Beruflich Dokumente
Kultur Dokumente
Extended Abstract: Superposition Coding For Wireless Mesh Networks
Hochgeladen von
Fatima AhsanOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Extended Abstract: Superposition Coding For Wireless Mesh Networks
Hochgeladen von
Fatima AhsanCopyright:
Verfügbare Formate
Extended Abstract: Superposition Coding for Wireless
Mesh Networks
Li (Erran) Li
Richard Alimi
Ramachandran Ramjee
Jingpu Shi
Yanjun Sun
Harish Viswanathan
Yang Richard Yang
Bell Labs, Alcatel-Lucent
Rice University
Microsoft Research, India
Yale University
ABSTRACT
A major barrier for the adoption of wireless mesh networks is se-
vere limits on throughput. In this paper, we apply superposition
coding to substantially improve network capacity of large, dense
wireless mesh networks. Superposition coding is a physical layer
technique that allows a transmitter to simultaneously send inde-
pendent packets to multiple receivers. While superposition coding
has been studied extensively by the physical layer community, we
present the rst design of practical and effective MAC protocols
to take advantage of superposition coding in wireless mesh net-
works. Extensive evaluations show that superposition coding can
be a practical method to increase the throughput of large, dense
wireless mesh networks. Specically, in a mesh network with 2 to
64 active receivers and one gateway, we show that our system can
increase throughput up to 154%, with average gain ranging from
10% to 21%. When there are multiple gateways forming a mesh
network, our system gains up to 98%, with average gain ranging
from 24% to 46%. These results clearly demonstrate the potential
benets of our system. We also present results from an implemen-
tation of superposition coding using GNU Radio.
Categories and Subject Descriptors: C.2.1 [Computer Commu-
nication Networks]: Network Architecture and Design Wireless
communications; C.2.5 [Computer Communication Networks]: Lo-
cal and Wide-Area Networks Access schemes
General Terms: Algorithms, Performance, Design.
Keywords: Superposition Coding, Scheduling, Wireless Mesh
1. INTRODUCTION
Wireless mesh networks are becoming a major paradigmfor con-
structing user access networks that provide community or city-wide
Internet connectivity. However, recent theoretical analysis (e.g.,
[3]) and experimental measurements (e.g., [2]) have shown that the
current wireless mesh networks are severely limited in throughput
and do not scale as they become large and dense.
In this paper, we conduct the rst study and design of wire-
less mesh networks that use superposition coding to substantially
improve network capacity. Unlike previous studies, which focus
mainly on physical layer issues of applying superposition coding,
our study proposes simple, practical, and effective MAC protocols
to take advantage of superposition coding.
2. BACKGROUND
We rst provide a brief introduction to the superposition coding
technique in the physical layer. While the focus of this paper is
Copyright is held by the author/owner(s).
MobiCom07, September 914, 2007, Montral, Qubec, Canada.
ACM 978-1-59593-681-3/07/0009.
on the MAC layer, we need a basic understanding of the physical
layer to design an effective MAC layer. For more details, please
refer to [6].
Specically, superposition coding is a physical layer technique
by which a transmitter can simultaneously send independent mes-
sages to multiple receivers. In this paper, for simplicity, we restrict
ourselves to the two-receiver case, in which the transmitter super-
imposes an additional message destined to a secondary receiver (re-
ceiver 2) on a basic message destined for a primary receiver (re-
ceiver 1). We also refer to the basic message as the rst, primary
or lower layer, and the additional message as the second, or upper
layer. It is natural to extend our technique to more than two layers.
In implementation, a transmitter using superposition coding splits
the available transmission power between the two layers, selects
the transmission rate for each of the layers, then encodes and mod-
ulates each of the packets separately at the selected rate. The mod-
ulated symbols are scaled appropriately to match the chosen power
split and summed to obtain the transmitted signal. For example,
if quadrature phase shift keying (QPSK) is used for modulation of
both layers, then the superposed transmitted signal will have a 16-
point constellation.
The two receivers decode their received signal using different
schemes. Receiver 1 decodes its packet treating the superimposed
additional layer as interference. Receiver 2 rst decodes the basic
layer, re-encodes it, and then subtracts it from the original signal.
It then decodes the remaining signal. This process is referred to
as successive interference cancellation (SIC). To allow receiver 2
to decode the basic layer whenever receiver 1 can and to ensure
that the remaining signal after subtraction has enough strength over
noise, the channel quality to receiver 2 should be better than that to
receiver 1; that is, the two channels should be asymmetric. Thus,
we also refer to receiver 1 as the weaker receiver and receiver 2 the
stronger.
To better appreciate the potential benets of superposition cod-
ing, consider applying superposition coding to 802.11 like wire-
less mesh networks. Recent measurement studies (e.g., [4]) have
shown that nodes in a wireless network may be distributed unevenly
and the channel quality of the links in such mesh networks varies
widely. Such rate diversity can drastically reduce network through-
put using standard 802.11. However, this channel diversity presents
a setting where it can be particularly effective for superposition
coding. Consider a simple scenario of one transmitter and two re-
ceivers. The channel quality to receiver 1 is low and can support
only 6 Mbps; the channel quality to receiver 2 is high and can sup-
port 54 Mbps. Without superposition coding, the transmitter using
FIFO scheduling may alternate transmissions to the two receivers.
Thus, the transmitter spends 54/(54+6) = 90% of the time trans-
mitting to receiver 1 and 10% to receiver 2. The total throughput
is only 10.8(= 60.9+540.1) Mbps. One way to improve total
throughput and still maintain fairness is to use a different scheduler
such as proportional fairness. However, this reduces the throughput
of the receiver with poor quality by 44%. With superposition cod-
ing, the transmitter can superimpose the messages to receiver 2 as
additional messages on the basic messages to receiver 1. Thus, the
transmitter maintains a constant throughput of 60(= 54+6) Mbps.
