Beruflich Dokumente
Kultur Dokumente
Cyber Security Challenges
Hochgeladen von
sreehariCopyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Cyber Security Challenges
Hochgeladen von
sreehariCopyright:
Verfügbare Formate
Cyber Security Challenges
Enlarge
Cyberspace comprises IT networks, computer resources, and all the fixed and mobile
devices connected to the global Internet. A nations cyberspace is part of the global
cyberspace; it cannot be isolated to define its boundaries since cyberspace is borderless.
This is what makes cyberspace unique. Unlike the physical world that is limited by
geographical boundaries in spaceland, sea, river waters, and aircyberspace can and is continuing to
expand. Increased Internet penetration is leading to growth of cyberspace, since its size is proportional to
the activities that are carried through it.
Nations are investing heavily in their ICT infrastructures with a view to providing higher bandwidths,
integrate national economies with the global marketplace, and to enable citizens or netizens to access
more and more e-services.
Given the security problems, there is increased emphasis on, and investment in, the security of cyber
infrastructure. Core Internet protocols are insecure, and an explosion of mobile devices continues to be
based on the same insecure systems. This is adding up to increased usage of the Internet in more
vulnerable cyberspace.
Protection of critical infrastructure operations has emerged as a major challenge. This is because trillions of
dollars move through the networks every day involving a broad range of activities, including e-commerce, e-
governance, travel, hospitality, health care, and general communications. Electricity distribution, water
distribution, and several other utility services are based on ICT infrastructures. The defense sector relies
heavily on electronic systems.
Ownership and Responsibility
Critical infrastructure is largely owned and operated by the private sector. But is security only the private
sectors responsibility? Does this mean that government has a lesser role? These are some of the important
cybersecurity issues that nations are grappling with. At an organizational level, too, cybersecurity is not
merely a technology issue, but a management issue. This is grounded in enterprise risk management, which
calls for an understanding of the human, process, legal, network, and ICT security aspects.
It is obvious that multiple agencies are involved in securing ICT infrastructure. These include private
operators for their respective pieces of the infrastructure. Their efforts need to be firmly coordinated through
an integrated command-and-control entity, which should serve as a unifying structure that is accountable for
cybersecurity.
Roles and responsibilities of each of the parties need to be clearly defined. At the same time, governments
need to establish the appropriate policy and legal structures. Nations, such as the United States, have
advocated for a market-based, voluntary approach to industry cybersecurity as part of the National Strategy
to Secure Cyberspace. But this has not worked entirely, because security investments made by industry, as
per their corporate needs, are not found to be commensurate with the broader national interest. How will
the additional private investments be generated? Is there a case for government incentives, as part of an
incentive program to bridge the gap between those security investments already made and those additional
ones that are needed to secure critical infrastructure?
Several security surveys point to this need. They reveal a lack of adequate knowledge among executives
about security policy and incidents, the latest technological solutions, data leakage, financial loss, and the
training that is needed for their employees.
Since cyberspace is relatively new, legal concepts for standards of care do not exist. Is there a case for
governments to offer incentives to generate collective action? For example, they could provide reduced
liability or tax incentives as a trade off for improved security, new regulatory requirements, and compliance
mechanisms.12 Governments need to provide incentives for industry to invest in security at a level that is
not justified by corporate business plans.
