Beruflich Dokumente
Kultur Dokumente
Configure Emergency Access
Hochgeladen von
Vamsi Krishna PeddineniCopyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Configure Emergency Access
Hochgeladen von
Vamsi Krishna PeddineniCopyright:
Verfügbare Formate
Configure Emergency Access (EAM) in GRC
10
Hello!
Configuring EAM in GRC 10 isnt a difficult task, but there are some details you have to take
into account. The document AC 10.0 Pre-Implementation From Post-Installation to First
Emergency Access is useful, but it doesnt consider all the details. Here Ill try to give you a
complete explanation about how to configure EAM successfully.
Configure Parameters:
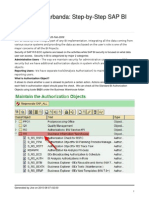
In GRC Box, execute transaction SPRO and navigate to here:
The following parameters should be set according to the table:
Parameter Recommended value (for
initial configuration)
4000Application type 1
4001Default Firefighter
Validity Period (Days)
30
4002Send Email Immediately YES
4003Retrieve Change Log YES
4004Retrieve System log YES
4005Retrieve Audit log YES
4006Retrieve OS Command
log
YES
4007Send Log Report
Execution Notification
Immediately
YES
4008Send FirefightId Login
Notification
YES
4009Log Report Execution
Notification
YES
4010Firefighter ID role name Chose a role name, for
example
Z_SAP_GRC_SPM_FFID
For a complete description of the above parameters, please refer to the guide:
https://service.sap.com/instguides - > SAP BusinessObjects Governance, Risk and Compliance (GRC) ->
Acess Control -> Release 10.0 -> Maintaining Configuration Settings Guide - SAP AC 10.0
You might want to change some of them; the recommended values only serve as a guide for the initial
configuration.
Changes in the parameters table will be included in a transport request, you should release the
transport to your QA/PROD systems when you finish the EAM tests and adapt the parameters according
to your requirements.
Parameter 4010: Whats for?
If youve been working with GRC 5.3, this parameter should sound weird to you.
The purpose is to identify to the application that the user who is logging on to the target system is a
Firefighter ID. The target system makes a call to the GRC Box and reads this configuration to check if the
user has this role assigned to them.
That means that you have to create the role that youve set in parameter 4010 in all the target systems
with the exact name provided there. Usually, you copy it from the standard SAP_GRC_SPM_FFID (it
contains RFC authorizations).
Only the users who have that role assigned in the target system will be available for selection in the GRC
Box as Firefighters IDs.
Kindly check note: 1668255 - Firefighter ID role name for Param ID 4010
For more information regarding default roles provided by SAP, please refer to Security Guide available
here:
https://service.sap.com/instguides - > SAP BusinessObjects Governance, Risk and Compliance
(GRC) -> Acess Control -> Release 10.0 -> Security Guide - SAP Access Control 10.0
Adding connector to the SUPMG Scenario:
Please check: Note 1562760 - AC10.0 - Intergration Scenarios to Connector link
At this point you have already created the connectors.
Now you have to link the corresponding connectors to the SUPMG scenario:
Click here:
And:
Required roles in the GRC Box:
SAP provides standard roles that must be copied to the customer namespace. For this sample
configuration you should need at least to create a copy for the following roles and generate the
corresponding profiles:
SAP_GRAC_SUPER_USER_MGMT_OWNER Emergency Access management
owner
SAP_GRAC_SUPER_USER_MGMT_CNTLR Emergency Access management
controller
SAP_GRAC_SUPER_USER_MGMT_USER Emergency Access management
firefighter
SAP_GRAC_SUPER_USER_MGMT_ADMIN Emergency Access management
administrator
SAP_GRAC_BASE Gives basic authorizations
required for all AC users. You
must assign this role to all AC
users.
SAP_GRAC_NWBC
Gives the authorizations to
launch NWBC. You must
assign this role to all AC
users.
You can just name them as Z_<full standard role name> or use a naming convention according to your
company requirements.
CAUTION: Please, follow he instructions provided in tha attachment of note:
Note 1663949 - EAM Authorization Fixes for Central Owners and Reason Codes
There are some changes you have to made to the standard roles and also there's a complete
explanation of the authorization objects.
For more information, kindly refer to the Security Guide (link provided above).
Security considerations for EAM Roles:
Kindly read a specific authorization guide for EAM that is attached to the note:
Note 1663949 - EAM: Authorization Fixes for Central Owners and Reason Codes
and take into account the authorization concept for the roles:
1730649 - Firefighter owner can assign ANY Firefighter ID to Firefighter User
"As per the functionality in AC10, we have concept of role based authorization. If a user is
having SAP_GRAC_SUPER_USER_MGMT_OWNER role at the backend, then he should be
able to assign any FFID to any Firefighter user.
The user Assigned with the Role of EAM Admin SAP_GRAC_SUPER_USER_MGMT_ADMIN
and EAM Owner SAP_GRAC_SUPER_USER_MGMT_OWNER can do all available owner
action for all connector.
