Beruflich Dokumente
Kultur Dokumente
UP Acceptable Use Policy
Hochgeladen von
Jihan PacerCopyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
UP Acceptable Use Policy
Hochgeladen von
Jihan PacerCopyright:
Verfügbare Formate
4/10/12
Acceptable Use Policy
APPROVEDACCEPTABLEUSEPOLICYFORINFORMATIONTECHNOLOGY(IT)RESOURCESOFTHEUPSYSTEM
Section1.PolicyStatement
(a)
Computersandnetworksarepowerfultechnologiesforaccessinganddistributinginformationandknowledge.Theyare
strategictechnologiesforthecurrentandfutureneedsoftheUPSYSTEM.
(b)
Fornow,computingfacilitiesandnetworkinfrastructureareacostlyresourceandthusmustbeusedsolelyfor
teaching,learning,research,andotherofficiallysanctionedactivities.Also,sincethesetechnologiesallowindividuals
toaccessandcopyinformationfromremotesources,usersmustrespecttherightsofothers,particularlytotheir
privacyandintellectualproperty.Thereisthereforeaneedforrulesandregulationstoensureequitable,secureand
reliableaccesstotheseresources.Thefollowingregulationswillgoverntheuseofcomputingfacilities,networksand
otherInformationTechnology(IT)resourcesoftheUniversityofthePhilippinesSystem.
(c)
Theseregulationsaimto:
(i)
ensureaninformationinfrastructurethatpromotesthebasicmissionsoftheUPSYSTEMinteaching,learning
andresearch
(ii)
protecttheintegrity,reliability,availability,confidentialityandefficiencyoftheITresourcesoftheUP
SYSTEM
(iii)
establishprocessesforaddressingpolicyviolationsandprovidingsanctionsforviolators
(iv)
emphasizethattheUPSYSTEMshallnotbeliableforanydamagesincurredfromtheuseofITresourcesand
foranyclaimsandsuitsarisingfromtheunauthorizedandirresponsibleuseofthesame
(v)
warnusersthatuseofITresourcesforpartisanpoliticalactivitiesasdefinedinrelevantrulesandregulations
ofthecivilservicecommissionortheuniversityofthePhilippines,orforanyunauthorizedcommercial
purposesisprohibitedand
(vi)
notifyusersoftheexistenceofthisPolicy.
Section2.BasicStandards
(a)
Thesamestandardsandprinciplesofintellectualandacademicfreedomdevelopedforuniversitylibrariesshallbe
appliedtomaterialreceivedfromthenetwork.Thesamestandardsofintellectualandacademicfreedomdeveloped
forfacultyandstudentpublicationintraditionalmediashallbeappliedtopublicationincomputermedia.
(b)
Asconstituentsoftheacademiccommunity,faculty,students,andacademicandnonacademicstaffshouldbefree,
individuallyandcollectively,toexpresstheirviewsonissuesofinstitutionalpolicyandonmattersofgeneralinterest
totheacademicbody.Theconstituentsoftheacademiccommunityshouldhaveclearlydefinedmeanstoparticipate
intheformulationandapplicationofinstitutionalpolicyaffectingacademicandstudentaffairs.Theactionsofthe
constituentsoftheacademiccommunitywithintheareasofitsjurisdictionsshouldbereviewedonlythroughorderly
prescribedprocedures.
Section3.Definitions
(a)
AgreementFormmeansdocumentinwhichtheuserundertakestocomplywiththisPolicy.Theformmaybe
electronic.
(b)
Confidentialinformationmeansdataorinformationwhichonitsfaceisnotintendedforunrestricteddissemination.
Examplesincludestudentrecords,examinationarchives,proprietarytechnicalinformation,disciplinarycaserecords,
administrativerecords,andthelike.
(c)
DocumentwhenusedinthisPolicyshallreferbothtothepaperanditselectronicformat.
(d)
InformationTechnologySystemorITSystemincludescomputers,terminals,printers,networks,modembanks,online
andofflinestoragemediaandrelatedequipment,andsoftware,databasesandotherdatafilesthatareowned,
managed,ormaintainedbyanyunitoftheUniversityofthePhilippines.
ForpurposesofthisPolicy,anyotherequipment,computerunitorexternalnetwork,whenattachedto,orusedto
accessand/orinteractwithanycomponentof,theITSystemmayalsobeconsideredpartoftheITSystem.
(e)
Privatefilesmeansinformationthatauserwouldreasonablyregardasprivate.Examplesincludethecontentsof
electronicmailboxes,privatefilestorageareasofindividualusers,andinformationstoredinotherareasthatarenot
public,evenifnomeasurehasbeentakentoprotectsuchinformation.
(f)
SystemandNetworkAdministratormeansapersondesignatedtomanagetheparticularsystemassignedtoher/him,
tooverseethedaytodayoperationofthesystem,ortopreliminarilydeterminewhoispermittedaccesstoparticular
facilitiesandresourcesoftheITSystem,whetherhiredonatemporary,contractualorpermanentbasis.
(g)
UPSYSTEMmeanstheUniversityofthePhilippinesSystemandallitsconstituentunits.
(h)
Usermeansanyperson,whetherauthorizedornot,whomakesanyuseoftheITSystemoranyofitscomponentsby
anymeansorfromanylocation.
Section4.ScopeAndApplicability
(a)
(b)
GeneralCoverage.
(i)
ThisPolicyappliestoallfacilitieswithintheITSystemandallitsusers.