This throughput is 5.55that of the scenario without superposition
coding.
3. MAC FOR SUPERPOSITION CODING
In this section, we present our MAC protocols utilizing superpo-
sition coding.
3.1 Medium Access Control
To maximize reuse of previous design and increase backwards
compatibility, we base the message ow of our MAC on 802.11
RTS/CTS/DATA/ACK. We make small extensions to address two
issues: (1) enable superposition coded messages to be sent to two
receivers; and (2) enable feedback of estimated SINRs to the trans-
mitter.
Specically, we extend RTS by adding an extra address. The rst
address denotes the receiver of the basic packet, while the second
address denotes the receiver of additional packet. Since an RTS
is addressed to two receivers, it triggers the transmission of one
CTS packet from each. These two CTSs are separated by SIFS to
avoid collision. Each CTS message contains the estimated SINR
calculated using the pilot symbols in the preceding RTS message.
The reported SINRs will be stored in the SINR table. Each node
maintains such a table which maps each link to the corresponding
estimated SINR. Superposition coding will be done based on the
stored SINR values. Each superposition coded DATA packet will
require two ACK packets, one from each receiver. This is handled
similarly to the two CTS packets. For channel estimation if RT-
S/CTS is disabled, please refer to our technical report [5].
3.2 MAC Scheduling: A Greedy Scheduler
Besides specifying message ow, the MAC layer will also need
a scheduling algorithm to select the data packets to transmit. We
design a scheduling algorithmthat takes advantage of superposition
coding. Our scheduler extends a given basic scheduler and treats it
as a blackbox.
Consider a node u and assume that the links to its n
u
neighbors
are numbered 1, . . . , n
u
. Let v
1
, . . . , v
n
u
be the corresponding neigh-
bors. Let the estimated channel gain to link i be h
i
. The routing
algorithm determines the next hop and thus the link to be used for
each data packet. Let Q
i
be the queue of packets waiting for trans-
mission on link i. We use |Q
i
| to denote the length of Q
i
.
For simplicity of presentation, we assume that the total power of
each transmission is xed to be P, all packets are of the same size
s, and the background noise is xed at N
0
at all nodes.
For each transmission, we assume that the transmitter picks one
rate for each layer. Let the set of discrete transmission rates be
R. We use the rate functions R
(1)
(i, p) and R
(2)
(i, p) to determine
the transmission rate for link i at transmission power level p, when
the packet to link i is encoded in the rst layer and second layer,
respectively. For R
(1)
(i, p), since the packet in the second layer
with transmission power Pp will become interference to the rst
layer packet, the SINR used is
p|h
i
|
2
(Pp)|h
i
|
2
+N
0
. On the other hand,
due to successive interference cancellation when a receiver recov-
ers a second layer packet, the SINR to determine R
(2)
(i, p) is just
p|h
i
|
2
N
0
. With SINR, we search a table generated from [1] showing
the relationship between packet error rate (PER) and SINR at dif-
ferent 802.11 rates. We pick a rate so that the PER is small, say
10%.
We impose two objectives on our scheduling algorithm. First,
since a network may already have a MAC scheduler (e.g., FIFO,
round robin, or proportional fairness) to determine which data packet
to transmit next, our scheduling algorithm shall be generic and eas-
ily integrated with the existing scheduler to take advantage of su-
perposition coding. We refer to the existing scheduler as the basic
scheduler and our scheduler the SC scheduler. Second, superposi-
tion shall only increase throughput.
We design a greedy scheduler, referred to as Gopp, to achieve
the preceding objectives. Figure 1 shows the complete scheduler.
We keep track of the arrival time of each packet. We use logical
time. If we have a new packet arrive at the queue, the time is in-
creased by one unit. Let pkt
1
be the packet to be transmitted next as
determined by the basic scheduler. We assume that its arrival time
is
1
. Without loss of generality, we assume the next hop of pkt
1
is v
1
. For ease of presentation, let pkt
1
be transmitted in the rst
layer. It is also possible that pkt
1
is transmitted in the second layer.
To handle this, we run the algorithm the second time assuming pkt
1
is in the second layer and take the better of the two solutions.
We rst consider each link i =1 to determine the maximum total
number of packets that can be transmitted if we use the packets for
link i as the second layer. Specically, the total number of packets
N
i
that can be transmitted using superposition coding during the
time to transmit a packet at the rst layer at a power level p is:
N
i
= 1+min
R
(2)
(i, Pp)
R
(1)
(1, p)
, |Q
i
|
, (1)
where
R
(2)
(i,Pp)
R
(1)
(1,p)
is the number of second layer packets we can
transmit and |Q
i
| is the number of backlogged packets at link i
whose arrival time is smaller than
1
+D. D is a parameter which
bounds on how far we can look ahead in the queue for second layer
packets. D is needed to prevent the unfair situation where one ow
gets a lower throughput than that without using superposition cod-
ing. Thus, the number of packets we transmit is upper bounded by
|Q
i
|.
It is straightforward to show that quantity
R
(2)
(i,Pp)
R
(1)
(1,p)
that deter-
mines the number of packets in the second layer correcty accounts
for the coding rates and modulations used in the 802.11a data rates.
