Beruflich Dokumente
Kultur Dokumente
ESG ISSA Research Report Abstract Life of Cybersecurity Professionals Nov 2017 PDF
Hochgeladen von
Anonymous w1asC3A1qOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
ESG ISSA Research Report Abstract Life of Cybersecurity Professionals Nov 2017 PDF
Hochgeladen von
Anonymous w1asC3A1qCopyright:
Verfügbare Formate
Enterprise Strategy Group | Getting to the bigger truth.
RESEARCH REPORT
Abstract:
The Life and Times of
Cybersecurity Professionals
By Jon Oltsik, ESG Senior Principal Analyst
November 2017
A Cooperative Research Project by ESG and ISSA
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
Research Report Abstract: The Life and Times of Cybersecurity Professionals
Introduction
Research Objectives
In order to assess the experiences, careers, and opinions of cybersecurity professionals, ESG/ISSA surveyed 343
cybersecurity professionals representing organizations of all sizes, across all industries and geographic locations. Survey
respondents were also ISSA members.
The survey and overall research project were designed to answer the following questions about:
• Cybersecurity careers
1. How long had survey respondents worked as cybersecurity professionals?
2. Why did they become cybersecurity professionals?
3. How were they developing and advancing their careers?
4. Were they happy at their jobs and with their career choices?
5. What is necessary for cybersecurity job satisfaction? Alternatively, what alienates cybersecurity
professionals and causes them to look for another job?
6. Are cybersecurity professionals being actively recruited to change jobs?
7. Are cybersecurity professionals experiencing burnout?
• Skills development
1. How important is continuing skills development in the minds of cybersecurity professionals?
2. How do cybersecurity professionals actually develop their skills? What works and what doesn’t work?
3. Do the responsibilities and workload associated with cybersecurity jobs get in the way of skills
development?
4. Do the organizations cybersecurity professionals work at provide adequate training, skills
development programs, or services for career advancement?
• Cybersecurity organizational considerations
1. Do organizations have CISOs or similar positions in place?
2. What makes CISOs successful?
3. Why do CISOs change jobs so often?
• Security incidents and vulnerabilities
1. Have organizations suffered security incidents? If so, which types of security incidents?
2. What factors contributed to these incidents?
3. Do cybersecurity professionals believe that organizations are vulnerable to cyber-attacks?
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
Research Report Abstract: The Life and Times of Cybersecurity Professionals
4. Do cybersecurity professionals believe that their employers are vulnerable to cyber-attacks?
• The cybersecurity skills shortage
1. Do cybersecurity professionals believe that their organization has been impacted by the global
cybersecurity skills shortage?
2. If so, in what way?
3. In which areas do their organizations have the biggest cybersecurity skills deficits?
• Cybersecurity activities
1. What types of cybersecurity actions have their organizations taken over the past few years?
2. What additional actions should their organizations take to help improve cybersecurity overall?
Survey participants represented a wide range of industries including health care, IT, financial services, manufacturing,
business services, communications and media, and government. For more details, please see the Research Methodology
and Respondent Demographics sections of this report.
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
Research Report Abstract: The Life and Times of Cybersecurity Professionals
Research Methodology
To gather data for this report, ESG conducted an online survey of security and IT professionals from the ISSA member list
(and beyond) in North America, Europe, Central/South America, Africa, and Asia, and Australia between August 7, 2017
and September 13, 2017.
After filtering out unqualified respondents, removing duplicate responses, and screening the remaining completed
responses (on a number of criteria) for data integrity, we were left with a final total sample of 343 security and IT
professionals.
Please see the Respondent Demographics section of this report for more information on these respondents.
Note: Totals in figures and tables throughout this report may not add up to 100% due to rounding.
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
Research Report Abstract: The Life and Times of Cybersecurity Professionals
Respondent Demographics
The data presented in this report is based on a survey of 343 qualified respondents and cybersecurity professionals. The
following figures detail the demographics of the respondent base at an individual and organizational level.
Respondents by Current Position
Respondents’ current role is shown in Figure 1.
Figure 1. Respondents by Current Position
Which of the following best describes your current position within your organization?
