Beruflich Dokumente
Kultur Dokumente
Ucon
Hochgeladen von
rathoremssssssOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Ucon
Hochgeladen von
rathoremssssssCopyright:
Verfügbare Formate
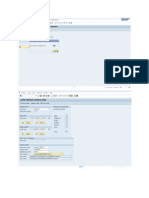
On the basis of specially prepared RFC statistics records, an administrator decides which remote-enabled
function modules (RFMs) are to be exposed to the outside and assigns them to a Default Communication
Assembly that is provided by the framework together with the default configuration and default host. Only
these RFMs in thedefault CA are then able to be reached from the outside, outside access is blocked for
all the other RFMs: They can no longer be accessed from outside the system but can still be called for
system-internal scenarios such asload balancing and asynchronous scenarios.
NoteAlongside the RFC Basic scenario, you can use the Role Builder scenario to determine which
RFC authorizations are required and create appropriate user roles.
Process
Logging Phase
To achieve this protection, you must first find out which RFMs must be reachable from the
outside in the affected system.
For this you persist the RFC calls with the UCON Framework in the relevant server system
using a freely-definable time period in the logging phase. This happens without affecting
performance by the framework saving the intended part of the statistics records collected
by the system.
After the selected time period has expired, it is possible to assign all RFMs called from the
outside to the default CA or to assign all RFMs that are to be exposed by default CA
individually. However, it is possible to assign additional RFMs to the default CA or to
remove an assignment.
Evaluation Phase
After the logging phase has expired, an evaluation or simulation phase follows. The
duration of this phase can be selected individually. Here you can check without risks if
you need to expose more RFMs for the business scenarios running in the system than
those that are already in the default CA.
In this evaluation phase there are no consequences if calling an RFM does not pass the
runtime checks of Unified Connectivity. In this way you can find out which RFMs you still
need to assign to the default CA without an RFM with errors possibly blocking productive
scenarios.
Productive Phase
If the security that all required RFMs are in the default CA exists after the logging and
evaluation phase, the UCON runtime checks can be activated in a third phase
(final or productive phase). The protection of the RFC server security scenarios exists
from this point: Only the RFMs in the default CA are still reachable from the outside at
runtime. If an RFM (that is not in the default CA) is called from the outside, a runtime
error is created with corresponding error message and error logging in the system log.
Role Builder Scenario: Process
Analyze the required RFC notifications and create the relevant user roles.
Process
Firstly, all function modules are selected on the basis of specific criteria (for example,
destination used, client to be run, users to be run on the server side).
In the next step you can assign function modules with the same authorization
requirements to different Communication Assemblies (CAs) that you have created for this
purpose.
The assignment to a CA takes place on the basis of the attributes selected above.
You can then create an ABAP user role that contains the corresponding authorization
object SRFC for each CA using transaction PFCG.
Example
You have created a MyDEST destination and have defined a user for external RFC
communication in this destination.
After activating the UCON loggings you can analyze the collected data by selecting all of the
function modules that were called using the MyDest destination and assign them to a
corresponding CA.
Using transaction PFCG you then create a user role with authorization object SRFC where the
authorization is only granted for the list of selected function modules.
If you then assign this role to the user defined in the destination, an external client can only
call those function modules that are defined in the list.
UCON CCMS Monitoring: Functions
Detailed information for monitoring UCON processes in the CCMS Monitor (transaction
RZ20).