Dividing N
i
by the transmission time s/R
(1)
(1, p), and ignoring
s since it is the same for all packets, we dene normalized effective
throughput:
T
i
= N
i
R
(1)
(1, p). (2)
We vary p to maximize T
i
. Let p
i
be the optimal power. We
choose the best performing link i
, and denote the power p
i
by p
.
However, we apply superposition coding on links 1 and i only
when it achieves better throughput than scheduling the two links
separately during the same time interval. That is,
s
R
(1)
(1,P)
is used to
transmit pkt
1
and the remaining time
s
R
(1)
(1,p)
s
R
(1)
(1,P)
to transmit
packets of link i. Thus, we have the following constraint:
1+min
R
(2)
(i,Pp)
R
(1)
(1,p)
, |Q
i
|
>
1+min
1
R
(1)
(1,p)
1
R
(1)
(1,P)
R
(2)
(i, P), |Q
i
|
.
(3)
If the link i is backlogged, the preceding equation is simplied
to:
R
(1)
(1, p)
R
(1)
(1, P)
+
R
(2)
(i, Pp)
R
(2)
(i, P)
> 1. (4)
Finally, we need to update certain scheduler specic parameters.
For example, if the scheduler is proportional fair, one needs to up-
date the average rate of a given next hop.
Process(pkt
1
) On getting a packet pkt
1
from basic
scheduler. Let its next hop be v
1
01. let T
= 0, i
=1 for all i = 1
02. for each link i = 1
03. for each discrete rate c
j
04. determine p such that c
j
= R
(1)
(1, p)
05. N
i
= 1+min
R
(2)
(i,Pp)
R
(1)
(1,p)
, |Q
i
|
06. N
s
= 1+min((
1
R
(1)
(1,p)
1
R
(1)
(1,P)
)R
(2)
(i, P), |Q
i
|)
07. if (N
i
R
(1)
(1, p) > T
and N
i
> N
s
) then
08. N
= N
i
09. T
= N
i
R
(1)
(1, p)
10. i
= i
11. p
i
= p
12. endif
13. endfor
14. endfor
15. if (i
=1) then
16. superposition coding pkt
1
using power p
and
17. N
1 packets of i
18. else
19. schedule pkt
1
only
20. endif
21. update scheduler specic parameters
Figure 1: Superposition scheduling algorithm Gopp at node u.
Assuming a FIFO queue, it is possible to show that our schedul-
ing algorithmensures that each link owgets a throughput no smaller
than it would get without superposition coding with a sufcient -
nite value for D. The full proof is in our technical report [5].
We can further extend the scheduler to directly handle PER. Let
q
1
be the PER for the rst layer of link (u, v
1
). Let q
2
, q
3
be
PER of the rst and second layer of link (u, v
i
) respectively. Then
the expression for N
i
, which reects expected number of deliv-
ered packets under independent losses, is revised to (1 q
1
) +
min
R
(2)
(i,Pp)
R
(1)
(1,p)
), |Q
i
|
(1q
2
)(1q
3
). We can use the revised
expression to compute N
i
and N
s
in our scheduler and add a loop
for PER to search for the best combination.
We now illustrate with a simple example. Suppose we have
two links l
1
and l
2
. The maximum individual rates achievable
by the two receivers are 9 and 36 respectively. In other words,
R
(1)
(1, P) = 9 and R
(1)
(2, P) = 36. Assume that when they are
transmitted using superposition coding, they can achieve 6 and 24.
Thus, R
(1)
(1, p
) = 6 and R
(2)
(2, P p
) = 24. Assuming suf-
cient queued packets, then N
= N
2
= 1 +24/6 = 5; N
s
= 1 +
(1/61/9)36 = 3. Since N
> N
s
, it is benecial to use superpo-
sition coding.
As stated, the Gopp algorithm treats the basic scheduler as a
blackbox. We can also design a scheduling algorithm that jointly
schedules two packets. For details, please see the technical re-
port [5].
4. SIMULATION EVALUATIONS
4.1 Methodology
We have implemented superposition coding as well as our MAC
protocol and scheduling algorithm in ns-2 (Ver. 2.28). We assume
that the basic scheduler is FIFO.
For our simulation setup, we use the 2-ray ground model with 0
dBi antenna gains and antenna heights of 1 meter. We use wireless
nodes with maximum transmit power P = 200 mW. To implement
a realistic packet decoding model, we use a lookup table for packet
error rates (PER) [1] given an observed SINR. There is a separate
PER curve for each 802.11g data rate. The SINR depends on the
received signal power P
r
, noise power N
0
=86 dBm, and imple-
mentation margin I
m
= 5 dB as specied in the 802.11g standard.
These parameters produce maximum transmission ranges similar
to those of the Cisco Aironet 802.11g in a typical outdoor environ-
ment.
When a packet is received in the physical layer, we decode it
as follows. If the packet is not a superposition coded packet, we
compute SINR=
P
r
I
m
N
0
and look up the PERcorreponding to the data
rate at which the packet was transmitted. The packet is dropped
with a probability equal to the PER.
If the packet is a superposition coded packet, we compute the
SINR for the basic layer as SINR =
P
r
p
1
I
m
P
r
(1p
1
)+N
0
where p
1
[0, 1]
is the fraction of power allocated to the basic layer packet. The
SINR lookup and decoding for the basic layer are done in the same
way as a non-superposition coded packet. If the basic layer is de-
coded successfully, we compute the SINR for the additional layer
as SINR =
P
r
(1p
1
)I
m
N
0
. SINR lookup and decoding for the addi-
tional layer are also done in the same way as the non-superposition
coded packet.
Note that there may be multiple packets packed into the addi-
tional layer of a superposition coded packet. These are unpacked
in the MAC layer before being delivered further up the protocol
stack.
