Beruflich Dokumente
Kultur Dokumente
Configuring An Ipsec Tunnel Through A Firewall With Nat: Document Id: 14138
Hochgeladen von
pandvas5Originalbeschreibung:
Originaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Configuring An Ipsec Tunnel Through A Firewall With Nat: Document Id: 14138
Hochgeladen von
pandvas5Copyright:
Verfügbare Formate
Configuring an IPSec Tunnel Through a Firewall
With NAT
Document ID: 14138
Introduction
Prerequisites
Requirements
Components Used
Conventions
Configure
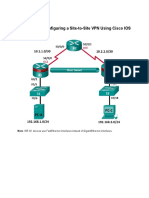
Network Diagram
Configurations
Verify
Troubleshoot
Troubleshooting Commands
Clearing Security Associations
NetPro Discussion Forums − Featured Conversations
Related Information
Introduction
This document provides a sample configuration for an IPSec tunnel through a firewall that performs network
address translation (NAT). This configuration does not work with port address translation (PAT) if you
use Cisco IOS® Software Releases prior to and not including 12.2(13)T. This kind of configuration can be
used to tunnel IP traffic. This cannot be used to encrypt traffic that does not go through a firewall, such as IPX
or routing updates. Generic routing encapsulation (GRE) tunneling is appropriate for that kind of
configuration. In the example in this document, the Cisco 2621 and 3660 Routers are the IPSec tunnel
endpoints that join two private networks, with conduits or access control lists (ACLs) on the PIX in between
to allow the IPSec traffic.
Note: NAT is a one−to−one address translation, not to be confused with PAT, which is a many (inside the
firewall)−to−one translation. Refer to Verifying NAT Operation and Basic NAT Troubleshooting or How
NAT Works for more information on NAT operation and configuration.
Note: IPSec with PAT might not work properly because the outside tunnel endpoint device cannot handle
multiple tunnels from one IP address. You need to contact your vendor to determine if the tunnel endpoint
devices work with PAT. Additionally, in versions 12.2(13)T and later, the NAT Transparency feature can also
be used for PAT. Refer to IPSec NAT Transparency for more information. Refer to Support for IPSec ESP
Through NAT for more information about these features in versions 12.2(13)T and later. Also, before you
open a case with TAC, refer to NAT Frequently Asked Questions, which has many answers to common
questions.
Prerequisites
Requirements
There are no specific requirements for this document.
Cisco − Configuring an IPSec Tunnel Through a Firewall With NAT
Components Used
The information in this document is based on these software and hardware versions:
• Cisco IOS Software Release12.0.7.T [up to but not including 12.2(13)T]
Refer to IPSec NAT Transparency for more recent versions.
• Cisco 2621 Router
• Cisco 3660 Router
• Cisco PIX Firewall
The information in this document was created from the devices in a specific lab environment. All of the
devices used in this document started with a cleared (default) configuration. If your network is live, make sure
that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Configure
In this section, you are presented with the information to configure the features described in this document.
Note: Use the Command Lookup Tool ( registered customers only) to find more information on the commands
used in this document.
Network Diagram
This document uses this network setup:
Cisco − Configuring an IPSec Tunnel Through a Firewall With NAT
Note: The IP addressing schemes used in this configuration are not legally routable on the Internet. These are
RFC 1918 addresses which have been used in a lab environment.
Configurations
This document uses these configurations:
• Cisco 2621 Configuration
• Cisco PIX Firewall Partial Configuration
• Cisco 3660 Configuration
Cisco 2621 Configuration
Current configuration:
!
version 12.0
service timestamps debug uptime
service timestamps log uptime
no service password−encryption
!
Cisco − Configuring an IPSec Tunnel Through a Firewall With NAT
hostname goss−2621
!
ip subnet−zero
!
ip audit notify log
ip audit po max−events 100
isdn voice−call−failure 0
cns event−service server
!
