Beruflich Dokumente
Kultur Dokumente
ECEC631
Hochgeladen von
broseidon94Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
ECEC631
Hochgeladen von
broseidon94Copyright:
Verfügbare Formate
Principles of Computer Networking (Fall, 2014)
Homework #1 Solutions
Please do ve of the following ten problems, found in the textbook on pages 8790:
2.1, 2.3, 2.4, 2.5, 2.6, 2.7, 2.9, 2.13, 2.15, 2.16
You are free to hand in more than ve answers, but the TA will only grade the rst ve and will ignore the
remaining answers. Please submit your solutions i) neatly written, ii) problems written in order, iii) stapled, and
iv) with your name(s) on the front page. Late homework will not be accepted.
2.1 Consider a channel in which bit errors occur independently from bit to bit, and the bit error probability (or
bit error rate) is p. This is called the Bernoulli packet error model. Show that the probability that a K bit packet
is received in error is approximated by Kp. Examine the validity of the approximation for K = 10, 000 bits, for
p = 10
7
and p = 10
4
, and discuss. If the packet length is a random variable, K, with f(k) being the probability
that the packet has k bits, show that the packet error probability is approximated by pE[K].
P(packet error) = 1 P(none of the bits in the packet is in error)
= 1 P(a bit is received correctly)
K
= 1 (1 p)
K
1 (1 Kp) = Kp.
With K = 10, 000, the probability of packet error, expressed up to 4 decimal places is 0.001 for p = 10
7
, which
is exactly the same as Kp, whereas it is 0.6321, for p = 10
4
, which is poorly approximated by Kp = 1. The
approximation in the above derivation basically retains the rst term of the Taylor expansion of (1p)
K
at p = 0.
For the approximation to work well we must have
1
2
K
2
p
2
Kp, which, with K = 10, 000, holds for p = 10
7
, but
not for p = 10
4
.
P(packet error | k bits in packet) kp
P(packet error)
k
f(k)kp
= pE[K]
2.3 A P bit packet is to be transported over L store-and-forward links; d
l
and C
l
are the propagation delay and
bit rate respectively on link l. Assuming zero queueing and processing delays on the links, argue that the end-
to-end delay would be
L
l=1
(
P+H
C
l
+ d
l
), where H is the number of header bits in a packet. If an M bit le is
to be transmitted as K packets and C
l
= C for all l, show that the end-to-end le transfer completion time is
1
C
[(
M
K
+H)(L 1) +
L
l=1
d
l
+M +KH]. Discuss the tradeos of choosing K. Show that the K that minimizes
the delay is
M
H
(L 1).
The transmission delay for a P bit packet with an H bit header over a link of capacity C is
P+H
C
. The
end-to-end delay across a series of links with propagation delay d
l
and transmission capacities C
l
is therefore:
L
l=1
P +H
C
l
+d
l
. (1)
1 October 2, 2014
Using K packets to transport an M bit le requires
M
K
bits per packet. The last packet begins transmission at
time (K 1)
M/K+H
C
, i.e., when the other K 1 packets have completed transmission at link 1. This last packet
then takes an additional
M/K+H
C
L +
d
l
to arrive at the destination. The end-to-end delay is therefore
(K 1)
M/K +H
C
+
M/K +H
C
L +
L
l=1
d
l
. (2)
Writing this as a function of K, we obtain: f(K)
M(L1)
K
+ HK. Dierentiation yields f
(K) = H
M(L1)
K
2
.
Looking at the second derivative we obtain f
(K) =
2M(L1)
K
3
> 0, hence f(K) is concave and thus the stationary
points are maximizers. The maximizing K
is easily seen to be K
M(L1)
H
. For K small (fewer packets,
heavier payload) we obtain less parallelism but have less overhead from headers, while for K large (more packets,
smaller payload) we obtain more parallelism but have more overhead from headers.
2.4 If the links in Problem 2.3 used cut-through switching rather than store-and-forward, obtain the end-to-end
delays for the packet and the le with K packets. Assume C
l
= C for all l.
Its helpful to consider a sequence of simpler models.
The end-to-end delay for a P bit packet with an H bit header over a sequence of L links with no propagation
delays and link capacities C is
P+H
C
L.
The same as above but with cut-through switching is
H
C
L +
P
C
.
Sending an M bit le using K packets over a sequence of L links is
M/K+H
C
(K 1) +
M/K+H
C
L.
Same as above but with cut-through switching is
M/K+H
C
(K 1) +
H
C
L +
M/K
C
.