(Percent of respondents, N=343)
CISO, CSO or similar
Other, 24% senior cybersecurity
position, 18%
VP-level position in an
information security
Security administrator,
department, 4%
15%
IT management, 11%
Director-level position in an
IT staff, 15%
information security department, 12%
Source: Enterprise Strategy Group and ISSA, 2017
Respondents by Region
The regional breakdown of respondents is shown in Figure 2.
Figure 2. Respondents by Region
Please indicate where you are based (i.e., where you live and work). (Percent of
respondents, N=343)
85%
7% 3% 3% 1%
North America Europe Central/South America Asia Africa
Source: Enterprise Strategy Group and ISSA, 2017
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
Research Report Abstract: The Life and Times of Cybersecurity Professionals
Respondents by Number of Employees
The number of employees in respondents’ organizations is shown in Figure 3.
Figure 3. Respondents by Number of Employees
How many total employees does your organization have worldwide? (Percent of
respondents, N=343)
20,000 or more, 21% Less than 500, 33%
10,000 to 19,999, 8%
500 to 999, 8%
5,000 to 9,999, 9%
1,000 to 2,499, 12%
2,500 to 4,999, 9%
Source: Enterprise Strategy Group and ISSA, 2017
Respondents by Industry
Respondents were asked to identify their organization’s primary industry. In total, ESG received completed, qualified
respondents from individuals in 19 distinct vertical industries, plus an “Other” category. Respondents were then grouped
into the broader categories shown in Figure 4.
Figure 4. Respondents by Industry
What is your organization’s primary industry? (Percent of respondents, N=343)
Other, 17%
Information
Technology, 19%
Retail/Wholesale, 2%
Manufacturing, 5% Financial (banking,
securities, insurance),
Communications & 16%
Media, 6%
Health Care, 10% Government
(Federal/National,
Business Services
State/Local), 15%
(accounting, consulting,
legal, etc.), 10%
Source: Enterprise Strategy Group and ISSA, 2017
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
Research Report Abstract: The Life and Times of Cybersecurity Professionals
Contents
List of Figures .......................................................................................................................................................................... 3
List of Tables ........................................................................................................................................................................... 3
Executive Summary ................................................................................................................................................................. 4
Report Conclusions ............................................................................................................................................................. 4
Introduction ............................................................................................................................................................................ 7
Research Objectives ............................................................................................................................................................ 7
Research Findings ................................................................................................................................................................... 9
The ISSA Survey Respondents ............................................................................................................................................. 9
The Cybersecurity Professional ......................................................................................................................................... 11
Cybersecurity Certifications .................................................................................................................................................. 16
Cybersecurity Jobs ............................................................................................................................................................ 18
Cybersecurity Leadership .................................................................................................................................................. 22
The State of Cybersecurity ................................................................................................................................................ 26
The Cybersecurity Skills Shortage ..................................................................................................................................... 32
Cybersecurity Improvement ............................................................................................................................................. 36
Conclusion ............................................................................................................................................................................. 37
Implications for Cybersecurity Professionals .................................................................................................................... 37
Research Implications for Employers................................................................................................................................ 38
Research Methodology ......................................................................................................................................................... 39
Respondent Demographics ................................................................................................................................................... 40
Respondents by Current Position ..................................................................................................................................... 40
Respondents by Region..................................................................................................................................................... 40
Respondents by Number of Employees ............................................................................................................................ 41
Respondents by Industry .................................................................................................................................................. 41
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
Research Report Abstract: The Life and Times of Cybersecurity Professionals
List of Figures
Figure 1. Length of Time Employed as a Cybersecurity Professional and at Current Organization/Job ................................ 9
Figure 2. Number of Different Organizations Respondents Have Worked for as a Cybersecurity Professional .................. 10
Figure 3. Phase of ISSA Cybersecurity Career Lifecycle ........................................................................................................ 10
Figure 4. Did Respondents Start Career as an IT Professional? ............................................................................................ 11
