Beruflich Dokumente
Kultur Dokumente
Zigbee Reminder System For Mobile Data Transfer in Airport
Hochgeladen von
देवेश सिंह राजपूतOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Zigbee Reminder System For Mobile Data Transfer in Airport
Hochgeladen von
देवेश सिंह राजपूतCopyright:
Verfügbare Formate
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 1 Introduction
VIVA INSTITUTE OF TECHNOLOGY
Page 1-1
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
1.1 IMPORTANCE OF PROJECT:Nowadays in airport use a fully wired system so here the cost of system is increased
due to using a wire or cable because of that the system complexity is also increased
and here have a fear of leaked a data which we have transmitted or received. The
security is not maintained here and this is the main purpose of our project, so that we
can overcome this drawback of current system using Zigbee wireless technology.
Our second main goal of the project is to decrease the processing time for passport
verification and increase the efficiency of airport management system and utilization
of time of passenger for better performance. Network in this paper the organization of
the paper is as follows. At first, the objectives, main concepts and the tools used are
mentioned. Then the system design is explained using flowcharts and later simulation
results are given along with the problems faced. Next, hardware implementation is
dealt with. Lastly, further developments are mentioned.
1.2 OBJECTIVES:1.2.1. Wireless
The wireless system refers to the communication which includes the data transmitter
and receiver by which we are sending information and receiving, the burden,
complexity and drawbacks of current wired system we are going to reduce
1.2.2. Security
We are designing the wireless system for maintaining security of prohibited areas
such as airports. Designing independent wireless system for the communication in
prohibited areas like airport by using the ZIGBEE TECHNOLOGY to maintain
security and privacy in these areas,
1.2.3. Low Cost
By using zigbee transceivers for wireless communication in airports we reduce the
cost of wires and other related hardware used to connect these wires.
1.2.4. Reduce processing time
It reduces the time required to process or verification at every counter on the airport
there by increasing the efficiency.
VIVA INSTITUTE OF TECHNOLOGY
Page 1-2
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
1.3 MAIN CONCEPT:The objectives of the system will be achieved by employing the following concepts.
1.3.1. Data command center
The device basically a central server managed by the government which issues
the passports to the peoples having all the information of passports. This command
centre managed in airport by the official who verifies the passports and gives pass
codes to the passengers for verification purpose which is used at every counter for
verification. This have zigbee module for wireless communication.
1.3.2. Mobile verification device
The code for verification is input at this device by using the keyboard which is
transmitted through the zigbee to data command center which verifies the code and
displays verification status on LCD display.
1.3.3. Software program
The pass code received by the receiver is verified by this program using the central
data base. This program is written in the C language.
1.3.4. Buzzer
When passport is verified using the pass-code provided by the passenger and if that is
wrong then at mobile device side the buzzer buzzes to tell the security officer that
something is wrong happening at particular gate . This maintains the security of the
airport which is frequently under threat now a day.
VIVA INSTITUTE OF TECHNOLOGY
Page 1-3
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
1.4ORAGANIZATION OF DESSERTION OF REPORT:Chapter 1: INTRODUCTION
It consists of the basic introduction about our deviceZigbee reminder system for mobile
data transfer in airport.
Chapter 2: LITERATURE SURVEY
It consists of Literature Survey of components and justify why we are choosing the selected
components.
Chapter 3: RELATED THEORY
It consists of Related Theory and basic description about the components we are using for
this device.
Chapter 4: DESIGN METHODOLOGY
In this chapter we are describing various software(Embedded C and BASCOM) and hardware
(components, circuit diagram and flowchart) methods and how we implemented the device.
Chapter 5: RESULTS AND DISCUSSIONS
The result obtained by implementing the device is mentioned in this chapter along with some
snapshots of our device.
Chapter 6: CONCLUSION AND FUTURE SCOPE
This chapter concludes our project and how the device is compatible with the existing
circuitry and what future implementations can be made in the device.
Chapter 7: REFERENCES
References from where we got the project ideas and the information about the components.
VIVA INSTITUTE OF TECHNOLOGY
Page 1-4
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 2 Literature Survey
VIVA INSTITUTE OF TECHNOLOGY
Page 2-5
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
2.1 INTRODUCTION:ZigBee is a specification for a suite of high level communication protocols used to create
personal area networks built from small, low-power digital radios. ZigBee is based on an
IEEE 802.15 standard. Though low-powered, ZigBee devices can transmit data over long
distances by passing data through intermediate devices to reach more distant ones,
creating a mesh network; i.e., a network with no centralized control or high-power
transmitter/receiver able to reach all of the networked devices. The decentralized nature
of such wireless ad hoc networks makes them suitable for applications where a central
node can't be relied upon.
ZigBee is used in applications that require only a low data rate, long battery life, and
secure networking. ZigBee has a defined rate of 250 Kbit/s, best suited for periodic or
intermittent data or a single signal transmission from a sensor or input device.
Applications include wireless light switches, electrical meters with in-home-displays,
traffic management systems, and other consumer and industrial equipment that requires
short-range wireless transfer of data at relatively low rates. The technology defined by
the ZigBee specification is intended to be simpler and less expensive than other WPANs,
such as Bluetooth or Wi-Fi.
ZigBee networks are secured by 128 bit symmetric encryption keys. In home automation
applications, transmission distances range from 10 to 100 meters line-of-sight, depending
on power output and environmental characteristics.
2.2 OVERVIEW:ZigBee is a low-cost, low-power, wireless mesh network standard. The low cost allows
the technology to be widely deployed in wireless control and monitoring applications.
Low power usage allows longer life with smaller batteries. Mesh networking provides
high reliability and more extensive range. ZigBee chip vendors typically sell integrated
radios and microcontrollers with between 60 KB and 256 KB flash memory.
ZigBee operates in the industrial, scientific and medical (ISM) radio bands: 868 MHz in
Europe, 915 MHz in the USA and Australia and 2.4 GHz in most jurisdictions
worldwide. Data transmission rates vary from 20 kilobits/second in the 868 MHz
frequency band to 250 kilobits/second in the 2.4 GHz frequency band.
The ZigBee network layer natively supports both star and tree typical networks, and
generic mesh networks. Every network must have one coordinator device, tasked with its
creation, the control of its parameters and basic maintenance. Within star networks, the
coordinator must be the central node. Both trees and meshes allow the use of
ZigBeerouters to extend communication at the network level.
VIVA INSTITUTE OF TECHNOLOGY
Page 2-6
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
ZigBee builds upon the physical layer and media access control defined in IEEE standard
802.15.4 (2003 version) for low-rate WPANs. The specification goes on to complete the
standard by adding four main components: network layer, application layer, ZigBee
device objects (ZDOs) and manufacturer-defined application objects which allow for
customization and favor total integration.
Besides adding two high-level network layers to the underlying structure, the most
significant improvement is the introduction of ZDOs. These are responsible for a number
of tasks, which include keeping of device roles, management of requests to join a
network, device discovery and security.
ZigBee is not intended to support powerline networking but to interface with it at least
for smart metering and smart appliance purposes. Because ZigBee nodes can go from
sleep to active mode in 30 ms or less, the latency can be low and devices can be
responsive, particularly compared to Bluetooth wake-up delays, which are typically
around three seconds. Because ZigBee nodes can sleep most of the time, average power
consumption can be low, resulting in long battery life.
The current list of application profiles either published, or in development are:
Released specifications
o ZigBee Home Automation 1.2
o ZigBee Smart Energy 1.1b
o ZigBee Telecommunication Services 1.0
o ZigBee Health Care 1.0
o ZigBee RF4CE Remote Control 1.0
o ZigBee RF4CE Input Device 1.0
o ZigBee Light Link 1.0
o ZigBee IP 1.0
o ZigBee Building Automation 1.0
o ZigBee Gateway 1.0
o ZigBee Green Power 1.0 as optional feature of ZigBee 2012
Specifications under development
o ZigBee Smart Energy 2.0
o ZigBee Retail Services
o ZigBee Smart Energy 1.2/1.3
o ZigBee Light Link 1.1
o ZigBee Home Automation 1.3
2.3 RADIO HARDWARE
The radio design used by ZigBee has been carefully optimized for low cost in large scale
production. It has few analog stages and uses digital circuits wherever possible.
VIVA INSTITUTE OF TECHNOLOGY
Page 2-7
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Though the radios themselves are inexpensive, the ZigBee Qualification Process
involves a full validation of the requirements of the physical layer. All radios derived
from the same validated semiconductor mask set would enjoy the same RF
characteristics. An uncertified physical layer that malfunctions could cripple the battery
lifespan of other devices on a ZigBee network. ZigBee radios have very tight constraints
on power and bandwidth. Thus, radios are tested with guidance given by Clause 6 of the
802.15.4-2006 Standard. Most vendors plan to integrate the radio and microcontroller
onto a single chip getting smaller devices.
This standard specifies operation in the unlicensed 2.4 GHz (worldwide), 915 MHz
(Americas and Australia) and 868 MHz (Europe) ISM bands. Sixteen channels are
allocated in the 2.4 GHz band, with each channel requiring 5 MHz of bandwidth. The
radios use direct-sequence spread spectrum coding, which is managed by the digital
stream into the modulator. Binary phase-shift keying (BPSK) is used in the 868 and
915 MHz bands, and offset quadrature phase-shift keying (OQPSK) that transmits two
bits per symbol is used in the 2.4 GHz band.
The raw, over-the-air data rate is 250 Kbit/s per channel in the 2.4 GHz band, 40 Kbit/s
per channel in the 915 MHz band, and 20 Kbit/s in the 868 MHz band. The actual data
throughput will be less than the maximum specified bit rate due to the packet overhead
and processing delays. For indoor applications at 2.4 GHz transmission distance may be
1020 m, depending on the construction materials, the number of walls to be penetrated
and the output power permitted in that geographical location.Outdoors with line-of-sight,
range may be up to 1500 m depending on power output and environmental
characteristics. The output power of the radios is generally 0-20 dBm (1-100 mW).
2.4 DEVICES TYPE AND OPERATING MODE
ZigBee devices are of three types:
ZigBee Coordinator (ZC): The most capable device, the Coordinator forms the root of
the network tree and might bridge to other networks. There is exactly one ZigBee
Coordinator in each network since it is the device that started the network originally
(the ZigBeeLight Link specification also allows operation without a ZigBee
Coordinator, making it more usable for over-the-shelf home products). It stores
information about the network, including acting as the Trust Center& repository for
security keys.
ZigBee Router (ZR): As well as running an application function, a Router can act as
an intermediate router, passing on data from other devices.
ZigBee End Device (ZED): Contains just enough functionality to talk to the parent
node (either the Coordinator or a Router); it cannot relay data from other devices.
This relationship allows the node to be asleep a significant amount of the time thereby
giving long battery life. A ZED requires the least amount of memory, and therefore
can be less expensive to manufacture than a ZR or ZC.
