio BuonomoNoch keine Bewertungen
- BSC6900 UMTS V900R021C10 Performance Counter ListDokument517 SeitenBSC6900 UMTS V900R021C10 Performance Counter ListAhmedMa'moonNoch keine Bewertungen
- MR CollectionDokument11 SeitenMR CollectionHICHAMNoch keine Bewertungen
- Useful Tips For EMS - V3.1Dokument62 SeitenUseful Tips For EMS - V3.1arinal09100% (1)
- Traffica 16SP2 Customer CareDokument59 SeitenTraffica 16SP2 Customer CareJJ LópezNoch keine Bewertungen
- Transmission Resource Management Parameter DescriptionDokument68 SeitenTransmission Resource Management Parameter DescriptionPaul MurphyNoch keine Bewertungen
- Flow ControlDokument87 SeitenFlow Controlibrahim_nfsNoch keine Bewertungen
- Toaz - Info Lte Pci Self Optimization Feature v100r015c10 01pdf en PRDokument74 SeitenToaz - Info Lte Pci Self Optimization Feature v100r015c10 01pdf en PRHakan KaracaNoch keine Bewertungen
- Discovery APP Description - Neighboring Cell CheckDokument29 SeitenDiscovery APP Description - Neighboring Cell CheckManos IatrouNoch keine Bewertungen
- Smartphone App-Aware Coordinated Control (ERAN13.1 - 01)Dokument41 SeitenSmartphone App-Aware Coordinated Control (ERAN13.1 - 01)GeorgeNoch keine Bewertungen
- 3G Signaling Trace and AnalysisDokument38 Seiten3G Signaling Trace and AnalysiscurtiskamotoNoch keine Bewertungen
- CHR ConfigDokument3 SeitenCHR ConfigmaryamalaNoch keine Bewertungen
- 2013 InfoVista-Aexio-VerR2 (XEDA-XEUS) - Edited - Tommy - Challenges - GenericDokument71 Seiten2013 InfoVista-Aexio-VerR2 (XEDA-XEUS) - Edited - Tommy - Challenges - GenericTommy Chin Yik Sean0% (1)
- GSM HuaweiDokument30 SeitenGSM HuaweiSri Datta Sameer AchantaNoch keine Bewertungen
- Huawei eRAN6.0 MIMO Feature Introduction: Node B Products of HuaweiDokument36 SeitenHuawei eRAN6.0 MIMO Feature Introduction: Node B Products of HuaweiSaghir TahirNoch keine Bewertungen
- Xeus, VistaNEO and Planet Call Trace Vendor Technology Support - 20170430Dokument6 SeitenXeus, VistaNEO and Planet Call Trace Vendor Technology Support - 20170430hanhdkNoch keine Bewertungen
- GSM Frequency PlanningDokument54 SeitenGSM Frequency Planningspuki210467% (3)
- CBS (RAN16.0 - Draft A)Dokument51 SeitenCBS (RAN16.0 - Draft A)Sam FicherNoch keine Bewertungen
- Configuration Management (SRAN9.0 02)Dokument31 SeitenConfiguration Management (SRAN9.0 02)waelq2003Noch keine Bewertungen
- Call ReestablishmentDokument426 SeitenCall ReestablishmentediicediicNoch keine Bewertungen
- SR@N12.0 GUL - Interoperability - GuideDokument598 SeitenSR@N12.0 GUL - Interoperability - GuideMuhammad GamalNoch keine Bewertungen
- Discovery APP Description - Antenna Reverse DetectionDokument10 SeitenDiscovery APP Description - Antenna Reverse DetectionManos IatrouNoch keine Bewertungen
- Execution of Huawei 3G Files On CME PDFDokument9 SeitenExecution of Huawei 3G Files On CME PDFalfonseoNoch keine Bewertungen
- OWO114030 WCDMA RAN12 Handover Algorithm and Parameters ISSUE 1.01Dokument166 SeitenOWO114030 WCDMA RAN12 Handover Algorithm and Parameters ISSUE 1.01ESkudaNoch keine Bewertungen