With cut-through switching we still must wait the same amount of time until the last packet can be transmitted
as in question 2.2, i.e., the last packet begins transmission at time (K1)
M/K+H
C
. That last packet traverses the
L links, but the transmission delay is now
H
C
L and the payload arrives
M/K
C
later. The nal expression is then:
(K 1)
M/K +H
C
+
H
C
L +
M/K
C
+
L
l=1
d
l
. (3)
2.5 A circuit multiplexed point to point link can accommodate one call at any time. The arrival times of calls X
and Y are uniformly distributed in the time interval [0, 5]. The holding time of call X is one unit and that of Y
is two units. An arriving call that nds a busy trunk is lost. Find the blocking probability for calls X and Y .
Let X and Y be the random variables representing the arrival times of calls X and Y respectively. (X, Y )
can take values in [0, 5]
2
and since they are uniformly distributed, the probability that (X, Y ) lies in an interval is
given by the ratio of the area corresponding to that interval to the total area of the square. Thus we have,
P(call X is blocked) = P(Y X Y + 2) =
8
25
P(call Y is blocked) = P(X Y X + 1) =
4.5
25
.
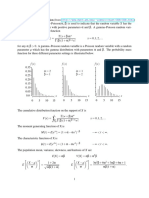
See Figure 1 for a sketch of these computations.
2 October 2, 2014
Figure 1: Computing the blocking probabilities for X and Y : each pair of possible arrival points is equi-probable,
i.e., f
XY
(x, y) =
1
25
for 0 x, y 5. The gray area denotes points where X is blocked and the black area denotes
points where Y is blocked. Their respective areas are proportional to their blocking probabilities.
2.6 A source generates bits according to a Poisson process of rate . The bits from the source are to be transmitted
as K-bit packets. The time to accumulate a full packet will be called the packetization delay. Find the distribution
of the packetization delay.
Assume a packet is transmitted at time 0 and a new packet formation begins at that time. The probability
that the packetisation delay exceeds t is the probability that at time t the packet has not lled up. This in turn
is the probability that in time (0, t) less than K bits have been generated by the Poisson source. We use the fact
that the number of bits generated by the Poisson source in the interval (0, t) is Poission distributed with mean t.
Thus
P(packetization delay > t) = e
t
K1
k=0
(t)
k1
k!
. (4)
Another solution would be to say the interval between consecutive bits has an exponential distribution with mean
1
, and the time to generate K bits would be a random variable with a K-Erlang distribution (a gamma distribution
is also correct). Hence, the probability density function of the packetisation delay will be
K
t
K1
K!
e
t
.
2.7 A video source generates K xed length packets per frame which are then transmitted over a link. The frame
rate is 25 frames per second; i.e., every 40 ms the source outputs K packets into the links buer. The transmission
time of each packet on the link is 1 ms. If K 40, nd the average packet delay and the time average occupancy of
the link buer. Assume that a packet is stored in the buer until its last bit has been transmitted. Now assume that
K is a random variable with probability mass function P(K = k) =
k1
(1 ) for k = 1, 2, . . . with 0 < < 1.
In each frame, packets in excess of 40 are lost. Find the probability of losing packets in a frame and the average
number of packets lost per frame. Also, nd the average packet delay and the average buer occupancy.
When K is deterministic, at the beginning of each interval of length 40 ms (inter frame time) there will be K
packets that reduces by one every millisecond. The rst packet is released after a delay of 1 ms, the second one
after 2 ms and so on. Thus the following is easy to verify.
Average packet delay =
1
K
K
k=1
k =
1
K
K(K + 1)
2
=
K + 1
2
Time Average Buer Occupancy =
1
40
K
k=1
k =
K(K + 1)
80
.
3 October 2, 2014
When K is a random variable, if there are more than 40 packets in the frame, then the excess is lost. The
probability that packets are lost from a frame is straightforward. The number of packets lost per frame is those
that are in excess of 40. Thus the average loss per frame is also straightforward. If a frame generates k packets,
k 40, then the conditional mean packet delay and buer occupancy is obtained as before. If a frame generates
more than 40 packets, then only 40 are retained. Thus the mean packet delay and the buer occupancy can be
easily written as below.
P(packets are lost in a frame) =
k=41
k1
(1 ) =
40
E(number of lost packets per frame) =
k=41
(k 40)
k1
(1 )
Average packet delay =
40
k=1
k1
(1 )
k + 1
2
40
41
2
Time average buer occupancy =
40
k=1
k(k + 1)
80
k1
(1 )
40
41
2
.