(ii)
Allusersshouldbeawareoftheseregulations,andshouldrealizethatwhenusingthecomputerswithintheUP
SYSTEM,theyareboundbytheseregulations.Usersmayberequiredtosignaformagreeingtocomplywith
thisPolicy.However,failuretosigntheagreementformwillnotreleaseusersfromcoverageofthisPolicy.
LocalandExternalConditionsofUse.
(i)
IndividualunitswithintheUPSYSTEMmaydefineadditional"conditionsofuse"forcomponentsofthe
ITSystemundertheircontrol.
(ii)
Theseconditionsmustbeconsistentwiththisoverallpolicybutmayprovideadditionaldetail,guidelines,
restrictions,and/orenforcementmechanisms.Theseunitswillberesponsibleforpublishingtheregulationsthey
establishandtheirpoliciesconcerningtheauthorizedandappropriateuseoftheequipmentforwhichtheyare
responsible.CopiesofthesepoliciesshouldbegiventothePresident,VicePresidentforDevelopment,the
IntellectualPropertyOfficeandtheOfficeofLegalServices.
(iii)
Whereuseofexternalnetworksisinvolved,policiesgoverningsuchusewillbeapplicableandmustbeadhered
to.
Section5.GeneralResponsibilities
(a)
GeneralResponsibilitiesofUsers.Ingeneral,usersoftheITSystemmust:
(i)
usetheITSystemonlyforitsintendedpurpose,andrefrainfrommisusingorabusingit
(ii)
maintaintheintegrity,reliability,availability,confidentialityandefficiencyofcomputerbasedinformation
resources
(iii)
refrainfromseekingtogainunauthorizedaccessorexceedauthorizedaccess
(iv)
respectsoftwarecopyrightandlicensesandotherintellectualpropertyrights
(v)
respecttherightsofothercomputerusersand
mail.up.edu.ph/local/files/aup.html
1/5
4/10/12
Acceptable Use Policy
(vi)
(b)
(c)
beawarethatalthoughcomputingandinformationtechnologyprovidersthroughouttheuniversityarecharged
withpreservingtheintegrityandsecurityofresources,securitysometimescanbebreachedthroughactions
beyondtheircontrol.Usersarethereforeurgedtotakeappropriateprecautionssuchassafeguardingtheir
accountandpassword,takingfulladvantageoffilesecuritymechanisms,backingupcriticaldataandpromptly
reportinganymisuseorviolationsofthepolicy.
EverymemberoftheuniversitycommunityhasanobligationtoreportsuspectedviolationsoftheAcceptable
UsePolicyforInformationTechnologyoftheU.P.Systemoranyofitsunits.Reportsshouldbedirectedtothe
systemandnetworkadministrators,Chairs,Deans,ChancellorsorthePresident.
GeneralResponsibilitiesOfSystemAndNetworkAdministrators
(i)
SystemandnetworkadministratorsandprovidersofuniversityInformationTechnologyresourceshavethe
additionalresponsibilityofensuringtheintegrity,confidentiality,andavailabilityoftheresourcestheyare
managing.Personsinthesepositionsaregrantedsignificanttrusttousetheirprivilegesappropriatelyfortheir
intendedpurposeandonlywhenrequiredtomaintainthesystem.Anyprivateinformationseenincarryingout
thesedutiesmustbetreatedinthestrictestconfidence,unlessitrelatestoaviolationorthesecurityofthe
system.
(ii)
Systemandnetworkadministratorsareexpectedtotreatthecontentsofelectronicfilesasprivateand
confidential.Anyinspectionofelectronicfiles,andanyactionbaseduponsuchinspection,willbegovernedby
thisPolicy,otheruniversityrulesandallapplicablelaws.
GeneralResponsibilitiesOfUniversityAdministrators
(i)
Tobeinformedandknowledgeableaboutthesepolicies
(ii)
Toinitiatesystematicprogramstoinformacademicandnonacademicpersonnelofthesepolicies
Section6.AppropriateUse
(a)
AppropriateUse.UsersmayonlyusetheITSystemforitsauthorizedpurposes,whichistosupporttheresearch,
education,clinical,administrativeandotherfunctionsoftheUPSYSTEM.Theparticularpurposesofanyofthe
componentsoftheITSystem,aswellasthenatureandscopeofauthorizedincidentalpersonaluse,mayvary
accordingtothedutiesandresponsibilitiesofauser.
(b)
ProperAuthorization.UsersmayaccessonlythosefacilitiesandcomponentsoftheITSystemthatareconsistentwith
theirauthorizationcomingfromcompetentauthorities.
(c)
SpecificProscriptionsonUse.ThefollowingcategoriesofuseoftheITSystemareconsideredprohibitedand/or
inappropriate:
(i)
(ii)
UsesContraryToLaw
1.
Unlawfuluse.UsersmaynotusetheITSystemforanyactivitythatiscontrarytoanylawor
administrativeruleorregulation,ortoencourageanysuchunlawfulactivity.Violatorsshallsuffera
penaltyrangingfromsuspensionforoneyeartoexpulsionordismissal
2.
Infringementofprotectedmaterial.Usersmustnotinfringeonthecopyrightandotherpropertyrights
coveringsoftware,databasesandallothercopyrightedmaterialsuchastext,images,icons,retrieved
fromorthroughtheITSystem.Theseactsshallinclude,butisnotlimitedto,theunauthorizedcopying,
reproduction,dissemination,distribution,importation,use,removal,alteration,substitution,
modification,storage,unloading,downloading,communication,publicationorbroadcastingofsuch
material.UsersmustproperlyattributeanymaterialtheycopyfromorthroughtheITSystem.Usersare
remindedthattheinfringementofintellectualpropertyrightsbelongingtoothersthroughtheuseof
telecommunicationsnetworksisacriminaloffenseunderSection33(b)oftheElectronicCommerceAct.
