Beruflich Dokumente
Kultur Dokumente
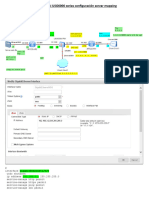
SRXB 1
Hochgeladen von
ufkazim2722Originaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
SRXB 1
Hochgeladen von
ufkazim2722Copyright:
Verfügbare Formate
system {
host-name srxB-1;
root-authentication {
encrypted-password "$1$KI99zGk6$MbYFuBbpLffu9tn2.sI7l1";
ssh-dsa "ssh-dss AAAAB3NzaC1kc3MAAACBAMQrfP2bZyBXJ6PC7XXZ+MzErI8Jl6jah5L
4/O8BsfP2hC7EvRfNoX7MqbrtCX/9gUH9gChVuBCB+ERULMdgRvM5uGhC/gs4UX+4dBbfBgKYYwgmisM
8EoT25m7qI8ybpl2YZvHNznvO8h7kr4kpYuQEpKvgsTdH/Jle4Uqnjv7DAAAAFQDZaqA6QAgbW3O/zve
aLCIDj6p0dwAAAIB1iL+krWrXiD8NPpY+w4dWXEqaV3bnobzPC4eyxQKBUCOr80Q5YBlWXVBHx9elwBW
Zwj0SF4hLKHznExnLerVsMuTMA846RbQmSz62vM6kGM13HFonWeQvWia0TDr78+rOEgWF2KHBSIxL51l
mIDW8Gql9hJfD/Dr/NKP97w3L0wAAAIEAr3FkWU8XbYytQYEKxsIN9P1UQ1ERXB3G40YwqFO484SlyKy
YCfaz+yNsaAJu2C8UebDIR3GieyNcOAKf3inCG8jQwjLvZskuZwrvlsz/xtcxSoAh9axJcdUfSJYMW/g
+mD26JK1Cliw5rwp2nH9kUrJxeI7IReDp4egNkM4i15o= configurator@server1.he"; ## SECRE
T-DATA
}
login {
user lab {
uid 2000;
class super-user;
authentication {
encrypted-password "$1$84J5Maes$cni5Hrazbd/IEHr/50oY30";
}
}
}
services {
ssh;
telnet;
web-management {
http;
}
}
syslog {
file messages {
any any;
authorization info;
}
file interactive-commands {
interactive-commands any;
}
}
}
interfaces {
ge-0/0/0 {
description "MGMT Interface - DO NOT DELETE";
unit 0 {
family inet {
address 10.210.12.133/26;
}
}
}
ge-0/0/3 {
unit 0 {
family inet {
address 172.18.1.2/30;
}
}
}
ge-0/0/4 {
vlan-tagging;
unit 103 {
vlan-id 103;
family inet {
address 172.20.103.1/24;
}
}
unit 203 {
vlan-id 203;
family inet {
address 172.20.203.1/24;
}
}
}
lo0 {
unit 0 {
family inet {
address 192.168.1.1/32;
}
}
}
}
routing-options {
static {
route 0.0.0.0/0 next-hop 172.18.1.1;
}
}
security {
address-book {
untrust {
address vr104 172.20.104.0/24;
address vr204 172.20.204.0/24;
address srxB-2 172.18.2.0/30;
attach {
zone untrust;
}
}
global {
address internet-host 172.31.15.1/32;
}
Juniper-SV {
address vr103 172.20.103.0/24;
attach {
zone Juniper-SV;
}
}
ACME-SV {
address vr203 172.20.203.0/24;
attach {
zone ACME-SV;
}
}
}
policies {
from-zone Juniper-SV to-zone Juniper-SV {
policy intrazone-Juniper-SV {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone ACME-SV to-zone ACME-SV {
policy intrazone-ACME-SV {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone Juniper-SV to-zone untrust {
policy outbound-ftp-auth {
match {
source-address vr103;
destination-address vr104;
application junos-ftp;
}
then {
permit;
}
}
policy deny-ftp-Juniper-SV {
match {
source-address any;
destination-address any;
application junos-ftp;
}
then {
reject;
}
}
policy internet-Juniper-SV {
match {
source-address vr103;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone ACME-SV to-zone untrust {
policy internet-ACME-SV {
match {
source-address vr203;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone Juniper-SV {
policy Juniper-WF-to-Juniper-SV {
match {
source-address vr104;