2.9 In a slotted multiaccess system, K nodes are each attempting transmission with probability p in each slot
independent of the other nodes. If N is the random number of slots consumed before the rst success, nd the
probability mass function of N.
We rst nd the probability that there is a successful transmission in a slot. A transmission is successful if
only one node attempts transmission and the others do not make the attempt.
P(successful transmission in a slot) = Kp(1 p)
K1
P
s
. (5)
The number of slots until the success is a geometric distribution with success probability P
s
, i.e.,
P(N = n) = P
s
(1 P
s
)
n1
, n = 1, 2, . . . , (6)
2.13 Consider a hierarchical construction of a network. At the lowest level, the nodes are formed into groups of
K
1
nodes and connected to one level-one switch; K
2
level-one switches are grouped together to be connected to one
level-two switch. Let there be L levels of this hierarchical construction. For K
i
= K, for i = 1, . . . , L, nd the
number of switches in the network and the number of links. Note that the links interconnecting the switches at the
higher levels will be longer but because they aggregate more trac, they will also be of increasing capacities.
There is one switch at level L at top of the hierarchy, connecting K switches of level L 1. Thus there are K
switches at level L 1. Continuing down the hierarchy, we get K
Ll
switches at level l. Thus the total number
of switches that will be used in the network is
L
l=1
K
Ll
.
2.15 One link in a network is failure prone and the other links are stable. The network topology is sampled every
second and, if the topology has changed, the routes are recalculated. Each second, the failure prone link changes
from up to down with probability p and from down to up with probability q. What is the rate at which the routes
in the network are calculated?
Starting with the link being good, the mean time for which it stays good is
1
p
seconds, and then it stays bad
for
1
q
seconds. Thus the route recalculation rate is
2pq
p+q
. A better way to do this is with a two state discrete time
4 October 2, 2014
Markov chain with transition probabilities from state 0 (good) to state 1 (bad) of p and from state 1 to state 0 of
q. The invariant distribution is then = ((0), (1)) =
q
p+q
,
p
p+q
. The rate of change is then:
p(0) +q(1) =
2pq
p +q
. (7)
2.16 On a link the mean delay can be approximated by
1
1
, where is the utilization of the link. If the network
monitoring management trac increases the utilisation by , nd the percentage increase in the mean delay and
plot the increase as a function of . What do you observe?
Observe that as the link utilization increases, the increase in the penalty increases faster. See Figure 2. There
are two ways to interpret : as the increase in the load or as the percent increase in the load. Under the former
the load + and the new mean delay becomes E[D
] =
1
1(+)
, while under the latter the load becomes (1+)
and the new mean delay becomes E[D
] =
1
1(1+)
. Assuming the latter to be the case, the percentage increase
in the mean delay is
E[D
] E[D
0
]
E[D
0
]
=
1 (1 +)
. (8)
This expression is plotted vs. in Figure 2 for various .
0.2 0.4 0.6 0.8
0.05
0.1
0.15
0.2
0.25
0.3
0.35
Figure 2: Percentage increase in average delay as a function of the nominal oered load , for = {0.01, 0.05, 0.10}.
