Beruflich Dokumente
Kultur Dokumente
Granulity in DBMS
Hochgeladen von
Jugalkishore FatehchandkaCopyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Granulity in DBMS
Hochgeladen von
Jugalkishore FatehchandkaCopyright:
Verfügbare Formate
1.
Granularity of Data Items and Multiple Granularity Locking
All concurrency control techniques assume that the database is formed of a number of named data items. A database record A field value of a database record(1,2,3..) A disk block(address of data in memory) A whole file(data) The whole database(eg:- .mdb file in ms access) . Each take space in memory The granularity can affect the performance of concurrency control and recovery.
2. Granularity Level Considerations for Locking
The size of data items is often called the data item granularity. Fine granularity refers to small item sizes coarse granularity refers to large item sizes. Several tradeoffs(as we exchange money to get the product required or negotiation) must be considered in choosing the data item size. V. For larger the data item size is, the lower the degree of concurrency permitted. VI. For example, if the data item size is a disk block(space in harddisk), If transaction T locks a record B then it must lock the whole disk block X that contains B because a lock is associated with the whole data item (block). VII. Now, if another transaction S, lock a different record C that happens to reside in the same block X in a Conflict OCCCUR BETWEEN LOCK, it is forced to wait. If the data item size was a single record, VIII. On the other hand, the smaller the data item size is, the more the number of items in the database. Because every item is associated with a lock, the system will have a larger number of active locks to be handled by the lock manager IX. More lock and unlock operations will be performed, causing a higher overhead. In addition, more storage space required for the lock table. X. For timestamps, storage is required for the read_TS and write_TS for each data item, and there will be similar overhead for handling a large number of items. Given the above tradeoffs, an obvious question can be asked:What is the best item size? The answer is that it depends on the types of transactions involved. If a typical transaction accesses a small number of records, it is advantageous to have the data item granularity be one record. On the other hand, if a transaction typically accesses many records in the same file, it may be better to have block or file granularity so that the transaction will consider all those records as one (or a few) data items. I. II. III. IV.
22.5.2 Multiple Granularity Level Locking
Since the best granularity size depends on the given transaction, it seems appropriate that a database system should support multiple levels of granularity, where the granularity level can be different for various mixes of transactions. Figure 22.7 shows a simple granularity hierarchy with a database containing two files, each file containing several disk pages, and each page containing several records. This can be used to illustrate a multiple granularity level 2PL protocol, where a lock can be requested at any level. However, additional types of locks will be needed to support
such a protocol efficiently.
Consider the following scenario,with only shared and exclusive lock types, that refers to the example in Figure 22.7. Suppose transaction T1 wants to update all the records in file f1, and T1 requests and is granted an exclusive lock for f1. Then all of f1s pages (p11 through p1n)and the records contained on those pagesare locked in exclusive mode. This is beneficial for T1 because setting a single file-level lock is more efficient than setting n page-level locks or having to lock each individual record. Now suppose another transaction T2 only wants to read record r1nj from page p1n of file f1; then T2 would request a shared record-level lock on r1nj. However, the database system (that is, the transaction manager or more specifically the lock manager) must verify the compatibility of the requested lock with already held locks. One way to verify this is to traverse the tree from the leaf r1nj to p1n to f1 to db. If at any time a conflicting lock is held on any of those items, then the lock request for r1nj is denied and T2 is blocked and must wait. This traversal would be fairly efficient. However, what if transaction T2s request came before transaction T1s request? In this case, the shared record lock is granted to T2 for r1nj, but when T1s file-level lock is requested, it is quite difficult for the lock manager to check all nodes (pages and records) that are descendants of node f1 for a lock conflict. This would be very inefficient and would defeat the purpose of having multiple granularity level locks. To make multiple granularity level locking practical, additional types of locks, called intention locks, are needed. The idea behind intention locks is for a transaction to indicate, along the path from the root to the desired node, what type of lock (shared or exclusive) it will require from one of the nodes descendants. There are three types of intention locks: 1. Intention-shared (IS) indicates that one or more shared locks will be requested on some descendant node(s). 2. Intention-exclusive (IX) indicates that one or more exclusive locks will be requested on some descendant node(s). 3. Shared-intention-exclusive (SIX) indicates that the current node is locked in shared mode but that one or more exclusive locks will be requested on some descendant node(s). The compatibility table of the three intention locks, and the shared and exclusive locks, is shown in Figure 22.8. Besides the introduction of the three types of intention locks, an appropriate locking protocol must be used. The multiple granularity locking (MGL) protocol consists of the following rules: 1. The lock compatibility (based on Figure 22.8) must be adhered to. 2. The root of the tree must be locked first, in any mode. 3. A node N can be locked by a transaction T in S or IS mode only if the parent node N is already locked by transaction T in either IS or IX mode. 4. A node N can be locked by a transaction T in X, IX, or SIX mode only if the parent of node N is already locked by transaction T in either IX or SIX mode. 5. A transaction T can lock a node only if it has not unlocked any node (to
enforce the 2PL protocol).