Violatorsshallsufferapenaltyrangingfromsuspensionforonemonthtoexpulsionordismissal.
3.
Hacking.UsersmaynotusetheITSystemtogainunauthorizedaccessintoorinterferewithanother
computer,system,server,informationorcommunicationsystem,ortoobtainanyaccessinorderto
corrupt,alter,stealordestroyanysuchsystemorinformationwithinsuchsystemortointroduce
viruses.UsersareremindedthatalloftheforegoingactsconstitutethecrimeofHackingunderSection
33(a)oftheElectronicCommerceActandarepunishablebymandatoryimprisonmentand/orafine.
Violatorsshallsufferapenaltyrangingfromsuspensionforoneyeartoexpulsionordismissal.The
penaltyshallcarrywithitpermanentwithdrawalofallITprivileges.
UsesInconsistentWithThePurposesOfTheUPSystem
1.
Cheating.UsersmaynotusetheITSystemtoengageincheatingoracademicdishonesty.Acts
prohibitedunderthisprovisionincludebutarenotlimitedtothefollowing:
a.
Copyingacomputerfilethatcontainsanotherperson'sworkandsubmittingitforone'sown
credit
b.
Copyingacomputerfilethatcontainsanotherperson'sworkandusingitasamodelforone'sown
work
c.
Collaboratingonawork,sharingthecomputerfilesandsubmittingthesharedfile,ora
modificationthereof,asone'sindividualwork,whentheworkissupposedtobedoneindividually
and
d.
Communicatingwithanotherpersononlineduringtheconductofanexamination.Violatorsshall
sufferapenaltyofsuspensionfornotlessthanonesemester.Studentsfoundguiltyofcheating
shallbebarredformgraduatingwithhonors,eveniftheirweightedaverageiswithinthe
requirementforgraduationwithhonors.
2.
Politicaluse.UsersmaynotusetheITSystemforanypartisanpoliticalactivities.Violatorsshallsuffer
apenaltyrangingfromsuspensionforonemonthtooneyear.
3.
UnauthorizedCommercialuse.
a.
UsersmaynotusetheITSystemforcommercialpurposes,exceptaspermittedunderother
writtenpoliciesoftheUPSYSTEMorwiththewrittenapprovalofacompetentauthority.
b.
Violatorsshallsufferapenaltyrangingfromsuspensionforonemonthtooneyearwithfine.If
theviolatorisastudent,thefineshallbeP1,000.00ortheamountequivalenttotheearnings,
whicheverishigher.Iftheviolatorisafacultymemberoranemployee,thefineshallbeonehalf
ofhismonthlysalaryortheamountequivalenttotheearnings,whicheverishigher.
4.
Personaluse.UsersmaynotusetheITSystemforpersonalactivitiesnotrelatedtoappropriate
Universityfunctionsexceptinapurelyincidentalmanner.Violatorsshallsufferapenaltyrangingfrom
suspensionforonemonthtooneyear.
5.
Unauthorizedgamingorentertainment.Usersmaynotplaygamesoruseentertainmentsoftwareonor
throughtheITSystemunlessauthorizedinwritingbycompetentauthorities.Violatorsshallsuffera
penaltyrangingfromsuspensionforoneweektooneyearprovided,thatthepenaltyforhabitual
offenseshallbeexpulsionordismissal.Thepresenceofgamesoftwareoranypartthereofmaybe
presumptiveevidenceofunauthorizedgamingorentertainment.
6.
UsecontrarytoUniversitypolicyorcontract.UsersmaynotusetheITSysteminviolationofother
policiesoftheUniversity,orinanymannerinconsistentwiththecontractualobligationsofthe
University.Violatorsshallsufferapenaltyrangingfromsuspensionforoneweektooneyearinaddition
tothepenaltyoftheoffensefacilitatedthroughITnetwork.
mail.up.edu.ph/local/files/aup.html
2/5
4/10/12
Acceptable Use Policy
(iii)
(iv)
UsesThatDamageTheIntegrity,Reliability,ConfidentialityAndEfficiencyOfTheITSystem
1.
Softwareandhardwareinstallationandremoval.Unlessproperlyauthorized,usersmaynotdestroy,
remove,modifyorinstallanycomputerequipment,peripheral,operatingsystem,diskpartition,
software,database,orothercomponentoftheITSystemorconnectanycomputerunitorexternal
networktotheITSystem.Violatorsshallsufferapenaltyrangingfromsuspensionforonemonthto
expulsion.
2.
Unauthorizedordestructiveprograms.Unlessproperlyauthorizedandpartofher/hisadministrativeor
academicduties,usersmaynotdeveloporuseprogramsontheITSystemthatmayorareintendedto:
interferewiththeabilityoftheUPSYSTEMtoenforcethesepolicies
b.
damageanysoftwareorhardwarecomponentofthesystem
c.
modifynormallyprotectedorrestrictedportionsofthesystemoruseraccounts
d.
accessprivateorrestrictedportionsofthesystemor
e.
interferewithordisruptothercomputerusers.Violatorsshallsufferapenaltyrangingfrom
suspensionforoneyeartoexpulsion.
3.
Destructiveacts.Usersmaynotattempttocrash,tieup,ordenyanyserviceon,theITSystem.
