Beruflich Dokumente
Kultur Dokumente
2015 Nss Breach Detection System Test Report Check Point
Hochgeladen von
mbaezasotoCopyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
2015 Nss Breach Detection System Test Report Check Point
Hochgeladen von
mbaezasotoCopyright:
Verfügbare Formate
BREACH DETECTION SYSTEM TEST REPORT
Check Point 13500 Next Generation Threat Prevention
Appliance with Threat Emulation Cloud Service R77.20
Authors Dipti Ghimire, Bhaarath Venkateswaran, Ahmed Garhy, Mohamed Saher
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Overview
NSS Labs performed an independent test of the Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service R77.20. The product was subjected to thorough testing at the NSS facility in
Austin, Texas, based on the Breach Detection System (BDS) Methodology v2.0 available at www.nsslabs.com. This
test was conducted free of charge and NSS did not receive any compensation in return for participation.
While the companion comparative reports on security, performance, and total cost of ownership (TCO) will
provide information about all tested products, this individual test report provides detailed information not
available elsewhere.
As part of the initial BDS test setup, devices are tuned as deemed necessary by the vendor. Every effort is made to
ensure the optimal combination of Security Effectiveness and performance, as would be the aim of a typical
customer deploying the device in a live network environment. Figure 1 presents the overall results of the tests.
Product
Check Point 13500 Next Generation Threat Prevention Appliance with
Threat Emulation Cloud Service R77.20
Detection
Rate1
NSS-Tested
Throughput
97.2%
1,000 Mbps
HTTP Malware
Email Malware
SMB Malware
Drive-by Exploits
Social Exploits
Evasions
100.0%
100.0%
100.0%
100.0%
88.9%
94.2%
Figure 1 Overall Test Results
The Check Point 13500 Next Generation Threat Prevention Appliance with Threat Emulation Cloud Service R77.20
received an overall detection rating of 97.2%. The 13500 Next Generation Threat Prevention Appliance with Threat
Emulation Cloud Service detected 94.2% of the evasions techniques tested. The solution also passed all stability
and reliability tests.
The solution was tested and rated by NSS at 1,000 Mbps. NSS-Tested Throughput is calculated as an average of the
real-world protocol mixes (Enterprise Perimeter and Education), and the 21 KB HTTP response-based tests.
Detection rate is defined as the average percentage of malware and exploits detected under test.
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Table of Contents
Overview............................................................................................................................... 2
Security Effectiveness ............................................................................................................ 5
Exploit and Malware Detection .....................................................................................................................................6
Resistance to Evasion Techniques .................................................................................................................................7
Network Device Performance ................................................................................................ 8
Raw Packet Processing Performance (UDP Traffic) .......................................................................................................8
Maximum Capacity ........................................................................................................................................................9
HTTP Capacity with No Transaction Delays .................................................................................................................11
HTTP Capacity with Transaction Delays .......................................................................................................................12
Real-World Traffic Mixes ..........................................................................................................................................13
Stability and Reliability ........................................................................................................ 14
Management and Configuration .......................................................................................... 15
Total Cost of Ownership (TCO) ............................................................................................. 15
Calculating the Total Cost of Ownership (TCO) ...........................................................................................................16
Installation Time ..........................................................................................................................................................16
Purchase Price And Total Cost Of Ownership ..............................................................................................................17
Value: Total Cost of Ownership per Protected Mbps ..................................................................................................18
Appendix: Product Scorecard ............................................................................................... 19
Test Methodology ............................................................................................................... 21
Contact Information ............................................................................................................ 21
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Table of Figures
Figure 1 Overall Test Results.......................................................................................................................................2
Figure 2 Exploit and Malware Detection Rates ...........................................................................................................6
Figure 3 Resistance to Evasion Results .......................................................................................................................7
Figure 4 Raw Packet Processing Performance (UDP Traffic) ......................................................................................8
Figure 5 Maximum Concurrent TCP Connections and Maximum TCP Connections per Second ..............................10
Figure 6 Detection under Load (HTTP Capacity with No Transaction Delay) ............................................................11
Figure 7 Detection under Load (HTTP Capacity with Transaction Delay) .................................................................12
Figure 8 Detection under Load (Real World Traffic) ..............................................................................................13
Figure 9 Stability and Reliability Results ...................................................................................................................14
Figure 10 Number of Users .......................................................................................................................................16
Figure 11 Installation Time (Hours) ..........................................................................................................................16
Figure 12 Total Cost of Ownership (TCO) .................................................................................................................17
Figure 13 Total Cost of Ownership per Protected Mbps ..........................................................................................18
Figure 14 Scorecard ..................................................................................................................................................20
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Security Effectiveness
This section aims to verify that the product can detect and log breaches and attempted breaches accurately. All
tests in this section are completed with no background network load.