Das könnte Ihnen auch gefallen
- Oasis 360 Overview 0710Dokument21 SeitenOasis 360 Overview 0710mychar600% (1)
- Information Security Handbook For EmployeesDokument13 SeitenInformation Security Handbook For EmployeesKarthikNoch keine Bewertungen
- Occupational Therapy in Mental HealthDokument16 SeitenOccupational Therapy in Mental HealthjethasNoch keine Bewertungen
- Cyber Security: Action Against Cyber CrimeDokument11 SeitenCyber Security: Action Against Cyber CrimeEducation Tech PoolNoch keine Bewertungen
- Atos Digital Vision For CybersecurityDokument32 SeitenAtos Digital Vision For CybersecuritypnorbertoNoch keine Bewertungen
- Cybersecurity Commission Report Final PostDokument100 SeitenCybersecurity Commission Report Final PostLuke R. Corde100% (1)
- CYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookVon EverandCYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookNoch keine Bewertungen
- CH 14Dokument34 SeitenCH 14Firas ZawaidehNoch keine Bewertungen
- CNS C 1Dokument23 SeitenCNS C 1Haritha100% (1)
- EMI-EMC - SHORT Q and ADokument5 SeitenEMI-EMC - SHORT Q and AVENKAT PATILNoch keine Bewertungen
- Sika Saudi Arabia: Safety Data SheetDokument4 SeitenSika Saudi Arabia: Safety Data Sheetusman khalid100% (1)
- Spare Parts ManagementDokument21 SeitenSpare Parts Managementdajit1100% (1)
- What Is Cybersecurity and Why It Is ImportantDokument22 SeitenWhat Is Cybersecurity and Why It Is ImportantOgieva ElvisNoch keine Bewertungen
- Multirate Signal Processing: I. Selesnick EL 713 Lecture NotesDokument32 SeitenMultirate Signal Processing: I. Selesnick EL 713 Lecture Notesboopathi123Noch keine Bewertungen
- Cencon Atm Security Lock Installation InstructionsDokument24 SeitenCencon Atm Security Lock Installation InstructionsbiggusxNoch keine Bewertungen
- Best Practices For Securing Computer NetworksDokument2 SeitenBest Practices For Securing Computer NetworksswvylNoch keine Bewertungen
- CYBERSECURITYDokument22 SeitenCYBERSECURITYmichellebulgar0Noch keine Bewertungen
- Lps - Config Doc of Fm-BcsDokument37 SeitenLps - Config Doc of Fm-Bcsraj01072007Noch keine Bewertungen
- Fortify Your Data: A Guide to the Emerging TechnologiesVon EverandFortify Your Data: A Guide to the Emerging TechnologiesNoch keine Bewertungen
- Safeguarding the Digital Fortress: A Guide to Cyber Security: The IT CollectionVon EverandSafeguarding the Digital Fortress: A Guide to Cyber Security: The IT CollectionNoch keine Bewertungen
- Defense Science Board: Resilient Military Systems & Cyber ThreatsDokument146 SeitenDefense Science Board: Resilient Military Systems & Cyber ThreatsJohn AndréNoch keine Bewertungen
- Cyber SecurityDokument48 SeitenCyber SecuritySuraj DasNoch keine Bewertungen
- Qatar National Information Assurance Framework IsmaelDokument24 SeitenQatar National Information Assurance Framework IsmaelkumarNoch keine Bewertungen
- Optimization of Crude Oil DistillationDokument8 SeitenOptimization of Crude Oil DistillationJar RSNoch keine Bewertungen
- Information Systems Security OfficerDokument19 SeitenInformation Systems Security OfficermabesninaNoch keine Bewertungen
- Ieee Cyber Security Using AiDokument4 SeitenIeee Cyber Security Using AiSandeep SutradharNoch keine Bewertungen
- Class 1: Security and Risk ManagementDokument24 SeitenClass 1: Security and Risk ManagementCapitan SwankNoch keine Bewertungen
- Cyber CrimeDokument17 SeitenCyber CrimeSanket BansalNoch keine Bewertungen
- AB103413 - Ch12 Privacy and SecurityDokument71 SeitenAB103413 - Ch12 Privacy and SecurityAnonymous mwW3vRT0rNoch keine Bewertungen
- Robotics Social RobotDokument5 SeitenRobotics Social RobotIJRASETPublicationsNoch keine Bewertungen