VIVA INSTITUTE OF TECHNOLOGY
Page 2-8
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
The current ZigBee protocols support beacon and non-beacon enabled networks. In nonbeacon-enabled networks, an unslotted CSMA/CA channel access mechanism is used. In
this type of network, ZigBee Routers typically have their receivers continuously active,
requiring a more robust power supply. However, this allows for heterogeneous networks
in which some devices receive continuously, while others only transmit when an external
stimulus is detected. The typical example of a heterogeneous network is a wireless light
switch: The ZigBee node at the lamp may receive constantly, since it is connected to the
mains supply, while a battery-powered light switch would remain asleep until the switch
is thrown. The switch then wakes up, sends a command to the lamp, receives an
acknowledgment, and returns to sleep. In such a network the lamp node will be at least a
ZigBee Router, if not the ZigBee Coordinator; the switch node is typically a ZigBee End
Device.
In beacon-enabled networks, the special network nodes called ZigBee Routers transmit
periodic beacons to confirm their presence to other network nodes. Nodes may sleep
between beacons, thus lowering their duty cycle and extending their battery life. Beacon
intervals depend on data rate; they may range from 15.36 milliseconds to 251.65824
seconds at 250 Kbit/s, from 24 milliseconds to 393.216 seconds at 40 Kbit/s and from 48
milliseconds to 786.432 seconds at 20 Kbit/s. However, low duty cycle operation with
long beacon intervals requires precise timing, which can conflict with the need for low
product cost.
In general, the ZigBee protocols minimize the time the radio is on, so as to reduce power
use. In beaconing networks, nodes only need to be active while a beacon is being
transmitted. In non-beacon-enabled networks, power consumption is decidedly
asymmetrical: some devices are always active, while others spend most of their time
sleeping.
Except for the Smart Energy Profile 2.0, ZigBee devices are required to conform to the
IEEE 802.15.4-2003 Low-Rate Wireless Personal Area Network (LR-WPAN) standard.
The standard specifies the lower protocol layersthe physical layer (PHY), and the
media access control portion of the data link layer (DLL). The basic channel access
mode is "carrier sense, multiple access/collision avoidance" (CSMA/CA). That is, the
nodes talk in the same way that humans converse; they briefly check to see that no one
is talking before they start, with three notable exceptions. Beacons are sent on a fixed
timing schedule and do not use CSMA. Message acknowledgments also do not use
CSMA. Finally, devices in beacon-enabled networks that have low latency real-time
requirements may also use Guaranteed Time Slots (GTS), which by definition do not use
CSMA.
VIVA INSTITUTE OF TECHNOLOGY
Page 2-9
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
2.5 SOFTWARE
2.5.1 Network layer
The main functions of the network layer are to enable the correct use of the MAC
sublayer and provide a suitable interface for use by the next upper layer, namely the
application layer. Its capabilities and structure are those typically associated to such
network layers, including routing.
On the one hand, the data entity creates and manages network layer data units from the
payload of the application layer and performs routing according to the current topology.
On the other hand, there is the layer control, which is used to handle configuration of
new devices and establish new networks: it can determine whether a neighboring device
belongs to the network and discovers new neighbors and routers. The control can also
detect the presence of a receiver, which allows direct communication and MAC
synchronization.
The routing protocol used by the network layer is AODV. In order to find the destination
device, it broadcasts out a route request to all of its neighbors. The neighbors then
broadcast the request to their neighbors, etc. until the destination is reached. Once the
destination is reached, it sends its route reply via unicast transmission following the
lowest cost path back to the source. Once the source receives the reply, it will update its
routing table for the destination address with the next hop in the path and the path cost.
2.5.2 Application layer
The application layer is the highest-level layer defined by the specification, and is the
effective interface of the ZigBee system to its end users. It comprises the majority of
components added by the ZigBee specification: both ZDO and its management
procedures, together with application objects defined by the manufacturer, are
considered part of this layer.
2.6 Main components
The ZDO,(ZigBee Device Object (ZDO), a protocol in the ZigBee protocol stack, is
responsible for overall device management, and security keys and policies), is
responsible for defining the role of a device as either coordinator or end device, as
mentioned above, but also for the discovery of new (one-hop) devices on the network
and the identification of their offered services. It may then go on to establish secure links
with external devices and reply to binding requests accordingly.
The application support sublayer (APS) is the other main standard component of the
layer, and as such it offers a well-defined interface and control services. It works as a
bridge between the network layer and the other components of the application layer: it
keeps up-to-date binding tables in the form of a database, which can be used to find
VIVA INSTITUTE OF TECHNOLOGY
Page 2-10
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
appropriate devices depending on the services that are needed and those the different
devices offer. As the union between both specified layers, it also routes messages across
the layers of the protocol stack..
An application may consist of communicating objects which cooperate to carry out
thedesired tasks. The focus of ZigBee is to distribute work among many different devices
which reside within individual ZigBee nodes which in turn form a network (said work
will typically be largely local to each device, for instance the control of each individual
household appliance).
The collection of objects that form the network communicate using the facilities
provided by APS, supervised by ZDO interfaces. The application layer data service
follows a typical request-confirm/indication-response structure. Within a single device,
up to 240 application objects can exist, numbered in the range 1-240. 0 is reserved for
the ZDO data interface and 255 for broadcast; the 241-254 range is not currently in use
but may be in the future.
Two services are available for application objects to use (in ZigBee 1.0):
The key-value pair service (KVP) is meant for configuration purposes. It enables
description, request and modification of object attributes through a simple interface
based on get/set and event primitives, some allowing a request for response.
Configuration uses compressed XML (full XML can be used) to provide an adaptable
and elegant solution.
The message service is designed to offer a general approach to information treatment,
avoiding the necessity to adapt application protocols and potential overhead incurred
on by KVP. It allows arbitrary payloads to be transmitted over APS frames.
Addressing is also part of the application layer. A network node consists of an 802.15.4conformant radio transceiver and one or more device descriptions (basically collections
of attributes which can be polled or set, or which can be monitored through events). The
transceiver is the base for addressing, and devices within a node are specified by an
endpoint identifier in the range 1-240.
2.7 Communication and device discovery
In order for applications to communicate, their comprising devices must use a common
application protocol (types of messages, formats and so on); these sets of conventions are
grouped in profiles. Furthermore, binding is decided upon by matching input and output
cluster identifiers, unique within the context of a given profile and associated to an
incoming or outgoing data flow in a device. Binding tables contain source and
destination pairs.
Depending on the available information, device discovery may follow different methods.
When the network address is known, the IEEE address can be requested using unicast
VIVA INSTITUTE OF TECHNOLOGY
Page 2-11
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
communication. When it is not, petitions are broadcast (the IEEE address being part of
the response payload). End devices will simply respond with the requested address,
while a network coordinator or a router will also send the addresses of all the devices
associated with it.
This extended discovery protocol permits external devices to find out about devices in a
network and the services that they offer, which endpoints can report when queried by the
discovering device (which has previously obtained their addresses). Matching services
can also be used.
The use of cluster identifiers enforces the binding of complementary entities by means of
the binding tables, which are maintained by ZigBee coordinators, as the table must be
always available within a network and coordinators are most likely to have a permanent
power supply. Backups, managed by higher-level layers, may be needed by some
applications. Binding requires an established communication link; after it exists, whether
to add a new node to the network is decided, according to the application and security
policies.
Communication can happen right after the association. Direct addressing uses both radio
address and endpoint identifier, whereas indirect addressing uses every relevant field
(address, endpoint, cluster and attribute) and requires that they be sent to the network
coordinator, which maintains associations and translates requests for communication.
Indirect addresing is particularly useful to keep some devices very simple and minimize
their need for storage. Besides these two methods, broadcast to all endpoints in a device
is available, and group addressing is used to communicate with groups of endpoints
belonging to a set of devices.
2.8 Security services
As one of its defining features, ZigBee provides facilities for carrying out secure
communications, protecting establishment and transport of cryptographic keys,
cyphering frames and controlling devices. It builds on the basic security framework
defined in IEEE 802.15.4. This part of the architecture relies on the correct management
of symmetric keys and the correct implementation of methods and security policies.
2.8.1 Basic security model
The basic mechanism to ensure confidentiality is the adequate protection of all keying
material. Trust must be assumed in the initial installation of the keys, as well as in the
processing of security information. In order for an implementation to globally work, its
general conformance to specified behaviors is assumed.
Keys are the cornerstone of the security architecture; as such their protection is of
paramount importance, and keys are never supposed to be transported through an
insecure channel. A momentary exception to this rule occurs during the initial phase of
VIVA INSTITUTE OF TECHNOLOGY
Page 2-12
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
the addition to the network of a previously unconfigured device. The ZigBee network
model must take particular care of security considerations, as ad hoc networks may be
physically accessible to external devices and the particular working environment cannot
be foretold; likewise, different applications running concurrently and using the same
transceiver to communicate are supposed to be mutually trustworthy: for cost reasons the
model does not assume a firewall exists between application-level entities.
Within the protocol stack, different network layers are not cryptographically separated,
so access policies are needed and correct design assumed. The open trust model within a
device allows for key sharing, which notably decreases potential cost. Nevertheless, the
layer which creates a frame is responsible for its security. If malicious devices may exist,
every network layer payload must be ciphered, so unauthorized traffic can be
immediately cut off. The exception, again, is the transmission of the network key, which
confers a unified security layer to the network, to a new connecting device.
2.8.2 Security architecture
ZigBee uses 128-bit keys to implement its security mechanisms. A key can be associated
either to a network, being usable by both ZigBee layers and the MAC sublayer, or to a
link, acquired through pre-installation, agreement or transport. Establishment of link
keys is based on a master key which controls link key correspondence. Ultimately, at
least the initial master key must be obtained through a secure medium (transport or preinstallation), as the security of the whole network depends on it. Link and master keys
are only visible to the application layer. Different services use different one-way
variations of the link key in order to avoid leaks and security risks.
Key distribution is one of the most important security functions of the network. A secure
network will designate one special device which other devices trust for the distribution of
security keys: the trust center. Ideally, devices will have the trust center address and
initial master key preloaded; if a momentary vulnerability is allowed, it will be sent as
described above. Typical applications without special security needs will use a network
key provided by the trust center (through the initially insecure channel) to communicate.
Thus, the trust center maintains both the network key and provides point-to-point
security. Devices will only accept communications originating from a key provided by
the trust center, except for the initial master key. The security architecture is distributed
among the network layers as follows:
The MAC sublayer is capable of single-hop reliable communications. As a rule, the
security level it is to use is specified by the upper layers.
The network layer manages routing, processing received messages and being capable
of broadcasting requests. Outgoing frames will use the adequate link key according to
the routing, if it is available; otherwise, the network key will be used to protect the
payload from external devices.
VIVA INSTITUTE OF TECHNOLOGY
Page 2-13
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
The application layer offers key establishment and transport services to both ZDO and
applications. It is also responsible for the propagation across the network of changes
in devices within it, which may originate in the devices themselves (for instance, a
simple status change) or in the trust manager (which may inform the network that a
certain device is to be eliminated from it). It also routes requests from devices to the
trust center and network key renewals from the trust center to all devices. Besides
this, the ZDO maintains the security policies of the device.
The security levels infrastructure is based on CCM*, which adds encryption- and
integrity-only features to CCM.
2.9 Simulation of ZigBee networks
Network simulators, like NS2, OPNET, and NetSim can be used to simulate IEEE
802.15.4 ZigBee networks.
These simulators come with open source C or C++ libraries for users to modify. These
way users can check out the validity of new algorithms prior to hardware
implementation.