5 October 2, 2014
Das könnte Ihnen auch gefallen
- 6.02 Practice Problems: Reliable Data Transport Protocols: Problem 1. Consider The Following Chain TopologyDokument13 Seiten6.02 Practice Problems: Reliable Data Transport Protocols: Problem 1. Consider The Following Chain TopologyAravindh CNoch keine Bewertungen
- Ps 04Dokument3 SeitenPs 04spitzersglareNoch keine Bewertungen
- Problem Set 2: F (N) Logf (N) o (F (N) ) Log (O (F (N) ) )Dokument3 SeitenProblem Set 2: F (N) Logf (N) o (F (N) ) Log (O (F (N) ) )hawk100% (1)
- Unit 1 Problem SolutionsDokument9 SeitenUnit 1 Problem SolutionsSashank PNoch keine Bewertungen
- Ee132b Hw3 SolDokument7 SeitenEe132b Hw3 SolDylan Ler100% (1)
- Solutions To Assignment 1 Questions: R L D R L S M DDokument2 SeitenSolutions To Assignment 1 Questions: R L D R L S M Daseef2009Noch keine Bewertungen
- Capacity of the Binary Erasure ChannelDokument4 SeitenCapacity of the Binary Erasure ChannelGeremu TilahunNoch keine Bewertungen
- HW 1 Solutions EE122 Fall 05 Book SolutionsDokument5 SeitenHW 1 Solutions EE122 Fall 05 Book SolutionsatiffitaNoch keine Bewertungen
- Delay SolutionsDokument7 SeitenDelay Solutionsstanley umohNoch keine Bewertungen
- C8.4 Problems2Dokument4 SeitenC8.4 Problems2Mihnea-Gabriel DoicaNoch keine Bewertungen
- Lotto DesignDokument25 SeitenLotto DesignClaudioNoch keine Bewertungen
- Thuat Toan K-TreeDokument10 SeitenThuat Toan K-TreediephtvNoch keine Bewertungen
- 2014 - Chakrabarty Et Al. - Integrality Gap of The Hypergraphic Relaxation of Steiner Trees - A Short Proof of A 1.55 Upper BoundDokument6 Seiten2014 - Chakrabarty Et Al. - Integrality Gap of The Hypergraphic Relaxation of Steiner Trees - A Short Proof of A 1.55 Upper Boundsumi_11Noch keine Bewertungen
- CS2105 Problem Set 1Dokument2 SeitenCS2105 Problem Set 1weitsangNoch keine Bewertungen
- Derivation of Plancks Formula Radiation Chapter10Dokument14 SeitenDerivation of Plancks Formula Radiation Chapter10TewodrosNoch keine Bewertungen
- Mathematical Problems and Solutions ReviewedDokument9 SeitenMathematical Problems and Solutions ReviewedthonguyenNoch keine Bewertungen
- Fountain Codes: Capacity Approaching Codes Design and Implementation Special SectionDokument7 SeitenFountain Codes: Capacity Approaching Codes Design and Implementation Special SectionAmer WarrakNoch keine Bewertungen
- Solvability by RadicalsDokument30 SeitenSolvability by RadicalsRay GobbiNoch keine Bewertungen
- Tifr 05Dokument228 SeitenTifr 05Atharva KordeNoch keine Bewertungen
- The Abundancy Index of Divisors of Spoof Odd Perfect NumbersDokument17 SeitenThe Abundancy Index of Divisors of Spoof Odd Perfect NumbersJose Arnaldo Bebita DrisNoch keine Bewertungen
- Part (A) : Anonymous Anonymous AnonymousDokument4 SeitenPart (A) : Anonymous Anonymous AnonymousKelum BuddhikaNoch keine Bewertungen
- Homework 2 SolutionsDokument10 SeitenHomework 2 SolutionsJosh at nightNoch keine Bewertungen
- HW 3 SolnDokument5 SeitenHW 3 SolnMUHAMMAD AHSANNoch keine Bewertungen
- Day 8 Contest TutorialsDokument6 SeitenDay 8 Contest TutorialsRoberto FrancoNoch keine Bewertungen
- HW 1Dokument2 SeitenHW 1Tạ ThốnNoch keine Bewertungen
- (Paper) The Discrete Noiseless Channel RevisitedDokument16 Seiten(Paper) The Discrete Noiseless Channel Revisited김기한Noch keine Bewertungen
- Fourier Transform PDFDokument7 SeitenFourier Transform PDFAhmed EdrisNoch keine Bewertungen
- New Constructions For Covering Designs - Daniel M. GordonDokument24 SeitenNew Constructions For Covering Designs - Daniel M. GordonClaudioNoch keine Bewertungen
- Soln8 1Dokument2 SeitenSoln8 1Nguyễn Đình Anh KhôiNoch keine Bewertungen
- 6.851 Advanced Data Structures Problem 8 Sample solution signature compressionDokument2 Seiten6.851 Advanced Data Structures Problem 8 Sample solution signature compressiondjoseph_1Noch keine Bewertungen