!−−− IKE Policy
crypto isakmp policy 10
hash md5
authentication pre−share
crypto isakmp key cisco123 address 10.99.99.2
!
crypto ipsec transform−set myset esp−des esp−md5−hmac
!
crypto map mymap local−address FastEthernet0/1
!−−− IPSec Policy
crypto map mymap 10 ipsec−isakmp
set peer 10.99.99.2
set transform−set myset
!−−− Include the private−network−to−private−network traffic
!−−− in the encryption process.
match address 101
!
controller T1 1/0
!
interface FastEthernet0/0
ip address 10.2.2.1 255.255.255.0
no ip directed−broadcast
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 10.1.1.2 255.255.255.0
no ip directed−broadcast
duplex auto
speed auto
!−−− Apply to interface.
crypto map mymap
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.1.1.1
no ip http server
!−−− Include the private−network−to−private−network traffic
!−−− in the encryption process.
access−list 101 permit ip 10.2.2.0 0.0.0.255 10.3.3.0 0.0.0.255
line con 0
transport input none
line aux 0
line vty 0 4
!
no scheduler allocate
Cisco − Configuring an IPSec Tunnel Through a Firewall With NAT
end
Cisco PIX Firewall Partial Configuration
ip address outside 10.99.99.1 255.255.255.0
ip address inside 10.1.1.1 255.255.255.0
!−−− Range of registered IP addresses for use.
global (outside) 1 10.99.99.50−10.99.99.60
!−−− Translate any internal source address when
!−−− going out to the Internet.
nat (inside) 1 0.0.0.0 0.0.0.0 0 0
static (inside,outside) 10.99.99.12 10.1.1.2 netmask 255.255.255.255 0 0
conduit permit esp host 10.99.99.12 host 10.99.99.2
conduit permit udp host 10.99.99.12 eq isakmp host 10.99.99.2
conduit permit udp host 10.99.99.12 eq 4500 host 10.99.99.2
!−−− or
access−list acl−out permit esp host 10.99.99.2 host 10.99.99.12
access−list acl−out permit udp host 10.99.99.2 host 10.99.99.12 eq isakmp
access−list acl−out permit udp host 10.99.99.2 host 10.99.99.12 eq 4500
!−−− It is important to permit UDP port 4500 for NAT−T because the PIX is acting
!−−− as a NAT device between the routers.
access−group acl−out in interface outside
isakmp enable outside
isakmp enable inside
Command configured in order to enable NAT−T
isakmp nat−traversal 20
route outside 0.0.0.0 0.0.0.0 99.99.99.2 1
route inside 10.2.2.0 255.255.255.0 10.1.1.2 1
Cisco 3660 Configuration
version 12.0
service timestamps debug uptime
service timestamps log uptime
no service password−encryption
!
hostname goss−3660
!
ip subnet−zero
!
cns event−service server
!
!−−− IKE Policy
crypto isakmp policy 10
hash md5
authentication pre−share
crypto isakmp key cisco123 address 10.99.99.12
!
crypto ipsec transform−set myset esp−des esp−md5−hmac
!
crypto map mymap local−address FastEthernet0/0
Cisco − Configuring an IPSec Tunnel Through a Firewall With NAT
!−−− IPSec Policy
crypto map mymap 10 ipsec−isakmp
set peer 10.99.99.12
set transform−set myset
!−−− Include the private−network−to−private−network traffic
!−−− in the encryption process.
match address 101
!
interface FastEthernet0/0
ip address 10.99.99.2 255.255.255.0
no ip directed−broadcast
ip nat outside
duplex auto
speed auto
!−−− Apply to interface.
crypto map mymap
!
interface FastEthernet0/1
ip address 10.3.3.1 255.255.255.0
no ip directed−broadcast
ip nat inside
duplex auto
speed auto
!
interface Ethernet3/0
no ip address
no ip directed−broadcast
shutdown
!
interface Serial3/0
no ip address
no ip directed−broadcast
no ip mroute−cache
shutdown
!
interface Ethernet3/1
no ip address
no ip directed−broadcast
interface Ethernet4/0
no ip address
no ip directed−broadcast
shutdown
!
interface TokenRing4/0
no ip address
no ip directed−broadcast
shutdown
ring−speed 16
!
!−−− Pool from which inside hosts translate to
!−−− the globally unique 10.99.99.0/24 network.
ip nat pool OUTSIDE 10.99.99.70 10.99.99.80 netmask 255.255.255.0
!−−− Except the private network from the NAT process.
ip nat inside source route−map nonat pool OUTSIDE
ip classless
Cisco − Configuring an IPSec Tunnel Through a Firewall With NAT
ip route 0.0.0.0 0.0.0.0 10.99.99.1
no ip http server
!