- Data Security in Local Network Using Distributed Firewall Seminar PresentationDokument28 SeitenData Security in Local Network Using Distributed Firewall Seminar PresentationTiju SinghNoch keine Bewertungen
- Unit-5 Cybersecurity: Organizational Implications: IV-II SEM CSE, Cyber Security Unit - VDokument13 SeitenUnit-5 Cybersecurity: Organizational Implications: IV-II SEM CSE, Cyber Security Unit - VLakshmi Narayana ReddyNoch keine Bewertungen
- Threat Report 1706163590Dokument47 SeitenThreat Report 1706163590banduuk1297Noch keine Bewertungen
- Cyber Security in 2021Dokument4 SeitenCyber Security in 2021Adeeba MuskanNoch keine Bewertungen
- Cyber Security PDFDokument5 SeitenCyber Security PDFSingh JagdishNoch keine Bewertungen
- Unit 38 DatabaseManagementSystDokument27 SeitenUnit 38 DatabaseManagementSystmomin nadeemNoch keine Bewertungen
- Role and Responsibilities of StakeholdersDokument7 SeitenRole and Responsibilities of StakeholdersSalma Ashraf gaberNoch keine Bewertungen
- Cyber Security and Policy: A substantive dialogueVon EverandCyber Security and Policy: A substantive dialogueNoch keine Bewertungen
- Cyber SecurityDokument22 SeitenCyber SecurityCarey HallNoch keine Bewertungen
- Project Report Titles For MBA in Information TechnologyDokument5 SeitenProject Report Titles For MBA in Information Technologyebrandingindia1Noch keine Bewertungen
- Cyber Security in AfricaDokument5 SeitenCyber Security in AfricaBlack Hat HackerNoch keine Bewertungen
- What Is Cyber Security?Dokument24 SeitenWhat Is Cyber Security?api-19653075Noch keine Bewertungen
- Cyber Threats and SecurityDokument17 SeitenCyber Threats and Securityno OneNoch keine Bewertungen
- Thwarting Attackers Defending Against Growing Security Sophistication While Managing ComplexityDokument18 SeitenThwarting Attackers Defending Against Growing Security Sophistication While Managing ComplexityducuhNoch keine Bewertungen
- Cyber Security Challenges - Praveen NayakDokument11 SeitenCyber Security Challenges - Praveen NayakPraveen NayakNoch keine Bewertungen
- ATTACK Design and Philosophy 2020Dokument46 SeitenATTACK Design and Philosophy 2020Free FoxNoch keine Bewertungen
- Cyber Espionage Threats - An Alarming Problem: White PaperDokument5 SeitenCyber Espionage Threats - An Alarming Problem: White PaperJuan Carlos Baron RinconNoch keine Bewertungen
- CSIC Cyber SecurityDokument52 SeitenCSIC Cyber SecurityMahendra Mandalapu100% (1)
- Cyber SecurityDokument13 SeitenCyber SecurityVinay BharwaniNoch keine Bewertungen
- OWASP Top 10 - Threats and MitigationsDokument54 SeitenOWASP Top 10 - Threats and MitigationsSwathi PatibandlaNoch keine Bewertungen
- Data Security: Block Ciphers and The Data Encryption StandardDokument12 SeitenData Security: Block Ciphers and The Data Encryption Standardapi-19822376Noch keine Bewertungen
- Certificate in Cyber Security Feb 2016Dokument3 SeitenCertificate in Cyber Security Feb 2016Waldon HendricksNoch keine Bewertungen
- Unit 3 CYBER SECURITY (AUC-002)Dokument15 SeitenUnit 3 CYBER SECURITY (AUC-002)PrachiNoch keine Bewertungen
- Malware Protection EbookDokument20 SeitenMalware Protection Ebookmarcelo santiniNoch keine Bewertungen
- Introduction To Cyber Security Chapter 4Dokument4 SeitenIntroduction To Cyber Security Chapter 4Pinoy Ako EntertainmentNoch keine Bewertungen
- Cyber Security BibliographyDokument6 SeitenCyber Security BibliographyhkingsmaNoch keine Bewertungen
- Nottingham Trent University Course SpecificationDokument8 SeitenNottingham Trent University Course SpecificationAk9850621267Noch keine Bewertungen
- Chapter OneDokument42 SeitenChapter OneMagarsa BedasaNoch keine Bewertungen
- Cyber Security BrochureDokument5 SeitenCyber Security BrochureShweta HosmaniNoch keine Bewertungen