Figure 5. Factors Most Helpful in Moving to a Cybersecurity Career ................................................................................... 12
Figure 6. Reasons for Becoming a Cybersecurity Professional ............................................................................................. 13
Figure 7. Do Respondents Believe They Have a Well-defined Career Path? ........................................................................ 14
Figure 8. Most Helpful Factors in Getting to the Next Level Career-wise ............................................................................ 14
Figure 9. Most Effective Methods for Increasing KSAs ......................................................................................................... 15
Figure 10. Cybersecurity Certifications Achieved ................................................................................................................. 16
Figure 11. Most Important Certifications to Get a Job ......................................................................................................... 17
Figure 12. Factors Determining Job Satisfaction................................................................................................................... 18
Figure 13. Level of Satisfaction with Current Job ................................................................................................................. 19
Figure 14. Training Provided to Keep Up with Business and IT Risk ..................................................................................... 20
Figure 15. Respondents’ Sentiment on Various Cybersecurity Topics ................................................................................. 21
Figure 16. Do Organizations Have a CISO/CSO? ................................................................................................................... 22
Figure 17. To Whom Does the CISO/CSO Report? ................................................................................................................ 22
Figure 18. Is CISO an Active Participant with Executive Management and Board of Directors?.......................................... 23
Figure 19. Is CISO Level of Participation with Executive Management and Board of Directors Adequate? ........................ 23
Figure 20. Most Important Qualities of a Successful CISO.................................................................................................... 24
Figure 21. Factors Likely to Cause CISOs to Leave an Organization...................................................................................... 25
Figure 22. Actions Taken around Cybersecurity Over the Past Two Years ........................................................................... 26
Figure 23. Frequency of Security Incidents over the Past Two Years ................................................................................... 27
Figure 24. Biggest Contributors to Security Events Experienced .......................................................................................... 28
Figure 25. Results of Security Incidents ................................................................................................................................ 29
Figure 26. Vulnerability of Most Organizations to a Significant Cyber-attack or Data Breach ............................................. 30
Figure 27. Biggest Cybersecurity Challenges ........................................................................................................................ 31
Figure 28. Level of Impact of Cybersecurity Skills Shortage ................................................................................................. 32
Figure 29. How Cybersecurity Skills Shortage Has Impacted Organizations......................................................................... 33
Figure 30. Area(s) with Biggest Shortage of Cybersecurity Skills .......................................................................................... 34
Figure 31. Frequency of Solicitation by Job Recruiters ......................................................................................................... 35
Figure 32. Actions That Would Provide the Most Cybersecurity Benefits to Organization .................................................. 36
Figure 33. Respondents by Current Position ........................................................................................................................ 40
Figure 34. Respondents by Region........................................................................................................................................ 40
Figure 35. Respondents by Number of Employees ............................................................................................................... 41
Figure 36. Respondents by Industry ..................................................................................................................................... 41
List of Tables
Table 1. Factors Most Helpful in Moving to a Cybersecurity Career, by Year ...................................................................... 12
Table 2. Actions Taken around Cybersecurity by Year.......................................................................................................... 27
Table 3. Biggest Contributors to Security Events Experienced by Year ................................................................................ 29
Table 4. How Cybersecurity Skills Shortage Has Impacted Organizations, by Year .............................................................. 34
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The
Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject
to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this
publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express
consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable,
criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.
The Information Systems Security Association (ISSA) is the community of choice for international cybersecurity professionals dedicated to advancing
individual growth, managing technology risk, and protecting critical information and infrastructure. ISSA members and award winners include many of
the industry’s notable luminaries and represents a broad range of industries - from communications, education, healthcare, manufacturing, financial
and consulting to IT - as well as federal, state and local government departments and agencies. Through regional chapter meetings, conferences,
networking events and content, members tap into a wealth of shared knowledge and expertise. Visit ISSA on the web at www.issa.org and follow us
on Twitter at @ISSAINTL.
The Enterprise Strategy Group (ESG) is an IT analyst, research, validation, and strategy firm that provides actionable insight and intelligence to the
global IT community.
© 2017 by The Enterprise Strategy Group, Inc. All Rights Reserved.