VIVA INSTITUTE OF TECHNOLOGY
Page 2-14
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 3 Related Theory
VIVA INSTITUTE OF TECHNOLOGY
Page 3-15
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
3.1 ZIGBEE:ZigBee is a specification for a suite of high level communication protocols using
small, low-power digital radios based on the IEEE 802.15.4-2003 standard for LowRate Wireless Personal Area Networks (LR-WPANs), such as wireless light switches
with lamps, electrical meters with in-home-displays, consumer electronics equipment
via short-range radio. The technology defined by the ZigBee specification is intended
to be simpler and less expensive than other WPANs, such as Bluetooth. ZigBee is
targeted at radio-frequency (RF) applications that require a low data rate, long battery
life, and secure networking
3.1.1 ZIGBEE 2.4 GHz kit:.
3.1 ZigBee 2.4Ghz kit
In order for applications to communicate, their comprising devices must use a
common application protocol (types of messages, formats and so on); these sets of
conventions are grouped in profiles. Furthermore, binding is decided upon by
matching input and output cluster identifiers, unique within the context of a given
profile and associated to an incoming or outgoing data flow in a device. Binding
tables contain source and destination pairs.
Depending on the available information, device discovery may follow different
methods. When the network address is known, the IEEE address can be requested
using unicast communication. When it is not, petitions are broadcast (the IEEE
address being part of the response payload). End devices will simply respond with the
requested address, while a network coordinator or a router will also send the addresses
of all the devices associated with it.
This extended discovery protocol permits external devices to find out about devices in
a network and the services that they offer, which endpoints can report when queried
by the discovering device (which has previously obtained their addresses). Matching
services can also be used.
VIVA INSTITUTE OF TECHNOLOGY
Page 3-16
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
The use of cluster identifiers enforces the binding of complementary entities by means
of the binding tables, which are maintained by ZigBee coordinators, as the table must
be always available within a network and coordinators are most likely to have a
permanent power supply. Backups, managed by higher-level layers, may be needed
by some applications. Binding requires an established communication link; after it
exists, whether to add a new node to the network is decided, according to the
application and security policies.
Communication can happen right after the association. Direct addressing uses both
radio address and endpoint identifier, whereas indirect addressing uses every relevant
field (address, endpoint, cluster and attribute) and requires that they be sent to the
network coordinator, which maintains associations and translates requests for
communication. Indirect addressing is particularly useful to keep some devices very
simple and minimize their need for storage. Besides these two methods, broadcast to
all endpoints in a device is available, and group addressing is used to communicate
with groups of endpoints belonging to a set of devices.
3.1.2 MAX 232:
Figure 3.2 max232
Since the RS232 is not compatible with todays microprocessors and
microcontrollers, we need a line drive (voltage convertor) to convert the RS232s
signals to the TTL voltage levels that will be acceptable to the 8051s TxD and RxD
pins. The MAX232 converts from RS232 voltage levels to TTL voltage levels, and
vice versa. One advantage of the MAX232 chip is that it uses a +5 V power source
which is the same as the source voltage for the 8051. In other words, with a single +5
V power supply we can power both the 8051 and MAX232, with no need for the dual
power supplies that are common in many older systems.
RS-232 is simple, universal, well understood and supportive. The serial port
transmits a '1' as -3 to -25 volts and a '0' as +3 to +25 volts. Devices which use serial
cables for their communication are split into two categories. These are DCE (Data
VIVA INSTITUTE OF TECHNOLOGY
Page 3-17
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Communications Equipment) and DTE (Data Terminal Equipment.) Data
Communications Equipment is devices such as the modem, TA adapter, plotter etc
while Data Terminal Equipment is your Computer or Terminal.
Advantages:
Serial Cables can be longer than Parallel cables. The serial port transmits a '1' as -3 to
-25 volts and a '0' as +3 to +25 volts where as a parallel port transmits a '0' as 0v and a
'1' as 5v. Therefore the serial port can have a maximum swing of 50V compared to the
parallel port which has a maximum swing of 5 Volts. Therefore cable loss is not going
to be as much of a problem for serial cables as they are for parallel.
Wires are less than parallel transmission.
Serial transmission is used where one bit is sent at a time.
Microcontrollers have also proven to be quite popular recently. Many of these have in
built SCI (Serial Communications Interfaces) which can be used to talk to the outside world.
Serial Communication reduces the pin count of these MPU's.
3.1.3 BUZZER:-
Figure 3.3 buzzer
A buzzer or beeper is an audio signalling device, which may be mechanical, electromechanical or piezoelectric .typical uses of buzzers and beepers include alarm
devices, timers and confirmation of user input such as a mouse click or keystroke.
Mechanical: a buzzer is an example of purely mechanical buzzer
Electro-mechanical: early devices were based on an electromechanical system
identical to an electric bell without the metal gong. Similarly, a relay may be
connected to interrupt its own actuating current, causing the contacts to buzz. Often
these units were anchored to a wall or ceiling to use it as a sounding board. The word
buzzer comes from the rasping noise that electromechanical buzzers made.
Piezoelectric: piezoelectric element may be driven by an oscillating electronic
circuit or other audio signal source. Driven with a piezoelectric audio amplifier.
VIVA INSTITUTE OF TECHNOLOGY
Page 3-18
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Sounds commonly used to indicate that a button has been pressed are a click, a ring or
abeep.
3.1.4 MATRIX KEY -BOARD:-
Figure 3.4 matrix keyboard
Many applications require large number of keys connected to a computing system.
Example includes a PC keyboard, Cell Phone keypad and Calculators. If we connect a
single key to MCU, we just connect it directly to I/O line. But we cannot connect, say 10
or 100 keys directly MCUs I/O. Because:It will eat up precious I/O line.
MCU to Keypad interface will contain lots of wires.
We want to avoid all these troubles so we use some clever technique. The technique is
called multiplexed matrix keypad. In this technique keys are connected in a matrix
(row/column) style as shown below.
The rows R0 to R3 are connected to Input lines of Microcontroller. The i/o pins where
they are connected are made Input. This is done by setting the proper DDR Register in
AVR and TRIS Register in PIC. The columns C0 to C3 are also connected to MCUs i/o
line. These are kept at High Impedance State (AKA input), in high z state (z=
impedance) state these pins are neither HIGH nor LOW they are in TRISTATE. And in
their PORT value we set them all as low, so as soon as we change their DDR bit to 1
they become output with value LOW.
One by One we make each Column LOW (from high Z state) and read state of R0 to R3.
VIVA INSTITUTE OF TECHNOLOGY
Page 3-19
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
As you can see in the image above C0 is made LOW while all other Columns are in
HIGH Z State. We can read the Value of R0 to R3 to get their pressed status. If they are
high the button is NOT pressed. As we have enabled internal pullups on them, these
pullups keep their value high when they are floating (that means NOT connected to
anything). But when a key is pressed it is connected to LOW line from the column thus
making it LOW.
After that we make the C0 High Z again and make C1 LOW. And read R0 to R3 again.
This gives us status of the second column of keys. Similarly we scan all columns.
3.1.5MICROCONTROLLER PIC16F887:-
Figure 3.5 PIC16F887
VIVA INSTITUTE OF TECHNOLOGY
Page 3-20
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Introduction:
This is powerful yet easy-to-program CMOS FLASH based microcontroller packs
architecture into an 40 or 44-pin package. The PIC16F887 features 256 bytes of
EEPROM data memory, self programming, an ICD, 2-comparators, 14 channels of
10-bit analog-to-digital converter, 1 capture/compare/PWM and one enhanced
capture/compare/PWM functions, a synchronous serial port that can be configured as
either 3-wire serial peripheral interface or the 2-wire inter-integrated circuit bus and
an enhanced universal asynchronous receiver transmitter. All of these features make it
ideal for more advanced level A/D applications in automotive, industrial, appliances
or consumer applications.
Features of PIC16F887:Following is the features of PIC18F887 microcontroller as per the datasheet:
Precision inter oscillator
Factory calibrated to +/- 1%
Software selectable frequency range of 8Mhz to 32Khz
Software tuneable
Two speed start-up mode
Fail safe clock monitoring for critical applications
Clock mode switching during operation for lower power operation
Power saving sleep mode
Power-on reset
Selectable brown out reset voltage
Extended watchdog timer with its on-chip RC oscillator for reliable operation
In-circuit serial programming via two pins
In circuit debug via two pins
Self-programmable under software 8-bit timer/counter with 8-bit prescaler
Programmable code protection
1 input only pin
36 I/O
High sink/source current 25mA
8-bit timer/counter with 8-bit prescaler
Auto-baud detect
Auto-wake on start bit
10-bit 14 channel A/D converter
Comparator input and outputs externally accessible
SR latch mode
VIVA INSTITUTE OF TECHNOLOGY
Page 3-21
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
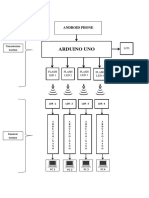
3.2BLOCK DIAGRAM:-
Figure 3.6 BLOCK DIAGRAM
Explanation:
According to block Diagram in this Project is divided in two different parts.
These parts are placed one as a data command centre which provides necessary data
base for verification and other is mobile data device which provides necessary
information for verification.
To work microcontroller needs1. Power supply +5V
2. Clock
Microcontroller takes the data and check the status according to the program
(Program in Embedded C language).
Microcontroller gives the first out put on LCD display (162 +5V). On LCD display
it shows the status.
Thus system verifies the passport and monitors the security of airport.
VIVA INSTITUTE OF TECHNOLOGY
Page 3-22
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
BLOCK DIAGRAM DESCRIPTION:3.2.1 INPUT SECTION:The Input section consists of threeparts. Mainly the input section consist of followingparts ,
PC s/w
RS232
ZigBee transmitter
PC S/W
The program which required to verify the passport is written in C language and
run in VISUAL BASIC 6 with the help of vb forms.
We used VB forms in our program for simplicity and convenience.
RS 232:
This zigbee kit is uses rs232 for serial communication to connect with the
personal computer
Zigbee transceiver:
It is used to communicate with the wireless mobile device for communication..
Step down Transformer:
Step down transformer is the first part of regulated power supply. To step down the
mains 230V A.C. we require step down transformer. Following are the main
characteristic of electronic transformer.
1) Power transformers are usually designed to operate from source of low impedance
at a single freq.
2) It is required to construct with sufficient insulation of necessary dielectric
strength.
3) Transformer ratings are expressed in voltamp. The volt-amp of each secondary
winding or windings are added for the total secondary VA. To this are added the
load losses.
4) Temperature rise of a transformer is decided on two well-known factors i.e. losses
on transformer and heat dissipating or cooling facility provided unit.
VIVA INSTITUTE OF TECHNOLOGY
Page 3-23
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
3.2.2OUTPUT SECTION:Output section consists of
Zigbee transceiver
RS232 & MAX232
PIC16F887
(162 +5V) LCD display
Buzzer
ZigBee transceiver receives status about verified passport or sends the initial
information for passport verification.
RS232 &. MAX232 are used to connect the zigbee kit and microcontroller.
Buzzer used to buzz for reminding purpose when pass-code is wrong.
