Beruflich Dokumente
Kultur Dokumente
Ollydump Oep
Hochgeladen von
jaiswalnilesh5132Originalbeschreibung:
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Ollydump Oep
Hochgeladen von
jaiswalnilesh5132Copyright:
Verfügbare Formate
MUP With OllyDbg for Really Beginner
TARGET = Crackme #1;-)- coded for this tute (download target here)
DIFF = 1/10
TOOLS USED = OllyDbg 1.09b + OllyDump v2.01.108 plugin, LordPE (optional)
Requirement = PE Knowledge
AUTHOR = Zephyrous
Intro
This is my 2nd tutorial for BiW-Reversing that will discuss about MUP with ollydbg + ollydump. BTW, my 2nd
should be about the truth lies behind a keygen. But i need more time to get as much as ideas to discuss about it
deeply. For this tute, i just want to unpack UPXed file and as a bonus, FSG 1.33 packed one. I assume the reade
a little knowledge about PE like Entry Point (EP), Original Entry Point (OEP) in packed PE executables. BTW,
want to recommend you to read 'Peering Inside the PE: A Tour of the Win32 Portable Executable File Format' b
Matt Pietrek, but other manual/docs about PE also recommended to read (and to learn too :P).
Let start the game
Dont waste the time, open crackme.upx.exe (11, 776 bytes) included with this tute. Unfortunately, olly will ask
about the file because it is packed/compressed. At this time, just click yes to continue our job. As we want, olly
stop at EP of the packed exe. EP is offset where the code that to be executed just after program loaded. Is it clea
to show it more clear, you can check the EP with any PE editor, i used LordPE by y0da.
The Basic of Finding OEP and Dumping and rebIT.
After a PE .exe has been packed/compressed, the original code is not available until the decompress/decrypt rou
take over the program flow. The problem of manual unpacking (MUP) .exe protector(read: Asprotect, Armadill
Safedics, Securerom, etc) is to find where is the OEP that came from original .exe yet dealing with anti-debuggi
anti-tracing, encryption, etc in the protection too. We're lucky because UPX has nothing to do with any protectio
against unpacking.
At the EP (RVA: 00408160) you can just scroll down the piece of decompress code to find the OEP, unless you
to reverse the decompression routine of UPX ;-). OK, i dont want to wait for you, just scroll down until you fou
the OEP. It's to easy to find OEP for UPX, isn't it?
Maybe you have a question how i can find where to set the breakpoint. The answer is 'Practice make perfect' an
'trial and error'.
004082AF .-E9 0C90FFFF JMP crackme_.004012C0
;4012C0 is offset of the OEP, we found it du
At this offset, toggle breakpoint because we dont want to trace the decompress routine of it. Then press F9 or 'P
button.
As we want to, olly will break here. Just press F8 to continue execution to the OEP.
004012C0
004012C1
004012C3
004012C5
004012CA
55
8BEC
6A FF
68 F8404000
68 F41D4000
PUSH EBP
; you will stop here, 12C0 is the OEP
MOV EBP,ESP
PUSH -1
PUSH crackme_.004040F8
PUSH crackme_.00401DF4
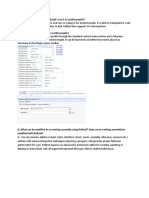
Now, we at the OEP, and we just have to dump the program with OllyDump. You will find OllyDump in 'Plugin
you installed it correctly :P.
Just choose 'Dump debugged process' because we had traced the routine manually, so tracer came with OllyDum
useless now.
Just leave all default setting because OllyDump will dump the program automatically for you including the Imp
Table rebuilding.
But its ok to learn how to rebuild IAT manually ;-).
Why? Because you're one of the reversers in the world.
What are you waiting for??? Just press 'Dump' and i want to go to class sooner.
Heh, i forgot something, if you dont satisfied with size of unpacked .exe, just rebuild it with any PE tools.
Damn!!! I'm too sleepy to go to class. Gud Nite Dude.
Yet Another Exercise for You.
Gud Morning All.
Just come back from class.
Included with this tute, another FSG v1.33 by dulek packed .exe.
You can analyze the decompression routine to find the OEP or simply just using OllyDump Tracing feature.
Just load keygenme.fsg.exe (4,288 bytes). small enough eh ;-).
Dont press anything yet, choose 'Find OEP by Section Hop (Trace Over)' or (Trace Into).
I think Trace Over is faster but Trace Into is safer. Am i right?
Just wait and see.
After the tracer found the OEP, Olly will break and this time you may dump it succesfully, using OLLYDUMP.
Outro
OllyDbg has a lot of features to offer to coders/reversers. Just doing some experiments or at least just 'playin
around with this damn good tool.