To handle channel estimation, the physical layer calculates the
channel gain h =
P
r
P
for each received transmission. This value
along with the transmission source address is passed up to the MAC
layer, which manages a table of channel gains for each link. These
channel gains are used to compute SINR values in the scheduling
and routing layers.
We assume that all transmitted packets are 1500 bytes. We also
disable RTS/CTS.
4.2 Simulation Results
4.2.1 Single gateway
We start with the case of two receivers and a single gateway
transmitter. The location of receiver 2 is xed at 10 m away from
the transmitter. We vary the position of receiver 1 at 100 random
locations. We run two UDP ows for a total of 60 seconds. Each
UDP ow generates CBR trafc.
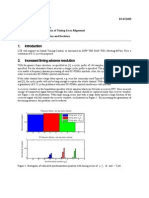
Figure 2-a is a scatter plot comparing the total throughput with
and without using our SC scheduler. The x-axis is the throughput
with SC scheduling turned off, and the y-axis repeats each experi-
ment with SC scheduling turned on. We add two lines in the gure:
y = x and y = 6x. We observe that with standard 802.11 scheduler,
the transmitter achieves total throughput in the range from 6 to 14
Mbps; with our SC scheduler, the total throughput improves to the
range from 14 to 32 Mbps.
0 5 10 15 20 25
0
5
10
15
20
25
30
35
40
Total throughput w/o SC (Mbps)
T
o
t
a
l
t
h
r
o
u
g
h
p
u
t
w
/
S
C
(
M
b
p
s
)
y = x
y = 3.54x
1 2 3 4
0
0.2
0.4
0.6
0.8
1
Throughput gain ratio
C
u
m
u
l
a
t
i
v
e
f
r
a
c
t
i
o
n
(a) Throughput gain with SC scheduler (b) CDF of throughput gain ratio
Figure 2: Single transmitter and two receivers (receiver 2 has a
xed position close to the transmitter).
Figure 2-b plots the cumulative distribution function (CDF) of
throughput gain ratio, where the throughput gain ratio is dened as
the ratio of throughput with SC scheduling to that without it. The
median gain ratio is 2.5, corresponding to a throughput increase
of 150%. We observe that the typical ratio is around 2 to 3, as
indicated by the steep increase of the curve.
0
0.5
1
1.5
2
2.5
2 4 8 16 32 64
T
h
r
o
u
g
h
p
u
t
g
a
i
n
r
a
t
i
o
Number of receivers
Figure 3: Throughput gain ratio of multiple receivers. There is a
single transmitter.
0
0.5
1
1.5
2
1 2 3 4 5 6 7 8 9 10
T
h
r
o
u
g
h
p
u
t
g
a
i
n
r
a
t
i
o
Number of gateways
Figure 4: Throughput gain ratio of multiple ows and multiple
gateways forming a mesh network.
Next we study the effect of the number of receivers. In this class
of experiments, we place all receivers randomly. Thus, this class of
experiments is different from the preceding one which always has
a receiver close to the transmitter. Typically gateways are placed
close to a set of receivers, so the preceding experiment might be
closer to reality and the results from this set of experiments pro-
vide a lower bound. We vary the number of receivers from 2 to 64.
Figure 3 plots the min (the bottom of each bar), max (the top), av-
erage (the heavy middle horizontal line), and individual results for
each given number of receivers. We observe that when we initially
increase the number of receivers from 2 to 4, it increases diversity
and creates opportunities for superposition coding. For example,
the average gain increases from 18% when the number of receivers
is 2 to 21% when the number of receivers is 4. The maximum gain
we observed is 154% when the number of receivers is 4. Further
increasing the number of receivers can reduce the average gain.
However, even when there are 64 simultaneous active receivers, we
still achieve an average gain of 10%.
4.2.2 Gateway mesh networks
Finally, we evaluate the throughput gain when there are multi-
ple gateways forming a mesh network. This evaluates the scalabil-
ity of our system with respect to the number of transmitters. We
randomly place 50 nodes in a square area of 600 meters by 600
meters. We designate a number of nodes with highest degreee as
gateway nodes. The number of gateways ranges from 1 to 10, thus
making the network dense relative to typical deployments. We x
the number of ows to 25. All ows are from gateway nodes to
non-gateway nodes. A non-gateway node communicates with the
closest gateway nodes through a multi-hop path. We use the in-
verse of the link data rate as the routing metric. Only links with
PER < 10% are used. This routing metric tries to minimize the
total transmission time for a given ow.
Figure 4 plots the results. We see that, our system consistently
achieves average gains ranging from 24% to 46% when there are
multiple gateways. When the number of gateways is 10, our system
gains up to 98%, with average at around 42%.
5. IMPLEMENTATION
Finally, we present results from measurement on an implementa-
tion of our algorithm using the GNU Radio platform. In this setup,
there is a transmitter and two receivers. The transmitter transmits
20 packets. When superposition coding is enabled, the transmitter
sends packets with BPSK modulation in both layers, with 70% of
the power allocated to the rst layer and 30% to the second layer.
Scheme Norm. exp. trans. time Gain ratio
No Coding 3.92 1
Superposition 2.88 1.4
Table 1: Testbed performance of superposition coding.
We report in Table 1 the mean normalized total transmission time
for the two receivers to recover their packets, where one unit of
time is the time to transmit one packet at 6 Mbps. We observe that
throughput gains are largely consistent with our simulation results.