- Cyber SecurityDokument4 SeitenCyber SecurityANoch keine Bewertungen
- Cyber Security: M. Kannan K. Sakthi VelDokument15 SeitenCyber Security: M. Kannan K. Sakthi VelcharlesmahimainathanNoch keine Bewertungen
- Syllabus For Diploma in Cyber SecurityDokument4 SeitenSyllabus For Diploma in Cyber SecurityppghoshinNoch keine Bewertungen
- Effect of Cyber Crime in Legal PracticeDokument2 SeitenEffect of Cyber Crime in Legal PracticeTwain JonesNoch keine Bewertungen
- Cloud Based SecurityDokument6 SeitenCloud Based SecurityEditor IJRITCCNoch keine Bewertungen
- Identifying and Mitigating Cyber Threats To Financial Systems - The MITRE CorporationDokument3 SeitenIdentifying and Mitigating Cyber Threats To Financial Systems - The MITRE CorporationSgt2Noch keine Bewertungen
- Cyber Forensic ArticleDokument6 SeitenCyber Forensic ArticleDeepika BansalNoch keine Bewertungen
- CISO Verification Form 1Dokument3 SeitenCISO Verification Form 1Hero KitaNoch keine Bewertungen
- PPT Ch03-Amr PDFDokument56 SeitenPPT Ch03-Amr PDFCharlito MikolliNoch keine Bewertungen
- PooriDokument15 SeitenPoorisreehariNoch keine Bewertungen
- RamyDokument2 SeitenRamysreehariNoch keine Bewertungen
- ATmega328 P PDFDokument442 SeitenATmega328 P PDFsreehariNoch keine Bewertungen
- BluetoothDokument14 SeitenBluetoothapi-26830587100% (1)
- Normal Consistency For GgbsDokument12 SeitenNormal Consistency For GgbssreehariNoch keine Bewertungen
- IeiDokument12 SeitenIeisreehariNoch keine Bewertungen
- Biomedical Signal Processing and ApplicationsDokument6 SeitenBiomedical Signal Processing and ApplicationssreehariNoch keine Bewertungen
- Multirate Digital Signal ProcessingDokument25 SeitenMultirate Digital Signal ProcessinghoangbabaoNoch keine Bewertungen
- Lecture 28: JPEG 2000 5/3 Filter-Bank and Spline MRADokument6 SeitenLecture 28: JPEG 2000 5/3 Filter-Bank and Spline MRAsreehariNoch keine Bewertungen
- Piecewise Constant Approximation and The Haar Wavelet: DT T X T T XDokument7 SeitenPiecewise Constant Approximation and The Haar Wavelet: DT T X T T XsreehariNoch keine Bewertungen
- Chapter 2 Digital Image CompressionDokument12 SeitenChapter 2 Digital Image CompressionKetan SharmaNoch keine Bewertungen
- Lecture 28: JPEG 2000 5/3 Filter-Bank and Spline MRADokument6 SeitenLecture 28: JPEG 2000 5/3 Filter-Bank and Spline MRAsreehariNoch keine Bewertungen
- SSG m6l17 PDFDokument12 SeitenSSG m6l17 PDFmanish 123Noch keine Bewertungen
- Kuppam Engineering College: Project TitleDokument15 SeitenKuppam Engineering College: Project TitlesreehariNoch keine Bewertungen
- 4 ScriptDokument7 Seiten4 ScriptsreehariNoch keine Bewertungen
- Department of Electronics and Communication Engineering: Kuppam Engineering College, Kuppam-517425Dokument10 SeitenDepartment of Electronics and Communication Engineering: Kuppam Engineering College, Kuppam-517425sreehariNoch keine Bewertungen
- Department of Electronics and Communication Engineering: Kuppam Engineering College, Kuppam-517425Dokument3 SeitenDepartment of Electronics and Communication Engineering: Kuppam Engineering College, Kuppam-517425sreehariNoch keine Bewertungen
- Department of Electronics and Communications Engineering: Kuppam Engineering College, Kuppam-517425Dokument1 SeiteDepartment of Electronics and Communications Engineering: Kuppam Engineering College, Kuppam-517425sreehariNoch keine Bewertungen
- Iv-Ii SemDokument11 SeitenIv-Ii SemsreehariNoch keine Bewertungen
- Normal Consistency For GgbsDokument12 SeitenNormal Consistency For GgbssreehariNoch keine Bewertungen
- HarDokument1 SeiteHarsreehariNoch keine Bewertungen
- Bonafide Certificate: Loon TechonologyDokument1 SeiteBonafide Certificate: Loon TechonologysreehariNoch keine Bewertungen