3.3LCD USER INTERFACE:
LCD User Interface shows the status of the passport verification.
It also shows the numbers when passenger is entering the number
Figure 3.7 LCD DISPLAY
A liquid crystal display (LCD) is a thin, flat panel used for electronically displaying
information such as text, images, and moving pictures.
Its uses include monitors for computers, televisions, instrument panels, and other
devices ranging from aircraft cockpit displays, to every-day consumer devices such as
video players, gaming
devices,
clocks,
watches, calculators,
and telephones. Among its major features are its lightweight construction, its
portability, and its ability to be produced in much larger screen sizes than are practical
for the construction of cathode ray tube (CRT) display technology.
Its low electrical power consumption enables it to be used in battery-powered
electronic equipment.
It is an electronically-modulated optical device made up of any number of pixels
filled with liquid crystals and arrayed in front of a light source (backlight) or reflector
to produce images in color or monochrome.
VIVA INSTITUTE OF TECHNOLOGY
Page 3-24
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
The earliest discovery leading to the development of LCD technology, the discovery
of liquid crystals, dates from 1888.[1] By 2008, worldwide sales of televisions with
LCD screens had surpassed the sale of CRT units.
GENERAL SPECIFICATION:
Drive method: 1/16 duty cycle
Display size: 16 character * 2 lines
Character structure: 5*8 dots.
Display data RAM: 80 characters (80*8 bits)
Character generate ROM: 192 characters
Character generate RAM: 8 characters (64*8 bits)
Both display data and character generator RAMs can be read from MPU.
Internal automatic reset circuit at power ON.
Built in oscillator circuit.
VIVA INSTITUTE OF TECHNOLOGY
Page 3-25
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 4 Design Methodology
VIVA INSTITUTE OF TECHNOLOGY
Page 4-26
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
4.1 Introduction:In our project, we are using both the software & hardware tools. Software is based on the
Embedded C with compiler BASCOM.In hardware we are using microcontroller, microchips,
transformer, wireless zigbee kit, display etc
4.2 SOFTWARE USED:Embedded C:
As time progressed, use of microprocessor-specific assembly-only as the
programming language reduced and embedded systems moved onto C as
the embedded programming language of choice.
C is the most widely used programming language for embedded
processors/controllers. Assembly is also used but mainly to implement those portions
of the code where very high timing accuracy, code size efficiency, etc. are prime
requirements.
As assembly language programs are specific to a processor, assembly language didnt
offer portability across systems. To overcome this disadvantage, several high level
languages, including C, came up. Some other languages like PLM, Modula-2, Pascal,
etc. also came but couldnt find wide acceptance.
Amongst those, C got wide acceptance for not only embedded systems, but also for
desktop applications. Even though C might have lost its sheen as mainstream
language for general purpose applications, it still is having a strong-hold in embedded
programming. Due to the wide acceptance of C in the embedded systems, various
kinds of support tools like compilers & cross-compilers, ICE, etc. came up and all this
facilitated development of embedded systems using C.
Advantages:
It is small and reasonably simpler to learn, understand, program and debug.
Compared to assembly language, C Code written is more reliable and scalable, more
portable between different platform.
C Compilers are available for almost all embedded devices in use today, and there is a
large pool of experienced C programmers.
Unlike assembly, C has advantage of processor-independence and is not specific to
any particular microprocessor/ microcontroller or any system. This makes it
convenient for a user to develop programs that can run on most of the systems.
As C combines functionality of assembly language and features of high level
languages, C is treated as a middle-level computer language or high level assembly
language
It is fairly efficient
It supports access to I/O and provides ease of management of large embedded
projects.
VIVA INSTITUTE OF TECHNOLOGY
Page 4-27
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
4.2.1Compiler:VISUAL BASIC 6.0
VIAUAL BASIC 6.0 is the Windows software. It is designed to run on
W95/W98/NT/W2000 and XP.
VISUAL BASIC is a high level programming language which evolved from the earlier DOS
version called BASIC.BASIC means Beginners' All-purpose Symbolic Instruction Code. It is
a very easy programming language to learn. The code looks a lot like English Language.
people prefer to use Microsoft Visual Basic today, as it is a well developed programming
language and supporting resources are available everywhere.VISUAL BASIC is a VISUAL
and events driven Programming Language.In VB, programming is done in a graphical
environment. In the old BASIC, you have to write program code for each graphical object
you wish to display it on screen, including its position and its color. However, In VB, you
just need to drag and drop any graphical object anywhere on the form, and you can change its
color any time using the properties windows.
4.2.2KEY FEATURES:Visual Basic was designed to be easily learned and used by beginner programmers. The
language not only allows programmers to create simple GUI applications, but can also
develop complex applications. Programming in VB is a combination of visually arranging
components or controls on a form, specifying attributes and actions of those components, and
writing additional lines of code for more functionality. Since default attributes and actions are
defined for the components, a simple program can be created without the programmer having
to write many lines of code. Performance problems were experienced by earlier versions, but
with faster computers and native code compilation this has become less of an issue.
Forms are created using drag-and-drop techniques. A tool is used to place controls (e.g., text
boxes, buttons, etc.) on the form (window). Controls have attributes and event handlers
associated with them. Default values are provided when the control is created, but may be
changed by the programmer. Many attribute values can be modified during run time based on
user actions or changes in the environment, providing a dynamic application The Visual
Basic compiler is shared with other Visual Studio languages (C, C++), but restrictions in the
IDE do not allow the creation of some targets (Windows model DLLs) and threading models.
VISUAL BASIC6:
With VB 6, you can create any program depending on your objective. For example, if you are
a college or university lecturer, you can create educational programs to teach business,
economics, engineering, computer science, accountancy, financial management, information
system and more to make teaching more effective and interesting. If you are in business, you
can also create business programs such as inventory management system,point-of-sale
system, payroll system, financial program as well as accounting program to help manage
your business and increase productivity. For those of you who like games and working as
VIVA INSTITUTE OF TECHNOLOGY
Page 4-28
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
games programmer, you can create those programs as well. Indeed, there is no limit to what
program you can create! There are many such programs in this tutorial, so you must spend
more time on the tutorial in order to learn how to create those programs.
START PAGE:
Before you can program in VB 6, you need to install Visual Basic 6 in your computer.
On start up, Visual Basic 6.0 will display the following dialog box as shown in figure 1.1.
You can choose to start a new project, open an existing project or select a list of recently
opened programs. A project is a collection of files that make up your application. There are
various types of applications that we could create; however, we shall concentrate on creating
Standard EXE programs (EXE means executable program). Now, click on the Standard EXE
icon to go into the actual Visual Basic 6 programming environment.
The Development Environment or Form Window :Learning the ins and outs of the
Development Environment before you learn visual basic is somewhat like learning for
a test you must know where all the functions belong and what their purpose is. First we
will start with labeling the development environment.
VIVA INSTITUTE OF TECHNOLOGY
Page 4-29
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
The above diagram shows the development environment with all the important points
labeled. Many of Visual basic functions work similar to Microsoft word e.g. the Tool
Barand the tool box is similar to other products on the market which work off a single
click then drag the width of the object required. The Tool Boxcontains the control you
placed on the form window. All of the controls that appear on the Tool Boxcontrols on
the above picture never runs out of controls as soon as you place one on the form another
awaits you on the Tool Boxready to be placed as needed.
VIVA INSTITUTE OF TECHNOLOGY
Page 4-30
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
4.3 FLOWCHART: Main Flowchart:START
ENTER THE PASS-CODE
Tx TO DATA COMMAND CENTRE FOR
VERIFICATION
CORRECT
CORRECT
PASS-CODE
OR
WRONG
PASS-CODE
WRONG?
BUZZER
Figure 4.1 MAIN FLOWCHART
Start the program and mobile data executer device.
Passenger will enter the pass-code using the key-board.
This data is transmitting to data command centre for verification using the ZigBee
transceiver.
Here using program decision is taken about the pass-code,
a. If pass-code is correct, then the status is displayed on the monitor and
counter device.
b. If pass-code is wrong then the status is displayed on the screen and buzzes
the alarm for reminding purpose.
VIVA INSTITUTE OF TECHNOLOGY
Page 4-31
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Data command centre:-
START
RECEIVE PASS-CODE
VERIFY PASS-CODE
DISPLAY VERIFIED STATUS
SEND BACK THE RESULT
ZigBee TRANSEIVER
Figure 4.2 DATA COMMAND CENTRE
Receive the entered pass-code through ZigBee from the mobile data command centre.
Verify using the program.
Display the verified result as a status on the monitor.
Send back this verified result back to the mobile data command centre for the the
display purpose using ZigBee transceiver.
VIVA INSTITUTE OF TECHNOLOGY
Page 4-32
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Mobile Device :START
SWITCH ON THE KIT
ENTER THE PASS-CODE
CONVERT TO SERIAL DIGITAL BEAT FORM. .
SEND TO DATA COMMAND CENTRE
ZigBee
TRANSCIVER
Figure 4.3 MOBILE DATA COMMAND EXECUTER
Switch on the kit by using the on-off switch
Enter the pass-code by using the key board provided on the counter
Programmed microcontroller convert it into the digital binary form
Sent to the data command centre for verification using the data base
The verified status received from data command centre will display on the device on
LCD screen.
VIVA INSTITUTE OF TECHNOLOGY
Page 4-33
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
4.4 HARDWARE:1.
ZigBee 2.4Ghz kit
2.
Microcontroller PIC16F887
3.
Matrix keyboard
4.
Buzzer
5.
2- 6V batteries.
6.
16*2 LCD display
7.
MAX 232 Chip
8.
Transformer
VIVA INSTITUTE OF TECHNOLOGY
Page 4-34
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
4.4.1 CIRCUIT DIAGRAM AND DESCRIPTION:CIRCUIT DIAGRAM:-
Figure 4.4 CIRCUIT DIAGRAM
4.4.2 CIRCUIT DESCRIPTION:
The main components of the circuit diagram shown above are Microcontroller
PIC16F887, ZigBee kit, MAX232 chip, 4*4 matrix keyboard and 2*16 LCD display.
The numerical values entered at the keyboard are in analog form, they are given as an
input to the microcontroller which convertss it into equivalent digital form.
The microcontrollers basically need clock, power supply to function properly ,
pic16f887 is a 40 pin microcontroller in which pin no 11,32 are connected to power
supply and pin no 1is connected to +5v power supply by 10k resistor.
Pin no 12 & 31 both are ground pins connected to the ground. Pin no 13 and 14 are
clock i/p pins, which are connected to 4 MHz crystal oscillator and through 22pf
capacitor to ground.
We connect 16*2 LCD display ports 4, 5, 6, 11,12and 13 are connected to port B of
microcontroller pic16f887 at port 34 to 40.
Port 1 and 16 of LCD display are connected to ground and at port 3, there is a 1k
variable resistor and port 2 is connected to +5v power supply.
VIVA INSTITUTE OF TECHNOLOGY
Page 4-35
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
The buzzer is connected to port 15 of microcontroller.
MAX232 ic which is used for RS232 serial communication ports 9 and 10 are
connected to 25 and 26 ports , which are RX and TX ports of pic16 and ZigBee is
connected to 7,8 pin of the MAX232.