This test utilizes threats and attack methods that exist in the wild and are currently being used by cybercriminals
and other threat actors, based on attacks collected from NSS global threat intelligence network. For details on live
testing, refer to the Security Stack Methodology v1.5.2
The ability of the product to detect and report successful infections in a timely manner is critical to maintaining the
security and functionality of the monitored network. Infection and transmission of malware should be reported
quickly and accurately, giving administrators the opportunity to contain the infection and minimize impact on the
network.
As response time is critical in halting the damage caused by malware infections, the system under test (SUT)
should be able to detect known samples, or analyze unknown samples, and report on them within 48 hours of
initial infection and command and control (C&C) callback. Any SUT that does not alert on an attack, infection, or
C&C callback within the detection window will not receive credit for the detection.
The following use cases may be examined to determine if the SUT can identify a security risk within each scenario.
Web-based malware attacks that rely on social engineering The user is deceived into clicking a malicious
link to download and execute malware.
Web-based exploits Also known as drive-by downloads, these occur when the user is infected merely by
visiting a web page that hosts malicious code.
Socially engineered malware delivered via non-HTTP traffic Malware is delivered by other common means
such as email, a cloaked executable (.jpeg, .exe, .zip), FTP, or an infected USB drive.
Blended exploits Also known as doc-jacking, these are typically delivered via common documents, such as
Microsoft Word documents or Excel spreadsheets, containing exploits. These exploits are typically delivered
via network protocols.
Offline infections Remote users with mobile devices can become infected while outside the protection of
the corporate network security. When infected devices are subsequently reattached to the corporate
network, the infection can spread.
https://www.nsslabs.com/reports/security-stack-test-methodology-v15
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Exploit and Malware Detection
Figure 2 depicts the percentage of malware and exploits detected by Check Point 13500 Next Generation Threat
Prevention Appliance with Threat Emulation Cloud Service for each of the delivery mechanisms used in the test:
Drive-by and social exploits Malicious software that is designed to take advantage of existing deficiencies in
hardware or software systems, such as vulnerabilities or bugs
HTTP protocol Malware using HTTP protocol as its transport mechanism; that is, the malware is downloaded
through a web browser
SMTP/IMAP Malware that uses email (SMTP/IMAP) as its transport mechanism; for example, a malicious
email attachment
SMB Malware that uses the server message block (SMB) protocol as its transport mechanism
Figure 2 Exploit and Malware Detection Rates
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Resistance to Evasion Techniques
Evasion techniques are a means of disguising and modifying attacks at the point of delivery in order to avoid
detection by security products. If a security device fails to correctly identify a specific type of evasion, an attacker
could potentially deliver malware that the device normally would detect. Figure 3 provides the results of the
evasion tests for Check Point 13500 Next Generation Threat Prevention Appliance with Threat Emulation Cloud
Service.
Evasions
Result
Packers
100.0%
Compressors
100.0%
Virtual machine
100.0%
Sandbox
100.0%
HTML obfuscation
90.0%
Layered evasions
75.0%
Figure 3 Resistance to Evasion Results
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Network Device Performance
There is frequently a trade-off between Security Effectiveness and performance; a products Security Effectiveness
should be evaluated within the context of its performance, and vice versa. This ensures that detection does not
adversely impact performance and that no security shortcuts are taken to maintain or improve performance. The
NSS performance tests are designed to validate that a network device inspection engine can maintain its detection
rate as background traffic increases.
Raw Packet Processing Performance (UDP Traffic)
This section uses UDP packets of varying sizes generated by test equipment. A constant stream of the appropriate
packet size with variable source and destination IP addresses transmitting from a fixed source port to a fixed
destination port is transmitted bidirectionally over the monitored network.
Each packet contains dummy data and is targeted at a valid port on a valid IP address on the target subnet. The
percentage load and frames per second (fps) figures across each inline port pair are verified by network monitoring
tools before each test begins. Multiple tests are run and averages are taken where necessary.
This traffic does not attempt to simulate any real-world network. No TCP sessions are created during this test, and
there is very little for the detection engine to do. However, each vendor will be required to write a signature to
detect the test packets in order to ensure that they are being passed through the detection engine and not fasttracked through the network device. The first stage at which one or more attacks is not detected is recorded as
the maximum raw packet processing capacity for the network device.
Figure 4 Raw Packet Processing Performance (UDP Traffic)
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Maximum Capacity
The use of automated testing and traffic generation appliances allows NSS engineers to create real-world, highspeed traffic as the background load for the tests.