The Auth. Object used for firefighter Maintenance is GRAC_FFOWN & GRAC_OWNER"
---->>> vote for a simpler way if you disagree with this weird role-based model !! -->>> Simple
setting for EAM owner/controller authorization
If you are not going to use ARM workflows and you want to restrict Owners, please have a look
at the thread:
GRC EAM Authorizations: Few Anomalies in Standard Roles
(Provided by Akshay Gupta)
Required users in the GRC Box:
In order to show a sample for testing, Its necessary to create (or use existing ones) three users:
FF_OWNER: This user will serve as owner for the firefighter ID. It should be assigned to the role
Z_SAP_GRAC_SUPER_USER_MGMT_OWNER
FF_CONTROL: This is the firefighter controller. You assign Z_SAP_GRAC_SUPER_USER_MGMT_CNTLR.
CAUTION: This user MUST have a valid e-mail address maintained in SU01 if you want the controller to
receive notifications via e-mail.
FIREFIGHTER: This is the firefighter user, who will be able to access in the target system with the
Firefighter ID. You assign Z_SAP_GRAC_SUPER_USER_MGMT_USER in addition to the base roles. If you
don't assign the base roles you won't see the user (FIREFIGHTER in this case) available for selection in
the Firefighters IDs.
<your user>: The user who is going to perform the configurations, must have at least the role
Z_SAP_GRAC_SUPER_USER_MGMT_ADMIN assigned.
In addition to all the mentioned roles above, all users must have the roles Z_SAP_GRAC_NWBC and
Z_SAP_GRAC_BASE assigned.
For a theoretical explanation of the users and its responsibilities, refer to
https://help.sap.com/saphelp_grcac10/helpdata/en/16/404938695540b398a5e76fe8cfb067/frameset.h
tm
Required roles in the target system:
In the target system you have to make a copy of the role SAP_GRAC_SPM_FFID and generate the profile.
CAUTION: The name of this role MUST be the same configured in the parameter 4010 in the GRC Box. In
this example: Z_SAP_GRC_SPM_FFID.
Required users in the target system:
You have to create a user (FIREFIGHTER_ID) in the target system with the corresponding roles required
roles/profiles according to your requirements. In addition you must assign to the FIREFIGHTER_ID the
role Z_SAP_GRC_SPM_FFID.
This user should be of type: Service as per note 1702439
The following note describes an issue you'll face with this kind of users: Note 1586989 - Object
Services icon not available in Firefighter ID session
I'll update this document when a specific note for GRC 10 is released regarding this issue.
Take into account this important note for service users: 1945098 - Service users are not
considered in decentralized firefighter
Creating central Owners and controllers:
Access to the NWBC: http://<server>:<port>/nwbc/ or execute Tcode NWBC in the GRC Box.
Go to the Setup tab and:
Create entries for the Firefighter controller and owner:
Creating reason codes:
You have to create at least one reason code to be able to use the firefighter ID later.
Associate the entry to the corresponding target system.
Synchronization Jobs:
In accordance with note: 1585079
You have to execute the synchronization Jobs in order to make the FF IDs available in GRC Box
for selection:
Please make sure that you have performed following configuration steps:
1. Integration Scenarios are configured as explained in note 1562760
2. Please make sure the Firefighter role is assigned to Firefighter IDs in the corresponding
client system and that the same role has been given as parameter value for configuration
parameter 4010. Configuration parameters can be configured in the transaction code SPRO =>
Governance, Risk & Compliance => Access Control => Maintain Configuration Settings
3. Run User/Role/Profile/Auth synchronization jobs. The Link to run these jobs can be found
Under transaction code SPRO => Governance, Risk & Compliance => Access Control =>
Synchronization Jobs.
Once you have executed the Repository Sync job with the corresponding target connector, the FF
ID will be available for selection in the GRC Box.
See also Note 1668255
Once you are done with the above steps, re-run an Incremental/Full User Sync for the
Firefighter IDs with the Firefighter Role to be SYNCed into the GRC box.Now re-launch the
application via NWBC or Portal and then search for the Firefighter ID and this should be
available in Firefighter ID list.
Assign Owners:
Assign Firefighter IDs to Firefighters
Here you assign the Firefighter ID to the corresponding Firefighters users (one or more)
And in the controller tab set the controller user:
Mass upload of assignments: In case you need to perform an initial load or a mass maintenance you can
use one of the programs provided for migration as described here 1744929 - Mass Upload of
Assignments for EAM
Firefighter collector Job:
Execute tx. GRAC_SPM_LOG_SYNC and schedule the log collection periodically as per note: 1617529
Known problems with time zones:
Note 1595462 - Logs not visible in the SPM Reports
Note 1775432 - Transaction logs are not getting captured by GRC 10.0
Known problem when connector is set to *:
Note 1726157 - GRAC10 EAM GRAC_SPM_LOG_SYNC_UPDATE doesn t collect data
Performance problems :
Note 1750024 - GRAC - Performance of the SPM Log Sync
You'll find many notes in SAP Marketplace related to performance issues.