destination-address vr103;
application internal-apps;
}
then {
permit;
log {
session-init;
session-close;
}
}
scheduler-name internal-apps-scheduler;
}
policy inbound-ftp-auth {
match {
source-address vr104;
destination-address vr103;
application junos-ftp;
}
then {
permit {
firewall-authentication {
pass-through {
client-match ftp-group;
}
}
}
}
}
}
}
zones {
functional-zone management {
interfaces {
ge-0/0/0.0;
}
host-inbound-traffic {
system-services {
ssh;
telnet;
ping;
traceroute;
http;
snmp;
}
}
}
security-zone Juniper-SV {
interfaces {
ge-0/0/4.103;
}
}
security-zone ACME-SV {
interfaces {
ge-0/0/4.203;
}
}
security-zone untrust {
interfaces {
ge-0/0/3.0;
}
}
}
}
access {
profile ftp-users {
client nancy {
firewall-user {
password "$9$7bds4aJDmfz-VQn/9pu8XxdYg"; ## SECRET-DATA
}
}
client walter {
firewall-user {
password "$9$8S67wgoaUk.5GD.5zFtpM8L7bs4aZ"; ## SECRET-DATA
}
}
session-options {
client-group ftp-group;
}
}
firewall-authentication {
pass-through {
default-profile ftp-users;
ftp {
banner {
login "Junos Rocks!";
}
}
}
}
}
applications {
application Juniper-gizmo {
protocol udp;
source-port 50000;
destination-port 50001;
}
application-set internal-apps {
application Juniper-gizmo;
application junos-telnet;
application junos-ping;
}
}
schedulers {
scheduler internal-apps-scheduler {
daily {
start-time 03:00:00 stop-time 23:00:00;
}
sunday exclude;
saturday exclude;
}
}
Das könnte Ihnen auch gefallen
- Video Games Industry FinalDokument44 SeitenVideo Games Industry FinalZee100% (4)
- Ade 364 Ade366 Workshop Manual Abby PDFDokument297 SeitenAde 364 Ade366 Workshop Manual Abby PDFJesu Jese68% (34)
- Why Rife Was Right and Hoyland Was Wrong and What To Do About ItDokument4 SeitenWhy Rife Was Right and Hoyland Was Wrong and What To Do About ItHayley As Allegedly-Called Yendell100% (1)
- Juniper SRXDokument8 SeitenJuniper SRXAmit DongreNoch keine Bewertungen
- IEC 60364-1 Electrical Installations in Buildings PDFDokument80 SeitenIEC 60364-1 Electrical Installations in Buildings PDFMarin PopescuNoch keine Bewertungen
- ExcavationDokument18 SeitenExcavationBogdan-Gabriel SchiopuNoch keine Bewertungen
- Palo Alto Nat FlowDokument36 SeitenPalo Alto Nat FlowzcnznqbzNoch keine Bewertungen
- 5 - Balanced and Unbalanced FaultsDokument117 Seiten5 - Balanced and Unbalanced FaultsJuan Manuel VegaNoch keine Bewertungen
- Caution!: Portable Digital Color Doppler Ultrasound SystemDokument177 SeitenCaution!: Portable Digital Color Doppler Ultrasound SystemDaniel Galindo100% (1)
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityVon EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNoch keine Bewertungen
- Scooptram ST14 Battery: Fully Battery Electric Loader With 14-Tonne CapacityDokument8 SeitenScooptram ST14 Battery: Fully Battery Electric Loader With 14-Tonne CapacityAnonymous Mdw6y7Q1Noch keine Bewertungen
- Network InfrastructureDokument74 SeitenNetwork Infrastructuremsaamir115851Noch keine Bewertungen
