Beruflich Dokumente
Kultur Dokumente
Tutorial TCP IP
Hochgeladen von
Ronald L PfengOriginalbeschreibung:
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Tutorial TCP IP
Hochgeladen von
Ronald L PfengCopyright:
Verfügbare Formate
1
TCP/IP Tutorial
Transmission Control Protocol
Internet Protocol
2
TCP/IP & OSI
In OSI reference model terminology -the
TCP/IP protocol suite covers the
network and transport layers.
TCP/IP can be used on many data-link
layers (can support many network
hardware implementations).
3
Ethernet - A Real Data-Link
Layer
It will be useful to discuss a real data-
link layer.
Ethernet (really IEEE 802.3) is widely
used.
Supported by a variety of physical layer
implementations.
4
Ethernet
Multi-access (shared medium).
Every Ethernet interface has a unique
48 bit address (a.k.a. hardware
address).
Example: C0:B3:44:17:21:17
The broadcast address is all 1s.
Addresses are assigned to vendors by
a central authority.
5
CSMA/CD
Carrier Sense Multiple Access
with Collision Detection
Carrier Sense: can tell when another
host is transmitting
Multiple Access: many hosts on 1 wire
Collision Detection: can tell when
another host transmits at the same
time.
6
An Ethernet Frame
The preamble is a sequence of
alternating 1s and 0s used for
synchronization.
CRC is Cyclic Redundency Check
2 -
Preamble
Destination
Address
Source
Address
Len CRC DATA
7
Ethernet Addressing
Each interface looks at every frame and
inspects the destination address. If the
address does not match the hardware
address of the interface or the
broadcast address, the frame is
discarded.
Some interfaces can also be
programmed to recognize multicast
addresses.
8
Internet Protocol
The IP in TCP/IP
IP is the network layer
packet delivery service (host-to-host).
translation between different data-link
protocols.
9
IP Datagrams
IP provides connectionless, unreliable
delivery of IP datagrams.
Connectionless: each datagram is
independent of all others.
Unreliable: there is no guarantee that
datagrams are delivered correctly or at
all.
10
IP Addresses
IP addresses are not the same as the
underlying data-link (MAC) addresses!
11
IP Addresses
IP is a network layer - it must be
capable of providing communication
between hosts on different kinds of
networks (different data-link
implementations).
The address must include information
about what network the receiving host is
on. This makes routing feasible.
12
IP Addresses
IP addresses are logical addresses (not
physical)
32 bits.
Includes a network ID and a host ID.
Every host must have a unique IP
address.
IP addresses are assigned by a central
authority (the NIC at SRI International).
13
The four formats of IP
Addresses
0 NetID
10
110 NetID
1110 Multicast Address
HostID
NetID HostID
HostID
Class
A
B
C
D
8 bits 8 bits 8 bits 8 bits
14
Class A
128 possible network IDs
over 4 million host IDs per network ID
Class B
16K possible network IDs
64K host IDs per network ID
Class C
over 2 million possible network IDs
about 256 host IDs per network ID
The four formats of IP
Addresses
15
Network and Host IDs
A Network ID is assigned to an
organization by a global authority.
Host IDs are assigned locally by a
system administrator.
Both the Network ID and the Host ID
are used for routing.
16
IP Addresses
IP Addresses are usually shown in
dotted decimal notation:
1.2.3.4 00000001 00000010
00000011 00000100
cs.rpi.edu is 128.213.1.1
10000000 11010101 00000001
00000001
CS has a class B network
17
Host and Network Addresses
A single network interface is assigned a
single IP address called the host
address.
A host may have multiple interfaces,
and therefore multiple host addresses.
Hosts that share a network all have the
same IP network address (the network
ID).
18
IP Broadcast and Network
Addresses
An IP broadcast addresses has a host
ID of all 1s.
IP broadcasting is not necessarily a true
broadcast, it relies on the underlying
hardware technology.