6. A transaction T can unlock a node, N, only if none of the children of node N
are currently locked by T. Rule 1 simply states that conflicting locks cannot be granted. Rules 2, 3, and 4 state the conditions when a transaction may lock a given node in any of the lock modes. Rules 5 and 6 of the MGL protocol enforce 2PL rules to produce serializable schedules. To illustrate the MGL protocol with the database hierarchy in Figure 22.7, consider the following three transactions: 1. T1 wants to update record r111 and record r211. 2. T2 wants to update all records on page p12. 3. T3 wants to read record r11j and the entire f2 file. Figure 22.9 shows a possible serializable schedule for these three transactions. Only the lock and unlock operations are shown. The notation <lock_type>(<item>) is used to display the locking operations in the schedule. The multiple granularity level protocol is especially suited when processing a mix of transactions that include (1) short transactions that access only a few items (records or fields) and (2) long transactions that access entire files. In this environment, less transaction blocking and less locking overhead is incurred by such a protocol when compared to a single level granularity locking approach.
Das könnte Ihnen auch gefallen
- Grit: The Power of Passion and PerseveranceVon EverandGrit: The Power of Passion and PerseveranceBewertung: 4 von 5 Sternen4/5 (588)
- The Yellow House: A Memoir (2019 National Book Award Winner)Von EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Bewertung: 4 von 5 Sternen4/5 (98)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeVon EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeBewertung: 4 von 5 Sternen4/5 (5795)
- Never Split the Difference: Negotiating As If Your Life Depended On ItVon EverandNever Split the Difference: Negotiating As If Your Life Depended On ItBewertung: 4.5 von 5 Sternen4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceVon EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceBewertung: 4 von 5 Sternen4/5 (895)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersVon EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersBewertung: 4.5 von 5 Sternen4.5/5 (345)
- Shoe Dog: A Memoir by the Creator of NikeVon EverandShoe Dog: A Memoir by the Creator of NikeBewertung: 4.5 von 5 Sternen4.5/5 (537)
- The Little Book of Hygge: Danish Secrets to Happy LivingVon EverandThe Little Book of Hygge: Danish Secrets to Happy LivingBewertung: 3.5 von 5 Sternen3.5/5 (400)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureVon EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureBewertung: 4.5 von 5 Sternen4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryVon EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryBewertung: 3.5 von 5 Sternen3.5/5 (231)
- On Fire: The (Burning) Case for a Green New DealVon EverandOn Fire: The (Burning) Case for a Green New DealBewertung: 4 von 5 Sternen4/5 (74)
- The Emperor of All Maladies: A Biography of CancerVon EverandThe Emperor of All Maladies: A Biography of CancerBewertung: 4.5 von 5 Sternen4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaVon EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaBewertung: 4.5 von 5 Sternen4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaVon EverandThe Unwinding: An Inner History of the New AmericaBewertung: 4 von 5 Sternen4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnVon EverandTeam of Rivals: The Political Genius of Abraham LincolnBewertung: 4.5 von 5 Sternen4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyVon EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyBewertung: 3.5 von 5 Sternen3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreVon EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreBewertung: 4 von 5 Sternen4/5 (1091)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Von EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Bewertung: 4.5 von 5 Sternen4.5/5 (121)