- Test UGWDokument533 SeitenTest UGWasusf6veNoch keine Bewertungen
- Set Commands JuniperDokument2 SeitenSet Commands Juniperjamski1200Noch keine Bewertungen
- Configuracion Firewall 2-5-2013Dokument8 SeitenConfiguracion Firewall 2-5-2013Miguel Angel Medina BerdejaNoch keine Bewertungen
- Configuracion JuniperDokument7 SeitenConfiguracion JuniperBill WenNoch keine Bewertungen
- Boticas y Salud Sede Huaral 02 - FinalDokument29 SeitenBoticas y Salud Sede Huaral 02 - FinalAnonymous oz3YPvW9HNNoch keine Bewertungen
- Port Mirroring Juniper SRX SeriesDokument3 SeitenPort Mirroring Juniper SRX SeriesSergei ZNoch keine Bewertungen
- R 4Dokument10 SeitenR 4Ramon PirbuxNoch keine Bewertungen
- Aa JuniperDokument15 SeitenAa JuniperSiva TejaNoch keine Bewertungen
- Belajar Mengkonfigurasi MPLS-VPN (PE-CE OSPF) Di JunosDokument21 SeitenBelajar Mengkonfigurasi MPLS-VPN (PE-CE OSPF) Di JunosiwingNoch keine Bewertungen
- Bras SidneiDokument90 SeitenBras SidneiLuiz CarlosNoch keine Bewertungen
- Juniper MX 1Dokument2 SeitenJuniper MX 1Jignesh BhalsodNoch keine Bewertungen
- Racoon Road Warrior ConfigurationDokument20 SeitenRacoon Road Warrior Configurationapi-3801485100% (1)
- CONFIG CMFA CFA EXP Sematinya Sampai Juni V7.yaml (SFILEDokument12 SeitenCONFIG CMFA CFA EXP Sematinya Sampai Juni V7.yaml (SFILEdinar PNoch keine Bewertungen
- All Config Cfa - 4 April (SfileDokument7 SeitenAll Config Cfa - 4 April (SfileRiyo ParhanNoch keine Bewertungen
- Juniper RPM and Event PolicyDokument7 SeitenJuniper RPM and Event PolicyAlex MachadoNoch keine Bewertungen
- Juniper FRCDokument40 SeitenJuniper FRCatik rahmanNoch keine Bewertungen
- Configuration Script MA5600T DSLAM V2Dokument7 SeitenConfiguration Script MA5600T DSLAM V2Ahmed SalemNoch keine Bewertungen
- CONFIG CMFA CFA EXP Sematinya Sampai Juni V8.yaml (SFILEDokument12 SeitenCONFIG CMFA CFA EXP Sematinya Sampai Juni V8.yaml (SFILEdinar PNoch keine Bewertungen
- Run Show ConfigurationDokument7 SeitenRun Show ConfigurationINDONESIA TRANS NETWORKNoch keine Bewertungen
- CONFIG CMFA CFA EXP Sematinya Sampai Juni V3.yaml (SFILEDokument12 SeitenCONFIG CMFA CFA EXP Sematinya Sampai Juni V3.yaml (SFILEdinar PNoch keine Bewertungen
- CONFIG CMFA CFA EXP Sematinya Sampai Juni V10.yaml (SFILEDokument12 SeitenCONFIG CMFA CFA EXP Sematinya Sampai Juni V10.yaml (SFILEdinar PNoch keine Bewertungen
- SRX Series To SSG Series Route-Based VPN ConfigurationDokument3 SeitenSRX Series To SSG Series Route-Based VPN ConfigurationarjanditoNoch keine Bewertungen
- SRX Ad FW AuthenticationDokument2 SeitenSRX Ad FW AuthenticationSisir KarmakerNoch keine Bewertungen
- ALL CONFIG CFA 21 Mei (SFILEDokument7 SeitenALL CONFIG CFA 21 Mei (SFILEdinar PNoch keine Bewertungen
- Preview Lab Huawei USG600V Firewall eNSP NAT PoliciesDokument22 SeitenPreview Lab Huawei USG600V Firewall eNSP NAT PoliciesSantiago Miguel Tapia GuajardoNoch keine Bewertungen
- Hooo0323 IssabelDokument6 SeitenHooo0323 IssabelEdgar Eduardo A MenaNoch keine Bewertungen