Violatorsshallsufferapenaltyrangingfromsuspensionforoneyeartoexpulsion.
4.
Unauthorizedaccess.Usersmaynotattempttogainunauthorizedaccess,exceedauthorizedaccess,or
enableunauthorizedaccesstotheITSystem,ortoothernetworksorsystemsofwhichtheITSystemis
apart.Violatorsshallsufferapenaltyrangingfromsuspensionforonemonthtooneyear.
5.
Passwordprotection.Auserwhohasbeenauthorizedtouseapasswordprotectedaccountmaynot
disclosesuchpasswordorotherwisemakestheaccountavailabletootherswithoutpermissionofthe
systemadministrator.Violatorsshallsufferapenaltyrangingfromsuspensionforoneweektooneyear.
6.
Concealingaccess.Usersmaynotconceal,delete,ormodifyinformationorrecordspertainingtoaccess
totheITSystematthetimeofaccess,oraltersystemlogsaftersuchaccessforthepurposeof
concealingidentityortohideunauthorizeduse.Usersmaynotconcealtheirownidentityormasquerade
asotheruserswhenaccessing,sending,receiving,processingorstoringthroughorontheITSystem.
Violatorsshallsufferapenaltyrangingfromsuspensionforoneyeartoexpulsion.
7.
Prohibitedmaterial.Usersmaynotpublish(onmailinglists,bulletinboards,andtheWorldWideWeb)
ordisseminateprohibitedmaterialsover,orstoresuchinformationon,theITSystem.Prohibited
materialsunderthisprovisionincludebutarenotlimitedtothefollowing:
a.
Anycollectionofpasswords,personalidentificationnumbers(PINs),privatedigitalcertificates,
creditcardnumbers,orothersecureidentificationinformation
b.
Anymaterialthatenablesotherstogainunauthorizedaccesstoacomputersystem.Thismay
includeinstructionsforgainingsuchaccess,computercode,orotherdevices.Thiswould
effectivelyprecludedisplayingitemssuchas'HackersGuides',etc.
c.
Anymaterialthatpermitsanunauthorizeduser,whohasgainedaccesstoasystem,tocarryout
anymodificationofthecomputerprogramsordatastoredinthesystemand
d.
Anymaterialthatincitesorencouragesotherstocarryoutunauthorizedaccesstoormodification
ofacomputersystem.Violatorsshallsufferapenaltyrangingfromsuspensionforoneyearto
expulsion.
UsesThatEncroachOnTheRightsOfTheUsers
1.
2.
3.
(v)
a.
Wastefulanddestructivepractices.Usersmaynotencroachonothers'accessanduseoftheITSystem
throughwastefulanddestructivepracticessuchasbutnotlimitedtothefollowing:
a.
Sendingchainlettersorexcessivemessagesincludingspamming,eitherlocallyoroffcampus
violatorsshallsufferapenaltyrangingfromsuspensionforoneweektoonemonthspamming,
includestheactof(1)repeatedcrosspostingthesamemessagetoasmanynewsgroupsor
mailinglistsaspossible,whetherornotthemessageisgermanetothestatedtopicofthe
newsgroupsormailingliststargeted,(2)maliciouslysendingoutofunsolicitedemailinbulk,or
(3)sendinglargeunwantedorunnecessaryfilestoasingleemailaddress.
b.
Printingexcesscopiesofdocuments,files,data,orprogramsviolatorsshallsufferapenalty
rangingfromsuspensionforoneweektoonemonth
c.
Runninggrosslyinefficientprogramswhenefficientalternativesareknownbytheusertobe
availableviolatorsshallsufferapenaltyrangingfromsuspensionforoneweektoonemonth
d.
Usingmorethanonecomputerterminalatatime,unlessspecificallyauthorizedbycompetent
authority.Facultymemberswhosedutiesrequiretheuseofmorethanonecomputershallbe
exempted.Violatorsshallsufferapenaltyrangingfromsuspensionforoneweektooneyear
e.
Lockingpublicaccesscomputersusingscreensaversorotherwise,unlessspecificallyauthorized
bycompetentauthorityviolatorsshallsufferapenaltyrangingfromsuspensionforoneweekto
onemonth
f.
Notloggingoutofthesystemtoallowotheruserstomakeuseofthepublicaccesscomputer
violatorsshallsufferapenaltyrangingfromsuspensionforoneweektoonemonthand
g.
UsingaservicewhichhasbeenidentifiedbytheSystemAdministratorascausinganexcessive
amountoftrafficontheITSystemoritsexternalnetworklinksviolatorsshallsufferapenalty
rangingfromsuspensionforoneweektooneyear.
Offensivematerial.
a.
UsersmaynotusethefacilitiesoftheITSystemtoproduce,disseminate,ordisplaymaterial
thatcouldbeconsideredoffensive,pornographic,raciallyabusive,orlibelousinnature.
b.
Usersmaynotuseelectroniccommunicationfacilities(suchasmail,chat,orsystemswithsimilar
functions)tosendmessageswhicharefraudulent,maliciouslyharassing,obscene,threatening,or
inviolationoflaws,administrativerulesandregulations,orotherpoliciesoftheUniversity
Systemoritsconstituentuniversities(CU).Violatorsshallsufferapenaltyrangingfrom
suspensionforonemonthtoexpulsionordismissal.