For example, you should inspect what olly had offered in View menu like Executable Moduls, Windows, Mem
Handles, etc.
You right mouse button will help you a lot ;-)
Greetings and respects: (not in specific order)
Oleh Yuschuk (OllyDbg), Gigapede (OllyDump), and y0da (rebIT.dll, LordPE, etc) - Thanx A Lot.
Ancient_One, Kwai_Lo, Bengaly, snaker (for teaching me UPX MUP), fuss, Detten, chainie, evileuA or clues
BiW-Reversing team, Bor0, X-Lock, and all reversers out there.
Real Life words:
"Reversing doesnt feed your stomach" - by a friend.
But reversing help you a lot in coding ;-)
I could be reached at r_etarded(at)yahoo(dot)com
6:58 p.m / 23 June 2003
biw.rult.at
Das könnte Ihnen auch gefallen
- Unpacking With UPXDokument23 SeitenUnpacking With UPXpatelpratik1972Noch keine Bewertungen
- Unprotecting The Crypter A Generic Approach: Author:Arunpreet SinghDokument17 SeitenUnprotecting The Crypter A Generic Approach: Author:Arunpreet Singhdogla88Noch keine Bewertungen
- Mup Molebox Pro 2.6.0.2375: by ColdfeverDokument8 SeitenMup Molebox Pro 2.6.0.2375: by ColdfeverJhwazkdNoch keine Bewertungen
- Unpacking DotFix NiceProtect v2 2 (TallfaZ)Dokument16 SeitenUnpacking DotFix NiceProtect v2 2 (TallfaZ)JhwazkdNoch keine Bewertungen
- Unpack Asprotect 2.xDokument1 SeiteUnpack Asprotect 2.xtigo2009Noch keine Bewertungen
- Unpacking CrypToCrackPeProtector v0 9 3 (TallfaZ)Dokument9 SeitenUnpacking CrypToCrackPeProtector v0 9 3 (TallfaZ)JhwazkdNoch keine Bewertungen
- Patching A Serial Using The BitmapsDokument12 SeitenPatching A Serial Using The BitmapsVuPhanNoch keine Bewertungen
- Tutorial #3 - Using OllyDBG - Part 1Dokument11 SeitenTutorial #3 - Using OllyDBG - Part 1gorazdboneid6129Noch keine Bewertungen
- Mup Drony Protect 3.0 & Luck007: by by by by Coldfever Coldfever Coldfever ColdfeverDokument6 SeitenMup Drony Protect 3.0 & Luck007: by by by by Coldfever Coldfever Coldfever ColdfeverJhwazkdNoch keine Bewertungen
- Python Programming Reference Guide: A Comprehensive Guide for Beginners to Master the Basics of Python Programming Language with Practical Coding & Learning TipsVon EverandPython Programming Reference Guide: A Comprehensive Guide for Beginners to Master the Basics of Python Programming Language with Practical Coding & Learning TipsNoch keine Bewertungen
- Crack MeDokument6 SeitenCrack MeJoe ProloNoch keine Bewertungen
- Aika SEA ASProtect Manual UnpackingDokument18 SeitenAika SEA ASProtect Manual Unpackingjaiswalnilesh5132Noch keine Bewertungen
- How To Disassemble A Program With IDADokument9 SeitenHow To Disassemble A Program With IDASpèedy JoesNoch keine Bewertungen
- Lab 1: Blink BlinkDokument5 SeitenLab 1: Blink BlinkBoo BoyolqNoch keine Bewertungen
- Little TextDokument4 SeitenLittle TextxuboyuansiquanNoch keine Bewertungen
- Bypassing A Serial in A Delphi Program by XOR06Dokument8 SeitenBypassing A Serial in A Delphi Program by XOR06VuPhanNoch keine Bewertungen
- Write Game 01Dokument25 SeitenWrite Game 01Kurnia BagoesdwNoch keine Bewertungen
- UD Methods1Dokument7 SeitenUD Methods1NightRang3rNoch keine Bewertungen
- Arduino Setup Guide For Otto RobotsDokument35 SeitenArduino Setup Guide For Otto RobotstoptenacademyNoch keine Bewertungen
- Unpacking - MoleBox.v2.6. (Extracting Embedded Files) - (ColdFeveDokument14 SeitenUnpacking - MoleBox.v2.6. (Extracting Embedded Files) - (ColdFeveJhwazkdNoch keine Bewertungen
- How To Repair Your USB Flash DriveDokument6 SeitenHow To Repair Your USB Flash DriveEarlNoch keine Bewertungen