- Her Body and Other Parties: StoriesVon EverandHer Body and Other Parties: StoriesBewertung: 4 von 5 Sternen4/5 (821)
- Cpco B Cisco Prime Collaboration Assurance Guide Advanced 12Dokument622 SeitenCpco B Cisco Prime Collaboration Assurance Guide Advanced 12bouzoualeghaNoch keine Bewertungen
- Smart Connection Reuse - Feature Modifies Some SYN PacketsDokument3 SeitenSmart Connection Reuse - Feature Modifies Some SYN PacketsTadele AlemuNoch keine Bewertungen
- Ason v1 2 PDFDokument1 SeiteAson v1 2 PDFGiorgio Valtolina100% (1)
- Unified Imap Mx-OneDokument83 SeitenUnified Imap Mx-OneStefano MarzinottoNoch keine Bewertungen
- Forticlient: 7.0 Visibility and Controls For Zero Trust Network Access (Ztna) and Secure Access Service Edge (Sase)Dokument6 SeitenForticlient: 7.0 Visibility and Controls For Zero Trust Network Access (Ztna) and Secure Access Service Edge (Sase)Marco CalderonNoch keine Bewertungen
- A Summer Training Report NetworkingDokument44 SeitenA Summer Training Report NetworkingMuditSinghChoudharyNoch keine Bewertungen
- PTT Mpls PSTN Vsat DSLDokument5 SeitenPTT Mpls PSTN Vsat DSLAndy TenorioNoch keine Bewertungen
- Network Programming With GoDokument123 SeitenNetwork Programming With GoTudor Luca100% (1)
- Peperiksaan Percubaan Selangor Ict SPM 09Dokument23 SeitenPeperiksaan Percubaan Selangor Ict SPM 09winyeeNoch keine Bewertungen
- Installation Guide: Lathe Mill-Turn Swiss Wire Router Design MillDokument6 SeitenInstallation Guide: Lathe Mill-Turn Swiss Wire Router Design MillAlex ChancúsigNoch keine Bewertungen
- How To Connect Cisco NX-OS Emulator - Titanium 5.1.2Dokument10 SeitenHow To Connect Cisco NX-OS Emulator - Titanium 5.1.2Rahul DhawanNoch keine Bewertungen
- Hwic 16a DatasheetDokument3 SeitenHwic 16a DatasheetAla JebnounNoch keine Bewertungen
- LTE AdvDokument79 SeitenLTE Advmonel_24671Noch keine Bewertungen
- 7470 - V3 2-4 0 - 2015-05-11 - Manual - EN (ATC)Dokument21 Seiten7470 - V3 2-4 0 - 2015-05-11 - Manual - EN (ATC)ahmed899Noch keine Bewertungen
- The Gifts of Youth Texts2Dokument4 SeitenThe Gifts of Youth Texts2wwe foreverNoch keine Bewertungen
- DanielDokument17 SeitenDanielBaloi-Mitrica DanielNoch keine Bewertungen
- 20.3 ZXDU68 G020 (V5.0) Pole Cabinet - PDDokument8 Seiten20.3 ZXDU68 G020 (V5.0) Pole Cabinet - PDLuis Alfonso Lopez ArroyabeNoch keine Bewertungen
- RBT ServiceDokument15 SeitenRBT ServicenajatNoch keine Bewertungen
- Network Protocols - TutorialspointDokument5 SeitenNetwork Protocols - TutorialspointThusharika ThilakaratneNoch keine Bewertungen
- Welcome To Mac OS X v10.4 TigerDokument32 SeitenWelcome To Mac OS X v10.4 TigerJeffry CuetinNoch keine Bewertungen
- Course Material PostgresqlDokument308 SeitenCourse Material Postgresqlmaleem60% (5)
- Project On Client Server Architecture and Peer To Peer Architecture Submitted byDokument64 SeitenProject On Client Server Architecture and Peer To Peer Architecture Submitted byPooja HemnaniNoch keine Bewertungen
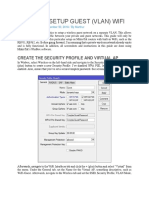
- Mikrotik Setup Guest (Vlan) WifiDokument12 SeitenMikrotik Setup Guest (Vlan) WifiKhodor AkoumNoch keine Bewertungen
- CIS Red Hat Enterprise Linux 8 Benchmark v1.0.1Dokument570 SeitenCIS Red Hat Enterprise Linux 8 Benchmark v1.0.1Julio BarreraNoch keine Bewertungen
- NX 64 Digital Radio LinkDokument6 SeitenNX 64 Digital Radio LinkSo Was RedNoch keine Bewertungen
- Explaining The StorMagic SvSAN Witness Digital PDFDokument8 SeitenExplaining The StorMagic SvSAN Witness Digital PDFpk bsdkNoch keine Bewertungen
- MSC Cyber SecurityDokument74 SeitenMSC Cyber SecuritykidproxyNoch keine Bewertungen
- Wireless Branch Office Network ArchitectureDokument65 SeitenWireless Branch Office Network ArchitectureCisco WirelessNoch keine Bewertungen
- HP Slimline 270-p041d Desktop PC Product Specifications - HP® Customer SupportDokument21 SeitenHP Slimline 270-p041d Desktop PC Product Specifications - HP® Customer Supportonard_deardoNoch keine Bewertungen
- A11yprovider LogDokument6 SeitenA11yprovider LogCris PintoNoch keine Bewertungen