These tests aim to stress the network device inspection engine and determine how it copes with high volumes of
concurrent transmission control protocol (TCP) open connections and TCP connections per second. All tests in this
section are repeated at 25%, 50%, 75%, and 100%3 of the maximum rated throughput of the SUT. At each stage,
multiple instances of malicious traffic are passed and the number detected is logged. The first stage at which one
or more attacks is not detected is recorded as the maximum capacity for that response size/traffic mix.
Maximum concurrent TCP connections This test determines the maximum concurrent TCP connections of
the SUT with no data passing across the connections. This type of traffic is not typically found on a normal
network, but it provides the means to determine the maximum possible concurrent connections figure. The
first stage at which one or more attacks is not detected is recorded as the maximum concurrent TCP open
connections.
Maximum TCP connections per second This test determines the maximum TCP connection rate of the SUT
with one byte of data passing across the connections. This type of traffic is not typically found on a normal
network, but it provides the means to determine the maximum possible TCP connection rate. The first stage at
which one or more attacks is not detected is recorded as the maximum TCP connections.
Maximum HTTP connections per second This test determines the maximum TCP connection rate of the
network device with a 1-byte HTTP response size. The response size defines the number of bytes contained in
the body, excluding any bytes associated with the HTTP header. A 1-byte response size is designed to provide
a theoretical maximum HTTP connections per second rate. The first stage at which one or more attacks is not
detected is recorded as the maximum HTTP connections.
Results for the maximum concurrent TCP connections per second, maximum TCP connections, and maximum HTTP
connections per second tests are provided in Figure 5.
The 100% load will actually be less than 100% to allow headroom for malicious traffic.
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Figure 5 Maximum Concurrent TCP Connections and Maximum TCP Connections per Second
10
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
HTTP Capacity with No Transaction Delays
These tests stress the HTTP detection engine and determine how the SUT copes with network loads of varying
average packet size and varying connections per second. By creating genuine session-based traffic with varying
session lengths, the SUT is forced to track valid TCP sessions, thus ensuring a higher workload than for simple
packet-based background traffic. This provides a test environment that is as close to real world as it is possible to
achieve in a lab environment, while also ensuring absolute accuracy and repeatability.
Each transaction consists of a single HTTP GET request with no transaction delays (that is, the web server responds
immediately to all requests). All packets contain valid payload (a mix of binary and ASCII objects) and address data.
This test provides an excellent representation of a live network (albeit one biased toward HTTP traffic) at various
network loads.
All tests in this section are repeated at 25%, 50%, 75%, and 100%4 of the maximum rated throughput of the SUT.
At each stage, multiple instances of malicious traffic are passed and the number detected is logged. The first stage
at which one or more attacks is not detected is recorded as the maximum HTTP capacity for that response
size/traffic mix.
Figure 6 Detection under Load (HTTP Capacity with No Transaction Delay)
The 100% load will actually be less than 100% to allow headroom for malicious traffic.
11
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
HTTP Capacity with Transaction Delays
Typical user behavior introduces delays between requests and reponses; for example, think time, as users read
web pages and decide which links to click next. This group of tests is identical to the previous group except that
these tests include a five-second delay in the server response for each transaction. This delay has the effect of
maintaining a high number of open connections throughout the test, thus forcing the sensor to utilize additional
resources to track those connections.
As with the tests that employ HTTP capacity with no transaction delays, tests are repeated at 25%, 50%, 75%, and
100%5 of the maximum rated throughput of the BDS. In order to highlight any differences in performance, Figure 7
presents the results for HTTP capacity both with and without transaction delays.
Figure 7 Detection under Load (HTTP Capacity with Transaction Delay)
5The
100% load will actually be less than 100% to allow headroom for malicious traffic.
12
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Real-World Traffic Mixes
This test measures the performance of the network device under test in a real-world environment by introducing
additional protocols and real content while still maintaining a precisely repeatable and consistent background
traffic load. The average result is a background traffic load that is closer to what may be found on a heavily utilized
normal production network. All tests are repeated at 25%, 50%, 75%, and 100%6 of the maximum rated
throughput of the SUT. At each stage, multiple instances of malicious traffic are passed and the number detected is
logged. The first stage at which one or more attacks is not detected is recorded as the maximum rated throughput
of the BDS. Results are presented in Figure 8.
The 13500 Next Generation Threat Prevention Appliance with Threat Emulation Cloud Service performed in line
with the throughput claimed by the vendor.
Figure 8 Detection under Load (Real World Traffic)
The 100% load will actually be less than 100% to allow headroom for malicious traffic.