- Basic Buffer Overflows ExplainedDokument14 SeitenBasic Buffer Overflows ExplainedGridmark100% (2)
- Exploit Writing Tutorial Part1 Stack Based OveflowsDokument15 SeitenExploit Writing Tutorial Part1 Stack Based OveflowsJonny KookoovigasNoch keine Bewertungen
- 5.a. Using AVR Studio 4: Next: 5.b. AVR Studio 4 in More Detail Previous: 5. Getting Started Using WindowsDokument3 Seiten5.a. Using AVR Studio 4: Next: 5.b. AVR Studio 4 in More Detail Previous: 5. Getting Started Using WindowsDipendra SenNoch keine Bewertungen
- Otto Blockly GuideDokument54 SeitenOtto Blockly Guideporsche6911Noch keine Bewertungen
- Real Hacking #3Dokument9 SeitenReal Hacking #3Abhishek KunalNoch keine Bewertungen
- 1.1.3 Explore The New Lab FeaturesDokument3 Seiten1.1.3 Explore The New Lab FeaturesrembrandtshiloahNoch keine Bewertungen
- WWW Ladyada Net Learn Arduino Lesson2 HTMLDokument7 SeitenWWW Ladyada Net Learn Arduino Lesson2 HTMLgui9871Noch keine Bewertungen
- Mouse As Joy TextDokument5 SeitenMouse As Joy TextWilliams NiloNoch keine Bewertungen
- Modern Windows Exploit DevelopmentDokument529 SeitenModern Windows Exploit DevelopmentJorge Cerda100% (3)
- BufferOverflowExploitation 17971Dokument15 SeitenBufferOverflowExploitation 17971alaska112Noch keine Bewertungen
- Bypassing A Keyfile by XOR06Dokument16 SeitenBypassing A Keyfile by XOR06VuPhanNoch keine Bewertungen
- Home of Bishoph Offline Voice ControlDokument130 SeitenHome of Bishoph Offline Voice ControlBai ToshoNoch keine Bewertungen
- Python Programming: 8 Simple Steps to Learn Python Programming Language in 24 hours! Practical Python Programming for Beginners, Python Commands and Python LanguageVon EverandPython Programming: 8 Simple Steps to Learn Python Programming Language in 24 hours! Practical Python Programming for Beginners, Python Commands and Python LanguageBewertung: 2 von 5 Sternen2/5 (1)
- Otto Blockly Guide PDFDokument51 SeitenOtto Blockly Guide PDFArtem SamoylenkoNoch keine Bewertungen
- Flexisign Pro Dongle CrackingDokument8 SeitenFlexisign Pro Dongle CrackingzeljkogrNoch keine Bewertungen
- Multiboot OpenELEC WindowsDokument8 SeitenMultiboot OpenELEC WindowsdidikkeNoch keine Bewertungen
- Programming RobotsDokument239 SeitenProgramming RobotsDeep Chaudhari100% (1)
- Enigma Alternativ UnpackerDokument4 SeitenEnigma Alternativ UnpackerxuboyuansiquanNoch keine Bewertungen
- Auto It Silent InstallDokument11 SeitenAuto It Silent InstallAgus CahzenenkNoch keine Bewertungen
- In Teory It EPROMDokument4 SeitenIn Teory It EPROMMade DuantaNoch keine Bewertungen
- SDS Cheatsheet For Python ErrorsDokument6 SeitenSDS Cheatsheet For Python ErrorsMD HUSSAIN MIRJINoch keine Bewertungen
- ASProtect VM AnalyzeDokument33 SeitenASProtect VM AnalyzegioruwreNoch keine Bewertungen
- Manual Unpacking of Upx Packed Executable Using Ollydbg and ImportrecDokument7 SeitenManual Unpacking of Upx Packed Executable Using Ollydbg and ImportrecInternational Organization of Scientific Research (IOSR)Noch keine Bewertungen
- ManualDokument97 SeitenManualdege88Noch keine Bewertungen
- Baithuchanh HDH1Dokument18 SeitenBaithuchanh HDH1yenlehai34Noch keine Bewertungen
- Install Scip yDokument6 SeitenInstall Scip yharshasbhatNoch keine Bewertungen
- Introduction To Exploit Development (Buffer Overflows) PDFDokument46 SeitenIntroduction To Exploit Development (Buffer Overflows) PDFRushikesh ThombreNoch keine Bewertungen
- Beginner Tips To Own Boxes at HackTheBox ! - Bug Bounty Hunting - MediumDokument11 SeitenBeginner Tips To Own Boxes at HackTheBox ! - Bug Bounty Hunting - Mediumamazokabali0% (1)