- Layered Paging in Idle Mode (RAN16.0 - 01)Dokument52 SeitenLayered Paging in Idle Mode (RAN16.0 - 01)jaxcom4578Noch keine Bewertungen
- Actix Analyzer Getting Started GuideDokument72 SeitenActix Analyzer Getting Started GuidejedossousNoch keine Bewertungen
- GU 900 MHZ Non-Standard Frequency Spacing (SRAN7.0 - 01)Dokument56 SeitenGU 900 MHZ Non-Standard Frequency Spacing (SRAN7.0 - 01)gopizizou50% (2)
- Ultima Forte Required Data Inputs For Huawei Infrastructure PDFDokument142 SeitenUltima Forte Required Data Inputs For Huawei Infrastructure PDFSarfaraz Akram100% (1)
- Bss Kpi ReferenceDokument70 SeitenBss Kpi ReferenceAhmed KamalNoch keine Bewertungen
- WCDMA RNO Access Problem Analysis Guidance-20040716-A-2.0Dokument39 SeitenWCDMA RNO Access Problem Analysis Guidance-20040716-A-2.0adhi_123scribdNoch keine Bewertungen
- Imanager U2000-Cme Northbound Interface Scenario Description (GSM)Dokument33 SeitenImanager U2000-Cme Northbound Interface Scenario Description (GSM)ramos_lisandroNoch keine Bewertungen
- RAN18.1 Capacity Monitoring Guide (BSC6910-Based) (02) (PDF) - EN PDFDokument78 SeitenRAN18.1 Capacity Monitoring Guide (BSC6910-Based) (02) (PDF) - EN PDFUmar MirNoch keine Bewertungen
- Cell Barring (RAN15.0 02)Dokument104 SeitenCell Barring (RAN15.0 02)Jonathan RuizNoch keine Bewertungen
- Inventory Management (SRAN16.1 - 01)Dokument20 SeitenInventory Management (SRAN16.1 - 01)Didier SepulvedaNoch keine Bewertungen
- High Speed Mobility (eRAN15.1 - Draft A)Dokument160 SeitenHigh Speed Mobility (eRAN15.1 - Draft A)Denmark WilsonNoch keine Bewertungen
- ERAN3.0 Data Transmission Analysis ManualDokument53 SeitenERAN3.0 Data Transmission Analysis ManualHarjeetsingh GillNoch keine Bewertungen
- Discovery APP Description - Engineering Parameter CheckDokument12 SeitenDiscovery APP Description - Engineering Parameter CheckManos IatrouNoch keine Bewertungen
- ConfigurationData 2021 03 04 21 50 49Dokument3.607 SeitenConfigurationData 2021 03 04 21 50 49fazadoNoch keine Bewertungen
- RnpData - BTS3900 V100R015C10SPC210 - 15 - 23 - 10Dokument848 SeitenRnpData - BTS3900 V100R015C10SPC210 - 15 - 23 - 10Joseph ChikuseNoch keine Bewertungen
- Ran19.1 Kpi Reference (Bsc6900 Based) (02) (PDF) enDokument162 SeitenRan19.1 Kpi Reference (Bsc6900 Based) (02) (PDF) enhekri100% (1)
- NSN BTSDokument19 SeitenNSN BTSAibout CheikhNoch keine Bewertungen
- HandoverDokument1.005 SeitenHandoverPapitch Do Dune100% (1)
- Ciphering Feature Parameter Description: GSM Bss GBSS14.0Dokument34 SeitenCiphering Feature Parameter Description: GSM Bss GBSS14.0Gunvant ParmarNoch keine Bewertungen
- GSM and UMTS Dynamic Spectrum Sharing (SRAN11.1 - 02)Dokument75 SeitenGSM and UMTS Dynamic Spectrum Sharing (SRAN11.1 - 02)waelq2003Noch keine Bewertungen
- Cell Broadcast (GBSS13.0 01)Dokument30 SeitenCell Broadcast (GBSS13.0 01)Rami DahhanNoch keine Bewertungen
- 2019 Customer Training Catalog-Training Programs (LTE) V1.0 PDFDokument91 Seiten2019 Customer Training Catalog-Training Programs (LTE) V1.0 PDFfazadoNoch keine Bewertungen