An IP address that has a host ID of all
0s is called a network address and
refers to an entire network.
19
Subnet Addresses
An organization can subdivide its host
address space into groups called
subnets.
The subnet ID is generally used to
group hosts based on the physical
network topology.
10 NetID SubnetID HostID
20
Subnetting
router
Subnet 1
128.213.1.x
Subnet 2
128.213.2.x
Subnet 3
128.213.3.x
21
Subnetting
Subnets can simplify routing.
IP subnet broadcasts have a hostID of
all 1s.
It is possible to have a single wire
network with multiple subnets.
22
Mapping IP Addresses to
Hardware Addresses
IP Addresses are not recognized by
hardware.
If we know the IP address of a host,
how do we find out the hardware
address ?
The process of finding the hardware
address of a host given the IP address
is called
Address Resolution
23
ARP
The Address Resolution Protocol is
used by a sending host when it knows
the IP address of the destination but
needs the Ethernet address.
ARP is a broadcast protocol - every
host on the network receives the
request.
Each host checks the request against
its IP address - the right one responds.
24
ARP (cont.)
ARP does not need to be done every
time an IP datagram is sent - hosts
remember the hardware addresses of
each other.
Part of the ARP protocol specifies that
the receiving host should also
remember the IP and hardware
addresses of the sending host.
25
ARP conversation
HEY - Everyone please listen!
Will 128.213.1.5 please send me his/her
Ethernet address?
not me
Hi Green! Im 128.213.1.5, and my
Ethernet address is 87:A2:15:35:02:C3
26
Services provided by IP
Connectionless Delivery (each
datagram is treated individually).
Unreliable (delivery is not guaranteed).
Fragmentation / Reassembly (based on
hardware MTU).
Routing.
Error detection.
27
IP Datagram
VERS HL
Fragment Offset
Fragment Length Service
Datagram ID FLAG
TTL Protocol Header Checksum
Source Address
Destination Address
Options (if any)
Data
1 byte 1 byte 1 byte 1 byte
28
IP Datagram Fragmentation
Each fragment (packet) has the same
structure as the IP datagram.
IP specifies that datagram reassembly
is done only at the destination (not on a
hop-by-hop basis).
If any of the fragments are lost - the
entire datagram is discarded (and an
ICMP message is sent to the sender).
29
IP Datagram Fragmentation
If packets arrive too fast - the receiver
discards excessive packets and sends
an ICMP message to the sender
(SOURCE QUENCH).
If an error is found (header checksum
problem) the packet is discarded and an
ICMP message is sent to the sender.
30
ICMP Internet
Control Message Protocol
ICMP is a protocol used for exchanging
control messages.
ICMP uses IP to deliver messages.
ICMP messages are usually generated
and processed by the IP software, not
the user process.
31
ICMP Message Types
Echo Request
Echo Response
Destination Unreachable
Redirect
Time Exceeded
Redirect (route change)
there are more ...
32
Transport Layer & TCP/IP
Q: We know that IP is the network layer
- so TCP must be the transport layer,
right ?
A: No.
TCP is only part of the TCP/IP transport
layer - the other part is UDP (User
Datagram Protocol).
33
TCP UDP
IP
Hardware
Process Layer
Transport Layer
Network Layer
Data-Link Layer
Process Process
ICMP, ARP
&
RARP
34
UDP User Datagram Protocol
UDP is a transport protocol
communication between processes
UDP uses IP to deliver datagrams to the
right host.
UDP uses ports to provide
communication services to individual
processes.
35
Ports
TCP/IP uses an abstract destination
point called a protocol port.
Ports are identified by a positive integer.
Operating systems provide some
mechanism that processes use to
specify a port.
36
Ports
Host A Host B
Process
Process
Process
Process
Process
Process
37
UDP
Datagram Delivery
Connectionless
Unreliable
Minimal
Source Port Destination Port
Length Checksum
Data
UDP Datagram Format
38
TCP
Transmission Control Protocol
TCP is an alternative transport layer
protocol supported by IP.