- CONFIG CMFA CFA EXP Sematinya Sampai Juni V13.yaml (SFILEDokument12 SeitenCONFIG CMFA CFA EXP Sematinya Sampai Juni V13.yaml (SFILEdinar PNoch keine Bewertungen
- Tablita-Comandos 2.3Dokument2 SeitenTablita-Comandos 2.3hernan_27Noch keine Bewertungen
- Senp D Id98872 - MurallaDokument5 SeitenSenp D Id98872 - Murallaguerrerokarina276Noch keine Bewertungen
- CONFIG CMFA CFA EXP Sematinya Sampai Juni - Yaml (SFILEDokument12 SeitenCONFIG CMFA CFA EXP Sematinya Sampai Juni - Yaml (SFILEdinar PNoch keine Bewertungen
- Palo Commit ErrorDokument1 SeitePalo Commit ErrorGabin TALLANoch keine Bewertungen
- Configuring Multiple Default Routes On Juniper SRX Using Routing InstancesDokument7 SeitenConfiguring Multiple Default Routes On Juniper SRX Using Routing InstancesM.Raza ZaidiNoch keine Bewertungen
- Route Leaking in MPLS/VPN Networks: Document ID: 47807Dokument5 SeitenRoute Leaking in MPLS/VPN Networks: Document ID: 47807a3172741Noch keine Bewertungen
- SBC 162 Maiezdi Sub Branch AR 651Dokument5 SeitenSBC 162 Maiezdi Sub Branch AR 651WasimulHaq WaimulNoch keine Bewertungen
- Hooo 0325Dokument6 SeitenHooo 0325Edgar Eduardo A MenaNoch keine Bewertungen
- A VPN Gateway SetupDokument6 SeitenA VPN Gateway Setupachmadzulkarnaen100% (1)
- Admin LinuxDokument2 SeitenAdmin Linuxnina rajaNoch keine Bewertungen
- Juniper Netscreen - VPN TroubleshootingDokument8 SeitenJuniper Netscreen - VPN TroubleshootingrubinbrittoNoch keine Bewertungen
- Router AuditingDokument24 SeitenRouter AuditingBala JE/BSNLNoch keine Bewertungen
- Acx4000 2Dokument10 SeitenAcx4000 2ziblurNoch keine Bewertungen
- Ntf200-2012-Challange Working VLC Multicast-Ver2Dokument9 SeitenNtf200-2012-Challange Working VLC Multicast-Ver2Niklas Tokbollen RiddarloNoch keine Bewertungen
- Senha para Abrir A Postila: Vc#Awrq S2L0Dokument3 SeitenSenha para Abrir A Postila: Vc#Awrq S2L0Hitalo MonteiroNoch keine Bewertungen
- Huawei USG Series - Configuracion Server Mapping (NAT Srver)Dokument26 SeitenHuawei USG Series - Configuracion Server Mapping (NAT Srver)Santiago Miguel Tapia GuajardoNoch keine Bewertungen
- Example For Configuring PPPoE Access For IPv4 UsersDokument7 SeitenExample For Configuring PPPoE Access For IPv4 UsersFTTH ISPNoch keine Bewertungen
- After ActifityDokument119 SeitenAfter ActifitymdsalindriNoch keine Bewertungen
- Abq RTR01Dokument6 SeitenAbq RTR01Mar Stephen SembranoNoch keine Bewertungen
- CCNA Challenge QuestionDokument7 SeitenCCNA Challenge Questionfarmd684Noch keine Bewertungen
- LA DC Cyberark RulesDokument4 SeitenLA DC Cyberark Rulesrkgraman86Noch keine Bewertungen
- CCNA Security Practice SBADokument13 SeitenCCNA Security Practice SBAAnjula DissanayakeNoch keine Bewertungen
- SRX Transparent ModeDokument4 SeitenSRX Transparent ModeSon Tran Hong NamNoch keine Bewertungen
- Configuracion de Un SwitchDokument6 SeitenConfiguracion de Un SwitchwillyNoch keine Bewertungen
- Cisco CCNA CommandsDokument5 SeitenCisco CCNA CommandsDaniel Benavides ONoch keine Bewertungen