In the following section you find a detailed description of the functions of the UCON CCMS
Monitoring that are available in the central CCMS Monitor (transaction RZ20). The individual
monitoring functions are shown in the following navigation nodes:
Prerequisites
Worklist for UCON Phase Tool
Transport Status of Phase Assignments
Status of Runtime and Design Time
Status of Batch Jobs
Das könnte Ihnen auch gefallen
- MMMMMMMMMMMMM: RRRRRR RR RRR R RRRDokument62 SeitenMMMMMMMMMMMMM: RRRRRR RR RRR R RRRrathoremssssss100% (1)
- DiskDokument1 SeiteDiskrathoremssssssNoch keine Bewertungen
- SAP HANA Administration TrainingDokument3 SeitenSAP HANA Administration TrainingrathoremssssssNoch keine Bewertungen
- Technical Monitoring SOLMANDokument29 SeitenTechnical Monitoring SOLMANrathoremssssssNoch keine Bewertungen
- Deepan Jain Sap BasisDokument3 SeitenDeepan Jain Sap BasisrathoremssssssNoch keine Bewertungen
- PassportApplicationForm Main English V1.0Dokument2 SeitenPassportApplicationForm Main English V1.0Triloki KumarNoch keine Bewertungen
- Parameter Check 112 ResultDokument29 SeitenParameter Check 112 ResultrathoremssssssNoch keine Bewertungen
- SAP Solution Manager ServiceDesk SetupDokument57 SeitenSAP Solution Manager ServiceDesk Setupchiruyours100% (2)
- CPPDokument1 SeiteCPPrathoremssssssNoch keine Bewertungen
- The List of Sap Icons 94175Dokument30 SeitenThe List of Sap Icons 94175rathoremssssssNoch keine Bewertungen
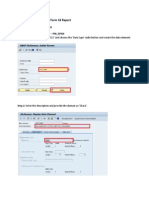
- Manual Instruction For FoTESrm 16 ReportDokument10 SeitenManual Instruction For FoTESrm 16 ReportrathoremssssssNoch keine Bewertungen
- CPPDokument1 SeiteCPPrathoremssssssNoch keine Bewertungen
- Near Mall Road,: House No 6, Subhash Colony, Near Lata Cinema, Jhotwara, Jaipur 302012 Jaipur Tel: 6545122Dokument2 SeitenNear Mall Road,: House No 6, Subhash Colony, Near Lata Cinema, Jhotwara, Jaipur 302012 Jaipur Tel: 6545122rathoremssssssNoch keine Bewertungen
- ServerDokument1 SeiteServerrathoremssssssNoch keine Bewertungen
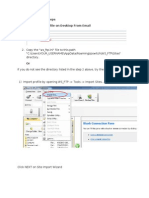
- WS - FTP - Ini Update Steps 1. Save Ws - FTP - Ini File On Desktop From EmailDokument4 SeitenWS - FTP - Ini Update Steps 1. Save Ws - FTP - Ini File On Desktop From EmailrathoremssssssNoch keine Bewertungen
- VersionDokument1 SeiteVersionrathoremssssssNoch keine Bewertungen
- Defaulttrace 1.trc - Part2Dokument1.255 SeitenDefaulttrace 1.trc - Part2rathoremssssssNoch keine Bewertungen
- DpmonDokument3 SeitenDpmonrathoremssssssNoch keine Bewertungen
- Si 1Dokument1 SeiteSi 1rathoremssssssNoch keine Bewertungen
- ChownDokument2 SeitenChownrathoremssssssNoch keine Bewertungen
- ChownDokument2 SeitenChownrathoremssssssNoch keine Bewertungen
- VersionDokument1 SeiteVersionrathoremssssssNoch keine Bewertungen
- Shoe Dog: A Memoir by the Creator of NikeVon EverandShoe Dog: A Memoir by the Creator of NikeBewertung: 4.5 von 5 Sternen4.5/5 (537)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeVon EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeBewertung: 4 von 5 Sternen4/5 (5794)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceVon EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceBewertung: 4 von 5 Sternen4/5 (890)
- The Yellow House: A Memoir (2019 National Book Award Winner)Von EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Bewertung: 4 von 5 Sternen4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingVon EverandThe Little Book of Hygge: Danish Secrets to Happy LivingBewertung: 3.5 von 5 Sternen3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryVon EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryBewertung: 3.5 von 5 Sternen3.5/5 (231)
- Never Split the Difference: Negotiating As If Your Life Depended On ItVon EverandNever Split the Difference: Negotiating As If Your Life Depended On ItBewertung: 4.5 von 5 Sternen4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureVon EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureBewertung: 4.5 von 5 Sternen4.5/5 (474)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersVon EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersBewertung: 4.5 von 5 Sternen4.5/5 (344)
- Grit: The Power of Passion and PerseveranceVon EverandGrit: The Power of Passion and PerseveranceBewertung: 4 von 5 Sternen4/5 (587)
- On Fire: The (Burning) Case for a Green New DealVon EverandOn Fire: The (Burning) Case for a Green New DealBewertung: 4 von 5 Sternen4/5 (73)