Inappropriatemessages.Usersmaynotsendtoamailinglist,includinglocalornetworknewsgroups
andbulletinboards,anyunsolicitedmaterialinconsistentwiththelist'spurpose.Usersofanelectronic
mailinglistareresponsiblefordeterminingthepurposeofthelistbeforesendingmessagestoor
receivingmessagesfromthelist.Subscriberstoanelectronicmailinglistaredeemedtohavesolicited
anymaterialdeliveredbythelistthatisconsistentwiththelist'spurpose.Violatorsshallsuffera
penaltyrangingfromsuspensionforoneweektoonemonth.
UseswhichViolatePrivacy
1.
Confidentialinformation.
a.
mail.up.edu.ph/local/files/aup.html
Unlessproperlyauthorized,usersmaynotattempttogainaccesstoarchivesorsystemsthat
contain,process,ortransmitconfidentialinformation.Authorizedusersmaynotexceedtheir
approvedlevelsofaccess,norshouldtheydiscloseconfidentialinformationtoothers.
3/5
4/10/12
Acceptable Use Policy
b.
Usersshalltreatasconfidentialsuchinformationwhichmaybecomeavailabletothemthrough
theuseoftheITSystem,whetherintentionallyoraccidentally.Usersmaynotcopy,modify,
disseminate,orusesuchinformation,eitherinwholeorinpart,withoutthepermissionofthe
personorbodyentitledtogiveit.Violatorsshallsufferapenaltyrangingfromsuspensionforone
yeartoexpulsionordismissal.
2.
Encryptedinformation.Usersshallconsiderasconfidentialallencryptedinformation.Thisincludesbutis
notlimitedtopasswords,digitalkeysandsignatures.Usersmaynotdecrypt,attempttodecrypt,or
enableotherstodecryptsuchinformationiftheyarenottheintendedrecipient.Violatorsshallsuffera
penaltyrangingfromsuspensionforoneyeartoexpulsionordismissal.
3.
Informationbelongingtoothers.Usersmaynotintentionallyseekorprovideinformationon,obtain
copiesof,ormodifyfiles,programs,orpasswordsbelongingtootherusers,withoutthepermissionof
thoseotherusers.Violatorsshallsufferapenaltyrangingfromsuspensionforonemonthtoexpulsionor
dismissal.
4.
Wiretapping,trafficcaptureandsnooping.Unlessproperlyauthorized,usersmaynotrerouteorcapture
datatransmittedovertheITSystem.Violatorsshallsufferapenaltyrangingfromsuspensionforone
yeartoexpulsionordismissal.
vi
Inadditiontothepenaltiesprovided,allITprivilegesoftheoffendermaybesuspendedforamaximumofthe
periodofthepenalty.Iftheviolationamountstoapenaltypunishablebyexpulsionordismissal,ITprivileges
mayberevokedpermanently.
vii
repeatedviolationsofanyoftheactsproscribedunderthispolicyshallbeconsideredasgrossmisconduct.
Section7.ToleratedUse
Fromtimetotime,theUPSYSTEMoritsconstituentuniversitiesmayissuealistclassifyingcertaintypesofuseunderthe
categoryoftolerateduse.ThislistshallformpartofthisPolicyandwillbeconsideredbindingonallusers.Usersshould
consulttheirsystemandnetworkadministratorsiftheyarenotsurewhetheracertaintypeofuseisconsideredallowed,
tolerated,unacceptableorprohibited.
Section8.EnforcementProcedures
(a)
Monitoring.TheUPSYSTEMoritsconstituentuniversitiesmaymonitoralluseoftheITSystematalltimesasmay
benecessaryforitspropermanagement.ActivitiesontheITSystemmaybeautomaticallyand/orcontinuously
logged.Systemandnetworkadministratorsmayexaminetheselogsanytime.Alllogsshallbeconsidered
confidential.
(b)
AccesstoPrivateFiles.TheUPSYSTEMmayaccessallaspectsoftheITSystem,includingprivatefiles,withoutthe
consentoftheuser,inthefollowinginstances:
(i)
Whennecessarytoidentifyordiagnosesystemsorsecurityvulnerabilitiesandproblems,orotherwisepreserve
theintegrity,reliability,availability,confidentialityandefficiencyoftheITSystem
(ii)
WhensuchaccesstotheITSystemisrequiredtocarryoutessentialbusinessfunctionsoftheUPSYSTEM
(iii)
WhennecessarytoavoiddisreputetotheUPSYSTEM
(iv)
WhentherearereasonablegroundstobelievethataviolationoflaworasignificantbreachofthisPolicyor
anyotherpolicyoftheUPSYSTEMmayhavetakenplace,andthataccessandinspectionmayproduce
evidencerelatedtothemisconduct
(v)
Whenrequiredbylaworadministrativerulesorcourtorderor
(vi)
Whenrequiredtopreservepublichealthandsafety.TheUPSYSTEMwillaccessprivatefileswithoutthe
consentoftheuseronlywiththeapprovaloftheChancellorexceptwhenanemergencyentryisnecessaryto
preservetheintegrity,reliability,availability,confidentialityandefficiencyoftheITSystemortopreserve
publichealthandsafety.TheUPSYSTEMthroughthesystemandnetworkadministratorswilldocumentall
instancesofaccesswithoutconsent.
(c)
ReportingProblemsandmisuse.Usersmustreporttotheappropriatesystemadministratorsanydefectsdiscoveredin
systemaccountingorsystemsecurity,allknownorsuspectedabuseormisuseoftheITSystem,andespeciallyany
damagetoorproblemswiththeirfacilitiesorfiles.