TCP provides:
Connection-oriented
Reliable
Full-duplex
Byte-Stream
39
Connection-Oriented
Connection oriented means that a
virtual connection is established before
any user data is transferred.
If the connection cannot be established
- the user program is notified.
If the connection is ever interrupted -
the user program(s) is notified.
40
Reliable
Reliable means that every transmission
of data is acknowledged by the receiver.
If the sender does not receive
acknowledgement within a specified
amount of time, the sender retransmits
the data.
41
Byte Stream
Stream means that the connection is
treated as a stream of bytes.
The user application does not need to
package data in individual datagrams
(as with UDP).
42
Buffering
TCP is responsible for buffering data
and determining when it is time to send
a datagram.
It is possible for an application to tell
TCP to send the data it has buffered
without waiting for a buffer to fill up.
43
Full Duplex
TCP provides transfer in both directions.
To the application program these
appear as 2 unrelated data streams,
although TCP can piggyback control
and data communication by providing
control information (such as an ACK)
along with user data.
44
TCP Ports
Interprocess communication via TCP is
achieved with the use of ports (just like
UDP).
UDP ports have no relation to TCP
ports (different name spaces).
45
TCP Segments
The chunk of data that TCP asks IP to
deliver is called a TCP segment.
Each segment contains:
data bytes from the byte stream
control information that identifies the data
bytes
46
TCP Segment Format
Destination Port
Options (if any)
Data
1 byte 1 byte
Source Port
Sequence Number
Request Number
1 byte 1 byte
offset Reser. Control Window
Checksum Urgent Pointer
47
Addressing in TCP/IP
Each TCP/IP address includes:
Internet Address
Protocol (UDP or TCP)
Port Number
48
TCP vs. UDP
Q: Which protocol is better ?
A: It depends on the application.
TCP provides a connection-oriented,
reliable byte stream service (lots of
overhead).
UDP offers minimal datagram delivery
service (as little overhead as possible).
49
TCP Lingo
When a client requests a connection it
sends a SYN segment (a special TCP
segment) to the server port.
SYN stands for synchronize. The SYN
message includes the clients ISN.
ISN is Initial Sequence Number.
50
More...
Every TCP segment includes a
Sequence Number that refers to the first
byte of data included in the segment.
Every TCP segment includes a Request
Number (Acknowledgement Number)
that indicates the byte number of the
next data that is expected to be
received.
All bytes up through this number have
already been received.
51
And more...
There are a bunch of control flags:
URG: urgent data included.
ACK: this segment is (among other things)
an acknowledgement.
RST: error - abort the session.
SYN: synchronize Sequence Numbers
(setup)
FIN: polite connection termination.
52
And more...
MSS: Maximum segment size (A TCP
option)
Window: Every ACK includes a Window
field that tells the sender how many
bytes it can send before the receiver will
have to toss it away (due to fixed buffer
size).
53
TCP Connection Creation
Programming details later - for now we
are concerned with the actual
communication.
A server accepts a connection.
Must be looking for new connections!
A client requests a connection.
Must know where the server is!
54
Client Starts
A client starts by sending a SYN
segment with the following information:
Clients ISN (generated pseudo-randomly)
Maximum Receive Window for client.
Optionally (but usually) MSS (largest
datagram accepted).
No payload! (Only TCP headers)
55
Sever Response
When a waiting server sees a new
connection request, the server sends
back a SYN segment with:
Servers ISN (generated pseudo-randomly)
Request Number is Client ISN+1
Maximum Receive Window for server.
Optionally (but usually) MSS
No payload! (Only TCP headers)
56
Finally
When the Servers SYN is received, the
client sends back an ACK with:
Request Number is Servers ISN+1
57
SYN
ISN=X
Client
Server
SYN
ISN=Y ACK=X+1
ACK=Y+1
1
2
3
58
TCP 3-way handshake
Client: I want to talk, and Im starting with
byte number X.