13
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Stability and Reliability
Long-term stability is important, since a failure can result in serious breaches remaining undetected and thus not
remediated. These tests verify the stability of a network device, along with its ability to maintain a minimum level
of detection while under normal load and while identifying malicious traffic. Products that cannot sustain logging
of legitimate traffic or that crash while under hostile attack will not pass.
The 13500 Next Generation Threat Prevention Appliance with Threat Emulation Cloud Service is required to
remain operational and stable throughout these tests and to operate at 100% scanning capability, raising an alert
each time malicious traffic is detected. If any malicious traffic passes undetected, caused by either the volume of
traffic or by the BDS failing for any reason, the product will fail.
Figure 9 presents the results of the stability and reliability tests for the Check Point 13500 Next Generation Threat
Prevention Appliance with Threat Emulation Cloud Service.
Stability and Reliability
Result
Detection under extended attack
PASS
Attack detection normal load
PASS
Protocol fuzzing and mutation detection ports
PASS
Persistence of data
PASS
Figure 9 Stability and Reliability Results
14
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Management and Configuration
Security devices are complicated to deploy, and essential components such as centralized management console
options, log aggregation, and event correlation/management systems further complicate the purchasing decision.
Understanding key comparison points will allow customers to model the overall impact on network service level
agreements (SLAs), estimate operational resource requirements to maintain and manage the systems, and better
evaluate the required skill and competencies of staff.
Enterprises should include management and configuration during their evaluation, focusing on the following at
minimum:
General management and configuration How easy is it to install and configure network devices and/or
agents, and how easy is it to deploy multiple devices throughout a large enterprise network?
Product customization How easy is it to create custom configurations, edit them, and deploy them across an
enterprise? Configurations may be policies, alert settings, and so on, depending on the product.
Alert handling How accurate and timely is the alerting, and how easy is it to drill down to locate critical
information needed to remediate a security problem?
Reporting How effective is the reporting capability, and how readily can it be customized?
Total Cost of Ownership (TCO)
Implementation of security solutions can be complex, with several factors affecting the overall cost of deployment,
maintenance fees, and upkeep.
The following factors should be considered over the course of the useful life of the solution:
Product purchase The cost of acquisition.
Product maintenance fees The recurring fees paid to the vendor (including software and hardware support,
maintenance, and other updates).
Installation time The time required to take the device out of the box, configure it, put it into the network,
apply updates and patches, and set up desired logging and reporting.
Upkeep The time required to apply periodic updates and patches from vendors, including hardware,
software, and other updates.
Management Day-to-day management tasks including device configuration, policy updates, policy
deployment, alert handling, and so on.
For the purposes of this report, capital expenditure (capex) items are included for a single product only (the cost of
acquisition and installation).
15
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Calculating the Total Cost of Ownership (TCO)
In procuring a BDS solution for the enterprise, it is essential to factor in both bandwidth and the number of users.
NSS has found that the malware detection rates of some BDS network devices drop when they operate at
maximum capacity. NSS research has shown that, in general, enterprise network administrators architect their
networks for up to 2 Mbps per employee of sustained throughput. Consequently, an enterprise must deploy 500
agents and/or one network device of 1,000 Mbps capacity to support 500 users.
Users
Mbps per User
Network Device Throughput
Centralized Management
500
2 Mbps
1,000 Mbps
Figure 10 Number of Users
Installation Time
This table depicts the number of hours of labor required to install each BDS. The table accurately reflects the
amount of time that NSS engineers, with the help of vendor engineers, needed to install and configure the BDS to
the point where it operated successfully in the test harness, ignored legitimate traffic, and detected prohibited or
malicious traffic. This closely mimics a typical enterprise deployment scenario for a single product.
The installation cost is based on the time that an experienced security engineer would require to perform the
installation tasks described above. This approach allows NSS to hold constant the talent cost and measure only the
difference in time required for installation. Readers should substitute their own costs to obtain accurate TCO
figures.
Product
Installation
Check Point 13500 Next Generation Threat Prevention Appliance with
Threat Emulation Cloud Service R77.20
Figure 11 Installation Time (Hours)
16
8 hours
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Purchase Price And Total Cost Of Ownership
Calculations are based on vendor-provided pricing. Where possible, the 24/7 maintenance and support option with
24-hour replacement is utilized, since this is the option typically selected by enterprise customers. Prices are for a
1,000 Mbps single network BDS and/or 500 software agents, and maintenance only; the cost for a central
management system (CMS) may be extra. For additional TCO analysis, including the CMS, refer to the TCO
Comparative Report.