- Novo Dokument Programa Microsoft WordDokument23 SeitenNovo Dokument Programa Microsoft WordJosip ŠpoljarićNoch keine Bewertungen
- How Main Functions WorksDokument12 SeitenHow Main Functions Worksh309820956Noch keine Bewertungen
- Troubleshooting in LinuxDokument4 SeitenTroubleshooting in LinuxViorel AldeaNoch keine Bewertungen
- Portal Speedrun GuideDokument38 SeitenPortal Speedrun GuideBoba FettNoch keine Bewertungen
- Bug Hunting With American Fuzzy LoopDokument6 SeitenBug Hunting With American Fuzzy LoopHelen OtisNoch keine Bewertungen
- Installing PythonDokument45 SeitenInstalling PythonWaqas MurtazaNoch keine Bewertungen
- Nstructions For Setting Up A New Raspberry Pi OS and OpenCVDokument6 SeitenNstructions For Setting Up A New Raspberry Pi OS and OpenCVChrista SutharsanNoch keine Bewertungen
- Eeebuntu InstallationDokument10 SeitenEeebuntu InstallationRoman Rachkov100% (2)
- Ottoblockly ManualDokument53 SeitenOttoblockly ManualAudrey BerlianNoch keine Bewertungen
- Guide On How To Install Lion Dp1 (Build 11A390) On Lenovo Ideapad S10 and S10EDokument5 SeitenGuide On How To Install Lion Dp1 (Build 11A390) On Lenovo Ideapad S10 and S10EJorge RibeiroNoch keine Bewertungen
- Facility App User ManualDokument25 SeitenFacility App User Manualjaiswalnilesh5132Noch keine Bewertungen
- C++ OptimizeDokument4 SeitenC++ OptimizeVarun NagpalNoch keine Bewertungen
- f1396429480827 PDFDokument1 Seitef1396429480827 PDFMona AbisaadNoch keine Bewertungen
- Android TutorialDokument836 SeitenAndroid TutorialSheetaltwuNoch keine Bewertungen
- Post Graduate Program In: Pediatric NutritionDokument4 SeitenPost Graduate Program In: Pediatric Nutritionjaiswalnilesh5132Noch keine Bewertungen
- Q: What Is Reflexil and Why Should I Use It in Justdecompile?Dokument4 SeitenQ: What Is Reflexil and Why Should I Use It in Justdecompile?jaiswalnilesh5132Noch keine Bewertungen
- ASProtect 2.0 Import Recovery + Scrambled Code Recovery (Delphi & Imagebase 400000)Dokument8 SeitenASProtect 2.0 Import Recovery + Scrambled Code Recovery (Delphi & Imagebase 400000)jaiswalnilesh5132Noch keine Bewertungen
- PeSpin 1.3 Beta 2 (Private) DebugDokument3 SeitenPeSpin 1.3 Beta 2 (Private) Debugjaiswalnilesh5132Noch keine Bewertungen
- Guru Pooja StotramDokument7 SeitenGuru Pooja Stotramjaiswalnilesh5132100% (1)
- PeSpin 1.3 UnpackerDokument3 SeitenPeSpin 1.3 Unpackerjaiswalnilesh5132Noch keine Bewertungen
- Armadillo OEP Finder + Fix Magic Jumps + Fix Anti-DumpDokument3 SeitenArmadillo OEP Finder + Fix Magic Jumps + Fix Anti-Dumpjaiswalnilesh5132Noch keine Bewertungen
- Aika SEA ASProtect Manual UnpackingDokument18 SeitenAika SEA ASProtect Manual Unpackingjaiswalnilesh5132Noch keine Bewertungen
- Swaimans Pediatric Neurology 5edDokument2 SeitenSwaimans Pediatric Neurology 5edjaiswalnilesh5132Noch keine Bewertungen
- Albuterol Contraindications 1Dokument1 SeiteAlbuterol Contraindications 1jaiswalnilesh5132Noch keine Bewertungen
- GSTR1 Excel Workbook Template-V1.2Dokument40 SeitenGSTR1 Excel Workbook Template-V1.2jaiswalnilesh5132Noch keine Bewertungen
- EN-Manual-Epson L805 PDFDokument93 SeitenEN-Manual-Epson L805 PDFjaiswalnilesh5132Noch keine Bewertungen
- Ondansetron Contraindications 1Dokument1 SeiteOndansetron Contraindications 1jaiswalnilesh5132Noch keine Bewertungen
- Acetaaminophen Contraindications 1Dokument1 SeiteAcetaaminophen Contraindications 1jaiswalnilesh5132Noch keine Bewertungen