6. CONCLUSIONS AND DISCUSSIONS
This paper is part of our larger project founded on the belief that
the key to increase network capacity is to treat a wireless network as
a medium that propagates information rather than packets as they
are originated from the sources. Many information transmission
techniques such as superposition coding, relay channel, network
coding, and MIMO must be accommodated in higher layers to re-
alize their full potential.
This paper presented our rst step in designing a MAC proto-
col to take advantage of superposition coding as an information
propagation technique. In our next step, we have formulated the
transmitter packet mixing problem and designed a MAC protocol
utilizing both network coding and superposition coding. Our pre-
liminary evaluations show that this integrated protocol can improve
throughput in a wide range of scenarios and outperform the bet-
ter performer of network coding and superposition coding by more
than 30% in a wide range of scenarios.
The ultimate goal is to design a framework that can accommo-
date a wide range of information theory and physical layer tech-
niques. To achieve this goal, there is a need to re-consider the
whole wireless network architecture starting from its basic link ab-
straction.
7. ACKNOWLEDGMENTS
Richard Alimi and Y. Richard Yang were supported in part by
grants from the U.S. NSF. We are grateful to Mehul Motani, our
shepherd, for his help in revising the paper. Gerhard Kramer and
Hao Wang have given us valuable comments.
8. REFERENCES
[1] K.-Y. Doo, J. young Song, and D.-H. Cho. Enhanced transmission
mode selection in IEEE 802.11a WLAN system. In Proceedings of
Vehicular Technology Conference, pages 50595062, Sept. 2004.
[2] Ugly truth about mesh networks.
http://www.dailywireless.org/2004/06/28/
ugly-truth-about-mesh-networks/%.
[3] P. Gupta and P. R. Kumar. The capacity of wireless networks. IEEE
Transactions on Information Theory, 46(2):388404, Jan. 2001.
[4] D. Kotz and K. Essien. Analysis of a campus-wide wireless network.
In Proceedings of the Eighth International Conference on Mobile
Computing and Networking (Mobicom), pages 107118, Atlanta, GA,
Nov. 2002.
[5] L. E. Li and et al. Supernet: Superposition coding for wireless mesh
networks. Technical report, Computer Science, Yale University,
available at http://www-net.cs.yale.edu/publications/supernet.pdf,
2007.
[6] D. Tse and P. Viswanath. Fundamentals of Wireless Communication.
Cambridge University Press, May 2005.
Das könnte Ihnen auch gefallen
- Calculus I CompleteDokument578 SeitenCalculus I Completexenocid3r83% (6)
- (IJCST-V9I5P12) :chandra Kanta SamalDokument6 Seiten(IJCST-V9I5P12) :chandra Kanta SamalEighthSenseGroupNoch keine Bewertungen
- Icc15c PrepDokument6 SeitenIcc15c PrepQuangTranNoch keine Bewertungen
- CCM: Cooperative Communication Model FOR Cooperative NetworksDokument6 SeitenCCM: Cooperative Communication Model FOR Cooperative NetworksSRI SAI COLLEGENoch keine Bewertungen
- Conet2012 Submission 12Dokument3 SeitenConet2012 Submission 12Roxi RoxxNoch keine Bewertungen
- MPLS Automatic Bandwidth Allocation Via Adaptive Hysteresis: Key WordsDokument36 SeitenMPLS Automatic Bandwidth Allocation Via Adaptive Hysteresis: Key WordsakarnailNoch keine Bewertungen
- Optimizing Aggregate Throughput in 802.11 Networks Through Balancing Spatial Reuse and Transmission RateDokument5 SeitenOptimizing Aggregate Throughput in 802.11 Networks Through Balancing Spatial Reuse and Transmission RateSatish NaiduNoch keine Bewertungen
- Distributed Bandwidth Allocation For Resilient Packet Ring NetworksDokument11 SeitenDistributed Bandwidth Allocation For Resilient Packet Ring NetworksSupriya Nagane-GaikwadNoch keine Bewertungen
- A Multichannel CSMA MAC Protocol With Receiver-Based Channel Selection For Multihop Wireless NetworksDokument8 SeitenA Multichannel CSMA MAC Protocol With Receiver-Based Channel Selection For Multihop Wireless NetworksSatish NaiduNoch keine Bewertungen
- NWC203c PE23Dokument4 SeitenNWC203c PE23hayhe2910Noch keine Bewertungen
- An Iterative Receiver For WCDMA Systems With MIMO Transmissions and Hierarchical ConstellationsDokument5 SeitenAn Iterative Receiver For WCDMA Systems With MIMO Transmissions and Hierarchical ConstellationsPablo Torres IglesiasNoch keine Bewertungen
- Spectrum Sharing in CRN Using Beamforming and Two-Path Successive RelayingDokument5 SeitenSpectrum Sharing in CRN Using Beamforming and Two-Path Successive RelayingannaNoch keine Bewertungen
- On Energy Level Performance of Adaptive Power Based WSN in Presence of FadingDokument14 SeitenOn Energy Level Performance of Adaptive Power Based WSN in Presence of FadingMuhammad TahirNoch keine Bewertungen