Working:
Objective:
The main objective of the device is to simplify and reduce the time required
for passport verification with additional security features provided in it with
power consumption using 2.4 GHz wireless ZigBee kit.
Basic idea behind the project:
The basic idea behind the project is that we are removes wires in the airport
and we use ZigBee for wireless implementation.
At the various counters, we provided the wireless kits at which passenger
have to input the pass-code which is verified by using the data base and status
is displayed.
If the pass-code or passport is wrong then automatically buzzes the buzzer for
reminding about the security threat.
The device basically works on 2 modes:
1. Correct pass-code mode.
2. Wrong pass-code mode.
1. Correct pass-code mode:
In this mode when the passenger enters the pass-code provided by the passport
verification officials by using the keyboard provided at the wireless kit.
This code is verified by the data command centre by using its database.
At this mode the code is correct and status is displayed at the both side as a
verified passport
2. Wrong pass-code mode:
In this mode when the passenger enters the pass-code provided by the passport
verification officials by using the keyboard provided at the wireless kit.
VIVA INSTITUTE OF TECHNOLOGY
Page 4-2
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Pass-code is verified and that is wrong then status displayed on both side as a
wrong passport
Then automatically buzzes the buzzer for reminding the security officers.
PCB Layouts:1. Circuit Layout:-
2. Power Supply:-
VIVA INSTITUTE OF TECHNOLOGY
Page 4-3
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 5 Results and Discussions
VIVA INSTITUTE OF TECHNOLOGY
Page 5-4
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
This ZBRS system provides efficient wireless system for passport verification on
airports,
This system has top priority for security.
On the various counters on airport passengers just have to enter the pass code
provided by the official which reduces the considerable time for verification , which is
very important issue for airport neat functioning and for passengers.
The two modes that are:
i.
On mobile device which is placed at the gate assume and has the keyboard,
passenger enters the code which verified by data command centre and
status displayed on the command centre and mobile device for further
action.
ii.
ii. when passenger enter the code and that is unauthorized then status
displayed on the mobile that is passenger is unauthorized and buzzes alarm
at mobile device for further action by security authorities.
ADVANTAGES:
1. Simple and user-friendly interface.
2. Reduces processing time for passenger and airport authorities.
3. displays status.
4. Alarm when status is not verified.
5. Secure.
6. Longer battery life.
OBSTACLES FOR THE SYSTEM:1. This system can communicate in the range of zigbee transceiver only.
2. pass-code can be stolen by others.
3. One person has to look-out data command centre for possible errors.
4. Batteries will have to change after discharging.
VIVA INSTITUTE OF TECHNOLOGY
Page 5-5
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
DISCUSSION:
Passport verified :
As we see in this figure the pass code entered by the passenger is accepted by the
system and shown status as ACCEPTED
Status Display at mobile device :
VIVA INSTITUTE OF TECHNOLOGY
Page 5-6
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
FAKE PASSPORT :
As we see in this figure the pass code entered by the passenger is not accepted by
the system and shown status as NOT ACCEPTED
Status Display at mobile device :
VIVA INSTITUTE OF TECHNOLOGY
Page 5-7
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 6 Conclusion and Future Scope
VIVA INSTITUTE OF TECHNOLOGY
Page 6-8
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
CONCLUSION:
This focuses on ways to designing the wireless and secure system for passport
verification.
Thus, it may replace the existing electrical wired system in the airports for
considerable reduction in the time for verification.
The time saved by this system passengers can use for shopping at the airports which
increases the revenue of the airport.
Secure transmission through encryption by using the using zigbee wireless system.
Reduction in power requirements.
FUTURE SCOPE:-
This system can be integrated with the face detection technology and finger prints
scanning for further secure the airport.
We can also use this system for other purposes also in the airport which further
improves the airport functioning.
For the battery charging purpose we can use solar power, it reduces the global
warming.
In future when the zigbee available in the mobiles we can give updates to the
passengers outside the airport premises about the current status of the flight.
VIVA INSTITUTE OF TECHNOLOGY
Page 6-9
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 7 References
VIVA INSTITUTE OF TECHNOLOGY
Page 7-10
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Reference :
1) IEEE Std 802.15.14: MAC and PHY Specifications for Low-Rate Wireless Personal
Area Networks (LR-WPANs), 2003
2) ZigBee Alliance, ZigBee Specification v1.0, 2004
3) Hong Kong International Airport, http://www.hongkongairport.com/
4) Department of census & statistics of Hong Kong Government, SAR,
http://www.censtatd.gov.hk/FileManager/EN/Content_807/transport.pdf
1) www.wikepedia.com\zigbee
VIVA INSTITUTE OF TECHNOLOGY
Page 7-11
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 8 Appendix A
VIVA INSTITUTE OF TECHNOLOGY
Page 7-12
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
8.1 Cost Analysis of Components:product Image
Item NameMicrocontroller PIC16F877
Price
Rs.200.00
MAX232 ic
Rs.22.00
Rs.10.00
1R to 1M Resistor 1/4 W
(10Pcs)
VIVA INSTITUTE OF TECHNOLOGY
1N4007
1.0A general purpose rectifier diode.
Rs.2.00
22pf ceramic disk capacitor
Rs.1.00
100 to 1000 uf electrolytic capacitor
Rs.8.00
7805 - 5V voltage regulator
This is an positive 5V - 500mA to
1.5A regulator
Rs.15.00
Page 7-13
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
LED Red 5mm
Rs.2.00
16x2 LCD with green Backlight
Rs.240.00
40 Pin IC Base
RS232 cable
Rs.400.00
BUZZER
Rs.25
push to on switch
VIVA INSTITUTE OF TECHNOLOGY
Rs.20.00
Rs.20.00
Page 7-14
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
6V battery
Rs.180.00
230v/6v Transformer
Rs.120.00
230v 2 pin power cord
Rs.20.00
8.2 Program:#include<pic.h>
#define _XTAL_FREQ 4000000
__CONFIG(0x2034);
__CONFIG(0x3fff);
#include<delay1.h>
#include<hextobcd.h>
#define rs RB0
#define rw RB1
#define en RB2
#define lcdport PORTB
#include<lcd4bit.h>
#define row1 RD0
#define row2 RD1
#define row3 RD2
#define row4 RD3
#define col1 RD4
#define col2 RD5
VIVA INSTITUTE OF TECHNOLOGY
Page 7-15
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
#define col3 RD6
#define col4 RD7
#define alarm RC0
const char convert[16]='0','1','2','3','4','5','6','7','8','9','A','B','C','D','E','F';
unsignedinttemp,keyvalue,try;
void key();
void check();
void main()
{
ANSEL=0X00;
ANSELH=0X00;
TRISA=0xFF;
TRISD=0xF0;
TRISC=0xF0;
TRISB=0x00;
// PORTA is input
// PORTD is input
// PORTC is output
// PORTB is output
PORTC=0x00; // PORTC is output
alarm=0;
BAUDCTL=0x00;
TXSTA=0b00100100; // Configure serialport
RCSTA=0b10010000; // Configure serialport
SPBRG=25; // Configure serialport
SPBRGH=0;
delay(50);
initialise_lcd();
initialise_lcd();
initialise_lcd();
delay(50);
command(0x01);
lcddisp(0x80,"ZIGBEE REMAINDER");
lcddisp(0xC0," FOR AIRPORTS ");
delay(3000);
while(1)
VIVA INSTITUTE OF TECHNOLOGY
Page 7-16
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
{
alarm=0;
command(0x01);
lcddisp(0x80,"ENTER NUMBER
");
command(0xc0);
key();
digit1=keyvalue;
display(convert[keyvalue]);
key();
digit2=keyvalue;
display(convert[keyvalue]);
key();
digit3=keyvalue;
display(convert[keyvalue]);
key();
digit4=keyvalue;
display(convert[keyvalue]);
key();
if(keyvalue==0x0b)
{
TXREG='F';
delay(50);
TXREG=(convert[digit1]);
delay(50);
TXREG=(convert[digit2]);
delay(50);
TXREG=(convert[digit3]);
delay(50);
TXREG=(convert[digit4]);
delay(50);
}
}
}
/////////////////////////////////////////////////////////////////////////////////////////////////////////////
void key()
{
//clear row1 and set row2,3&4
VIVA INSTITUTE OF TECHNOLOGY
Page 7-17
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
while(1)
{
row1=0;
row2=1;
row3=1;
row4=1;
delay(50);
if(col1==0)
{
keyvalue=0x00;
goto exit;
}
else if(col2==0)
{
keyvalue=0x01;
goto exit;
}
else if(col3==0)
{
keyvalue=0x02;
goto exit;
}
else if(col4==0)
{
keyvalue=0x03;
goto exit;
}
else
{
}
row1=1;
row2=0;
row3=1;
row4=1;
delay(50);
//clear row2 and set row1,3&4
if(col1==0)
{
keyvalue=0x04;
goto exit;
}
else if(col2==0)
{
VIVA INSTITUTE OF TECHNOLOGY
Page 7-18
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
keyvalue=0x05;
goto exit;
}
else if(col3==0)
{
keyvalue=0x06;
goto exit;
}
else if(col4==0)
{
keyvalue=0x07;
goto exit;
}
else
{
}
//clear row3 and set row1,2&4
row1=1;
row2=1;
row3=0;
row4=1;
delay(50);
if(col1==0)
{
keyvalue=0x08;
goto exit;
}
else if(col2==0)
{
keyvalue=0x09;
goto exit;
}
else if(col3==0)
{
keyvalue=0x0a;
goto exit;
}
else if(col4==0)
{
keyvalue=0x0b;
goto exit;
}
else
VIVA INSTITUTE OF TECHNOLOGY
Page 7-19
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
{
}
//clear row4 and set row1,2&3
row1=1;
row2=1;
row3=1;
row4=0;
delay(50);
if(col1==0)
{
keyvalue=0x0c;
goto exit;
}
else if(col2==0)
{
keyvalue=0x0d;
goto exit;
}
else if(col3==0)
{
keyvalue=0x0e;
goto exit;
}
else if(col4==0)
{
keyvalue=0x0f;
goto exit;
}
else
{
}
if(RCIF==1)
{
check();
}
}
exit:
while((col1==0)||(col2==0)||(col3==0)||(col4==0))
{
VIVA INSTITUTE OF TECHNOLOGY
Page 7-20
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
row1=0;
row2=0;
row3=0;
row4=0;
delay(50);
}
}
/////////////////////////////////////////////////////////////////////////////////////////////////////////////
void check()
{
if(OERR==1)
{
SREN=0;
temp=RCREG;
temp=RCREG;
CREN=0;
CREN=1;
SREN=1;
}
temp=RCREG;
if(temp=='1')
{
alarm=0;
command(0x01);
lcddisp(0x80," PASSPORT ");
lcddisp(0xC0," VERIFIED ");
}
else if(temp=='0')
{
alarm=1;
command(0x01);
lcddisp(0x80," FAKE PASSPORT ");
lcddisp(0xC0,"
");
}
else
{
}
delay(2000);
alarm=0;
command(0x01);
lcddisp(0x80,"ENTER NUMBER ");
command(0xc0);
}
//////////////////////////////////////////////////
VIVA INSTITUTE OF TECHNOLOGY
Page 7-21
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Chapter 8 Appendix B
VIVA INSTITUTE OF TECHNOLOGY
Page 8-22
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
DATASHEET OF PIC16F887 :
Block diagram :
VIVA INSTITUTE OF TECHNOLOGY
Page 8-23
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Pin description :
VIVA INSTITUTE OF TECHNOLOGY
Page 8-24
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
Program Memory Organization :
The PIC16F882/883/884/886/887 has a 13-bit program counter capable of addressing
a 2K x 14 (0000h-07FFh) for the PIC16F882, 4K x 14 (0000h-0FFFh) for the
PIC16F883/PIC16F884, and 8K x 14 (0000h-1FFFh) for the PIC16F886/PIC16F887
program memory space. Accessing a location above these boundaries will cause a
wraparound within the first 8K x 14 space. The Reset vector is at 0000h and the
interrupt vector is at 0004h
Data Memory Organization :
The data memory is partitioned into four banks which contain the General Purpose
Registers (GPR) and the Special Function Registers (SFR). The Special Function
Registers are located in the first 32 locations of each bank. The General Purpose
Registers, implemented as static RAM, are located in the last 96 locations of each
Bank. Register locations F0h-FFh in Bank 1, 170h-17Fh in Bank 2 and 1F0h-1FFh in
Bank 3, point to addresses
70h-7Fh in Bank 0. The actual number of General Purpose Resisters (GPR)
implemented in each Bank
depends on the device. All other RAM is unimplemented and returns 0 when read.