(d)
UserCooperation.Users,whenrequested,areexpectedtocooperatewithUPSYSTEMinanyinvestigationofIT
systemabuse.
(e)
GuidelinesforImmediateAction.
(f)
(i)
Notification.Whenanysystemadministratorormemberofthefacultyorstaffhaspersuasiveevidenceof
abuseormisuseoftheITSystem,andifthatevidencepointstotheactivitiesorthefilesofanindividual,he
orsheshall,within24hoursofthediscoveryofthepossiblemisuse,notifytheChancellororhis/herduly
designatedauthority.
(ii)
Suspension.Insuchcases,thesystemadministratormaytemporarilysuspendorrestricttheuser'saccess
privilegesforaperiodnotexceeding72hours.Ausermayappealsuchsuspensionorrestrictionandpetition
forimmediatereinstatementofprivilegesthroughtheChancellororhis/herdulydesignatedauthority.The
Chancellormayextendthesuspensionforthirty(30)days.
(iii)
Removal.Inaddition,insuchcases,thesystemadministratormayimmediatelyremoveoruninstallfromthe
ITSystemanymaterial,softwareorhardwarewhichposesanimmediatethreattotheintegrity,reliability,
availability,confidentialityandefficiencyoftheITSystemoranyofitscomponentsoriftheusemightbe
contrarytothisPolicy.Theusershallbenotifiedoftheactiontaken.Ausermayappealsuchremovaland
petitionforreinstatementofthematerialwithinfifteen(15)daysfromremoval.
Investigation.Theinvestigationandprosecutionofacademicandadministrativepersonnelandstudentsshallbein
accordancewiththeregulationsoftheUPSYSTEM.Theinvestigatingcommittee,bodyortribunalmusthaveatleast
onememberknowledgeableaboutIT.Theactionstheproperofficermayundertakeincludebutarenotlimitedtothe
following:
(i)
Extendthesuspensionorrestrictionofauser'sprivilegesforthedurationoftheinvestigation,orasmaybe
deemednecessarytopreserveevidenceandprotectthesystemanditsusers
(ii)
Callandinterviewpotentialwitnessesand
(iii)
Summonthesubjectofthecomplainttoprovideinformation.
(g)
FilingofCriminalCharges.Incaseswherethereisevidenceofseriousmisconductorpossiblecriminalactivity,the
Chancellorshallfiletheappropriatecriminalchargeswiththepropercourts.Whereproceedingshavebeeninstituted
againstauserforviolationofthisPolicy,theChancellormayindefinitelysuspendorrestricttheuser'saccess
privilegesforthedurationofsuchproceedings.
(h)
CumulativeRemedies.TheproceduresunderthisPolicyshallnotexcludeanyotherremedyavailabletoanyinjuredor
interestedpartyunderanyrelevantlaw,administrativeruleorregulation,orotherpolicyoftheUPSYSTEM.
(i)
ExternalLegalProcesses.TheUPSYSTEMshallcomplywithanylawfulordertoprovideelectronicorotherrecordsor
otherinformationrelatedtothoserecordsorrelatingtouseoftheITSystemwhichmayresultfromcoercive
processesinadministrativeinvestigations,orjudicialactionsorproceedings.
Section9.Waiver
(a)
LossofData.Usersrecognizethatsystemsandnetworksareimperfectandwaiveanyclaimforlostworkortime
mail.up.edu.ph/local/files/aup.html
4/5
4/10/12
Acceptable Use Policy
thatmayarisefromtheuseoftheITSystem.TheUPSYSTEMshallnotbeliablefordegradationorlossofpersonal
data,software,orhardwareasaresultoftheiruseoftheITSystem.
(b)
Authorization.UsersrecognizethattheUPSYSTEMprovidesaccesstotheITSystemonlyasaprivilegeandnota
rightthattheyhavenorighttouseitforanypurposeotherthanthosedirectlyconnectedwiththeworkoftheUP
SYSTEMandthattheUPSYSTEMmaytakewhatevermeasuresitdeemsnecessarytoenforcethis.Userstherefore
waiveanyactiontheymayhaveagainsttheUPSYSTEMunderanylaworadministrativeruleorregulationforanyact
theUPSYSTEMundertakesunderthisPolicy,specificallyincluding,butnotlimitedto,thoseactsenumeratedunder
Section7hereof.