- VJJVJVJDokument7 SeitenVJJVJVJAnirudh KawNoch keine Bewertungen
- NWC HaTrangDokument15 SeitenNWC HaTrangDong Xuan VietNoch keine Bewertungen
- 04 - Cooperative Relay Networks Using FountainDokument6 Seiten04 - Cooperative Relay Networks Using FountainAndré José SilveiraNoch keine Bewertungen
- Comparative Study of RMST and STCP Protocol For Qos Provisioning in WSNDokument6 SeitenComparative Study of RMST and STCP Protocol For Qos Provisioning in WSNUbiquitous Computing and Communication JournalNoch keine Bewertungen
- 18EC743M5Dokument48 Seiten18EC743M5Pavan ReddyNoch keine Bewertungen
- NWC HaTrangDokument15 SeitenNWC HaTrangquylhhe176826Noch keine Bewertungen
- Rbmulticast: Receiver Based Multicast For Wireless Sensor NetworksDokument6 SeitenRbmulticast: Receiver Based Multicast For Wireless Sensor Networkssnet solutionsNoch keine Bewertungen
- TCP Performance Enhancement Over UMTS Network With RNC FeedbackDokument6 SeitenTCP Performance Enhancement Over UMTS Network With RNC FeedbackumtsrfNoch keine Bewertungen
- A Signal-to-Interference Ratio Based Downlink Scheduling Scheme For WCDMA Mobile Communication SystemDokument6 SeitenA Signal-to-Interference Ratio Based Downlink Scheduling Scheme For WCDMA Mobile Communication SystemrezadigitNoch keine Bewertungen
- Using Switched Beam Smart Antennas in Wireless Ad Hoc Networks With Angular MAC ProtocolDokument11 SeitenUsing Switched Beam Smart Antennas in Wireless Ad Hoc Networks With Angular MAC ProtocolbaburaokodavatiNoch keine Bewertungen
- Interference Based Call Admission Control For Wireless Ad Hoc NetworksDokument8 SeitenInterference Based Call Admission Control For Wireless Ad Hoc NetworkssakathhotmagaNoch keine Bewertungen
- Jecet: Journal of Electronics and Communication Engineering & Technology (JECET)Dokument6 SeitenJecet: Journal of Electronics and Communication Engineering & Technology (JECET)IAEME PublicationNoch keine Bewertungen
- Implementation and Evaluation of Hybridnetwork Using Smart DevicesDokument5 SeitenImplementation and Evaluation of Hybridnetwork Using Smart DevicesVijay KumarNoch keine Bewertungen
- tr413 PDFDokument17 Seitentr413 PDFWANKHAMANoch keine Bewertungen
- Opportunistic Scheduling of Randomly Coded Multicast Transmissions at Half-Duplex Relay StationsDokument18 SeitenOpportunistic Scheduling of Randomly Coded Multicast Transmissions at Half-Duplex Relay Stationse.lamgood2008Noch keine Bewertungen
- RAVIKANT Paper 1 SuveyDokument8 SeitenRAVIKANT Paper 1 SuveyDeepak SharmaNoch keine Bewertungen
- Performance Evaluation of AODV For Mobile Ad Hoc Network With Varying Probability and Node MobilityDokument5 SeitenPerformance Evaluation of AODV For Mobile Ad Hoc Network With Varying Probability and Node MobilityThu HangNoch keine Bewertungen
- Optimized Latency Secured (LS) MAC Protocols For Delay Sensitive Large Sensor NetworksDokument7 SeitenOptimized Latency Secured (LS) MAC Protocols For Delay Sensitive Large Sensor NetworksShafayet UddinNoch keine Bewertungen
- RESILIENT PACKET RING Networks Seminar ReportDokument25 SeitenRESILIENT PACKET RING Networks Seminar ReportSimmi JoshiNoch keine Bewertungen
- 2013 13 LibmanDokument30 Seiten2013 13 LibmanGuru MekalaNoch keine Bewertungen
- RPL For Supporting Energy Efficient Transmission PDFDokument5 SeitenRPL For Supporting Energy Efficient Transmission PDFr_wilawan6234Noch keine Bewertungen
- Zs 2010 19 ChinacomDokument7 SeitenZs 2010 19 ChinacomkonenianithaNoch keine Bewertungen
- Energy-Efficient MAC For Broadcast Problems in Wireless Sensor NetworksDokument4 SeitenEnergy-Efficient MAC For Broadcast Problems in Wireless Sensor Networkstariq76Noch keine Bewertungen
- Quiz 1 SolutionDokument3 SeitenQuiz 1 SolutionAli AhmadNoch keine Bewertungen
- Adhoc03 Oscar Version FinalDokument6 SeitenAdhoc03 Oscar Version FinaloscarmanoloNoch keine Bewertungen
- Performance of Hybrid-ARQ With Incremental Redundancy Over Relay ChannelsDokument6 SeitenPerformance of Hybrid-ARQ With Incremental Redundancy Over Relay ChannelsViệt DũngNoch keine Bewertungen
- Performance Study of The GSM Circuit-Switched Data Channel Research ProjectDokument25 SeitenPerformance Study of The GSM Circuit-Switched Data Channel Research ProjectnngoweNoch keine Bewertungen
- Adaptively Delay Retransmission Scheme For SR ARQ in Wireless Data NetworksDokument4 SeitenAdaptively Delay Retransmission Scheme For SR ARQ in Wireless Data Networksআনিসুর রহমানNoch keine Bewertungen
- Phara NWC203Dokument21 SeitenPhara NWC203Tran Minh AnhNoch keine Bewertungen