RP<1:0> of the STATUS
register are the bank select bits:
RP1 RP0
0 0 Bank 0 is selected
0 1 Bank 1 is selected
1 0 Bank 2 is selected
1 1 Bank 3 is selected
I/O PORTS :
There are as many as thirty-five general purpose I/O pins available. Depending on
which peripherals are enabled, some or all of the pins may not be available as general
purpose I/O. In general, when a peripheral is enabled, the associated pin may not be
used as a general purpose I/O pin.
VIVA INSTITUTE OF TECHNOLOGY
Page 8-25
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
PORTA and the TRISA Registers :
PORTA is a 8-bit wide, bidirectional port. The corresponding data direction register is
TRISA. Setting a TRISA bit (= 1) will make the corresponding PORTA pin an input
(i.e., disable the output driver). Clearing a TRISA bit (= 0) will make the
corresponding PORTA pin an output (i.e., enables output driver and puts the contents
of the output latch on the selected pin). Reading the PORTA register (Register 3-1)
reads the status of the pins, whereas writing to it will write to the PORT latch. All
write operations are read-modify-write operations. Therefore, a write to a port implies
that the port pins are read; this value is modified and then written to the PORT data
latchThe TRISA register controls the PORTA pin output drivers, even when they are
being used as analog inputs. The user should ensure the bits in the TRISA register are
maintained set when using them as Analog inputs. I/O pins configured as analog input
always read 0.
PORTB and TRISB Registers :
PORTB is an 8-bit wide, bidirectional port. The corresponding data direction register
is TRISB
Setting a TRISB bit (= 1) will make the corresponding PORTB pin an
input (i.e., put the corresponding output driver in a High-Impedance mode). Clearing
a TRISB bit (= 0) will make the corresponding PORTB pin an output (i.e., enable the
output driver and put the contents of the output latch on the selected pin). Reading the
PORTB register reads the status of the pins, whereas writing to it will write to the
PORT latch. All write operations are read-modify-write operations. Therefore, a write
to a port implies that the port pins are read, this value is modified and then written to
the PORT data latch. The TRISB register controls the PORTB pin output drivers,
even when they are being used as analog inputs. The user should ensure the bits in the
TRISB register are maintained set when using them as analog inputs. I/O pins
configured as analog input always read 0. Example 3-3 shows how to initialize
PORTB.
PORTC and TRISC Registers :
PORTC is a 8-bit wide, bidirectional port. The corresponding data direction register is
TRISC Setting a TRISC bit (= 1) will make the bcorresponding PORTC pin an input
(i.e., put the corresponding output driver in a High-Impedance mode). Clearing a
VIVA INSTITUTE OF TECHNOLOGY
Page 8-26
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
TRISC bit (= 0) will make the corresponding PORTC pin an output (i.e., enable the
output driver and n put the contents of the output latch on the selected pin). shows
how to initialize PORTC.Reading the PORTC register reads the status of the pins,
whereas writing to it will write to the PORT latch. All write operations are readmodify-write operations. Therefore, a write to a port implies that the port pins are
read, this value is modified and then written to the PORT data latch.
PORTD and TRISD Registers:
PORTD(1) is a 8-bit wide, bidirectional port. The corresponding data direction
register is TRISD
Setting a TRISD bit (= 1) will make the corresponding PORTD pin an input (i.e., put
the corresponding output driver in a High-Impedance mode). Clearing a TRISD bit (=
0) will make the corresponding PORTD pin an output (i.e., enable the output driver
and put the contents of the output latch on the selected pin). Example 3-5 shows how
to initialize PORTD. Reading the PORTD register reads the status of the pins,
whereas writing to it will write to the PORT latch. All write operations are readmodify-write operations. Therefore, a write to a port implies that the port pins are
read, this value is modified and then written to the PORT data latch.
PORTE and TRISE Registers :
PORTE(1) is a 4-bit wide, bidirectional port. The corresponding data direction register is
TRISE. Setting a
TRISE bit (= 1) will make the corresponding PORTE pin an input (i.e., put the corresponding
output driver in a High-Impedance mode). Clearing a TRISE bit (= 0) will make the
corresponding PORTE pin an output (i.e., enable the output driver and put the contents of the
output latch on the selected pin). The exception is RE3,
VIVA INSTITUTE OF TECHNOLOGY
Page 8-27
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
which is input only and its TRIS bit will always read as 1. Reading the PORTE register
reads the status of the pins, whereas writing to it will write to the PORT latch. All write
operations are read-modify-write
operations. Therefore, a write to a port implies that the port pins are read, this value is
modified and then written
to the PORT data latch. RE3 reads 0 when MCLRE = 1. The TRISE register controls the
PORTE pin output drivers, even when they are being used as analog inputs. The user should
ensure the bits in the TRISE register are maintained set when using them as analog inputs.
I/O pins configured as analog input always read 0.
OSCILLATOR MODULE (WITH FAIL-SAFE CLOCK MONITOR) :
The Oscillator module has a wide variety of clock sources and selection features that
allow it to be used in a wide range of applications while maximizing performance and
minimizing power consumption. Figure 4-1 illustrates a block diagram of the
Oscillator module. Clock sources can be configured from external oscillators, quartz
crystal resonators, ceramic resonators and Resistor-Capacitor (RC) circuits. In
addition, the system clock source can be configured from one of two internal
oscillators, with a choice of speeds selectable via software. Additional clock features
include:
Selectable system clock source between external or internal via software.
Two-Speed Start-up mode, which minimizes latency between external oscillator startup and code execution.
Fail-Safe Clock Monitor (FSCM) designed to detect a failure of the external clock
source (LP, XT, HS, EC or RC modes) and switch automatically to the internal
oscillator
The Oscillator module can be configured in one of eight clock modes.
1. EC External clock with I/O on OSC2/CLKOUT.
2. LP 32 kHz Low-Power Crystal mode.
3. XT Medium Gain Crystal or Ceramic Resonator Oscillator mode.
4. HS High Gain Crystal or Ceramic Resonator mode.
5. RC External Resistor-Capacitor (RC) with FOSC/4 output on OSC2/CLKOUT.
6. RCIO External Resistor-Capacitor (RC) with I/O on OSC2/CLKOUT.
VIVA INSTITUTE OF TECHNOLOGY
Page 8-28
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
7. INTOSC Internal oscillator with FOSC/4 output on OSC2 and I/O on
OSC1/CLKIN.
8. INTOSCIO Internal oscillator with I/O on OSC1/CLKIN and OSC2/CLKOUT.
Clock Source modes are configured by the FOSC<2:0> bits in the Configuration
Word Register 1 (CONFIG1).
The internal clock can be generated from two internal oscillators. The HFINTOSC is
a calibrated high-frequency oscillator. The LFINTOSC is an uncalibrated lowfrequency oscillator
Oscillator Control :
The Oscillator Control (OSCCON) register controls the system clock and
frequency selection options. The OSCCON register contains the following
bits:
Frequency selection bits (IRCF)
Frequency Status bits (HTS, LTS)
System clock control bits (OSTS, SCS)
VIVA INSTITUTE OF TECHNOLOGY
Page 8-29
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
TIMER0 MODULE :
The Timer0 module is an 8-bit timer/counter with the following features:
8-bit timer/counter register (TMR0)
8-bit prescaler (shared with Watchdog Timer)
Programmable internal or external clock source
Programmable external clock edge selection
Interrupt on overflow Figure 5-1 is a block diagram of the Timer0 module
Timer0 Operation
When used as a timer, the Timer0 module can be used as either an 8-bit timer or an 8bit counter
8-BIT TIMER MODE :
When used as a timer, the Timer0 module will increment every instruction
cycle (without prescaler). Timer mode is selected by clearing the T0CS bit of
the OPTION register to 0. When TMR0 is written, the increment is inhibited
for two instruction cycles immediately following the write.
8-BIT COUNTER MODE :
When used as a counter, the Timer0 module will increment on every rising or
falling edge of the T0CKI pin. The incrementing edge is determined by the
T0SE bit of the OPTION register. Counter mode is selected by setting the
T0CS bit of the OPTION register to 1.
TIMER1 MODULE WITH GATE CONTROL:
The Timer1 module is a 16-bit timer/counter with the following features:
16-bit timer/counter register pair (TMR1H:TMR1L)
Programmable internal or external clock source
VIVA INSTITUTE OF TECHNOLOGY
Page 8-30
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
3-bit prescaler
Optional LP oscillator
Synchronous or asynchronous operation
Timer1 gate (count enable) via comparator or T1G pin
Interrupt on overflow
Wake-up on overflow (external clock, Asynchronous mode only)
Time base for the Capture/Compare function
Special Event Trigger (with ECCP)
Comparator output synchronization to Timer1 clock
TIMER2 MODULE :
The Timer2 module is an eight-bit timer with the following features:
8-bit timer register (TMR2)
8-bit period register (PR2)
Interrupt on TMR2 match with PR2
Software programmable prescaler (1:1, 1:4, 1:16)
Software programmable postscaler (1:1 to 1:16)
Timer2 Operation:
The clock input to the Timer2 module is the system
instruction clock (FOSC/4). The clock is fed into the Timer2 prescaler, which has
prescale options of 1:1, 1:4 or 1:16. The output of the prescaler is then used to
increment the TMR2 register. The values of TMR2 and PR2 are constantly compared
to determine when they match. TMR2 will increment from 00h until it matches the
value in PR2. When a match occurs, two things happen:
TMR2 is reset to 00h on the next increment cycle
The Timer2 postscaler is incremented
The match output of the Timer2/PR2 comparator is then fed into the Timer2
postscaler. The postscaler has postscale options of 1:1 to 1:16 inclusive. The output of
the Timer2 postscaler is used to set the TMR2IF interrupt flag bit in the PIR1 register.