Other errors:
Note 1773855 - EAM10.0 Sometimes Workflows and transaction logs are missed
Note 1776070 - GRC EAM program is giving a short dump and no logs generated
Note 1731923 - EAM:Transaction Logs are not being captured while sync
Have you lost EAM logs?
If you lost some EAM logs and the data is still available in the plug-in system you can schedule a time-
based special sync:
1934127 - GRC10 EAM: EAM recovery program to retrieve missing log and to generate the missing
workflows
E-mail configuration (Centralized Firefighter):
If you want the controller to receive e-mails (firefighter log on notification and firefighter session details)
you have to check the following:
Make sure your Basis team has properly configured outgoing e-emails from GRC Box (Tx. SCOT)
Controller notification method was set to: Email (see above)
SPRO parameters:
4002 Send E-mail Immediately YES
4007 Send Log Report Execution
Notification Immediately YES
4008 Send FirefightID Logon Notification YES
4009 Log Report Execution Notification YES
Controller user (FF_CONTROL) has "Comm.Method set to E-Mail in SU01 and has a valid e-
mail address.
WF-BATCH User must also have an e-mail address in SU01; otherwise youll get the following
error in tx. SLG1:
According to the configuration settings guide:
You can change the parameter and use another user to send the e-mails.
After executing the GRAC_SPM_LOG_SYNC_UPDATE, please execute tx. SOST and check if the e-
mails were generated (you have to access the firefighter to get the e-mails).
Implement Firefighter user Exit:
Despite the Firefighter ID password is changed by the application each time you start the
firefighter (you can check it via change documents in the target system), Firefighter Ids need to
be restricted from Logging in into SAP System directly via SAP GUI. For this purpose either we
need to create and modify the SAP User Login Exit.
Check
1545511 - Firefighter User Exit
1735971 - User exit to prevent direct firefighter login
Security Issue???: http://scn.sap.com/thread/3273562
If the user exit is properly implemented you'll get the following message when trying to log-on
directly with a Firefighter ID (or any user assigned to role configured in the parameter 1090
in the plug-in System !!!):
Required RFC connections for EAM:
Please check: Note 1701047 - Is it mandatory to use trusted connection in the RFC destination
for Firefighter Connector?
"Yes it is mandatory to make a trusted relationship so that communication can be established
between the GRC system and the plug-in."
This topic has been discussed here (see comments below). The note is for Centralized FF and
true is that it works anyway with non trusted connection. In case of decentralized model the
connector is used to retrieve logs, so it doesn't need to be trusted.
Links to more documentation:
Note 1394281 - Superuser Privilege Management Log Report Content
Note 1065048 - Firefighter Log Not sent in Email to Controller <<- for 5.3, but useful
Note 1618040 - Performance fix for SPM transaction logs for large systems
Note 1732938 - Firefighter incorrect language setting on ERP Production
Note 1730649 - Firefighter owner can assign ANY Firefighter ID to Firefighter User
Note 1747283 - EAM: Entries in EAM logon pad not Visible for a firefighter
Decentralized firefighting (as in GRC 5.3) is
available as of GRC 10.0 SP10
As of SP10, Emergency Access decentralized firefighting features are available.Users can install
and use the EAM Launchpad to perform ID-based firefighting directly on plug-in systems. This
means that Firefighter session could be started from the plugin system itself without the need to
access the GRC Box. This approach was used in GRC 5.3. With GRC 10 SP10 you can chose
between centralized or decentralized firefighting.
The most important advantage of decentralized firefighting is that you can continue using
firefighter even when the GRC Box is down. In my opinion, its also more user-friendly since
the firefighter doesnt have to log on to GRC Box in order to start the firefighting session, he/she
only needs to execute a transaction in the plugin system. For some companies, the centralized
approach is better since the user access to a system (GRC Box) and can start firefighter sessions
in multiple systems.
Bottom line, the most important thing is that with SP10 you have to option to choose and below
youll find information thatll help you to configure decentralized Firefighting.
The idea of a decentralized firefighting was submitted by Daniela Bork on SAP Idea Place:
Access Firefighter application locally in AC10
So, if you have a good Idea, please share it with SAP customers and employees in the Idea Place
and maybe it becomes a new functionality!
Main documentation can be found in the guide attached to the note: Note 1690964 - Emergency
Access Management Overview Documentation
In the GRC Box a new parameter is available and must be set accordingly:
Under transaction SPRO, navigate to here:
And create a new entry for parameter 4015 which has to be set to the value YES
Additionally a new synchronization job is available and must be executed in order to synchronize
the EAM data from GRC Box to the plug-in system. Remember that configurations (firefighter
assignments, controllers, owners, reason codes, etc.) are still maintained in a centralized way, i.e
in the GRC Box.
In order to sync this data with the plug-in, a new job is available and can be found here:
In the connector field you have to set the corresponding plug-in connector. In order to keep you
plugin system updated with the changes you made in the GRC Box, this report should be
scheduled periodically, I think hourly would be fine. In addition, if you have multiple plug-in
systems, you should follow the same approach as with the log synch: create individual jobs for
each connector instead of a unique job with connector value *.