- Flow Control ManagementDokument11 SeitenFlow Control ManagementsinansafaaNoch keine Bewertungen
- BSS Troubleshooting Manual PDFDokument220 SeitenBSS Troubleshooting Manual PDFleonardomarinNoch keine Bewertungen
- Licensed Assisted Access (eRAN12.1 - 06)Dokument103 SeitenLicensed Assisted Access (eRAN12.1 - 06)waelq2003Noch keine Bewertungen
- RL45TD Feature DescriptionDokument95 SeitenRL45TD Feature DescriptionNur Chairil SyamNoch keine Bewertungen
- Voice Fault Diagnosis (GBSS18.1 - 01)Dokument45 SeitenVoice Fault Diagnosis (GBSS18.1 - 01)waelq2003Noch keine Bewertungen
- Soft-Synchronized Network (GBSS16.0 01)Dokument122 SeitenSoft-Synchronized Network (GBSS16.0 01)Wael AlkodamiNoch keine Bewertungen
- Critical Alarms For Huawei GSMDokument37 SeitenCritical Alarms For Huawei GSManandkusNoch keine Bewertungen
- Network Impact Report 2016 04Dokument273 SeitenNetwork Impact Report 2016 04juliosantanaNoch keine Bewertungen
- Cross-Layer Resource Allocation in Wireless Communications: Techniques and Models from PHY and MAC Layer InteractionVon EverandCross-Layer Resource Allocation in Wireless Communications: Techniques and Models from PHY and MAC Layer InteractionNoch keine Bewertungen
- VoLTE and ViLTE: Voice and Conversational Video Services over the 4G Mobile NetworkVon EverandVoLTE and ViLTE: Voice and Conversational Video Services over the 4G Mobile NetworkNoch keine Bewertungen
- Signaling in Telecommunication NetworksVon EverandSignaling in Telecommunication NetworksBewertung: 4 von 5 Sternen4/5 (1)
- # of Expansion Sites 1 1 0 # of Rollout Sites 0 0 0 # of Swap Sites 3 2 1Dokument8 Seiten# of Expansion Sites 1 1 0 # of Rollout Sites 0 0 0 # of Swap Sites 3 2 1Sunny HaqNoch keine Bewertungen
- Ericsson BSC Cell Alias Ericsson CGI CI Ericsson BSIC Ericsson BCCHNO Huawei BSC NameDokument14 SeitenEricsson BSC Cell Alias Ericsson CGI CI Ericsson BSIC Ericsson BCCHNO Huawei BSC NameSunny HaqNoch keine Bewertungen
- RF Optimization TechniquesDokument4 SeitenRF Optimization TechniquesSunny HaqNoch keine Bewertungen
- Migration of GSM Networks To GPRSDokument11 SeitenMigration of GSM Networks To GPRSSunny HaqNoch keine Bewertungen
- 11 Antennas and Radiating SystemsDokument129 Seiten11 Antennas and Radiating SystemsSunny HaqNoch keine Bewertungen
- Course Information Sheet: College of EnoineeringDokument20 SeitenCourse Information Sheet: College of EnoineeringSunny HaqNoch keine Bewertungen
- IBM Cognos 10 Active Report CookbookDokument68 SeitenIBM Cognos 10 Active Report CookbookRocio HerreroNoch keine Bewertungen
- CommandDokument8 SeitenCommandFaiz Ur RehmanNoch keine Bewertungen
- Mindjet MindManager User GuideDokument344 SeitenMindjet MindManager User GuideHeru HeriyantoNoch keine Bewertungen
- How To Create A Document in MS WordDokument8 SeitenHow To Create A Document in MS WordZainab IshfaqNoch keine Bewertungen
- IQPC MAnual P03185 - 20 - 0G0 - 06Dokument186 SeitenIQPC MAnual P03185 - 20 - 0G0 - 06Oae FlorinNoch keine Bewertungen