!−−− Include the private−network−to−private−network traffic
!−−− in the encryption process.
access−list 101 permit ip 10.3.3.0 0.0.0.255 10.2.2.0 0.0.0.255
access−list 101 deny ip 10.3.3.0 0.0.0.255 any
!−−− Except the private network from the NAT process.
access−list 110 deny ip 10.3.3.0 0.0.0.255 10.2.2.0 0.0.0.255
access−list 110 permit ip 10.3.3.0 0.0.0.255 any
route−map nonat permit 10
match ip address 110
!
line con 0
transport input none
line aux 0
line vty 0 4
!
end
Verify
Use this section to confirm that your configuration works properly.
The Output Interpreter Tool ( registered customers only) (OIT) supports certain show commands. Use the OIT to
view an analysis of show command output.
• show crypto ipsec saShows the phase 2 security associations.
• show crypto isakmp saShows the phase 1 security associations.
• show crypto engine connections activeUse to see the encrypted and decrypted packets.
Troubleshoot
Use this section to troubleshoot your configuration.
Troubleshooting Commands
Note: Refer to Important Information on Debug Commands before you use debug commands.
• debug crypto engineShows the traffic that is encrypted.
• debug crypto ipsecUse to see the IPSec negotiations of phase 2.
• debug crypto isakmp Use to see the Internet Security Association and Key Management Protocol
(ISAKMP) negotiations of phase 1.
Clearing Security Associations
• clear crypto isakmpClears Internet Key Exchange (IKE) security associations.
• clear crypto ipsec saClears IPSec security associations.
Cisco − Configuring an IPSec Tunnel Through a Firewall With NAT
NetPro Discussion Forums − Featured Conversations
Networking Professionals Connection is a forum for networking professionals to share questions, suggestions,
and information about networking solutions, products, and technologies. The featured links are some of the
most recent conversations available in this technology.
NetPro Discussion Forums − Featured Conversations for VPN
Service Providers: VPN Service Architectures
Service Providers: Network Management
Virtual Private Networks: General
Related Information
• Cisco PIX 500 Series Security Appliances
• Documentation for PIX Firewall
• Cisco Secure PIX Firewall Command References
• NAT Support Page
• Request for Comments (RFCs)
• Technical Support & Documentation − Cisco Systems
All contents are Copyright © 1992−2006 Cisco Systems, Inc. All rights reserved. Important Notices and Privacy Statement.
Updated: Jan 05, 2007 Document ID: 14138
Cisco − Configuring an IPSec Tunnel Through a Firewall With NAT
Das könnte Ihnen auch gefallen
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Von EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Noch keine Bewertungen
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationVon EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNoch keine Bewertungen
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkVon EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNoch keine Bewertungen
- ASA Firewall LabDokument5 SeitenASA Firewall LabLindsey Benter100% (3)
- CCNAS v1.1 Skills-Based Assessment Hands On AnswersDokument18 SeitenCCNAS v1.1 Skills-Based Assessment Hands On AnswersAdelaide-City South Australia86% (14)
- Configuring Site To Site Ipsec VPN Tunnel Between Cisco RoutersDokument6 SeitenConfiguring Site To Site Ipsec VPN Tunnel Between Cisco RoutersSyed AliNoch keine Bewertungen
- Secure SwitchDokument10 SeitenSecure Switchepeace2009Noch keine Bewertungen
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityVon EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNoch keine Bewertungen
- SBC Advanced Teams Practical Exam Dec 2022Dokument19 SeitenSBC Advanced Teams Practical Exam Dec 2022Ahmed Qunibi100% (1)