- Iris Recognition Using Less Expensive CameraDokument1 SeiteIris Recognition Using Less Expensive CamerasreehariNoch keine Bewertungen
- Resume::: Gunda Vinod Kumar Contact No IDDokument2 SeitenResume::: Gunda Vinod Kumar Contact No IDsreehariNoch keine Bewertungen
- IOTDokument5 SeitenIOTsreehariNoch keine Bewertungen
- RotationDokument18 SeitenRotationsreehariNoch keine Bewertungen
- The Sea BassDokument4 SeitenThe Sea BasssreehariNoch keine Bewertungen
- Wi-Vi TechnologyDokument21 SeitenWi-Vi Technologysreehari33% (3)
- Immovable Sale-Purchase (Land) ContractDokument6 SeitenImmovable Sale-Purchase (Land) ContractMeta GoNoch keine Bewertungen
- Jainithesh - Docx CorrectedDokument54 SeitenJainithesh - Docx CorrectedBala MuruganNoch keine Bewertungen
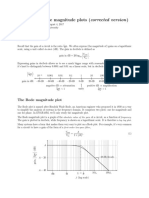
- Bode PlotsDokument6 SeitenBode PlotshasanozdNoch keine Bewertungen
- Double Inlet Airfoil Fans - AtzafDokument52 SeitenDouble Inlet Airfoil Fans - AtzafDaniel AlonsoNoch keine Bewertungen
- Reading TPO 49 Used June 17 To 20 10am To 12pm Small Group Tutoring1Dokument27 SeitenReading TPO 49 Used June 17 To 20 10am To 12pm Small Group Tutoring1shehla khanNoch keine Bewertungen
- Troubleshooting For Rb750Glr4: Poe Does Not WorkDokument7 SeitenTroubleshooting For Rb750Glr4: Poe Does Not Workjocimar1000Noch keine Bewertungen
- ACC403 Week 10 Assignment Rebecca MillerDokument7 SeitenACC403 Week 10 Assignment Rebecca MillerRebecca Miller HorneNoch keine Bewertungen
- 1.2 The Main Components of Computer SystemsDokument11 Seiten1.2 The Main Components of Computer SystemsAdithya ShettyNoch keine Bewertungen
- Marshall Baillieu: Ian Marshall Baillieu (Born 6 June 1937) Is A Former AustralianDokument3 SeitenMarshall Baillieu: Ian Marshall Baillieu (Born 6 June 1937) Is A Former AustralianValenVidelaNoch keine Bewertungen
- 14 CE Chapter 14 - Developing Pricing StrategiesDokument34 Seiten14 CE Chapter 14 - Developing Pricing StrategiesAsha JaylalNoch keine Bewertungen
- Solved - in Capital Budgeting, Should The Following Be Ignored, ...Dokument3 SeitenSolved - in Capital Budgeting, Should The Following Be Ignored, ...rifa hanaNoch keine Bewertungen
- Questionnaire: ON Measures For Employee Welfare in HCL InfosystemsDokument3 SeitenQuestionnaire: ON Measures For Employee Welfare in HCL Infosystemsseelam manoj sai kumarNoch keine Bewertungen
- Ap06 - Ev04 Taller en Idioma Inglés Sobre Sistema de DistribuciónDokument9 SeitenAp06 - Ev04 Taller en Idioma Inglés Sobre Sistema de DistribuciónJenny Lozano Charry50% (2)
- Contemp World Module 2 Topics 1 4Dokument95 SeitenContemp World Module 2 Topics 1 4Miguel EderNoch keine Bewertungen
- Manulife Health Flex Cancer Plus Benefit IllustrationDokument2 SeitenManulife Health Flex Cancer Plus Benefit Illustrationroschi dayritNoch keine Bewertungen
- Faida WTP - Control PhilosophyDokument19 SeitenFaida WTP - Control PhilosophyDelshad DuhokiNoch keine Bewertungen
- MG206 Chapter 3 Slides On Marketing Principles and StrategiesDokument33 SeitenMG206 Chapter 3 Slides On Marketing Principles and StrategiesIsfundiyerTaungaNoch keine Bewertungen
- Simplified Concrete Modeling: Mat - Concrete - Damage - Rel3Dokument14 SeitenSimplified Concrete Modeling: Mat - Concrete - Damage - Rel3amarNoch keine Bewertungen
- Sec2 8 PDFDokument3 SeitenSec2 8 PDFpolistaNoch keine Bewertungen
- Company Law Handout 3Dokument10 SeitenCompany Law Handout 3nicoleclleeNoch keine Bewertungen
- Permit To Work Audit Checklist OctoberDokument3 SeitenPermit To Work Audit Checklist OctoberefeNoch keine Bewertungen
- ODF-2 - Learning MaterialDokument24 SeitenODF-2 - Learning MateriallevychafsNoch keine Bewertungen