Server: OK, Im here and Ill talk. My first
byte will be called number Y, and I know
your first byte will be number X.
Client: Got it - you start at byte number Y.
1
2
3
?
59
Why 3-Way?
Why is the third message necessary?
HINTS:
TCP is a reliable service.
IP delivers each TCP segment.
IP is not reliable.
60
TCP Data and ACK
Once the connection is established,
data can be sent.
Each data segment includes a
sequence number identifying the first
byte in the segment.
Each segment (data or empty) includes
a request number indicating what data
has been received.
61
Buffering
Keep in mind that TCP is part of the
Operating System. It takes care of all
these details asynchronously.
The TCP layer doesnt know when the
application will ask for any received
data.
TCP buffers incoming data so its ready
when we ask for it.
62
TCP Buffers
Both the client and server allocate
buffers to hold incoming and outgoing
data
The TCP layer does this.
Both the client and server announce
with every ACK how much buffer space
remains (the Window field in a TCP
segment).
63
Send Buffers
The application gives the TCP layer
some data to send.
The data is put in a send buffer, where it
stays until the data is ACKd.
The TCP layer wont accept data from
the application unless (or until) there is
buffer space.
64
ACKs
A receiver doesnt have to ACK every
segment (it can ACK many segments
with a single ACK segment).
Each ACK can also contain outgoing
data (piggybacking).
If a sender doesnt get an ACK after
some time limit (MSL) it resends the
data.
65
TCP Segment Order
Most TCP implementations will accept
out-of-order segments (if there is room
in the buffer).
Once the missing segments arrive, a
single ACK can be sent for the whole
thing.
Remember: IP delivers TCP segments,
and IP in not reliable - IP datagrams can
be lost or arrive out of order.
66
Termination
The TCP layer can send a RST
segment that terminates a connection if
something is wrong.
Usually the application tells TCP to
terminate the connection politely with a
FIN segment.
67
FIN
Either end of the connection can initiate
termination.
A FIN is sent, which means the
application is done sending data.
The FIN is ACKd.
The other end must now send a FIN.
That FIN must be ACKd.
68
FIN
SN=X
App1
App2
ACK=X+1
ACK=Y+1
1
2
4
FIN
SN=Y
3
.
.
.
69
TCP Termination
1
2
3
4
App1: I have no more data for you.
App2: OK, I understand you are done sending.
dramatic pause
App2: OK - Now Im also done sending data.
App1: Roger, Over and Out, Goodbye, Astalavista Baby,
Adios, Its been real ...
camera fades to black ...
70
TCP TIME_WAIT
Once a TCP connection has been
terminated (the last ACK sent) there is
some unfinished business:
What if the ACK is lost? The last FIN will be
resent and it must be ACKd.
What if there are lost or duplicated
segments that finally reach the destination
after a long delay?
TCP hangs out for a while to handle
these situations.
71
Routing Tables
Routers store information about the the
network topology in routing tables.
Lists known networks, distance and router
sequence: which to send to next
Manual or Dynamic Configuration
RIP: TCP/IP Routing Information
Protocol
Enables routers to tell each other about the
network they are minding.
72
Routing Tables
Default Address: minimizes routing
table size.
Uses 0.0.0.0 as the address
Means Send the packet to me if you cant
find the network address
RIP broadcasts updates every 30
seconds. Impacts network.
OSPF: Open Shortest Path First protocol.
Dynamic information gathering
73
Routing Tables
Distance: also the cost of a network.
Simply the count of how many routers,
hops, a packet goes through to reach a
network.
A distance of 0 means the destination
host is on the same network as the
source host.
74
Routing Table
If a network is not recorded in the table,
a packet can not be sent and is dropped
(ignored).