- Polycom HDX Configuration Guide: How To Configure A Polycom HDX To Work With 8x8 ServiceDokument11 SeitenPolycom HDX Configuration Guide: How To Configure A Polycom HDX To Work With 8x8 ServicetheanhcbNoch keine Bewertungen
- EdgeProbe Advanced Users Manual 3 1Dokument82 SeitenEdgeProbe Advanced Users Manual 3 1jeri_aries11Noch keine Bewertungen
- Anite 2Dokument76 SeitenAnite 2Vamshi PoshalaNoch keine Bewertungen
- User Manual For Aeon TimelineDokument63 SeitenUser Manual For Aeon TimelineSvetaFialNoch keine Bewertungen
- MobileTutorials TokyoDokument313 SeitenMobileTutorials Tokyostclara_lapaNoch keine Bewertungen
- User's Guide To Mini6410 Linux - 041611Dokument265 SeitenUser's Guide To Mini6410 Linux - 041611Cristina Glez. LoboNoch keine Bewertungen
- Salesforce Interview QuestionsDokument18 SeitenSalesforce Interview Questionsకెవి సాయి100% (3)
- Oracle 10g Reports 2 of 4Dokument92 SeitenOracle 10g Reports 2 of 4SureshVitusNoch keine Bewertungen
- Patrol LogMgmtDokument152 SeitenPatrol LogMgmtCharl11eNoch keine Bewertungen
- AutoCAD Civil 3D Survey - Practical ApplicationsDokument68 SeitenAutoCAD Civil 3D Survey - Practical ApplicationsMajk Shkurti100% (1)
- Wijmo TreeViewDokument61 SeitenWijmo TreeViewTio Lampard Chelsea FcNoch keine Bewertungen
- Configure NIC Teaming Broadcom Advanced Control Suite 3 OverviewDokument67 SeitenConfigure NIC Teaming Broadcom Advanced Control Suite 3 Overviewمرید عباسNoch keine Bewertungen
- Cymcap 6.0.5Dokument36 SeitenCymcap 6.0.5mherold2100% (1)
- Smartrecord: Group Administrator'S End User Interface User'S GuideDokument262 SeitenSmartrecord: Group Administrator'S End User Interface User'S GuideChad QuintanillaNoch keine Bewertungen
- BEX Query DesignerDokument111 SeitenBEX Query Designerhisap12367% (3)
- Introduction To ICC AVR: Setting Up A New Project: NEX Robotics Fire Bird III - ICCAVR ManualDokument12 SeitenIntroduction To ICC AVR: Setting Up A New Project: NEX Robotics Fire Bird III - ICCAVR ManualChester Noel Brenes AguirreNoch keine Bewertungen
- 2008 CFast Tutorial 1 PRR Corrected CheatDokument10 Seiten2008 CFast Tutorial 1 PRR Corrected CheatKrissh SaahiNoch keine Bewertungen
- IHSDM UserManualDokument55 SeitenIHSDM UserManualCamilo Méndez100% (1)
- SyncServer S250Dokument6 SeitenSyncServer S250faraz2010Noch keine Bewertungen
- APSI 12.2chapter 18 - KendallDokument43 SeitenAPSI 12.2chapter 18 - KendallLu'luil MaknunaNoch keine Bewertungen
- All Shortcut Keys For MS WordDokument10 SeitenAll Shortcut Keys For MS Wordprasad_786in100% (1)
- Quality Toolkit User GuideDokument127 SeitenQuality Toolkit User GuideGurkirtanNoch keine Bewertungen
- Sage CRM - Guide - Manual 7.2Dokument341 SeitenSage CRM - Guide - Manual 7.2caplusincNoch keine Bewertungen
- Broadband SPICE Model GeneratorDokument88 SeitenBroadband SPICE Model GeneratorKyusang ParkNoch keine Bewertungen
- Fusion HCM Implementation GuideDokument220 SeitenFusion HCM Implementation GuideKrishna Chaitanya100% (2)