The TMR2 and PR2 registers are both fully readable and writable. On any Reset, the
TMR2 register is set to 00h and the PR2 register is set to FFh. Timer2 is turned on by
setting the TMR2ON bit in the T2CON register to a 1. Timer2 is turned off by
clearing the TMR2ON bit to a 0. The Timer2 prescaler is controlled by the T2CKPS
bits in the T2CON register. The Timer2 postscaler is controlled by the TOUTPS bits
in the T2CON register. The prescaler and postscaler counters are cleared when:
A write to TMR2 occurs.
A write to T2CON occurs.
Any device Reset occurs (Power-on Reset, MCLR Reset, Watchdog Timer Reset, or
Brown-out Reset).
VIVA INSTITUTE OF TECHNOLOGY
Page 8-31
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
COMPARATOR MODULE :
Comparators are used to interface analog circuits to a digital circuit by
comparing two analog voltages and providing a digital indication of their
relative magnitudes. The comparators are very useful mixed signal building
blocks because they provide analog functionality independent of the program
execution. The analog Comparator module includes the following features:
Independent comparator control
Programmable input selection
Comparator output is available internally/externally
Programmable output polarity
Interrupt-on-change
Wake-up from Sleep
PWM shutdown
Timer1 gate (count enable)
Output synchronization to Timer1 clock input
SR Latch
Programmable and fixed voltage reference
VIVA INSTITUTE OF TECHNOLOGY
Page 8-32
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
MAX232:
description/ordering information
The MAX232 is a dual driver/receiver that includes a capacitive voltage
generator to supply TIA/EIA-232-F
voltage levels from a single 5-V supply. Each receiver converts TIA/EIA-232F inputs to 5-V TTL/CMOS levels.
These receivers have a typical threshold of 1.3 V, a typical hysteresis of 0.5 V,
and can accept 30-V inputs.
Each driver converts TTL/CMOS input levels into TIA/EIA-232-F levels. The
driver, receiver, and
VIVA INSTITUTE OF TECHNOLOGY
Page 8-33
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
VIVA INSTITUTE OF TECHNOLOGY
Page 8-34
ZIGBEE REMINDER SYSTEM FOR MOBILE DATA TRANSFER IN AIRPORT
VIVA INSTITUTE OF TECHNOLOGY
Page 8-35
Das könnte Ihnen auch gefallen
- Types of WomanDokument16 SeitenTypes of Womanveerendra75% (4)
- Flashes of Light From The Spirit-Land - J ConantDokument397 SeitenFlashes of Light From The Spirit-Land - J ConantmcadaviesNoch keine Bewertungen
- Microcontroller Based Heartbeat Monitoring With Display LCDDokument90 SeitenMicrocontroller Based Heartbeat Monitoring With Display LCDRama Krishna M64% (14)
- Natural Law and The Theory of Society 1500 To 1800 (Scan Perso) PDFDokument508 SeitenNatural Law and The Theory of Society 1500 To 1800 (Scan Perso) PDFjcfichte100% (1)
- Seismic Earth Pressures On Retaining WallsDokument71 SeitenSeismic Earth Pressures On Retaining Wallsradespino1Noch keine Bewertungen
- Psych ManualDokument340 SeitenPsych ManualMarius_20100% (1)
- Seminar WorkshopDokument3 SeitenSeminar Workshopsir_mhickoNoch keine Bewertungen
- Zerkle Dalcroze Workshop HandoutDokument2 SeitenZerkle Dalcroze Workshop HandoutEricDoCarmoNoch keine Bewertungen
- O.E.Lab - Docx For Direct Shear TestDokument14 SeitenO.E.Lab - Docx For Direct Shear TestAmirah SyakiraNoch keine Bewertungen
- Johnson, David W - Johnson, Frank P - Joining Together - Group Theory and Group Skills (2013)Dokument643 SeitenJohnson, David W - Johnson, Frank P - Joining Together - Group Theory and Group Skills (2013)Farah Ridzky Ananda88% (8)
- Remote Monitoring and Control System For DC Motor Using Zigbee ProtocolDokument7 SeitenRemote Monitoring and Control System For DC Motor Using Zigbee ProtocolInternational Journal of Application or Innovation in Engineering & ManagementNoch keine Bewertungen
- A Smart Zigbee Based Wireless Weather Station Monitoring SystemDokument6 SeitenA Smart Zigbee Based Wireless Weather Station Monitoring SystemHachem ElyousfiNoch keine Bewertungen
- Zigbee: Presented byDokument9 SeitenZigbee: Presented bySwathi YennamNoch keine Bewertungen
- ZigbeeDokument9 SeitenZigbeelikithavonamalaNoch keine Bewertungen
- Zigbee TechnologyDokument9 SeitenZigbee Technologyarjun royalNoch keine Bewertungen
- Advanced Telecommunication Networks (Assignment-Bluetooth)Dokument7 SeitenAdvanced Telecommunication Networks (Assignment-Bluetooth)black widowNoch keine Bewertungen
- Zigbee Transmitter For Iot Wireless DevicesDokument13 SeitenZigbee Transmitter For Iot Wireless DevicesAnonymous e4UpOQEPNoch keine Bewertungen
- SECC - Design and Implementation of ZigBee Based Infrastructure For Smart EnvironmentsDokument26 SeitenSECC - Design and Implementation of ZigBee Based Infrastructure For Smart EnvironmentsDavidleonardo GalindoNoch keine Bewertungen
- Users Make A Beeline For Zigbee Sensor Technology: Industry TrendsDokument4 SeitenUsers Make A Beeline For Zigbee Sensor Technology: Industry TrendsdabrevipulNoch keine Bewertungen
- Zigbee Protocol: A Seminar Report OnDokument31 SeitenZigbee Protocol: A Seminar Report OnKranthi ReddyNoch keine Bewertungen
- Zigbee: Origin of WordDokument9 SeitenZigbee: Origin of WordRajan VermaNoch keine Bewertungen
- Design and Construction of Microcontroller Based Wireless Remote Controlled Industrial Electrical Appliances Using ZigBee TechnologyDokument6 SeitenDesign and Construction of Microcontroller Based Wireless Remote Controlled Industrial Electrical Appliances Using ZigBee TechnologyijsretNoch keine Bewertungen
- Design and Implementation of A Zigbee-Based Wireless Automatic Meter Reading SystemDokument5 SeitenDesign and Implementation of A Zigbee-Based Wireless Automatic Meter Reading SystemPatricio Rojas CarrascoNoch keine Bewertungen
- Technical Overview: Wireless Mesh NetworkDokument13 SeitenTechnical Overview: Wireless Mesh NetworkNaveen Telugudesam0% (1)
- Project Overview: PC by The Help of Visual Basic We Monitor The Parameters in The SystemDokument4 SeitenProject Overview: PC by The Help of Visual Basic We Monitor The Parameters in The SystemMohammed ShadabNoch keine Bewertungen
- Gas Management & Disaster System Using ZigBeeDokument6 SeitenGas Management & Disaster System Using ZigBeesalmanrashid79Noch keine Bewertungen
- Zigbee TutorialDokument9 SeitenZigbee TutorialrahulNoch keine Bewertungen
- ProjectDokument22 SeitenProjectShriresh PillaiNoch keine Bewertungen
- Zigbee Wireless Control That Simply WorksDokument11 SeitenZigbee Wireless Control That Simply WorksTb ShilpaNoch keine Bewertungen
- Technical Overview: Zigbee Is ADokument12 SeitenTechnical Overview: Zigbee Is AyouaredeadNoch keine Bewertungen
- Introduction To Zigbee TechnologyDokument24 SeitenIntroduction To Zigbee Technologyveere_arunNoch keine Bewertungen
- Zigbee Literature ReviewDokument22 SeitenZigbee Literature ReviewBhaskar Rao PNoch keine Bewertungen
- Design of A Wireless Medical Monitoring System: Computer and Management (CAMAN), 2011 International Conference OnDokument8 SeitenDesign of A Wireless Medical Monitoring System: Computer and Management (CAMAN), 2011 International Conference Onbopparajuswathi_8787Noch keine Bewertungen
- Zigbee: Zigbee Is An Ieee 802.15.4-Based Specification For A Suite of High-Level CommunicationDokument6 SeitenZigbee: Zigbee Is An Ieee 802.15.4-Based Specification For A Suite of High-Level CommunicationsweetsureshNoch keine Bewertungen
- Working With Zigbee ModuleDokument10 SeitenWorking With Zigbee ModuleShabaz MondalNoch keine Bewertungen
- Manually Controlled Surveillance System Using Zigbee CommunicationDokument7 SeitenManually Controlled Surveillance System Using Zigbee CommunicationInternational Journal of Application or Innovation in Engineering & ManagementNoch keine Bewertungen
- International Journal of Engineering Research and Development (IJERD)Dokument5 SeitenInternational Journal of Engineering Research and Development (IJERD)IJERDNoch keine Bewertungen
- Synopsis: Wireless Device Controlling With ZigbeeDokument6 SeitenSynopsis: Wireless Device Controlling With ZigbeeJaiparkash SaveliaNoch keine Bewertungen
- 1 Coin: Zigbee Is ADokument17 Seiten1 Coin: Zigbee Is AShrikant JagtapNoch keine Bewertungen
- Seminar ReportDokument21 SeitenSeminar ReportKunjesh MehtaNoch keine Bewertungen
- 19rj1a05l7 ZigbeetechnologydocumentationDokument21 Seiten19rj1a05l7 ZigbeetechnologydocumentationSuddapalli NeelimaNoch keine Bewertungen
- Zigbee Technology IJERTCONV3IS10001Dokument4 SeitenZigbee Technology IJERTCONV3IS10001bhuvaneshv274Noch keine Bewertungen
- Wireless Automation Using Zigbee Technology: Presentation-IDokument14 SeitenWireless Automation Using Zigbee Technology: Presentation-IVijay EmmanuelNoch keine Bewertungen
- Examples of Flow ChartDokument17 SeitenExamples of Flow ChartLello Flo0% (1)
- ST ST: My Registration Code Is CS02103 "It's An Interesting Paradox: Open Standards Versus High Security"Dokument14 SeitenST ST: My Registration Code Is CS02103 "It's An Interesting Paradox: Open Standards Versus High Security"Arun ChowdaryNoch keine Bewertungen
- Design and Simulation of State-Of-Art Zigbee Transmitter For Iot Wireless DevicesDokument4 SeitenDesign and Simulation of State-Of-Art Zigbee Transmitter For Iot Wireless DevicesEdgar A.BNoch keine Bewertungen