Configuration in the plug-in system
In the plug-in system youll find new activities under SPRO:
These activities are described in here: 1804207 - GRC EAM 10.0: Configuration parameters introduced in
SP10 for EAM
If you havent set the parameter 1000 in the plug-in system, youll have to do it in order to use
decentralized firefighting, otherwise youll get an error message as described here:1800772 - Error 'No
Destination specified' when using transaction /GRCPI/GRIA_EAM
Then, check the parameter as described below:
If the parameter 1000 isnt present you have to create it and set the value to an RFC destination
pointing to the system itself:
Since this configuration is transported I used to recommend to create a new RFC destination in
DEV, QAS and PRD system with the same name, lets say GRC_CONNECTOR and transport
the configuration throughout your entire landscape. But nowadays, this parameter is used in the
log-in notification e-mail to the controller, and if you are going to use that functionality you
might want to create a system name independent connector, i.e. "P01CLNT800" and temporally
change the client settings in SCC4 in order to allow the table modification in production systems.
The RFC connection does not require a user. It just has to point to the correct system/instance
and a specific client.
Required users
Controllers have to be created in the GRC Box as well as with centralized firefighting. In
addition these users must exist in the plugin system and have a valid e-mail address because
login notifications are sent from plug-in system
With the decentralized scheme its not necessary to create the firefighter users in the GRC Box,
because theyll start firefighter transaction from the plug-in system.
E-mail considerations (Decentralized model)
Log-in notifications are sent from the plug-in system (the e-mail is sent with the Firefighter user,
so remember to properly configure it in SU01):
But, as with the Centralized approach, Log notifications are sent from GRC Box
These requires a proper mail configuration (tx. SCOT) in both systems: plug-in and GRC Box.
General Note for problems with e-mail in decentralized EAM:
1877706 - Login and Log Report Notifications are not being sent to the firefighter controller in
case of decentralized firefighting
Plug-in roles
Youll have to create a new role as a copy of SAP_GRAC_SUPER_USER_MGMT_USER.
You should add the following authorization to it:
For some NW releases ACTVT=02 will be also required. Kindly Check 1753459 - EAM:
S_USER_GRP with ACTVT=02 required
This role is assigned to the firefighter users. Bear in mind that these users should not have access
to user maintenance transactions, for example SU01. If the firefighter IDs are properly assigned
to a group and you can restrict the CLASS field this is not a big issue, since despite they could
change the password, they wont be able to access because the user exit is implemented in order
to prevent it.
This extra authorization was documented by SAP in November 2013 in the note:
1944417 - In decentralized firefighting firefighter is not able to perform firefighter logon
Previous versions of this post contain this solution as unofficial, but now has become official.
"..The firefighter is not having the authorization to change the passowrd. In centralized
firefighting the password is changed by RFC user, but in decentralized version as there is not
RFC connection, the password is changed by firefighter. The functionality works as in EAM
5.3...."
In addition to this role you also have to create roles for administrator and owner. Remember that
extending the validity period is a new activity available in the plug-in system and owners and
administrators should have access to it.
Known Problems ( specific to decentralized EAM)
Note 1849289 - For Decentral EAM No Reasoncode and Activity desc captured
Specific for CUA systems:Note 1814400 - Decentral call is opening different session in CUA
(Documentation provided by:Guido Stusinsky)
Common Issue: Logon screen appears when starting FF session
It's possible that we get a log on screen after starting the FF session. This is an incorrect behavior
since the user doesn't need to enter the FF ID password.
Here some tips:
Check the RFC connection. Perform an authorization check in SM59 to check if the RFC user is
OK.
Check that the RFC is pointing to the correct client.
Look for dumps in ST22 in the plugin system.
Check if the FF ID password is productive, reset the password or check with changing the user to
type "Service" if you are using "Dialog" user for FF ID.
CUA Systems: Since EAM requires to change the password of the Firefighter ID each time you
log-on from the launchpad, the CUA's initial password needs to be set as 'Everywhere' or
'Proposal'. Please check point 6 of note 1861981 - Things to check when error message 'Error in
opening RFC destination' appears in GRAC_SPM
Have a look at the following notes:
1861981 - Things to check when error message 'Error in opening RFC destination' appears in
GRAC_SPM
1777094 - EAM log on is not possible with the error: 'Error found in RFC (plug in system) and
respective logon\logons are disabled'
Note 1886332 - GRC 10.0 EAM prompts for user/password while logging
Note 1872709 - Logon popup shown when launching the EAM session
Common Issue II: Logs are not getting captured
If you cannot get the FF Logs don't get frustrated. This is not unusual. I'll give some tips (and hopefully
you can help in order to add more!):
General recommendations an errors are included in note: 2029368 - EAM Synchronization Jobs
Not Completing Resulted in Data Loss
It could be to an authorization issue with the RFC user. The usual one is related to object
S_TOOLS_EX as described 1916172 - User Action Usage Sync Error - User ID showing as -- ? --
. Anyway you can trace the RFC user via ST01 in the back-end while performing a log synch and
check if you have some authorization issue.