What could be wrong
Sending node misconfigured
Router misconfigured
Routes to that network are down
75
TCP/IP Summary
IP: network layer protocol
unreliable datagram delivery between
hosts.
UDP: transport layer protocol
unreliable datagram delivery between
processes.
TCP: transport layer protocol
reliable, byte-stream delivery between
processes.
76
Conclusion: TCP or UDP ?
Internet commerce ?
Video server?
File transfer?
Email ?
Chat groups?
Robotic surgery controlled remotely
over a network?
Das könnte Ihnen auch gefallen
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeVon EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeBewertung: 4 von 5 Sternen4/5 (5794)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreVon EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreBewertung: 4 von 5 Sternen4/5 (1090)
- Never Split the Difference: Negotiating As If Your Life Depended On ItVon EverandNever Split the Difference: Negotiating As If Your Life Depended On ItBewertung: 4.5 von 5 Sternen4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceVon EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceBewertung: 4 von 5 Sternen4/5 (895)
- Grit: The Power of Passion and PerseveranceVon EverandGrit: The Power of Passion and PerseveranceBewertung: 4 von 5 Sternen4/5 (588)
- Shoe Dog: A Memoir by the Creator of NikeVon EverandShoe Dog: A Memoir by the Creator of NikeBewertung: 4.5 von 5 Sternen4.5/5 (537)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersVon EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersBewertung: 4.5 von 5 Sternen4.5/5 (344)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureVon EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureBewertung: 4.5 von 5 Sternen4.5/5 (474)
- Her Body and Other Parties: StoriesVon EverandHer Body and Other Parties: StoriesBewertung: 4 von 5 Sternen4/5 (821)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Von EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Bewertung: 4.5 von 5 Sternen4.5/5 (120)
- The Emperor of All Maladies: A Biography of CancerVon EverandThe Emperor of All Maladies: A Biography of CancerBewertung: 4.5 von 5 Sternen4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingVon EverandThe Little Book of Hygge: Danish Secrets to Happy LivingBewertung: 3.5 von 5 Sternen3.5/5 (399)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyVon EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyBewertung: 3.5 von 5 Sternen3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)Von EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Bewertung: 4 von 5 Sternen4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaVon EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaBewertung: 4.5 von 5 Sternen4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryVon EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryBewertung: 3.5 von 5 Sternen3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnVon EverandTeam of Rivals: The Political Genius of Abraham LincolnBewertung: 4.5 von 5 Sternen4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealVon EverandOn Fire: The (Burning) Case for a Green New DealBewertung: 4 von 5 Sternen4/5 (73)
- The Way of The Samurai, Shadowrun BookDokument19 SeitenThe Way of The Samurai, Shadowrun BookBraedon Montgomery100% (8)