- The Emperor of All Maladies: A Biography of CancerVon EverandThe Emperor of All Maladies: A Biography of CancerBewertung: 4.5 von 5 Sternen4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaVon EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaBewertung: 4.5 von 5 Sternen4.5/5 (265)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreVon EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreBewertung: 4 von 5 Sternen4/5 (1090)
- Team of Rivals: The Political Genius of Abraham LincolnVon EverandTeam of Rivals: The Political Genius of Abraham LincolnBewertung: 4.5 von 5 Sternen4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyVon EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyBewertung: 3.5 von 5 Sternen3.5/5 (2219)
- The Unwinding: An Inner History of the New AmericaVon EverandThe Unwinding: An Inner History of the New AmericaBewertung: 4 von 5 Sternen4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Von EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Bewertung: 4.5 von 5 Sternen4.5/5 (119)
- Her Body and Other Parties: StoriesVon EverandHer Body and Other Parties: StoriesBewertung: 4 von 5 Sternen4/5 (821)
- G6 - (DS G6) Universal GatewayDokument2 SeitenG6 - (DS G6) Universal GatewayengrqazijanNoch keine Bewertungen
- Oracle MetricsDokument31 SeitenOracle MetricseramitsarohaNoch keine Bewertungen
- Medical Store Billing System Project ReportDokument31 SeitenMedical Store Billing System Project ReportLokendra SahuNoch keine Bewertungen
- DBMS Project Report - $#$&Dokument22 SeitenDBMS Project Report - $#$&Rati Shankar100% (1)
- Manual: Communication ProtocolsDokument41 SeitenManual: Communication ProtocolsmNoch keine Bewertungen
- Zero Trust Reference ArchitectureDokument104 SeitenZero Trust Reference ArchitectureMarcelo JuniorNoch keine Bewertungen
- VT6212LDokument26 SeitenVT6212LkaraislimNoch keine Bewertungen
- GEN 107 Hyperterminal COM SetupDokument4 SeitenGEN 107 Hyperterminal COM SetupRobinson SanchezNoch keine Bewertungen
- Corious - Visual Studio .NET-The .NET Framework Black BookDokument642 SeitenCorious - Visual Studio .NET-The .NET Framework Black Bookghay3Noch keine Bewertungen
- Bba CaDokument68 SeitenBba CaAkshay AmbarteNoch keine Bewertungen
- Requirement Traceability Matrix - Recherche GoogleDokument4 SeitenRequirement Traceability Matrix - Recherche GoogletraoreNoch keine Bewertungen
- BH US 12 Serna Leak Era SlidesDokument45 SeitenBH US 12 Serna Leak Era SlidesGianluca BoccacciNoch keine Bewertungen
- MXE 4G 6000 VA Inbuit BatteryDokument4 SeitenMXE 4G 6000 VA Inbuit BatteryLeonardo RamosNoch keine Bewertungen
- Solcon RVS-AXO ManualDokument38 SeitenSolcon RVS-AXO ManualCESAR AUGUSTO ORTIZ ALVAREZNoch keine Bewertungen
- Voxengo MSED User Guide enDokument6 SeitenVoxengo MSED User Guide enJose Luis DorronsoroNoch keine Bewertungen
- 535 Installation Manual Moore Industries PDFDokument144 Seiten535 Installation Manual Moore Industries PDFAnonymous AsIbqUNoch keine Bewertungen
- Process Automation (Anewcerefresher) A 14-Part SeriesDokument96 SeitenProcess Automation (Anewcerefresher) A 14-Part SeriesJared TapiaNoch keine Bewertungen
- Wifi - BVDK - Agg Project ReportDokument19 SeitenWifi - BVDK - Agg Project ReportDũng HuỳnhNoch keine Bewertungen
- (Req-3) 1180-5013 Technical Manual Peru r3Dokument9 Seiten(Req-3) 1180-5013 Technical Manual Peru r3José DelgadoNoch keine Bewertungen
- VTSP 5.5 Questions and AnswersDokument6 SeitenVTSP 5.5 Questions and AnswersThomasNoch keine Bewertungen
- 23-70-08 R3 CVFDR Installation ManualDokument251 Seiten23-70-08 R3 CVFDR Installation ManualSylfia Hellena100% (3)
- PG17 User Manual 20220923Dokument58 SeitenPG17 User Manual 20220923pedro100% (1)
- As440 Automatic VoltageDokument2 SeitenAs440 Automatic VoltageSergio SaldañaNoch keine Bewertungen
- Openbts SWDokument37 SeitenOpenbts SWrampravesh kumarNoch keine Bewertungen
- NDI SDK DocumentationDokument49 SeitenNDI SDK DocumentationElon Farias100% (1)
- Practical 10Dokument10 SeitenPractical 10jenni kokoNoch keine Bewertungen
- Hospital Management System ProjectDokument150 SeitenHospital Management System ProjectmohdghalbNoch keine Bewertungen
- Release NoteDokument20 SeitenRelease Notedangcongtru100% (1)
- ch1 - Basics of Graphics (CGR)Dokument15 Seitench1 - Basics of Graphics (CGR)Ravindra NawaleNoch keine Bewertungen
- Vut Pqec ItDokument4.185 SeitenVut Pqec ItSHARAN SASINoch keine Bewertungen