Product
Check Point 13500 Next Generation
Threat Prevention Appliance with
Threat Emulation Cloud Service R77.20
Purchase
Maintenance
/Year
Year 1
Cost
Year 2
Cost
Year 3
Cost
3-Year
TCO
$79,600
$29,976
$110,176
$29,976
$29,976
$170,128
Figure 12 Total Cost of Ownership (TCO)
Year 1 Cost is calculated by adding installation costs (US$75 per hour fully loaded labor x installation time) +
purchase price + first-year maintenance/support fees.
Year 2 Cost consists only of maintenance/support fees.
Year 3 Cost consists only of maintenance/support fees.
This formula provides a TCO consisting of software, hardware, installation, and maintenance costs for a BDS that
includes 1,000 Mbps of bandwidth and/or 500 agents. Additional management and labor costs are excluded, as are
TCO calculations for additional devices or agents, since they are modeled extensively in the TCO Comparative
Report.
17
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Value: Total Cost of Ownership per Protected Mbps
There is a clear difference between price and value. The least expensive product does not necessarily offer the
greatest value if it offers significantly lower performance than only slightly more expensive competitors. The best
value is a product with a low TCO and high level of secure throughput (Detection Rate x NSS-Tested Throughput).
Figure 13 depicts the relative cost per unit of work performed, described as TCO per Protected Mbps.
Product
Detection
Rate
3-Year
TCO
NSS-Tested
Throughput
TCO per
Protected Mbps
97.2%
$170,128
1,000 Mbps
$175
Check Point 13500 Next Generation Threat
Prevention Appliance with Threat Emulation
Cloud Service R77.20
Figure 13 Total Cost of Ownership per Protected Mbps
The TCO per Protected Mbps was calculated by taking the 3-Year TCO and dividing it by the product of the
detection rate multiplied by the NSS-Tested Throughput. Therefore, 3-Year TCO/ (Detection Rate x NSS-Tested
Throughput) = TCO per Protected Mbps.
18
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Appendix: Product Scorecard
Description
Security Effectiveness
Detection Rate
Exploits
Drive-by Exploits
Social Exploits
Malware (various delivery mechanisms)
HTTP
SMB
Evasions
Packers
Compressors
Virtual Machine
Sandbox
HTML Obfuscation
Layered Evasions
Performance
Raw Packet Processing Performance (UDP Traffic)
64 Byte Packets
128 Byte Packets
265 Byte Packets
512 Byte Packets
1024 Byte Packets
1514 Byte Packets
Maximum Capacity
Maximum Concurrent TCP Connections
Maximum TCP Connections per Second
Maximum HTTP Connections per Second
HTTP Capacity with No Transaction Delays
44 KB HTTP Response Size 2,500 Connections per Second
21 KB HTTP Response Size 5,000 Connections per Second
10 KB HTTP Response Size 10,000 Connections per Second
4.5 KB HTTP Response Size 20,000 Connections per Second
1.7 KB HTTP Response Size 40,000 Connections per Second
HTTP Capacity With Transaction Delays
21 KB HTTP Response Size with Delay
10 KB HTTP Response Size with Delay
19
Result
97.2%
94.4%
100.0%
88.9%
100.0%
100.0%
100.0%
100.0%
94.2%
100.0%
100.0%
100.0%
100.0%
90.0%
75.0%
Max Capacity (Mbps)
1,000
1,000
1,000
1,000
1,000
1,000
Max Capacity
15,000,000
125,000
75,000
Max Capacity (Mbps)
1,000
1,000
1,000
1,000
1,000
Max Capacity (Mbps)
1,000
1,000
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Real-World Traffic
Real-World Protocol Mix (Enterprise Perimeter)
Real-World Protocol Mix (Education)
Stability & Reliability
Detection Under Extended Attack
Attack Detection Normal Load
Protocol Fuzzing and Mutation Detection Ports
Persistence of Data
TCO
Ease of Use
Initial Setup (Hours) Hardware
Initial Setup (Hours) Software
Expected Costs
Initial Purchase (hardware as tested)
Initial Purchase (software as tested per agent)
Setup Cost ($75 Hour)
Initial Purchase (enterprise management system)
Annual Cost of Maintenance & Support (hardware)
Annual Cost of Maintenance & Support (software per agent)
Annual Cost of Maintenance & Support (enterprise management)
Total Cost of Ownership (TCO)
Year 1
Year 2
Year 3
3-Year TCO
Figure 14 Scorecard
20
Max Capacity (Mbps)
1000
1000
PASS
PASS
PASS
PASS
8
0
$79,600
$0
$600
See Comparative
$29,976
$0
See Comparative
$110,176
$29,976
$29,976
$170,128
NSS Labs
Breach Detection System Test Report Check Point 13500 Next Generation Threat Prevention Appliance
with Threat Emulation Cloud Service
Test Methodology
Breach Detection Systems (BDS): v2.0
A copy of the test methodology is available on the NSS Labs website at www.nsslabs.com.