Clock skew: check the system time in the GRC box and compare with the plugin system. You can
do it by check System -> Status at "the same time" in both systems. A clock skew of 1-2 minutes
can cause severe problems in the log collection. Time zones do not need to be same... it doesn't
make sense by the way, cause having the GRC box in a Server in India and the ECC in Argentina
will be impossible. Even here in South America we usually work with Servers in Chile, Brazil,
Argentina and these countries sometimes do not use the same time zone. So...using different
time zones has to be a possibility, but you have to be very careful with the clock skews, and if you
have differences ask your Server Admins to check it and use a NTP Sever to keep all systems
synched.
Check that you have data in transaction STAD and ST03N in the plugin system for the FF ID
you're trying to get the logs. If necessary check with your Basis team if the Statics are being
collected properly.Try executing an action usage synch and check in table GRACACTUSAGE if
you have data for the FF ID.
Remember to schedule the job hourly as per SAP recommendation an not running it just when
you want to get the logs. This probably will cause lose of data.
Check transaction SLG1 in the GRC Box in order to know the result of the collection. Sometimes
you get there the exact cause, for example "RFC Timeout", "RFC error", etc.
Check for dumps in the plugin system (transaction ST22) and look for dumps created by the RFC
user. TIME_OUT or memory related dumps are usual for large systems.
SAP has released many enhancements and corrections related to log collection. Just to name
one of them that isn't included in
the latest SP: 1962440 - GRC EAM - Change Log Collection Performance Enhancement but
you'll find others in the marketplace an probably SAP will release more. Make sure you have all
the corrections applied.
A last resort when you have problems with log collection (due to performance) would be to create
an index on CDHDR table if the dumps in the back-end are related to some queries with such
tables and indicate that. The official note is 1741151 - GRC 10.0 Indexing on CDHDR table in
case of time out issue due to huge data Creating an index on such table is something that you
have to discuss with your DBA, Basis and Development teams. You have to be very careful with
that and you should ask SAP if this is recommended to your scenario and there're no chances to
improve the queries in the code. The table stores change documents and also can be reduced via
archiving and this should be also an option to discuss before creating an index.
SAP released a note recently indicating that mass activities cannot be performed by Firefighters:
1378276 - Mass Transaction support through Firefighter product
Common Issue III: Firefighter sessions remain open
SAP considers that such issue isn't specific to EAM: 1290018 - Firefighter ID is locked in Superuser
Privilege Management
Co-existence of firefighting models
Both models could be used. The decentralized firefighter configuration doesnt block the
centralized firefighter approach. Since you can start only one firefighter session at a time, you
cannot use both at the same time and this is automatically controlled by the application.
Administration functions
The administration functions are maintained in the GRC Box. The decentralized firefighting adds
a couple of tasks in the plugin system such as logging notification customizations and the
possibility to extend the validity date of firefighters if the GRC Box is down. Youll find a nice
illustration in the guide attached to note mentioned earlier (1690964).
Access to decentralized FF
Some standard roles do not include the correct SPM transaction. In order to start decentralized
FF the Firefighter user have to type /n/GRCPI/GRIA_EAM in the transaction bar. If you use
other tcodes might see an empty table, and if you don't use /n you'll receive a message stating
something like it's impossible to execute this function.
GRC 10.1 - What's new for EAM??
In GRC 10.1 a new option is included in order to set the Firefighter ID Role (parameter 4010) in
a system-independant manner.
SPRO documentation:
"This allows you the flexibility of specifying different firefighter I D roles per plug-in system.
For example, you can specify thefollowing:
For Target Connector ERP_001, thefirefighter I D roleis Z_SAP_FF01.
For Target Connector ERP_002, thefirefighter I D roleis Z_SAP_FF02.