- Improving MIMO Spectral Efficiency in 4G Macro-Cellular NetworksDokument6 SeitenImproving MIMO Spectral Efficiency in 4G Macro-Cellular Networksወንድሙ ዘገዬNoch keine Bewertungen
- Cross-Layer Combination of Cooperative HARQ With AMC in Wireless Ad-Hoc NetworksDokument5 SeitenCross-Layer Combination of Cooperative HARQ With AMC in Wireless Ad-Hoc NetworksozkibrNoch keine Bewertungen
- On SCTP Multi-Homing Performance: Andreas JungmaierDokument21 SeitenOn SCTP Multi-Homing Performance: Andreas JungmaierhalmstadkkNoch keine Bewertungen
- Correct-Basepaper-Efficient Broadcasting in Mobile Ad Hoc NetworksDokument15 SeitenCorrect-Basepaper-Efficient Broadcasting in Mobile Ad Hoc NetworksieeexploreprojectsNoch keine Bewertungen
- Power Control in Ad-Hoc Networks: Theory, Architecture, Algorithm and Implementation of The COMPOW ProtocolDokument7 SeitenPower Control in Ad-Hoc Networks: Theory, Architecture, Algorithm and Implementation of The COMPOW ProtocolMohamed Adnene ZayeneNoch keine Bewertungen
- A Neighbor Coverage-Based Probabilistic Rebroadcast For Reducing Routing Overhead in Mobile Ad Hoc NetworksDokument7 SeitenA Neighbor Coverage-Based Probabilistic Rebroadcast For Reducing Routing Overhead in Mobile Ad Hoc NetworksIJMERNoch keine Bewertungen
- Energy Efficiency Maximized Resource Allocation FoDokument10 SeitenEnergy Efficiency Maximized Resource Allocation Foمحمد مطيعNoch keine Bewertungen
- When Both Transmitting and Receiving Energies Matter: An Application of Network Coding in Wireless Body Area NetworksDokument10 SeitenWhen Both Transmitting and Receiving Energies Matter: An Application of Network Coding in Wireless Body Area NetworksjagruthimsNoch keine Bewertungen
- NWC203c PE SU2023Dokument85 SeitenNWC203c PE SU2023Hoàng PhạmNoch keine Bewertungen
- A Hybrid Path-Oriented Code Assignment CDMA-Based MAC Protocol For Underwater Acoustic Sensor Networks (Summary)Dokument5 SeitenA Hybrid Path-Oriented Code Assignment CDMA-Based MAC Protocol For Underwater Acoustic Sensor Networks (Summary)Tanzeel ShakeelNoch keine Bewertungen
- A New Approach For Reducing Routing Overhead in MANET: AbstractDokument6 SeitenA New Approach For Reducing Routing Overhead in MANET: AbstractInternational Journal of Engineering and TechniquesNoch keine Bewertungen
- Nctuns Tool For Ieee 802.16J Mobile Wimax Relay Network SimulationsDokument34 SeitenNctuns Tool For Ieee 802.16J Mobile Wimax Relay Network Simulationskannan_alaguNoch keine Bewertungen
- Reliable Multicast MAC Protocol For Wireless LansDokument5 SeitenReliable Multicast MAC Protocol For Wireless LansKaan Avşar AsanNoch keine Bewertungen
- p132 Li PDFDokument9 Seitenp132 Li PDFHenrique Mariano AmaralNoch keine Bewertungen
- Modeling UMTS Discontinuous Reception MechanismDokument8 SeitenModeling UMTS Discontinuous Reception Mechanismregistraz1557Noch keine Bewertungen
- RSSI Is Under Appreciated: Kannan Srinivasan and Philip LevisDokument5 SeitenRSSI Is Under Appreciated: Kannan Srinivasan and Philip LevisdiogosmoreiraNoch keine Bewertungen
- Encore 2Dokument6 SeitenEncore 2Sahar Ben YaalaNoch keine Bewertungen
- P A I A P C Mac P (Iapcmp) Manet: Erformance Nalysis of Mproved Utonomous Ower Ontrol Rotocol FOR SDokument11 SeitenP A I A P C Mac P (Iapcmp) Manet: Erformance Nalysis of Mproved Utonomous Ower Ontrol Rotocol FOR SijansjournalNoch keine Bewertungen
- EE4601 Communication Systems: Channel CapacityDokument8 SeitenEE4601 Communication Systems: Channel CapacityFatima AhsanNoch keine Bewertungen
- Students' Difficulties in Understanding The Concepts of Magnetic Field Strength, Magnetic Flux Density and MagnetizationDokument8 SeitenStudents' Difficulties in Understanding The Concepts of Magnetic Field Strength, Magnetic Flux Density and MagnetizationFatima AhsanNoch keine Bewertungen
- Lect21QAM Error ProbabilityDokument7 SeitenLect21QAM Error ProbabilityFatima AhsanNoch keine Bewertungen
- Week1Introduction To Digital CommunicationsDokument22 SeitenWeek1Introduction To Digital CommunicationsFatima AhsanNoch keine Bewertungen
- Final 03Dokument5 SeitenFinal 03Fatima AhsanNoch keine Bewertungen
- Lect11Nyquist Pulse ShapingDokument11 SeitenLect11Nyquist Pulse ShapingFatima AhsanNoch keine Bewertungen
- To Convolutional Codes: ExampleDokument18 SeitenTo Convolutional Codes: ExampleFatima AhsanNoch keine Bewertungen
- Evolutionary Robot Wall-Following Control UsingDokument13 SeitenEvolutionary Robot Wall-Following Control UsingFatima AhsanNoch keine Bewertungen
- Efficient Error Estimating Coding: Feasibility and ApplicationsDokument12 SeitenEfficient Error Estimating Coding: Feasibility and ApplicationsFatima AhsanNoch keine Bewertungen