- HW 1Dokument3 SeitenHW 1samsiksonNoch keine Bewertungen
- Solution to practice problem set 1Dokument3 SeitenSolution to practice problem set 1agentrangomanNoch keine Bewertungen
- hw4 SolDokument3 Seitenhw4 SolDylan LerNoch keine Bewertungen
- Kraft-McMillan InequalityDokument5 SeitenKraft-McMillan InequalityAlice KarayiannisNoch keine Bewertungen
- Measurement and Modelling IDokument36 SeitenMeasurement and Modelling I23wingsNoch keine Bewertungen
- (Lecture Notes) Jyrki Lahtonen - Convolutional Codes (With Exercises in Finnish) (2013) PDFDokument76 Seiten(Lecture Notes) Jyrki Lahtonen - Convolutional Codes (With Exercises in Finnish) (2013) PDFAhsan JameelNoch keine Bewertungen
- Notes On Fibonacci Trees and Their Optimality Yasuichi HoribeDokument11 SeitenNotes On Fibonacci Trees and Their Optimality Yasuichi HoribeΑλέξανδρος ΓεωργίουNoch keine Bewertungen
- Online and Streaming Algorithms For Clustering - UCSD - Lec6Dokument9 SeitenOnline and Streaming Algorithms For Clustering - UCSD - Lec6Thuy NguyenNoch keine Bewertungen
- Shannon's theorem for noisy channelsDokument7 SeitenShannon's theorem for noisy channelsSoham PalNoch keine Bewertungen
- SET2SOLNDokument6 SeitenSET2SOLNporplemontageNoch keine Bewertungen
- PFTKDokument2 SeitenPFTKweitsangNoch keine Bewertungen
- Performance 99Dokument7 SeitenPerformance 99Tessla ArakalNoch keine Bewertungen
- Homework answers analyze network protocolsDokument6 SeitenHomework answers analyze network protocolsAjay MalikNoch keine Bewertungen
- National Institute of Technology Exam Questions on Statistical Signal TheoryDokument4 SeitenNational Institute of Technology Exam Questions on Statistical Signal TheoryPratiksha HoleyNoch keine Bewertungen
- EE616A Semiconductor modelling examDokument2 SeitenEE616A Semiconductor modelling examrik_deyNoch keine Bewertungen
- Matter Waves: PH 333: Quantum PhysicsDokument22 SeitenMatter Waves: PH 333: Quantum PhysicsAntonio BernardoNoch keine Bewertungen
- Advanced Algorithms Course - Small Vertex CoversDokument3 SeitenAdvanced Algorithms Course - Small Vertex CoversKasapaNoch keine Bewertungen
- The Primes That Euclid ForgotDokument6 SeitenThe Primes That Euclid ForgotCarlos Adrian SoberanoNoch keine Bewertungen
- Module 2 - Sample Delay CalculationsDokument2 SeitenModule 2 - Sample Delay CalculationsBehin SamNoch keine Bewertungen
- Nearly-Free Electrons Model: Jacob Shapiro December 18, 2012Dokument7 SeitenNearly-Free Electrons Model: Jacob Shapiro December 18, 2012nouserhere123Noch keine Bewertungen
- E0 235. Cryptography Assignment 1: Answer 1Dokument4 SeitenE0 235. Cryptography Assignment 1: Answer 1Biswajit NagNoch keine Bewertungen
- HC1 Kernels5 OnlineDokument52 SeitenHC1 Kernels5 Onlinefrefre12345Noch keine Bewertungen
- Introduction to Quantum Physics Wave Packet ProblemsDokument3 SeitenIntroduction to Quantum Physics Wave Packet ProblemsSUDEEP SAHANoch keine Bewertungen
- Solutions To Assignment1Dokument4 SeitenSolutions To Assignment1semacokNoch keine Bewertungen
- Delay CalculationsDokument2 SeitenDelay CalculationsYohannes AbrhaNoch keine Bewertungen
- Lecture 13: Coding, Error Detection and CorrectionDokument44 SeitenLecture 13: Coding, Error Detection and CorrectionAlexis Marcano PradaNoch keine Bewertungen
- Fourier TransformDokument7 SeitenFourier TransformMahmoud NaguibNoch keine Bewertungen
- Spaces of PL Manifolds and Categories of Simple Maps (AM-186)Von EverandSpaces of PL Manifolds and Categories of Simple Maps (AM-186)Noch keine Bewertungen
- When Least Is Best: How Mathematicians Discovered Many Clever Ways to Make Things as Small (or as Large) as PossibleVon EverandWhen Least Is Best: How Mathematicians Discovered Many Clever Ways to Make Things as Small (or as Large) as PossibleBewertung: 3 von 5 Sternen3/5 (4)
- PROBABILITY DISTRIBUTIONSDokument16 SeitenPROBABILITY DISTRIBUTIONSSam prabhakarNoch keine Bewertungen