I f you choose to not use this option, theapplication uses the role name specified in theconfiguration parameter Firefighter I D Role Name4010 for all
systems including plug-in systems"
Das könnte Ihnen auch gefallen
- Cloud Integration A Complete Guide - 2019 EditionVon EverandCloud Integration A Complete Guide - 2019 EditionBewertung: 5 von 5 Sternen5/5 (1)
- GRC 10 Configure Emergency AccessDokument16 SeitenGRC 10 Configure Emergency AccessgvkrishnaNoch keine Bewertungen
- What You Need To Know and Benefits To Expect From Implementing SAP GRC Release 12.0Dokument34 SeitenWhat You Need To Know and Benefits To Expect From Implementing SAP GRC Release 12.0Melanie LeppersNoch keine Bewertungen
- Security UpgradeDokument10 SeitenSecurity UpgradeSuneetha VejandlaNoch keine Bewertungen
- C AUDSEC 731 PDF Questions and AnswersDokument5 SeitenC AUDSEC 731 PDF Questions and Answersflaviolink2466Noch keine Bewertungen
- Configuration Emergency Access Management 12Dokument42 SeitenConfiguration Emergency Access Management 12Mehmet F BATURNoch keine Bewertungen
- When To Use SU24?: Important!!! SAP Security Interview Questions SAP Security-AuthorizitionDokument3 SeitenWhen To Use SU24?: Important!!! SAP Security Interview Questions SAP Security-AuthorizitionKarthik EgNoch keine Bewertungen
- How To Create A New Launchpad and Associate To A RoleDokument5 SeitenHow To Create A New Launchpad and Associate To A Rolevtech070% (1)
- Portal Roles and AuthorizationsDokument62 SeitenPortal Roles and AuthorizationsArmando Agostini100% (1)
- SSO Between SAP Enterprise Portals To BO & SAP BO To BW SSO Configuration Document - SAP BlogsDokument16 SeitenSSO Between SAP Enterprise Portals To BO & SAP BO To BW SSO Configuration Document - SAP Blogssrinivas kolluriNoch keine Bewertungen
- SU25 Profile UpgradationDokument2 SeitenSU25 Profile Upgradationsri_plnsNoch keine Bewertungen
- Configure SsoDokument4 SeitenConfigure SsoRobbin PintoNoch keine Bewertungen
- Emergency Access ManagementDokument5 SeitenEmergency Access ManagementPabitraKumarNoch keine Bewertungen
- SAP Identity Management 8.0 UnderstandingDokument11 SeitenSAP Identity Management 8.0 UnderstandingChandan KumarNoch keine Bewertungen
- SAP GRC 12 EAM On HDB Using Web IDEDokument18 SeitenSAP GRC 12 EAM On HDB Using Web IDEVinay Prakash DasariNoch keine Bewertungen
- BRF Plus Flate Rule - GRC IntegrationDokument12 SeitenBRF Plus Flate Rule - GRC IntegrationTEndaiNoch keine Bewertungen
- GRC BO Access ControlDokument6 SeitenGRC BO Access ControlJohn SpartonNoch keine Bewertungen
- Reporting Authorizations in SAP BWDokument13 SeitenReporting Authorizations in SAP BWsatyamkalaNoch keine Bewertungen
- Background Jobs in Risk Analysis and Remediation 5Dokument8 SeitenBackground Jobs in Risk Analysis and Remediation 5Shiva KumarNoch keine Bewertungen
- Pradeep Pothala Sap ResumeDokument3 SeitenPradeep Pothala Sap Resumekeerthi reddyNoch keine Bewertungen
- The Ultimate C - C - GRCAC - 12 - SAP Certified Application Associate - SAP Access Control 12.0Dokument2 SeitenThe Ultimate C - C - GRCAC - 12 - SAP Certified Application Associate - SAP Access Control 12.0Stefan100% (1)
- And Products in Data Processing. It Is A Standard Software PackageDokument33 SeitenAnd Products in Data Processing. It Is A Standard Software PackageShafiq Ahmed ShahbazNoch keine Bewertungen
- BW SecurityDokument2 SeitenBW SecurityBOBBILINoch keine Bewertungen
- RMS Role Mapper TrainingDokument23 SeitenRMS Role Mapper TrainingCesar ArevaloNoch keine Bewertungen
- RSUSR 008 009 New - Critical AuthorizationsDokument10 SeitenRSUSR 008 009 New - Critical Authorizationsgreat_indianNoch keine Bewertungen
- PC 10.1Dokument33 SeitenPC 10.1ManoharManuNoch keine Bewertungen
- Structural Authorizations Step by Step With Gotchas TooDokument36 SeitenStructural Authorizations Step by Step With Gotchas Toosuhas_12345Noch keine Bewertungen
- SAP GRC Access Control Solution PDFDokument13 SeitenSAP GRC Access Control Solution PDFSree Hari MNoch keine Bewertungen
- User Manual GRC - UAR v.09Dokument48 SeitenUser Manual GRC - UAR v.09Ricardo SoaresNoch keine Bewertungen
- SAP Authorization Concept: Term ExplanationDokument3 SeitenSAP Authorization Concept: Term Explanationtapera_mangeziNoch keine Bewertungen
- GRC10 - 1 Course ContentDokument3 SeitenGRC10 - 1 Course ContentPabitraKumarNoch keine Bewertungen