- Discrete Time Signals and Fourier SeriesDokument34 SeitenDiscrete Time Signals and Fourier SeriesFatima AhsanNoch keine Bewertungen
- Trellis Coded Modulation (TCM) : Intuitive Guide To Principles of CommunicationsDokument0 SeitenTrellis Coded Modulation (TCM) : Intuitive Guide To Principles of CommunicationsFatima AhsanNoch keine Bewertungen
- Homework1 SolutionDokument5 SeitenHomework1 SolutionFatima AhsanNoch keine Bewertungen
- Question # 1:: SolutionDokument2 SeitenQuestion # 1:: SolutionFatima AhsanNoch keine Bewertungen
- Signal Processing & Simulation Newsletter: Tutorial 3Dokument3 SeitenSignal Processing & Simulation Newsletter: Tutorial 3Fatima AhsanNoch keine Bewertungen
- 2 DiffcodDokument3 Seiten2 DiffcodFatima AhsanNoch keine Bewertungen
- AirTight C 10 WIPS Sensor DatasheetDokument4 SeitenAirTight C 10 WIPS Sensor DatasheetangelinosNoch keine Bewertungen
- 05.static Routing LabDokument3 Seiten05.static Routing LabasegunloluNoch keine Bewertungen
- HP Deskjet 3700 All-In-One SeriesDokument120 SeitenHP Deskjet 3700 All-In-One SeriesTina ConoverNoch keine Bewertungen
- DS 19A08BN Users ManualDokument145 SeitenDS 19A08BN Users Manualkunene07Noch keine Bewertungen
- R1-072489 Timing Alignment Error For RachDokument3 SeitenR1-072489 Timing Alignment Error For RachsrmanoharaNoch keine Bewertungen
- FTP ModelDokument7 SeitenFTP ModelChallapalli RajyalaxmiNoch keine Bewertungen
- Image/Digit Recognition Using Machine Learning: by Raghav Chawla, I.T/B.Tech/Hmritm/5 Semester 43713303117Dokument15 SeitenImage/Digit Recognition Using Machine Learning: by Raghav Chawla, I.T/B.Tech/Hmritm/5 Semester 43713303117Raghav Chawla100% (1)
- G107 Alarm SystemDokument14 SeitenG107 Alarm SystemSomchai LoeyvanicharoenNoch keine Bewertungen
- Control 07 2015 30pa PH Pac PHCDokument44 SeitenControl 07 2015 30pa PH Pac PHCЕвгений РогозинNoch keine Bewertungen
- Top-Down Network Design, Second EditionDokument2 SeitenTop-Down Network Design, Second EditionNguyễn Hùng0% (1)
- Hack Admin Password of Network NeighbourhoodDokument2 SeitenHack Admin Password of Network Neighbourhoodakhu_79Noch keine Bewertungen
- Installation and Operation Manual (26099)Dokument52 SeitenInstallation and Operation Manual (26099)Anderson DuarteNoch keine Bewertungen
- How To Model Support Bracket in Inventor 2011 - GrabCADDokument8 SeitenHow To Model Support Bracket in Inventor 2011 - GrabCADAndy MezetaNoch keine Bewertungen
- Macsec: Encryption For The Wired Lan Networking Services Team, Red Hat Sabrina DubrocaDokument40 SeitenMacsec: Encryption For The Wired Lan Networking Services Team, Red Hat Sabrina DubrocaAbhimanyu AdityaNoch keine Bewertungen
- 3par Autonomic GroupsDokument4 Seiten3par Autonomic Groupsjd_hernandezNoch keine Bewertungen
- Huawei 5g Cpe Pro h112 370 372 Datasheet PDFDokument3 SeitenHuawei 5g Cpe Pro h112 370 372 Datasheet PDFKunjali KummalilNoch keine Bewertungen
- 1 Wireless and Mobile Device AttackDokument17 Seiten1 Wireless and Mobile Device AttackJibril Dauda MuhammadNoch keine Bewertungen
- Spectra Enhanced - Firmware Release Notes v2.13.7.1Dokument10 SeitenSpectra Enhanced - Firmware Release Notes v2.13.7.1yacht.alaiyaNoch keine Bewertungen
- DC Manual Final PDFDokument25 SeitenDC Manual Final PDFAsma FirdouseNoch keine Bewertungen
- Browser Settings For SAP: Currently Supported Operating Systems and Browser VersionsDokument9 SeitenBrowser Settings For SAP: Currently Supported Operating Systems and Browser Versionsokb33Noch keine Bewertungen
- Ibm Cognos 8 Business Intelligence: Powerplay ClientDokument21 SeitenIbm Cognos 8 Business Intelligence: Powerplay Clientfindu_2005Noch keine Bewertungen
- Ss7analysiswiresharkandsnort en 180402121113 PDFDokument68 SeitenSs7analysiswiresharkandsnort en 180402121113 PDFLuca GarufiNoch keine Bewertungen
- Cyber SecurityDokument17 SeitenCyber SecurityanjulNoch keine Bewertungen
- Metro Ethernet Services: Ralph SantitoroDokument29 SeitenMetro Ethernet Services: Ralph SantitoroFirman OoredooNoch keine Bewertungen
- Ansible TebotDokument30 SeitenAnsible Tebotvinodbabu24Noch keine Bewertungen
- Synology DS107+ Data - Sheet - Enu PDFDokument2 SeitenSynology DS107+ Data - Sheet - Enu PDFasalihovicNoch keine Bewertungen
- Dell PowerEdge T630 Spec SheetDokument2 SeitenDell PowerEdge T630 Spec SheetPatrickChanCFNoch keine Bewertungen
- Communication SystemDokument13 SeitenCommunication SystemSyieda ZamryNoch keine Bewertungen
- LTE Design Requirements - Coexistence With WIMI, DVB-C, DVB-TDokument14 SeitenLTE Design Requirements - Coexistence With WIMI, DVB-C, DVB-TsivakumarNoch keine Bewertungen