- The Unwinding: An Inner History of the New AmericaVon EverandThe Unwinding: An Inner History of the New AmericaBewertung: 4 von 5 Sternen4/5 (45)
- Essay WritingDokument74 SeitenEssay Writingtiendn92% (50)
- Lista de Verbos Irregulares en InglésDokument5 SeitenLista de Verbos Irregulares en Inglésaleslo8100% (3)
- Outside inDokument8 SeitenOutside incllewNoch keine Bewertungen
- Frozen - True Treasure 001 (2019) (Digital) (Salem-Empire)Dokument22 SeitenFrozen - True Treasure 001 (2019) (Digital) (Salem-Empire)Ronald L PfengNoch keine Bewertungen
- Deputy Chief Operating OfficerDokument6 SeitenDeputy Chief Operating OfficerRonald L PfengNoch keine Bewertungen
- Matlab FemDokument45 SeitenMatlab Femsohailrao100% (3)
- Birmingham Shopping MapDokument2 SeitenBirmingham Shopping MapRonald L PfengNoch keine Bewertungen
- RiskMgmtFramework To StrategicHRMDokument22 SeitenRiskMgmtFramework To StrategicHRMRonald L PfengNoch keine Bewertungen
- Reading Test NuevoDokument99 SeitenReading Test NuevoRonald L Pfeng100% (2)
- A Theory of Smart CitiesDokument15 SeitenA Theory of Smart CitiesreagrupamentNoch keine Bewertungen
- The Balance On The Balanced ScorecardA Critical Analysis of Some of Its AssumptionsDokument24 SeitenThe Balance On The Balanced ScorecardA Critical Analysis of Some of Its Assumptionsক্লান্তপদাতিকNoch keine Bewertungen
- Bus Timetable Service 87: Coventry To Berkswell Station Via Burton GreenDokument2 SeitenBus Timetable Service 87: Coventry To Berkswell Station Via Burton GreenRonald L PfengNoch keine Bewertungen
- CITYkeys D14 IndicatorsforsmartcityprojectsandsmartcitiesDokument305 SeitenCITYkeys D14 IndicatorsforsmartcityprojectsandsmartcitiesRonald L PfengNoch keine Bewertungen
- Teacher - S Notes For The Jungle BookDokument3 SeitenTeacher - S Notes For The Jungle BookMurely Ponnusamy100% (4)
- Ielts Listening 2Dokument20 SeitenIelts Listening 2Ronald L PfengNoch keine Bewertungen
- 28 John Grace Street - Lettings Details 2017Dokument2 Seiten28 John Grace Street - Lettings Details 2017Ronald L PfengNoch keine Bewertungen
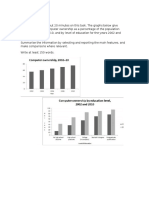
- The Bar Charts Show Data About Computer OwnershipDokument2 SeitenThe Bar Charts Show Data About Computer OwnershipRonald L PfengNoch keine Bewertungen
- 72 Climate-Change CanDokument8 Seiten72 Climate-Change CanRonald L PfengNoch keine Bewertungen
- British Council IELTS Online ApplicationDokument5 SeitenBritish Council IELTS Online ApplicationRonald L PfengNoch keine Bewertungen
- 0 IELTS Band ScoreDokument1 Seite0 IELTS Band ScoreRonald L PfengNoch keine Bewertungen
- Studyguide ImportantrulesDokument1 SeiteStudyguide Importantrulesahmadmasood786Noch keine Bewertungen
- Teacher - S Notes For The Jungle BookDokument3 SeitenTeacher - S Notes For The Jungle BookMurely Ponnusamy100% (4)
- CCleaner 5.04 LicenseDokument2 SeitenCCleaner 5.04 Licenseg1859602Noch keine Bewertungen
- Resumen Gramatica InglesaDokument49 SeitenResumen Gramatica InglesaFabián Araneda Baltierra100% (1)
- Grammar: "To Be" ("To Be or Not To Be... ")Dokument3 SeitenGrammar: "To Be" ("To Be or Not To Be... ")Ronald L PfengNoch keine Bewertungen
- FO Team PDFDokument2 SeitenFO Team PDFRonald L PfengNoch keine Bewertungen
- Iot Practical 1Dokument15 SeitenIot Practical 1A26Harsh KalokheNoch keine Bewertungen
- Inclusions in Gross IncomeDokument2 SeitenInclusions in Gross Incomeloonie tunesNoch keine Bewertungen