mail.up.edu.ph/local/files/aup.html
5/5
Das könnte Ihnen auch gefallen
- Shoe Dog: A Memoir by the Creator of NikeVon EverandShoe Dog: A Memoir by the Creator of NikeBewertung: 4.5 von 5 Sternen4.5/5 (537)
- PDokument30 SeitenPJihan PacerNoch keine Bewertungen
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeVon EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeBewertung: 4 von 5 Sternen4/5 (5795)
- Lecture 2.0 - Introduction To LRFD Bridge DesignDokument51 SeitenLecture 2.0 - Introduction To LRFD Bridge DesignJihan PacerNoch keine Bewertungen
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceVon EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceBewertung: 4 von 5 Sternen4/5 (895)
- References For Thesis ProposalDokument6 SeitenReferences For Thesis ProposalJihan PacerNoch keine Bewertungen
- The Yellow House: A Memoir (2019 National Book Award Winner)Von EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Bewertung: 4 von 5 Sternen4/5 (98)
- 0 DegreesDokument97 Seiten0 DegreesJihan PacerNoch keine Bewertungen
- Grit: The Power of Passion and PerseveranceVon EverandGrit: The Power of Passion and PerseveranceBewertung: 4 von 5 Sternen4/5 (588)
- DesignDokument3 SeitenDesignJihan PacerNoch keine Bewertungen
- The Little Book of Hygge: Danish Secrets to Happy LivingVon EverandThe Little Book of Hygge: Danish Secrets to Happy LivingBewertung: 3.5 von 5 Sternen3.5/5 (400)
- Lecture 9 Intro To Finite Element Method Part 2Dokument32 SeitenLecture 9 Intro To Finite Element Method Part 2Jihan PacerNoch keine Bewertungen
- The Emperor of All Maladies: A Biography of CancerVon EverandThe Emperor of All Maladies: A Biography of CancerBewertung: 4.5 von 5 Sternen4.5/5 (271)
- CP 9. EXAMPLES Particle Kinetics-Force Inertia MethodDokument2 SeitenCP 9. EXAMPLES Particle Kinetics-Force Inertia MethodJihan PacerNoch keine Bewertungen
- Never Split the Difference: Negotiating As If Your Life Depended On ItVon EverandNever Split the Difference: Negotiating As If Your Life Depended On ItBewertung: 4.5 von 5 Sternen4.5/5 (838)
- Complex Fourier Series PDFDokument15 SeitenComplex Fourier Series PDFJihan PacerNoch keine Bewertungen
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyVon EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyBewertung: 3.5 von 5 Sternen3.5/5 (2259)
- Intro To PdesDokument16 SeitenIntro To PdesJihan PacerNoch keine Bewertungen
- On Fire: The (Burning) Case for a Green New DealVon EverandOn Fire: The (Burning) Case for a Green New DealBewertung: 4 von 5 Sternen4/5 (74)
- CP 5Dokument2 SeitenCP 5Jihan PacerNoch keine Bewertungen
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureVon EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureBewertung: 4.5 von 5 Sternen4.5/5 (474)
- Che 413 - Environmental Engineering: Submitted By: Pacer, Judea SDokument11 SeitenChe 413 - Environmental Engineering: Submitted By: Pacer, Judea SJihan PacerNoch keine Bewertungen
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryVon EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryBewertung: 3.5 von 5 Sternen3.5/5 (231)
- Exercises PHYSICSDokument2 SeitenExercises PHYSICSJihan PacerNoch keine Bewertungen
- Team of Rivals: The Political Genius of Abraham LincolnVon EverandTeam of Rivals: The Political Genius of Abraham LincolnBewertung: 4.5 von 5 Sternen4.5/5 (234)
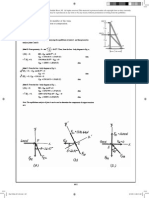
- Name: Date: SN: Quiz 4: D-K Transformation Prove That The Flexibility Matrix For The Given Beam Below IsDokument2 SeitenName: Date: SN: Quiz 4: D-K Transformation Prove That The Flexibility Matrix For The Given Beam Below IsJihan PacerNoch keine Bewertungen
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaVon EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaBewertung: 4.5 von 5 Sternen4.5/5 (266)
- B, (B) The Number of Revolutions Executed byDokument2 SeitenB, (B) The Number of Revolutions Executed byJihan PacerNoch keine Bewertungen
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersVon EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersBewertung: 4.5 von 5 Sternen4.5/5 (345)
- Review ProblemsDokument3 SeitenReview ProblemsJihan PacerNoch keine Bewertungen
- 2010 Besavilla Transportation Engineering PDFDokument8 Seiten2010 Besavilla Transportation Engineering PDFJihan PacerNoch keine Bewertungen
- The Unwinding: An Inner History of the New AmericaVon EverandThe Unwinding: An Inner History of the New AmericaBewertung: 4 von 5 Sternen4/5 (45)
- Art Man and Society (Symbolism)Dokument6 SeitenArt Man and Society (Symbolism)Jihan PacerNoch keine Bewertungen
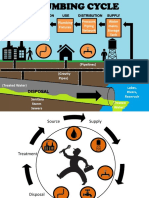
- Water Source: Sewage Plants Gravity Piping Networks Plumbing Fixtures Pressure, Piping Network Water Mains, Storage TankDokument2 SeitenWater Source: Sewage Plants Gravity Piping Networks Plumbing Fixtures Pressure, Piping Network Water Mains, Storage TankJihan PacerNoch keine Bewertungen
- Voiding Taxation: Judea Pacer BSCE 2-1Dokument10 SeitenVoiding Taxation: Judea Pacer BSCE 2-1Jihan PacerNoch keine Bewertungen
- B, (B) The Number of Revolutions Executed byDokument2 SeitenB, (B) The Number of Revolutions Executed byJihan PacerNoch keine Bewertungen
- The Sea Trading System: PresentsDokument12 SeitenThe Sea Trading System: PresentsAmmar Adli100% (2)