- Lab Sous Gns3-Configuring A Site-To-Site Ipsec VPN Using CCP and AsdmDokument31 SeitenLab Sous Gns3-Configuring A Site-To-Site Ipsec VPN Using CCP and Asdmaboubakeriam djibirldararNoch keine Bewertungen
- Configuring Site To Site IPSec VPN Tunnel Between Cisco RoutersDokument4 SeitenConfiguring Site To Site IPSec VPN Tunnel Between Cisco RoutersSuhas KanikarNoch keine Bewertungen
- Configure and Verify A Site-To-Site IPsec VPN Using CLIDokument6 SeitenConfigure and Verify A Site-To-Site IPsec VPN Using CLIMilošKovačevićNoch keine Bewertungen
- Ccnasv1.1 Chp10 Lab D Asa Isr s2s VPN StudentDokument36 SeitenCcnasv1.1 Chp10 Lab D Asa Isr s2s VPN Studentmuscle260% (1)
- Ccie Security v4 Workbook v2.5 - Lab 1Dokument76 SeitenCcie Security v4 Workbook v2.5 - Lab 1Praveen RaiNoch keine Bewertungen
- Fireware Essentials Student Guide (En US) v11!10!1Dokument510 SeitenFireware Essentials Student Guide (En US) v11!10!1Anonymous RE8LRRM100% (1)
- 5.4.1.1 Lab - Configure An Intrusion Prevention System (IPS) PDFDokument21 Seiten5.4.1.1 Lab - Configure An Intrusion Prevention System (IPS) PDFIvan ZuritaNoch keine Bewertungen
- Ipsec Pix70 NatDokument28 SeitenIpsec Pix70 NatRicardo Cien FuegosNoch keine Bewertungen
- Cisco Ipsec Static DynamicDokument9 SeitenCisco Ipsec Static DynamichsitadmNoch keine Bewertungen
- Ipsec/Gre With Nat On Ios Router Configuration Example: Document Id: 14137Dokument7 SeitenIpsec/Gre With Nat On Ios Router Configuration Example: Document Id: 14137Gustavo SánchezNoch keine Bewertungen
- Dynamic PixDokument15 SeitenDynamic PixAndika PajriNoch keine Bewertungen
- Configuring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingDokument9 SeitenConfiguring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingAndika PajriNoch keine Bewertungen
- 827pppoa Nat DHCPDokument4 Seiten827pppoa Nat DHCPLarry TembuNoch keine Bewertungen
- ASA 5505 Site To Site VPN With PolicyNATDokument10 SeitenASA 5505 Site To Site VPN With PolicyNATAbhay Nidhi SharmaNoch keine Bewertungen
- Configuration Example of Dynamic IPsec BDokument15 SeitenConfiguration Example of Dynamic IPsec BTransmission EngineerNoch keine Bewertungen
- Cisco - Configuring A Virtual Tunnel Interface With IP SecurityDokument9 SeitenCisco - Configuring A Virtual Tunnel Interface With IP SecurityandrezassoNoch keine Bewertungen
- Static Nat PixDokument15 SeitenStatic Nat Pixdia3phongNoch keine Bewertungen
- DMVPN and Easy VPN Server With ISAKMP Profiles Configuration ExampleDokument16 SeitenDMVPN and Easy VPN Server With ISAKMP Profiles Configuration Examplejhony_sieteNoch keine Bewertungen
- How To Configure-Dynamic Routing Over IPSec Against Cisco-VcDokument19 SeitenHow To Configure-Dynamic Routing Over IPSec Against Cisco-VcChandru BlueEyesNoch keine Bewertungen
- EzVPN, Configure, TroubleshootDokument13 SeitenEzVPN, Configure, TroubleshootAlviso1Noch keine Bewertungen
- Router Vpnclient Pi StickDokument10 SeitenRouter Vpnclient Pi Stickjames SpywangNoch keine Bewertungen
- CCNAS v1.1 SBADokument10 SeitenCCNAS v1.1 SBACaleb Peters0% (1)
- Configuring Security FeaturesDokument8 SeitenConfiguring Security FeaturesedinNoch keine Bewertungen
- Tunnel SplitDokument8 SeitenTunnel SplitAlviso1Noch keine Bewertungen
- Configuring A Terminal Comm ServerDokument7 SeitenConfiguring A Terminal Comm Serverbingo2kNoch keine Bewertungen
- VPN Pix PrivateDokument13 SeitenVPN Pix PrivateRaj KaranNoch keine Bewertungen
- Technical ReportDokument19 SeitenTechnical ReportUsmanNoch keine Bewertungen
- 2.3.3.4 Lab - Configuring A Switch Management AddressDokument9 Seiten2.3.3.4 Lab - Configuring A Switch Management AddressIchwan Habibie20% (5)
- 10.2.1.9 Lab - Configure A Site-To-Site IPsec VPN Using ISR CLI and ASA 5505 ASDMDokument22 Seiten10.2.1.9 Lab - Configure A Site-To-Site IPsec VPN Using ISR CLI and ASA 5505 ASDMerojasNoch keine Bewertungen