- O) Ok/Mr KXN .O'Ovyzwox Yp Ro WDSQ, Oox Ry/ Kxqo As/Ovo) ) - Yww - XSMK Syx KXNK/NDokument5 SeitenO) Ok/Mr KXN .O'Ovyzwox Yp Ro WDSQ, Oox Ry/ Kxqo As/Ovo) ) - Yww - XSMK Syx KXNK/Nknight_flycnNoch keine Bewertungen
- A Smart ZIGBEE Based Wireless Sensor Meter System: Christos Tatsiopoulos Aphrodite KtenaDokument4 SeitenA Smart ZIGBEE Based Wireless Sensor Meter System: Christos Tatsiopoulos Aphrodite KtenaShobhit JainNoch keine Bewertungen
- Seminar Report On ZigbeeDokument17 SeitenSeminar Report On ZigbeeMansoor ChowdhuryNoch keine Bewertungen
- Zigbee Technology Seminar PresentationDokument10 SeitenZigbee Technology Seminar PresentationmithNoch keine Bewertungen
- 1 s2.0 S2212671614000808 MainDokument7 Seiten1 s2.0 S2212671614000808 MainZoro ZoroNoch keine Bewertungen
- The Networking Technology Within Smart Home System - Zigbee TechnologyDokument5 SeitenThe Networking Technology Within Smart Home System - Zigbee Technologyhyj890417Noch keine Bewertungen
- Embedded Wireless ProjectsDokument3 SeitenEmbedded Wireless Projectspraveen_kodgirwarNoch keine Bewertungen
- Zigbee Technology FinalDokument14 SeitenZigbee Technology Finalduduck1000Noch keine Bewertungen
- Wireless Control and Monitoring Using Programmable Logic Controller (PLC)Dokument5 SeitenWireless Control and Monitoring Using Programmable Logic Controller (PLC)Vinod KumbharNoch keine Bewertungen
- ZigbeeDokument6 SeitenZigbeeRavikumar GoliNoch keine Bewertungen
- ZigbeeDokument38 SeitenZigbeePrabhat SharmaNoch keine Bewertungen
- Wireless Communication ZigbeeDokument11 SeitenWireless Communication ZigbeeChirag MistryNoch keine Bewertungen
- Multi-Stage Real Time Health Monitoring Via Zigbee in Smart HomesDokument7 SeitenMulti-Stage Real Time Health Monitoring Via Zigbee in Smart HomesPhoyagerNoch keine Bewertungen
- Fundamentals of IoTDokument24 SeitenFundamentals of IoTRohit SaindaneNoch keine Bewertungen
- Seminar ReportDokument22 SeitenSeminar ReportArchana BrahmaNoch keine Bewertungen
- Report 1Dokument8 SeitenReport 1Swapnil BangarNoch keine Bewertungen
- Zigbee TechnologyDokument20 SeitenZigbee TechnologyVigneshInfotechNoch keine Bewertungen
- Zigbee Based Wireless Motor Control - Part 1Dokument10 SeitenZigbee Based Wireless Motor Control - Part 1harrisrajNoch keine Bewertungen
- The Mobile Video Surveillance System Based On Wireless LAN: Chunhua Wang Zheng Mao Yu Zhang Hailong LuoDokument7 SeitenThe Mobile Video Surveillance System Based On Wireless LAN: Chunhua Wang Zheng Mao Yu Zhang Hailong LuoWERMERMNoch keine Bewertungen
- Smart Electrical Lighting NewDokument8 SeitenSmart Electrical Lighting NewgebruNoch keine Bewertungen
- Building the Internet of Things with IPv6 and MIPv6: The Evolving World of M2M CommunicationsVon EverandBuilding the Internet of Things with IPv6 and MIPv6: The Evolving World of M2M CommunicationsNoch keine Bewertungen
- Software Based Project 2018Dokument13 SeitenSoftware Based Project 2018देवेश सिंह राजपूतNoch keine Bewertungen
- Touch Panel Based Modern Restaurants Atomization Using Zigbee TechnologyDokument4 SeitenTouch Panel Based Modern Restaurants Atomization Using Zigbee Technologyदेवेश सिंह राजपूतNoch keine Bewertungen
- PCB Design Design and Fabrication of Printed Circuit BoardsDokument2 SeitenPCB Design Design and Fabrication of Printed Circuit Boardsदेवेश सिंह राजपूतNoch keine Bewertungen
- Touch Screen Based Device ControllingDokument5 SeitenTouch Screen Based Device Controllingदेवेश सिंह राजपूतNoch keine Bewertungen
- An Electronic Voting System Through Touch Screen InterfaceDokument3 SeitenAn Electronic Voting System Through Touch Screen Interfaceदेवेश सिंह राजपूतNoch keine Bewertungen
- Solar Operated Grass CutterDokument3 SeitenSolar Operated Grass Cutterदेवेश सिंह राजपूतNoch keine Bewertungen
- RFID Based Security SystemDokument2 SeitenRFID Based Security Systemदेवेश सिंह राजपूतNoch keine Bewertungen
- Accident Identification and Alerting ProjectDokument3 SeitenAccident Identification and Alerting Projectदेवेश सिंह राजपूतNoch keine Bewertungen
- 3 Weather ReportingDokument5 Seiten3 Weather Reportingदेवेश सिंह राजपूतNoch keine Bewertungen
- KeywordsDokument7 SeitenKeywordsदेवेश सिंह राजपूतNoch keine Bewertungen
- Aim and ObjectivesDokument1 SeiteAim and Objectivesदेवेश सिंह राजपूतNoch keine Bewertungen
- Li Fi Block DiagramDokument2 SeitenLi Fi Block Diagramदेवेश सिंह राजपूतNoch keine Bewertungen
- Final Report Li-FiDokument13 SeitenFinal Report Li-Fiदेवेश सिंह राजपूतNoch keine Bewertungen
- Transformer Designing.Dokument3 SeitenTransformer Designing.देवेश सिंह राजपूतNoch keine Bewertungen
- Advanced Rectangle Pneumatic Wire Forming MachineDokument3 SeitenAdvanced Rectangle Pneumatic Wire Forming Machineदेवेश सिंह राजपूतNoch keine Bewertungen
- War FieldDokument2 SeitenWar Fieldदेवेश सिंह राजपूतNoch keine Bewertungen
- Automatic Pneumatic Multi Purpose PressDokument3 SeitenAutomatic Pneumatic Multi Purpose Pressदेवेश सिंह राजपूतNoch keine Bewertungen
- Fabrication of Pneumatic Footstep Lifting SystemDokument3 SeitenFabrication of Pneumatic Footstep Lifting Systemदेवेश सिंह राजपूतNoch keine Bewertungen
- Design and Fabrication of Tricycle For Physically Challenged and Elder PeopleDokument6 SeitenDesign and Fabrication of Tricycle For Physically Challenged and Elder Peopleदेवेश सिंह राजपूतNoch keine Bewertungen
- Automatic Pneumatic Multi Purpose PressDokument3 SeitenAutomatic Pneumatic Multi Purpose Pressदेवेश सिंह राजपूतNoch keine Bewertungen
- Black BookDokument21 SeitenBlack Bookदेवेश सिंह राजपूतNoch keine Bewertungen
- Angular Pneumatic HacksawDokument2 SeitenAngular Pneumatic Hacksawदेवेश सिंह राजपूतNoch keine Bewertungen
- Automated Braking SystemDokument13 SeitenAutomated Braking Systemदेवेश सिंह राजपूतNoch keine Bewertungen
- Bluetooth Operated Robot Using Android MobileDokument4 SeitenBluetooth Operated Robot Using Android Mobileदेवेश सिंह राजपूतNoch keine Bewertungen
- Greenhouse Environment Controlling With Monitoring On Android Mobile ApplicationDokument3 SeitenGreenhouse Environment Controlling With Monitoring On Android Mobile Applicationदेवेश सिंह राजपूतNoch keine Bewertungen
- Energy MeterDokument45 SeitenEnergy Meterदेवेश सिंह राजपूतNoch keine Bewertungen
- Power Supplay UnittDokument1 SeitePower Supplay Unittदेवेश सिंह राजपूतNoch keine Bewertungen
- SynopsisCOMPARISON OF EXPERIMENTAL AND ANALYTICAL STUDY FOR VIBRATION CHARACTERISTICS OF MR CANTILEVER BEAMDokument9 SeitenSynopsisCOMPARISON OF EXPERIMENTAL AND ANALYTICAL STUDY FOR VIBRATION CHARACTERISTICS OF MR CANTILEVER BEAMदेवेश सिंह राजपूतNoch keine Bewertungen
- English 4 Realistic FictionDokument5 SeitenEnglish 4 Realistic FictionRose Marie RebutaNoch keine Bewertungen
- استخدام الشبكة الإدارية في السلوك القيادي بحث محكمDokument22 Seitenاستخدام الشبكة الإدارية في السلوك القيادي بحث محكمsalm yasmenNoch keine Bewertungen
- Operating Temperature Considerations and Performance PDFDokument12 SeitenOperating Temperature Considerations and Performance PDFccprado1Noch keine Bewertungen
- Expanding UNIT 1 For 2º ESO.-the History of Music NotationDokument1 SeiteExpanding UNIT 1 For 2º ESO.-the History of Music NotationEwerton CândidoNoch keine Bewertungen
- SAHCorporateBrochure WEBDokument72 SeitenSAHCorporateBrochure WEBKrsna SinghNoch keine Bewertungen
- PreliminaryDokument65 SeitenPreliminarysame.pxtNoch keine Bewertungen
- 9-12 Lesson PlanDokument3 Seiten9-12 Lesson Planapi-364700795Noch keine Bewertungen
- Design of Power Converters For Renewable Energy Sources and Electric Vehicles ChargingDokument6 SeitenDesign of Power Converters For Renewable Energy Sources and Electric Vehicles ChargingRay Aavanged IINoch keine Bewertungen
- CP100 Module 2 - Getting Started With Google Cloud PlatformDokument33 SeitenCP100 Module 2 - Getting Started With Google Cloud PlatformManjunath BheemappaNoch keine Bewertungen
- Performance Management System: Business Essentials Business Accelerators Business ValuesDokument10 SeitenPerformance Management System: Business Essentials Business Accelerators Business ValuesVishwa Mohan PandeyNoch keine Bewertungen
- TOS Physical ScienceDokument1 SeiteTOS Physical ScienceSuzette De Leon0% (1)
- Windows Steady State HandbookDokument81 SeitenWindows Steady State HandbookcapellaNoch keine Bewertungen
- Tables Log ActivatedDokument575 SeitenTables Log ActivateddcdiasNoch keine Bewertungen
- Skripsi Tanpa Bab Pembahasan PDFDokument67 SeitenSkripsi Tanpa Bab Pembahasan PDFaaaaNoch keine Bewertungen
- Vmod Pht3d TutorialDokument32 SeitenVmod Pht3d TutorialluisgeologoNoch keine Bewertungen
- Waqas Ahmed C.VDokument2 SeitenWaqas Ahmed C.VWAQAS AHMEDNoch keine Bewertungen
- Android TV Media Player User ManualDokument17 SeitenAndroid TV Media Player User ManualAneez Ahmed NNoch keine Bewertungen
- Making Things: The Essence and Evolution of The Toyota Production SystemDokument2 SeitenMaking Things: The Essence and Evolution of The Toyota Production Systemkt44974085Noch keine Bewertungen
- Upper Int U2 OnlineReviewsAndRecommendations PDFDokument2 SeitenUpper Int U2 OnlineReviewsAndRecommendations PDFZsuzsa StefánNoch keine Bewertungen
- Water TableDokument5 SeitenWater TableJay DoshiNoch keine Bewertungen
- Youtube Poop: Subverting Art OnlineDokument14 SeitenYoutube Poop: Subverting Art OnlineWill KurlinkusNoch keine Bewertungen