Contact Information
NSS Labs, Inc.
206 Wild Basin Road
Building A, Suite 200
Austin, TX 78746 USA
info@nsslabs.com
www.nsslabs.com
This and other related documents are available at: www.nsslabs.com. To receive a licensed copy or report misuse,
please contact NSS Labs.
2015 NSS Labs, Inc. All rights reserved. No part of this publication may be reproduced, copied/scanned, stored on a retrieval
system, e-mailed or otherwise disseminated or transmitted without the express written consent of NSS Labs, Inc. (us or we).
Please read the disclaimer in this box because it contains important information that binds you. If you do not agree to these
conditions, you should not read the rest of this report but should instead return the report immediately to us. You or your
means the person who accesses this report and any entity on whose behalf he/she has obtained this report.
1. The information in this report is subject to change by us without notice, and we disclaim any obligation to update it.
2. The information in this report is believed by us to be accurate and reliable at the time of publication, but is not guaranteed.
All use of and reliance on this report are at your sole risk. We are not liable or responsible for any damages, losses, or expenses
of any nature whatsoever arising from any error or omission in this report.
3. NO WARRANTIES, EXPRESS OR IMPLIED ARE GIVEN BY US. ALL IMPLIED WARRANTIES, INCLUDING IMPLIED WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT, ARE HEREBY DISCLAIMED AND EXCLUDED
BY US. IN NO EVENT SHALL WE BE LIABLE FOR ANY DIRECT, CONSEQUENTIAL, INCIDENTAL, PUNITIVE, EXEMPLARY, OR INDIRECT
DAMAGES, OR FOR ANY LOSS OF PROFIT, REVENUE, DATA, COMPUTER PROGRAMS, OR OTHER ASSETS, EVEN IF ADVISED OF THE
POSSIBILITY THEREOF.
4. This report does not constitute an endorsement, recommendation, or guarantee of any of the products (hardware or
software) tested or the hardware and/or software used in testing the products. The testing does not guarantee that there are
no errors or defects in the products or that the products will meet your expectations, requirements, needs, or specifications, or
that they will operate without interruption.
5. This report does not imply any endorsement, sponsorship, affiliation, or verification by or with any organizations mentioned
in this report.
6. All trademarks, service marks, and trade names used in this report are the trademarks, service marks, and trade names of
their respective owners.
21
Das könnte Ihnen auch gefallen
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeVon EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeBewertung: 4 von 5 Sternen4/5 (5794)
- Kernel Debug Flags R77.10Dokument16 SeitenKernel Debug Flags R77.10mbaezasotoNoch keine Bewertungen
- Shoe Dog: A Memoir by the Creator of NikeVon EverandShoe Dog: A Memoir by the Creator of NikeBewertung: 4.5 von 5 Sternen4.5/5 (537)
- How To Update The Firmware of TP-LINK Powerline Adapters Using The TPPLC Utility PDFDokument2 SeitenHow To Update The Firmware of TP-LINK Powerline Adapters Using The TPPLC Utility PDFmbaezasotoNoch keine Bewertungen
- PAN OS Panorama 81 Help Web Int Ref SpanishDokument846 SeitenPAN OS Panorama 81 Help Web Int Ref SpanishmbaezasotoNoch keine Bewertungen
- The Yellow House: A Memoir (2019 National Book Award Winner)Von EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Bewertung: 4 von 5 Sternen4/5 (98)
- Esm 103x PG En-Us PDFDokument338 SeitenEsm 103x PG En-Us PDFmbaezasotoNoch keine Bewertungen
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceVon EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceBewertung: 4 von 5 Sternen4/5 (895)
- Amp Bds ReportDokument21 SeitenAmp Bds ReportJonatan RodriguezNoch keine Bewertungen
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersVon EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersBewertung: 4.5 von 5 Sternen4.5/5 (344)
- Cooking With Less Fuel: Breathing Less SmokeDokument54 SeitenCooking With Less Fuel: Breathing Less SmokeFredrik GaddNoch keine Bewertungen