- 10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5505 ASDMDokument22 Seiten10.2.1.9 Lab - Configure A Site-to-Site IPsec VPN Using ISR CLI and ASA 5505 ASDMelizaNoch keine Bewertungen
- Case Study 1&2 AnswersDokument12 SeitenCase Study 1&2 AnswersudnuwanNoch keine Bewertungen
- Configure Ipsec 00Dokument12 SeitenConfigure Ipsec 00Huy MengNoch keine Bewertungen
- Labs of Computer NetwokingDokument28 SeitenLabs of Computer Netwokingdmhsguk21Noch keine Bewertungen
- 8 4 1 3 Lab Configure Site To Site VPN Using CLI InstructorDokument15 Seiten8 4 1 3 Lab Configure Site To Site VPN Using CLI InstructorMujeeb Rahman DostNoch keine Bewertungen
- Site To Site IPsec VPNDokument27 SeitenSite To Site IPsec VPNRasakiRraskiNoch keine Bewertungen
- PIX/ASA: Establish and Troubleshoot Connectivity Through The Cisco Security ApplianceDokument7 SeitenPIX/ASA: Establish and Troubleshoot Connectivity Through The Cisco Security AppliancetsibiNoch keine Bewertungen
- Configurar VPN ASA PIX CiscoDokument23 SeitenConfigurar VPN ASA PIX CiscoMauro GuañoNoch keine Bewertungen
- Cisco IOS Security TemplateDokument10 SeitenCisco IOS Security TemplateshankerunrNoch keine Bewertungen
- 09 - How To Connect Securely Between 2 Regional Offices Using CISCO VPNDokument4 Seiten09 - How To Connect Securely Between 2 Regional Offices Using CISCO VPNJohnpatrick DejesusNoch keine Bewertungen
- 8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLIDokument5 Seiten8.4.1.2 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN Using CLITalha Ur RehmanNoch keine Bewertungen
- HQ-ASA Practice Lab.pkt - копияDokument13 SeitenHQ-ASA Practice Lab.pkt - копияDavid VardanyanNoch keine Bewertungen
- Configuring SPAN On Cisco Catalyst Switches - Monitor & Capture Network Traffic - PacketsDokument5 SeitenConfiguring SPAN On Cisco Catalyst Switches - Monitor & Capture Network Traffic - PacketsPranav GuptaNoch keine Bewertungen
- Cisco ASA 5505 Configuration For PPPOEDokument4 SeitenCisco ASA 5505 Configuration For PPPOEdownloadpostaNoch keine Bewertungen
- 19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersDokument5 Seiten19.5.5 Packet Tracer - Configure and Verify A Site-To-Site IPsec VPN - ITExamAnswersAna Maria Citlali Diaz HernandezNoch keine Bewertungen
- 19.5.6 Lab Configure A Site To Site VPNDokument15 Seiten19.5.6 Lab Configure A Site To Site VPNJuan Carlos BolivarNoch keine Bewertungen
- InteropDokument6 SeitenInteropSaurav LodhNoch keine Bewertungen
- Remote Access IPsec TshootDokument50 SeitenRemote Access IPsec Tshootsoumen1977Noch keine Bewertungen
- Troubleshoot Connections Through The PIX and ASADokument14 SeitenTroubleshoot Connections Through The PIX and ASAgabroo5abiNoch keine Bewertungen
- Lan2lan VPNDokument6 SeitenLan2lan VPNFelix BlasioNoch keine Bewertungen
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksVon EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNoch keine Bewertungen
- Cisco Networks: Engineers' Handbook of Routing, Switching, and Security with IOS, NX-OS, and ASAVon EverandCisco Networks: Engineers' Handbook of Routing, Switching, and Security with IOS, NX-OS, and ASANoch keine Bewertungen
- Tplink Ap EAP110 - V1 - Datasheet PDFDokument5 SeitenTplink Ap EAP110 - V1 - Datasheet PDFiraudyNoch keine Bewertungen
- Midterm Examination - IT 312 I. Subnetting Scenario-Fill All The Blanks With The Appropriate Answer From The Topology, Tables and QuestionsDokument2 SeitenMidterm Examination - IT 312 I. Subnetting Scenario-Fill All The Blanks With The Appropriate Answer From The Topology, Tables and QuestionsAldrin MarianoNoch keine Bewertungen
- Hughesnet ht2000w Satellite Modem User Guide 1041264-0001 ADokument53 SeitenHughesnet ht2000w Satellite Modem User Guide 1041264-0001 AArizal CotoNoch keine Bewertungen