- Linux DHCP Server NotesDokument3 SeitenLinux DHCP Server Notesmaxim faqihNoch keine Bewertungen
- Share (SfileDokument7 SeitenShare (Sfilef.a.kemai.lm.y.idNoch keine Bewertungen
- Mixed-Port - 789-WPS OfficeDokument23 SeitenMixed-Port - 789-WPS OfficeVũ Đằng Minh AnNoch keine Bewertungen
- srx220 Juniper VPN ConfigDokument4 Seitensrx220 Juniper VPN ConfigHumberto BellidoNoch keine Bewertungen
- Toshiba Multi Split and Single Split Systems BrochureDokument32 SeitenToshiba Multi Split and Single Split Systems Brochurethanhlong2005Noch keine Bewertungen
- MDLink User Manual PDFDokument41 SeitenMDLink User Manual PDFkulov1592Noch keine Bewertungen
- Sixthsense: - Sanjana Sukumar 3Rd YearDokument2 SeitenSixthsense: - Sanjana Sukumar 3Rd YearSanjana SukumarNoch keine Bewertungen
- TCE BE EEE RulesandRegulationsDokument509 SeitenTCE BE EEE RulesandRegulationsAplieNoch keine Bewertungen
- Transition SignalsDokument10 SeitenTransition Signalshana nixmaNoch keine Bewertungen
- T-Spice User's Guide: Release 16.3 June 2015Dokument579 SeitenT-Spice User's Guide: Release 16.3 June 2015Laxmi GuptaNoch keine Bewertungen
- Sandisk X400 SSD (Solid State Drive) : The World'S First 1Tb, Single-Sided SSDDokument2 SeitenSandisk X400 SSD (Solid State Drive) : The World'S First 1Tb, Single-Sided SSDlechurzNoch keine Bewertungen
- The Impact of Greed On Academic Medicine and Patient CareDokument5 SeitenThe Impact of Greed On Academic Medicine and Patient CareBhawana Prashant AgrawalNoch keine Bewertungen
- Mouse 200Dokument2 SeitenMouse 200Amjad AliNoch keine Bewertungen
- GautierDokument164 SeitenGautierDimitar NedkovNoch keine Bewertungen
- 11kv BB1Dokument1 Seite11kv BB1Hammadiqbal12Noch keine Bewertungen
- EP T8 Diesel ForkliftsDokument7 SeitenEP T8 Diesel ForkliftsHein Sithu KyawNoch keine Bewertungen
- Assessment of Reinforcement CorrosionDokument5 SeitenAssessment of Reinforcement CorrosionClethHirenNoch keine Bewertungen
- 7ML19981GC61 1Dokument59 Seiten7ML19981GC61 1Andres ColladoNoch keine Bewertungen
- Alimentacion Baterias TiposDokument11 SeitenAlimentacion Baterias TiposjulioclavijoNoch keine Bewertungen
- Resume EeeeDokument4 SeitenResume EeeeWhilmark Tican MucaNoch keine Bewertungen
- Product Handling: Complete Solutions From A Single SourceDokument24 SeitenProduct Handling: Complete Solutions From A Single Sourcemarciojunk100% (1)
- Poiseuille Lab ExperimentDokument7 SeitenPoiseuille Lab ExperimentArjun SinghNoch keine Bewertungen
- Curriculum Vitae: Rajeev RanjanDokument3 SeitenCurriculum Vitae: Rajeev RanjanPratik AnandNoch keine Bewertungen
- Grade 7 and 8 November NewsletterDokument1 SeiteGrade 7 and 8 November Newsletterapi-296332562Noch keine Bewertungen
- Topic 5 FB Stability PDFDokument26 SeitenTopic 5 FB Stability PDFAbdulrahman NasserNoch keine Bewertungen
- New Process Performance IE4 Motors: Product NotesDokument2 SeitenNew Process Performance IE4 Motors: Product NotesCali MelendezNoch keine Bewertungen