- Republic of the Philippines Science and Technology University course syllabusDokument5 SeitenRepublic of the Philippines Science and Technology University course syllabusIris Kayte Huesca EvicnerNoch keine Bewertungen
- (10.5.23) Applications of Queuing Theory in Quantitative Business AnalysisDokument5 Seiten(10.5.23) Applications of Queuing Theory in Quantitative Business AnalysisGrace MeldiNoch keine Bewertungen
- Optimization Research Problems and SolutionsDokument2 SeitenOptimization Research Problems and SolutionsrkNoch keine Bewertungen
- Poisson DistributionDokument5 SeitenPoisson DistributionSoftkillerNoch keine Bewertungen
- Syllabus CS1 IFoA 2019 FinalDokument13 SeitenSyllabus CS1 IFoA 2019 FinalnalinlNoch keine Bewertungen
- Cars Arriving For Gasoline at A Shell Station Foll...Dokument5 SeitenCars Arriving For Gasoline at A Shell Station Foll...ilyasNoch keine Bewertungen
- Exponential DistributionDokument9 SeitenExponential DistributionJoshua BautistaNoch keine Bewertungen
- Course Guide in EnggMath 3Dokument13 SeitenCourse Guide in EnggMath 3Iano LeungNoch keine Bewertungen
- Normal Distribution Problems & SolutionsDokument7 SeitenNormal Distribution Problems & SolutionsKeyur PopatNoch keine Bewertungen
- QT Assignment FinalDokument17 SeitenQT Assignment FinalParikshit KoiriNoch keine Bewertungen
- Quiz 4 Bme4aDokument15 SeitenQuiz 4 Bme4aUsman YounasNoch keine Bewertungen
- (International Series On Actuarial Science) David C. M. Dickson - Insurance Risk and Ruin-Cambridge University Press (2016)Dokument306 Seiten(International Series On Actuarial Science) David C. M. Dickson - Insurance Risk and Ruin-Cambridge University Press (2016)Parakh AhoojaNoch keine Bewertungen
- CS1 CMP Upgrade 2020Dokument94 SeitenCS1 CMP Upgrade 2020Devesh MaheshwariNoch keine Bewertungen
- Hvac Chapter 6 Solution ManualDokument20 SeitenHvac Chapter 6 Solution ManualArijit GangulyNoch keine Bewertungen
- Panel Data Lecture RomeDokument47 SeitenPanel Data Lecture RomeAndri_Ahmad_Na_5590Noch keine Bewertungen
- Some Discrete and Continuous Probability DistributionsDokument20 SeitenSome Discrete and Continuous Probability DistributionsSheikh Fahad ShaonNoch keine Bewertungen
- 570.assignment 2 Frontsheet - Fall2020Dokument23 Seiten570.assignment 2 Frontsheet - Fall2020Nguyen Ngoc Long (FGW HN)Noch keine Bewertungen
- Hw4-Sol KBDokument7 SeitenHw4-Sol KBAnonymous LSu67KNoch keine Bewertungen
- Queuing Theory FundamentalsDokument22 SeitenQueuing Theory FundamentalsRaymund Rumbaoa IVNoch keine Bewertungen
- Ruin TheoryDokument29 SeitenRuin TheoryAnonymous M8Bvu4FExNoch keine Bewertungen
- Lean 6 Sigma FormulasDokument30 SeitenLean 6 Sigma FormulasHetal PatelNoch keine Bewertungen
- Business Statistics 6th Edition Levine Test Bank 1Dokument24 SeitenBusiness Statistics 6th Edition Levine Test Bank 1steven100% (36)
- Poisson DistributionDokument4 SeitenPoisson DistributionMT20622 Nik Nur Zahidah Binti Nik HassanNoch keine Bewertungen
- Extended Quasi-Likelihood Function Compares Variance FunctionsDokument13 SeitenExtended Quasi-Likelihood Function Compares Variance FunctionssssNoch keine Bewertungen
- in Binomial Distribution, The Formula of Calculating Standard Deviation Is A) Square Root of P B) Square Root of PQ D) Square Root of NP 2Dokument14 Seitenin Binomial Distribution, The Formula of Calculating Standard Deviation Is A) Square Root of P B) Square Root of PQ D) Square Root of NP 2Arunaachalam .uNoch keine Bewertungen
- Gamma-Poisson Distribution (FromDokument1 SeiteGamma-Poisson Distribution (FromJuan PiñeroNoch keine Bewertungen
- Probability MCQ'sDokument8 SeitenProbability MCQ'sannie naeem100% (1)
- Binomial, Poisson & Normal DistributionDokument17 SeitenBinomial, Poisson & Normal DistributionParth AnajwalaNoch keine Bewertungen