- Post-Installation Steps of The NWDIDokument4 SeitenPost-Installation Steps of The NWDIlmroccoNoch keine Bewertungen
- Shiva Shankar: Mobile: +91 7396352089Dokument4 SeitenShiva Shankar: Mobile: +91 7396352089ashok varmaNoch keine Bewertungen
- SSO Logon Ticket ConfigurationDokument17 SeitenSSO Logon Ticket Configurationsaty_temp2864Noch keine Bewertungen
- Structural Authorizations Step by StepDokument36 SeitenStructural Authorizations Step by StepMadhukar Raghavendran100% (1)
- PC 10 SoD Mon SubscenarioDokument35 SeitenPC 10 SoD Mon Subscenariokalla.mohan10% (1)
- SAP Net Weaver BI SecurityDokument30 SeitenSAP Net Weaver BI SecurityRajeshwar Rao TNoch keine Bewertungen
- AC10 Transactions and ProgramsDokument31 SeitenAC10 Transactions and ProgramsRamadevi KanisettyNoch keine Bewertungen
- GRC10 Sync JobsDokument2 SeitenGRC10 Sync JobsJulian GrayNoch keine Bewertungen
- PC10 MDUG UG v60Dokument32 SeitenPC10 MDUG UG v60Sankar NayakNoch keine Bewertungen
- Access Request Management (ARQ) Debugging Scenarios - Governance, Risk and Compliance - SCN WikiDokument26 SeitenAccess Request Management (ARQ) Debugging Scenarios - Governance, Risk and Compliance - SCN WikiGautam MalhotraNoch keine Bewertungen
- SAP Security Level 1Dokument121 SeitenSAP Security Level 1sandeep kumarNoch keine Bewertungen
- Sap™ GRC Access Control: Configuration GuideDokument329 SeitenSap™ GRC Access Control: Configuration GuideShyamNoch keine Bewertungen
- GRC - SAP Cloud Identity Access GovernanceDokument8 SeitenGRC - SAP Cloud Identity Access Governancesekoy20122827Noch keine Bewertungen
- Maintenance Optimizer (Mopz) Confidential Document Applies ToDokument21 SeitenMaintenance Optimizer (Mopz) Confidential Document Applies Tossv pNoch keine Bewertungen
- Sap SecurityDokument1 SeiteSap SecurityHarry SNoch keine Bewertungen
- SAP GRC 10 TransactionsDokument1 SeiteSAP GRC 10 TransactionsSuresh GundalaNoch keine Bewertungen
- C GRCAC 10 PDF Questions and AnswersDokument5 SeitenC GRCAC 10 PDF Questions and AnswersMukesh DSNoch keine Bewertungen
- C Tadmsec 04Dokument8 SeitenC Tadmsec 04api-27398944100% (2)
- Understanding HR Triggers in Access Control 10.0 - Governance, Risk and Compliance - SCN WikiDokument2 SeitenUnderstanding HR Triggers in Access Control 10.0 - Governance, Risk and Compliance - SCN WikiArun Varshney (MULAYAM)Noch keine Bewertungen
- Operating System Security Hardening Guide For Sap HanaDokument26 SeitenOperating System Security Hardening Guide For Sap HanakerimNoch keine Bewertungen
- Step by Step Sap Bi SecurityDokument47 SeitenStep by Step Sap Bi SecurityDeven BhandarkarNoch keine Bewertungen
- MSMPDokument5 SeitenMSMPabhinay8721100% (1)
- Parent & Derived RoleDokument4 SeitenParent & Derived RoleDHL123Noch keine Bewertungen
- Sailpoint IdentityIQ A Complete Guide - 2021 EditionVon EverandSailpoint IdentityIQ A Complete Guide - 2021 EditionNoch keine Bewertungen
- Salesforce ModulesDokument4 SeitenSalesforce ModulesVamsi Krishna PeddineniNoch keine Bewertungen
- Linux Overview: John Mathieson IEEE Monthly Meeting February 3, 2009 Official Mascot of Linux KernelDokument11 SeitenLinux Overview: John Mathieson IEEE Monthly Meeting February 3, 2009 Official Mascot of Linux KernelMadhujaya HazarikaNoch keine Bewertungen
- USA Visa QuestionsDokument5 SeitenUSA Visa QuestionsVamsi Krishna PeddineniNoch keine Bewertungen
- Introduction To VS 2005 Application and Page Frameworks GUI Controls Validation Server ControlsDokument34 SeitenIntroduction To VS 2005 Application and Page Frameworks GUI Controls Validation Server Controlsonline_narendraNoch keine Bewertungen
- Introduction To VS 2005 Application and Page Frameworks GUI Controls Validation Server ControlsDokument34 SeitenIntroduction To VS 2005 Application and Page Frameworks GUI Controls Validation Server Controlsonline_narendraNoch keine Bewertungen
- Java SyllabusDokument7 SeitenJava SyllabusVamsi Krishna PeddineniNoch keine Bewertungen
- Background Verification FormDokument5 SeitenBackground Verification FormVamsi Krishna Peddineni0% (1)
- Hadoop TutorialDokument22 SeitenHadoop TutorialkpbhimaniNoch keine Bewertungen
- Java SyllabusDokument7 SeitenJava SyllabusVamsi Krishna PeddineniNoch keine Bewertungen
- HR SecurityDokument5 SeitenHR SecurityVamsi Krishna PeddineniNoch keine Bewertungen