- Brkaci 2102Dokument121 SeitenBrkaci 2102ivnnpcNoch keine Bewertungen
- HiPath Wireless Access Points Software V1R3.10504.0 Release Notes PDFDokument25 SeitenHiPath Wireless Access Points Software V1R3.10504.0 Release Notes PDFrichardNoch keine Bewertungen
- 2.0 Huawei S5720-LI Series Switch Product Data Sheet (Detailed) ITADokument20 Seiten2.0 Huawei S5720-LI Series Switch Product Data Sheet (Detailed) ITALuis Alberto YarangaNoch keine Bewertungen
- DGTL BRKNWT 2151Dokument37 SeitenDGTL BRKNWT 2151Ala JebnounNoch keine Bewertungen
- Redistribution Between RIP and EIGRPDokument11 SeitenRedistribution Between RIP and EIGRPNay OoNoch keine Bewertungen
- Huawei AirEngine 5761R-11 & AirEngine 5761R-11E Access Points DatasheetDokument16 SeitenHuawei AirEngine 5761R-11 & AirEngine 5761R-11E Access Points Datasheetyuri meloNoch keine Bewertungen
- Lec 2. Computer NetworksDokument42 SeitenLec 2. Computer NetworksHayam UmarNoch keine Bewertungen
- Bulletcat4-Gl: Bulletcat4-Gl - 4G/Lte Ethernet/Serial/Usb GatewayDokument2 SeitenBulletcat4-Gl: Bulletcat4-Gl - 4G/Lte Ethernet/Serial/Usb GatewayJo AnorienNoch keine Bewertungen
- Broadband Access Configuration GuideDokument342 SeitenBroadband Access Configuration GuidethanhstoreNoch keine Bewertungen
- RCS Interworking Guidelines 17 October 2019: This Is A Non-Binding Permanent Reference Document of The GSMADokument27 SeitenRCS Interworking Guidelines 17 October 2019: This Is A Non-Binding Permanent Reference Document of The GSMAMohsin KhanNoch keine Bewertungen
- 9YZ037459416FMZZA - V1 - LTE End-to-End Solution LE5.0.1 Release Notes PDFDokument59 Seiten9YZ037459416FMZZA - V1 - LTE End-to-End Solution LE5.0.1 Release Notes PDFWaqas AhmedNoch keine Bewertungen
- Application Request Routing For Microsoft Exchange ServerDokument40 SeitenApplication Request Routing For Microsoft Exchange ServerabdoNoch keine Bewertungen
- GW - WiFi Configuration Instruction-ENDokument38 SeitenGW - WiFi Configuration Instruction-ENAnis BouhastineNoch keine Bewertungen
- Huawei CloudEngine 9860 Switch DatasheetDokument12 SeitenHuawei CloudEngine 9860 Switch Datasheetremart24Noch keine Bewertungen
- Technical Standards Advisory Committee Working Group On Common Connection Standards (CCS)Dokument18 SeitenTechnical Standards Advisory Committee Working Group On Common Connection Standards (CCS)Syah Brian ArdNoch keine Bewertungen
- Network LayerDokument22 SeitenNetwork LayerRashed SobujNoch keine Bewertungen
- Cisa 2 PDFDokument8 SeitenCisa 2 PDFneeloufershaikNoch keine Bewertungen
- CCNA Exploration Network Fundamentals Ver4 0 Enetwork Final Exam v1 92 With Feedback CorrectionsDokument29 SeitenCCNA Exploration Network Fundamentals Ver4 0 Enetwork Final Exam v1 92 With Feedback Correctionsgumball19100% (3)
- Acl 4.2.2.10 Packet Tracer - Configuring Extended ACLs Scenario 1Dokument3 SeitenAcl 4.2.2.10 Packet Tracer - Configuring Extended ACLs Scenario 1Emerson Emerson AemersonNoch keine Bewertungen
- Converting A Cisco 7940/7960 SCCP Phone To A SIP Phone and The Reverse ProcessDokument12 SeitenConverting A Cisco 7940/7960 SCCP Phone To A SIP Phone and The Reverse ProcessFerencz CsabaNoch keine Bewertungen
- NetwerkDokument2 SeitenNetwerkIvan John SanchezNoch keine Bewertungen
- INWPASRTG04 Listening Port DetailsDokument5 SeitenINWPASRTG04 Listening Port DetailsBhabana SahuNoch keine Bewertungen
- Modbus Master (Serial and TCP/IP) Driver For Field Device System Integrator ModulesDokument8 SeitenModbus Master (Serial and TCP/IP) Driver For Field Device System Integrator ModulesEddie Gomez VillalobosNoch keine Bewertungen
- MikrotikDokument179 SeitenMikrotikJorge Enrique Escobar CastroNoch keine Bewertungen
- Optiswitch 900 Series - : Service DemarcationDokument4 SeitenOptiswitch 900 Series - : Service DemarcationAmiNoch keine Bewertungen