- Ws Tip Headers PDFDokument8 SeitenWs Tip Headers PDFTolga AkatNoch keine Bewertungen
- Method Hiding in C# - CodeProject PDFDokument6 SeitenMethod Hiding in C# - CodeProject PDFArun VijayNoch keine Bewertungen
- Vol 1 Chapter 1Dokument20 SeitenVol 1 Chapter 1MWANGI BRUCE FELIX MACHARIANoch keine Bewertungen
- Raj Mishra Training ReportDokument28 SeitenRaj Mishra Training ReportRAJ MISHRA RAJ MISHRANoch keine Bewertungen
- WPF TutorialDokument306 SeitenWPF TutorialNenad LackovicNoch keine Bewertungen
- @ITBooks4U SQL - 2 - Books - in - 1 PDFDokument92 Seiten@ITBooks4U SQL - 2 - Books - in - 1 PDFMuleNoch keine Bewertungen
- IT Crisisology: Smart Crisis Management in Software EngineeringDokument194 SeitenIT Crisisology: Smart Crisis Management in Software EngineeringkhNoch keine Bewertungen
- F (X) Cos (X) + 2 Sin (X) + X: CPE 202 - Numerical MethodsDokument4 SeitenF (X) Cos (X) + 2 Sin (X) + X: CPE 202 - Numerical Methodstae hoonNoch keine Bewertungen
- Java Language White PaperDokument8 SeitenJava Language White PaperReggeloNoch keine Bewertungen
- PDF of Instruction FormatDokument18 SeitenPDF of Instruction FormatSaGar MallaNoch keine Bewertungen
- Operating SystemDokument2 SeitenOperating SystemDreamtech PressNoch keine Bewertungen
- Top 25 Unix Interview Questions With AnswersDokument8 SeitenTop 25 Unix Interview Questions With Answerssanjay.gupta8194Noch keine Bewertungen
- 1D, 2D and Multi-Dimensional Arrays - ComputerSC PDFDokument49 Seiten1D, 2D and Multi-Dimensional Arrays - ComputerSC PDFParamartha BanerjeeNoch keine Bewertungen
- M251 Meeting 4Dokument39 SeitenM251 Meeting 4ray hajjarNoch keine Bewertungen
- Interrupts Interrupts: GoalsDokument8 SeitenInterrupts Interrupts: GoalsSreekanth PagadapalliNoch keine Bewertungen
- DBM Unit 3 - Sequence DiagramDokument35 SeitenDBM Unit 3 - Sequence DiagramDeepa ShelkeNoch keine Bewertungen
- PostGIS 1Dokument367 SeitenPostGIS 1Alvaro Dario Ramos TiradoNoch keine Bewertungen
- Assignment - 6 - Compiler DesignDokument3 SeitenAssignment - 6 - Compiler Designdheena thayalanNoch keine Bewertungen
- Excel Basic To Advanced CourseDokument13 SeitenExcel Basic To Advanced CourseHarish PechettiNoch keine Bewertungen
- Install Siesta Psml1Dokument15 SeitenInstall Siesta Psml1Ioan Mihail GhitiuNoch keine Bewertungen
- Modulo 8. Data Visualization With PythonDokument30 SeitenModulo 8. Data Visualization With Pythongia ferNoch keine Bewertungen
- Brandon Charles: EducationDokument1 SeiteBrandon Charles: EducationsamyoeNoch keine Bewertungen
- Number Based-Special Two Digit No 7th June21Dokument2 SeitenNumber Based-Special Two Digit No 7th June21Shailendra SinghNoch keine Bewertungen
- Design Engineering - Software DesignDokument84 SeitenDesign Engineering - Software DesignHarshavardhan Virendra MallaNoch keine Bewertungen
- Hands On Experience CH 6 To CH 10Dokument24 SeitenHands On Experience CH 6 To CH 10KavithaNoch keine Bewertungen
- Quiz s8Dokument10 SeitenQuiz s8a23mer1439Noch keine Bewertungen
- Kernel Configuration and Building in Linux PDFDokument18 SeitenKernel Configuration and Building in Linux PDFShah ShujaatNoch keine Bewertungen
- NCS Dummy - Taking The Expert Out of NCS Expert: FSW - PSW - TRC Nettodat - TRCDokument37 SeitenNCS Dummy - Taking The Expert Out of NCS Expert: FSW - PSW - TRC Nettodat - TRCadimaio_3dNoch keine Bewertungen
- S-DES:: Experiment: 4 AimDokument7 SeitenS-DES:: Experiment: 4 AimJaimishNoch keine Bewertungen
- Ocs PythonDokument13 SeitenOcs PythonkubowNoch keine Bewertungen