- Teacher Resource Disc: Betty Schrampfer Azar Stacy A. HagenDokument10 SeitenTeacher Resource Disc: Betty Schrampfer Azar Stacy A. HagenRaveli pieceNoch keine Bewertungen
- Chapter-4 Conditional and Iterative Statements in PythonDokument30 SeitenChapter-4 Conditional and Iterative Statements in Pythonashishiet100% (1)
- Acm Queue PDFDokument12 SeitenAcm Queue PDFShubham Anil ShahareNoch keine Bewertungen
- Hormone Replacement Therapy Real Concerns and FalsDokument13 SeitenHormone Replacement Therapy Real Concerns and FalsDxng 1Noch keine Bewertungen
- What Is The Effective Method For Dissolution of HDPE and LDPE - PDFDokument12 SeitenWhat Is The Effective Method For Dissolution of HDPE and LDPE - PDFAliNoch keine Bewertungen
- Standards Guide 1021 1407Dokument8 SeitenStandards Guide 1021 1407Anjur SiNoch keine Bewertungen
- Comparativa Microplex F40 Printronix P8220 enDokument1 SeiteComparativa Microplex F40 Printronix P8220 enangel ricaNoch keine Bewertungen
- Electrical System in AENDokument21 SeitenElectrical System in AENNilesh PatilNoch keine Bewertungen
- International Beach Soccer Cup Bali 2023 October 4-7 - Ver 15-3-2023 - Sponsor UPDATED PDFDokument23 SeitenInternational Beach Soccer Cup Bali 2023 October 4-7 - Ver 15-3-2023 - Sponsor UPDATED PDFPrincess Jasmine100% (1)
- Inkolo Namasiko Kuyamakha Umuntu - Brainly - inDokument1 SeiteInkolo Namasiko Kuyamakha Umuntu - Brainly - inxqxfkqpy5qNoch keine Bewertungen
- Guide Rail Bracket AssemblyDokument1 SeiteGuide Rail Bracket AssemblyPrasanth VarrierNoch keine Bewertungen
- Sip TrunkDokument288 SeitenSip TrunkSayaOtanashiNoch keine Bewertungen
- Control Flow, Arrays - DocDokument34 SeitenControl Flow, Arrays - DocHARIBABU N SEC 2020Noch keine Bewertungen
- 04 10 ALINT DatasheetDokument2 Seiten04 10 ALINT DatasheetJoakim LangletNoch keine Bewertungen
- Bai Tap Avtc2 PrepositionsDokument5 SeitenBai Tap Avtc2 PrepositionsShy NotNoch keine Bewertungen
- Reflection Frog 1Dokument3 SeitenReflection Frog 1mariamNoch keine Bewertungen
- Chiba International, IncDokument15 SeitenChiba International, IncMiklós SzerdahelyiNoch keine Bewertungen
- Role of Quick Response To Supply ChainDokument15 SeitenRole of Quick Response To Supply ChainSanuwar RashidNoch keine Bewertungen
- Fish Siomai RecipeDokument12 SeitenFish Siomai RecipeRhyz Mareschal DongonNoch keine Bewertungen
- CHAPTER I KyleDokument13 SeitenCHAPTER I KyleCresiel Pontijon100% (1)
- The Morning Calm Korea Weekly - August 22,2008Dokument24 SeitenThe Morning Calm Korea Weekly - August 22,2008Morning Calm Weekly NewspaperNoch keine Bewertungen
- NS1 UserManual EN V1.2Dokument31 SeitenNS1 UserManual EN V1.2T5 TecnologiaNoch keine Bewertungen
- Flyweis Services Pvt. LTDDokument11 SeitenFlyweis Services Pvt. LTDFlyweis TechnologyNoch keine Bewertungen
- Antibiotic I and II HWDokument4 SeitenAntibiotic I and II HWAsma AhmedNoch keine Bewertungen
- TLE-Carpentry7 Q4M4Week4 PASSED NoAKDokument12 SeitenTLE-Carpentry7 Q4M4Week4 PASSED NoAKAmelita Benignos OsorioNoch keine Bewertungen
- Where Business Happens Where Happens: SupportDokument19 SeitenWhere Business Happens Where Happens: SupportRahul RamtekkarNoch keine Bewertungen
- Materials Selection in Mechanical Design - EPDF - TipsDokument1 SeiteMaterials Selection in Mechanical Design - EPDF - TipsbannetNoch keine Bewertungen