- FASH2000 Garment and The Body Semester 1 2022 Bentley Perth Campus INTDokument14 SeitenFASH2000 Garment and The Body Semester 1 2022 Bentley Perth Campus INTArchVFXNoch keine Bewertungen
- (Contemporary Topics in Entomology Series) Stefan Jarau, Michael Hrncir-Food Exploitation by Social Insects - Ecological, Behavioral, and Theoretical Approaches-CRC Press (2009)Dokument345 Seiten(Contemporary Topics in Entomology Series) Stefan Jarau, Michael Hrncir-Food Exploitation by Social Insects - Ecological, Behavioral, and Theoretical Approaches-CRC Press (2009)Hasmin BarilNoch keine Bewertungen
- Nationalism and Labor MovementDokument266 SeitenNationalism and Labor MovementIrfan KokdasNoch keine Bewertungen
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreVon EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreBewertung: 4 von 5 Sternen4/5 (1090)
- HP M602 CPMDDokument202 SeitenHP M602 CPMDLarry LinchNoch keine Bewertungen
- Our Invisible SupplyDokument177 SeitenOur Invisible SupplystanjessicaNoch keine Bewertungen
- Guidance On A Blended Approach To Auditing of MSDokument10 SeitenGuidance On A Blended Approach To Auditing of MSketanmsNoch keine Bewertungen
- Siebel Applications Administration Guide: Version 8.1, Rev. B December 2010Dokument476 SeitenSiebel Applications Administration Guide: Version 8.1, Rev. B December 2010Raveendra ReddyNoch keine Bewertungen
- EMPOWERMENT-TECHNOLOGIES-Q3-M1-M5 (1) GasDokument39 SeitenEMPOWERMENT-TECHNOLOGIES-Q3-M1-M5 (1) GasAngel PicazoNoch keine Bewertungen
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Von EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Bewertung: 4.5 von 5 Sternen4.5/5 (121)
- AEQQ MAA 32T32R 192AE n78 200W DatasheetDokument8 SeitenAEQQ MAA 32T32R 192AE n78 200W DatasheetporcariuirinelNoch keine Bewertungen
- Marc 2010 User's GuideDokument1.946 SeitenMarc 2010 User's GuideDan Wolf100% (1)
- Third Party NoticesDokument10 SeitenThird Party NoticesAndriu MolinaNoch keine Bewertungen
- Winglink 2-01 01Dokument256 SeitenWinglink 2-01 01Edna MariaNoch keine Bewertungen
- 1830-The Code of Terpsichore The Art of Dancing, Tr. by R. BartonDokument653 Seiten1830-The Code of Terpsichore The Art of Dancing, Tr. by R. BartonStivenNoch keine Bewertungen
- The Good Girls Guide To Being A DCK The Art of Saying What You Want and Getting The Life You Deserve by Alexandra ReinwarthDokument119 SeitenThe Good Girls Guide To Being A DCK The Art of Saying What You Want and Getting The Life You Deserve by Alexandra ReinwarthaniacgNoch keine Bewertungen
- ASM 12cDokument304 SeitenASM 12cFrank Hack100% (2)
- Her Body and Other Parties: StoriesVon EverandHer Body and Other Parties: StoriesBewertung: 4 von 5 Sternen4/5 (821)
- Jizi and His Art in Contemporary China - Unification - David Adam Brubaker, Chuchen WangDokument162 SeitenJizi and His Art in Contemporary China - Unification - David Adam Brubaker, Chuchen WangMadhuri RaoNoch keine Bewertungen
- Freedom of Information - Information Request FOI - 3311Dokument4 SeitenFreedom of Information - Information Request FOI - 3311api-308014349Noch keine Bewertungen
- GMR v. One PuttDokument16 SeitenGMR v. One PuttBillboardNoch keine Bewertungen
- Sejal Choudhary - 18010351 - IPR Research PaperDokument10 SeitenSejal Choudhary - 18010351 - IPR Research PaperThe JindalNoch keine Bewertungen
- Alan Kreider - Testimony As Sharing Hope, A Sermon On Matthew 8 VV 5 A 13Dokument10 SeitenAlan Kreider - Testimony As Sharing Hope, A Sermon On Matthew 8 VV 5 A 13Eliceo Saavedra Rios100% (1)
- Cultural Influences On Personality-TriandisDokument28 SeitenCultural Influences On Personality-TriandisLuz María Cruz MartínezNoch keine Bewertungen
- Thomé H. Fang, Tang Junyi and The Appropriation of Huayan ThoughtDokument223 SeitenThomé H. Fang, Tang Junyi and The Appropriation of Huayan Thoughtfede_mina130100% (1)
- Psychologist As Detective An Introduction To Conducting 6th Edition Smith Test BankDokument36 SeitenPsychologist As Detective An Introduction To Conducting 6th Edition Smith Test Bankmoldwarp.collumgn81100% (16)
- Solutions Simple TrussesDokument45 SeitenSolutions Simple Trussesmiahpangxie50% (2)
- BenchMark Ultra Advanced Staining Operator Guide PDFDokument322 SeitenBenchMark Ultra Advanced Staining Operator Guide PDFGamal Abdel MoityNoch keine Bewertungen
- An Analysis of The Effect of Procurement ProcedureDokument12 SeitenAn Analysis of The Effect of Procurement ProcedureImane SassaouiNoch keine Bewertungen
- LifeCycle Designer ScriptingReferenceDokument442 SeitenLifeCycle Designer ScriptingReferenceaurber2013Noch keine Bewertungen
- 0001 Codebook PDFDokument347 Seiten0001 Codebook PDFJulia FioreNoch keine Bewertungen
- 10979C ENU TrainerHandbookDokument166 Seiten10979C ENU TrainerHandbookAlfio SaglimbeniNoch keine Bewertungen
- OSCP Offensive Security Certified Professional Practice Tests With Answers To Pass the OSCP Ethical Hacking Certification ExamVon EverandOSCP Offensive Security Certified Professional Practice Tests With Answers To Pass the OSCP Ethical Hacking Certification ExamNoch keine Bewertungen
- The Internet Con: How to Seize the Means of ComputationVon EverandThe Internet Con: How to Seize the Means of ComputationBewertung: 5 von 5 Sternen5/5 (6)