- The Little Book of Hygge: Danish Secrets to Happy LivingVon EverandThe Little Book of Hygge: Danish Secrets to Happy LivingBewertung: 3.5 von 5 Sternen3.5/5 (399)
- Osstmm 3Dokument213 SeitenOsstmm 3Ben ZiriNoch keine Bewertungen
- Grit: The Power of Passion and PerseveranceVon EverandGrit: The Power of Passion and PerseveranceBewertung: 4 von 5 Sternen4/5 (588)
- Performance Piano: Examination MusicDokument51 SeitenPerformance Piano: Examination MusicKylie Carney100% (2)
- The Emperor of All Maladies: A Biography of CancerVon EverandThe Emperor of All Maladies: A Biography of CancerBewertung: 4.5 von 5 Sternen4.5/5 (271)
- Rocket Mass StovesDokument58 SeitenRocket Mass StovesΚαπετάν ΜύγαςNoch keine Bewertungen
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaVon EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaBewertung: 4.5 von 5 Sternen4.5/5 (266)
- Exalogic System Overview 1724075Dokument28 SeitenExalogic System Overview 1724075mbaezasotoNoch keine Bewertungen
- Never Split the Difference: Negotiating As If Your Life Depended On ItVon EverandNever Split the Difference: Negotiating As If Your Life Depended On ItBewertung: 4.5 von 5 Sternen4.5/5 (838)
- C Major For PianoDokument1 SeiteC Major For PianoHoàng BùiNoch keine Bewertungen
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryVon EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryBewertung: 3.5 von 5 Sternen3.5/5 (231)
- Sid800 DS 1109Dokument2 SeitenSid800 DS 1109mbaezasotoNoch keine Bewertungen
- SAFE RGDokument354 SeitenSAFE RGAnatolie ErnuNoch keine Bewertungen
- On Fire: The (Burning) Case for a Green New DealVon EverandOn Fire: The (Burning) Case for a Green New DealBewertung: 4 von 5 Sternen4/5 (73)
- DX50 UserGuideDokument15 SeitenDX50 UserGuidembaezasotoNoch keine Bewertungen
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureVon EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureBewertung: 4.5 von 5 Sternen4.5/5 (474)
- HOHNER Accordions 02 2013 EnglishDokument29 SeitenHOHNER Accordions 02 2013 Englishmbaezasoto0% (4)
- Team of Rivals: The Political Genius of Abraham LincolnVon EverandTeam of Rivals: The Political Genius of Abraham LincolnBewertung: 4.5 von 5 Sternen4.5/5 (234)
- DX50 UserGuideDokument15 SeitenDX50 UserGuidembaezasotoNoch keine Bewertungen
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyVon EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyBewertung: 3.5 von 5 Sternen3.5/5 (2259)
- Kernel Debug Flags R77.10Dokument16 SeitenKernel Debug Flags R77.10mbaezasotoNoch keine Bewertungen
- CP E80.50 EPSWindowsClient UserGuide enDokument36 SeitenCP E80.50 EPSWindowsClient UserGuide enmbaezasotoNoch keine Bewertungen
- Leadership With Mobility and BYOD FINALDokument8 SeitenLeadership With Mobility and BYOD FINALmbaezasotoNoch keine Bewertungen
- Gartner MQ Global MSSP 2014Dokument23 SeitenGartner MQ Global MSSP 2014mbaezasotoNoch keine Bewertungen
- Am 61 Security Best PracticesDokument22 SeitenAm 61 Security Best PracticesmbaezasotoNoch keine Bewertungen
- The Unwinding: An Inner History of the New AmericaVon EverandThe Unwinding: An Inner History of the New AmericaBewertung: 4 von 5 Sternen4/5 (45)
- Oracle® Linux Virtualization Manager: Architecture and Planning GuideDokument42 SeitenOracle® Linux Virtualization Manager: Architecture and Planning GuideAlem MezgeboNoch keine Bewertungen
- Reading ComprehensionDokument2 SeitenReading ComprehensionMuhamad Khoerudin100% (2)
- Exin - Premium.DEVOPSF - by .VCEplus.40q-DEMODokument13 SeitenExin - Premium.DEVOPSF - by .VCEplus.40q-DEMOQuique FdezNoch keine Bewertungen
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreVon EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreBewertung: 4 von 5 Sternen4/5 (1090)
- GUI Testing On A Product Suite Using On-The-Shelf Testing SoftwareDokument15 SeitenGUI Testing On A Product Suite Using On-The-Shelf Testing SoftwareAnubhav JainNoch keine Bewertungen
- CH3 - STM32 SoftwareprogrammingDokument15 SeitenCH3 - STM32 Softwareprogramminghouda bouzekriNoch keine Bewertungen