- Hadoop TutorialDokument22 SeitenHadoop TutorialkpbhimaniNoch keine Bewertungen
- Top 100 WordsDokument3 SeitenTop 100 Wordsapi-3764413100% (2)
- Sourcing Strategy Supply ChainDokument15 SeitenSourcing Strategy Supply Chainchetshumtum0% (1)
- SAP GRC 10 Course ContentDokument2 SeitenSAP GRC 10 Course ContentVamsi Krishna PeddineniNoch keine Bewertungen
- Words ListDokument14 SeitenWords ListVamsi Krishna PeddineniNoch keine Bewertungen
- Ioug Cloud Study FinalDokument33 SeitenIoug Cloud Study FinalVamsi Krishna PeddineniNoch keine Bewertungen
- Electrical Engineering Sample Sop 1Dokument2 SeitenElectrical Engineering Sample Sop 1Brijen Raval67% (6)
- Government of Andhra Pradesh, Grama/Ward Sachivalayam Recruitment-2019 Hall TicketDokument2 SeitenGovernment of Andhra Pradesh, Grama/Ward Sachivalayam Recruitment-2019 Hall TicketAnilNoch keine Bewertungen
- Student'S Corner (/Blog/Studentscorner) E-NewslettersubscriptionDokument11 SeitenStudent'S Corner (/Blog/Studentscorner) E-NewslettersubscriptionThirumalNoch keine Bewertungen
- Three Level Password Authentication SystemsDokument5 SeitenThree Level Password Authentication SystemsMahesh IbsNoch keine Bewertungen
- Research Paper On JewelleryDokument4 SeitenResearch Paper On Jewelleryafnkjoegttybbk100% (1)
- Security Report - WeCodexDokument3 SeitenSecurity Report - WeCodexJorge PacoraNoch keine Bewertungen
- Product Design Specification: Automatic Teller Machine (Atm)Dokument10 SeitenProduct Design Specification: Automatic Teller Machine (Atm)EminaTopalovićNoch keine Bewertungen
- Inside RavenDB 4 0Dokument465 SeitenInside RavenDB 4 0nepoznate100% (1)
- 700 150 Corrected PDFDokument40 Seiten700 150 Corrected PDFRamakrishnan Ramachandran57% (7)
- História Da Indumentária e Da ModaDokument253 SeitenHistória Da Indumentária e Da ModaCris GóisNoch keine Bewertungen
- NSA Mind Control and Psyops by Will FilerDokument16 SeitenNSA Mind Control and Psyops by Will FilerSimon Benjamin100% (5)
- LG P350 UserguideDokument50 SeitenLG P350 UserguideivajonNoch keine Bewertungen
- End Chan ThreadDokument92 SeitenEnd Chan ThreadAnonymous Rcp5o7RNoch keine Bewertungen
- Webgoat DeveloperWorkbookDokument279 SeitenWebgoat DeveloperWorkbookEdison AcostaNoch keine Bewertungen
- LNL Iklcqd /: Grand Total 9,492 2,903 0 0 6,572Dokument1 SeiteLNL Iklcqd /: Grand Total 9,492 2,903 0 0 6,572MUNNA SKNoch keine Bewertungen
- ISO IEC 27017 BackgrounderDokument2 SeitenISO IEC 27017 BackgrounderJuan RiveraNoch keine Bewertungen
- E 133 Thermo LyneDokument48 SeitenE 133 Thermo LyneJITENDRA KUMAR SHARMANoch keine Bewertungen
- Lecture 1 Classical CryptographyDokument61 SeitenLecture 1 Classical CryptographypipiNoch keine Bewertungen
- Medeco Price Book January 1st 2015Dokument200 SeitenMedeco Price Book January 1st 2015Security Lock DistributorsNoch keine Bewertungen
- Tom Glaessner Thomas Kellermann Valerie Mcnevin: Electronic Security and Payment Systems: Some New ChallengesDokument22 SeitenTom Glaessner Thomas Kellermann Valerie Mcnevin: Electronic Security and Payment Systems: Some New ChallengesAbdullah Al MamunNoch keine Bewertungen
- 5th Generation Warfare (GW)Dokument5 Seiten5th Generation Warfare (GW)anees baigNoch keine Bewertungen
- Nmap6 Cheatsheet Eng v1 PDFDokument1 SeiteNmap6 Cheatsheet Eng v1 PDFJhon Darío Montoya García100% (1)
- Chapter 9 - Electronic CommerceDokument30 SeitenChapter 9 - Electronic CommerceAna Maria100% (1)
- 9.2.2.6 Lab - Configuring Dynamic and Static NATDokument9 Seiten9.2.2.6 Lab - Configuring Dynamic and Static NATOnke Avr-dude NkqwiliNoch keine Bewertungen
- Error Control Coding Fundamentals and Applications PDFDokument2 SeitenError Control Coding Fundamentals and Applications PDFEveNoch keine Bewertungen
- Final Project PresentationDokument27 SeitenFinal Project PresentationEng Ahmed KaraayeNoch keine Bewertungen
- The Information Technology Act 2000Dokument29 SeitenThe Information Technology Act 2000prasanna deosarkarNoch keine Bewertungen
- 01-10-2022 TN - Swap - Kyndt1 Pre LogDokument15 Seiten01-10-2022 TN - Swap - Kyndt1 Pre Logyou are awesomeNoch keine Bewertungen
- TALK On How To Keep The Environment CleanDokument3 SeitenTALK On How To Keep The Environment CleanAZIM AMRI MUSTAFAKAMALNoch keine Bewertungen
- A6V10463194 enDokument52 SeitenA6V10463194 enVOLTA PRONoch keine Bewertungen