- Nymble Blocking System - NeedDokument21 SeitenNymble Blocking System - NeedManzeer FasaludeenNoch keine Bewertungen
- 2.chapter - 9 - Public Key Cryptography and RSADokument40 Seiten2.chapter - 9 - Public Key Cryptography and RSAtt hhNoch keine Bewertungen
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Von EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Bewertung: 4.5 von 5 Sternen4.5/5 (120)
- Description Run CommandDokument3 SeitenDescription Run CommandJitesh giriNoch keine Bewertungen
- Building Web Applications With: Course 977Dokument463 SeitenBuilding Web Applications With: Course 977Adrian GorganNoch keine Bewertungen
- Chapter Iii: Physical LayerDokument8 SeitenChapter Iii: Physical LayerEcho greenNoch keine Bewertungen
- Cognizant Information For Task 3Dokument14 SeitenCognizant Information For Task 3Jackson Tom100% (1)
- 4.4.8 Packet Tracer - Troubleshoot Inter-VLAN RoutingDokument2 Seiten4.4.8 Packet Tracer - Troubleshoot Inter-VLAN RoutingPablo BautistaNoch keine Bewertungen
- KSN enDokument9 SeitenKSN enWellin SantanaNoch keine Bewertungen
- Addressing: Four Levels of Addresses Are Used in An Internet Employing The TCP/IP Protocols:, ,, andDokument11 SeitenAddressing: Four Levels of Addresses Are Used in An Internet Employing The TCP/IP Protocols:, ,, andSurachet WongchomphuNoch keine Bewertungen
- 5GC Corporation TajikistanDokument44 Seiten5GC Corporation TajikistanDaler ShorahmonovNoch keine Bewertungen
- Blackmagic Switchers SDKDokument637 SeitenBlackmagic Switchers SDKyukiNoch keine Bewertungen
- IC WBS With Gantt Chart Template 8721Dokument8 SeitenIC WBS With Gantt Chart Template 8721Shidqi PranitiNoch keine Bewertungen
- Soal PHBDokument11 SeitenSoal PHBAmira Nur AuliaNoch keine Bewertungen
- Her Body and Other Parties: StoriesVon EverandHer Body and Other Parties: StoriesBewertung: 4 von 5 Sternen4/5 (821)
- Cybercrime English TaskDokument6 SeitenCybercrime English TaskYvette RufoNoch keine Bewertungen
- Question No. 1: Sr. No Points SolutionDokument2 SeitenQuestion No. 1: Sr. No Points Solutionbc160402062 Esha AshfaqNoch keine Bewertungen
- SMU02B V500R002C20SPC005 One Key Upgrade GuideDokument24 SeitenSMU02B V500R002C20SPC005 One Key Upgrade GuideManuel RivasNoch keine Bewertungen
- How To Implement AES in RubyDokument13 SeitenHow To Implement AES in Rubychris_hulbertNoch keine Bewertungen
- Produktinformation: Vi Reserverar Oss Mot Fel Samt Förbehåller Oss Rätten Till Ändringar Utan Föregående MeddelandeDokument3 SeitenProduktinformation: Vi Reserverar Oss Mot Fel Samt Förbehåller Oss Rätten Till Ändringar Utan Föregående MeddelandeRabah AmidiNoch keine Bewertungen
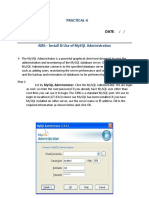
- Practical-6: DATEDokument19 SeitenPractical-6: DATESarthak RavatNoch keine Bewertungen
- SCADA Modbus Scan Task User's GuideDokument61 SeitenSCADA Modbus Scan Task User's GuideGESELL CABEZASNoch keine Bewertungen
- DocumentDokument37 SeitenDocumentDigambar S TatkareNoch keine Bewertungen
- Chapter 2 Data Processing Peter NortonDokument20 SeitenChapter 2 Data Processing Peter NortonUsama AdilNoch keine Bewertungen
- MVP Salessheet Decoders-1Dokument4 SeitenMVP Salessheet Decoders-1Paul ShepherdNoch keine Bewertungen
- Class - IV Subject - Computer Introduction To Windows - 7: Q.1 Tick The Correct AnswerDokument3 SeitenClass - IV Subject - Computer Introduction To Windows - 7: Q.1 Tick The Correct AnswerSrishti SharmaNoch keine Bewertungen
- 2nd International Conference On Big Data, IoT and Machine Learning (BIOM 2022)Dokument2 Seiten2nd International Conference On Big Data, IoT and Machine Learning (BIOM 2022)Lewis TorresNoch keine Bewertungen
- The Dark Net: Inside the Digital UnderworldVon EverandThe Dark Net: Inside the Digital UnderworldBewertung: 3.5 von 5 Sternen3.5/5 (104)
- Defensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityVon EverandDefensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityBewertung: 5 von 5 Sternen5/5 (1)
- The Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellVon EverandThe Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellBewertung: 5 von 5 Sternen5/5 (6)