Das könnte Ihnen auch gefallen
- State of Cybersecurity 2019: Part 1: Current Trends in Workforce DevelopmentDokument21 SeitenState of Cybersecurity 2019: Part 1: Current Trends in Workforce DevelopmentViriato LeaoNoch keine Bewertungen
- Wombat - Proofpoint - 2019 State of The Phish Report - FinalDokument23 SeitenWombat - Proofpoint - 2019 State of The Phish Report - FinalTyler DurdenNoch keine Bewertungen
- Information Security Benchmark 2019: A Balanced View On The Information Security LandscapeDokument20 SeitenInformation Security Benchmark 2019: A Balanced View On The Information Security LandscapeJonas MeierNoch keine Bewertungen
- Fortify Your Data: A Guide to the Emerging TechnologiesVon EverandFortify Your Data: A Guide to the Emerging TechnologiesNoch keine Bewertungen
- Cyber Risk SurveyDokument27 SeitenCyber Risk SurveyCanitocheNoch keine Bewertungen
- State of Cybersecurity 2019 Part 1 Res Eng 0319Dokument21 SeitenState of Cybersecurity 2019 Part 1 Res Eng 0319Elena VaciagoNoch keine Bewertungen
- How To Become A Cybersecurity Pro: A Cheat Sheet: by Alison Denisco RayomeDokument11 SeitenHow To Become A Cybersecurity Pro: A Cheat Sheet: by Alison Denisco RayomeWalter MacuadaNoch keine Bewertungen
- ICT380 Assignment 1Dokument14 SeitenICT380 Assignment 1Neelav BaraiNoch keine Bewertungen
- Essentials of Management Information Systems,: Learning Track 5: Occupational and Career Outlook ForDokument10 SeitenEssentials of Management Information Systems,: Learning Track 5: Occupational and Career Outlook ForCynthia kangNoch keine Bewertungen
- Final PDF Krishna 6Dokument84 SeitenFinal PDF Krishna 6Elizabeth ThomasNoch keine Bewertungen
- Breaking Into IT: Your Roadmap to Success in the Tech IndustryVon EverandBreaking Into IT: Your Roadmap to Success in the Tech IndustryNoch keine Bewertungen
- Chapter 1 DesignDokument20 SeitenChapter 1 DesignMomentum PressNoch keine Bewertungen
- The Economic Value of Prevention in The ReportDokument51 SeitenThe Economic Value of Prevention in The ReportIkponmwosa AghimienNoch keine Bewertungen
- Colorful Retro Playful Asking Game Presentation - 20231127 - 172300 - 0000Dokument18 SeitenColorful Retro Playful Asking Game Presentation - 20231127 - 172300 - 0000fellipe.5fernadesNoch keine Bewertungen
- EY Security Operations Centers Helping You Get Ahead of CybercrimeDokument20 SeitenEY Security Operations Centers Helping You Get Ahead of Cybercrimeashish100% (1)
- CyberEdge 2020 - Cybersecurity Defense ReportDokument113 SeitenCyberEdge 2020 - Cybersecurity Defense Reportshirley liliana peña carlosNoch keine Bewertungen
- The CISO Perspective: Understand the importance of the CISO in the cyber threat landscapeVon EverandThe CISO Perspective: Understand the importance of the CISO in the cyber threat landscapeNoch keine Bewertungen
- ISC2 Cybersecurity Workforce Study 2019Dokument37 SeitenISC2 Cybersecurity Workforce Study 2019Dinesh GaikwadNoch keine Bewertungen
- Can. Trust. Will.: Hiring for the Human Element in the New Age of CybersecurityVon EverandCan. Trust. Will.: Hiring for the Human Element in the New Age of CybersecurityBewertung: 5 von 5 Sternen5/5 (1)
- PWC Global State of Information SecurityDokument24 SeitenPWC Global State of Information SecurityshopereiraNoch keine Bewertungen
- RP Hacking Skills ShortageDokument20 SeitenRP Hacking Skills ShortageRobin RichardsonNoch keine Bewertungen
- Communicating The Value of Cybersecurity To Boards and LeadershipDokument20 SeitenCommunicating The Value of Cybersecurity To Boards and LeadershipManuela OliveiraNoch keine Bewertungen
- 2008 IT Skill and Salary ReportDokument12 Seiten2008 IT Skill and Salary ReportChong Zhang100% (2)
- Documentación Principal SecundariaDokument2 SeitenDocumentación Principal SecundariaPaolo del SurNoch keine Bewertungen
- Security Enforcer Vs Enabler Report Draft 1-16-19Dokument14 SeitenSecurity Enforcer Vs Enabler Report Draft 1-16-19Anonymous v8sB76r0vNoch keine Bewertungen
- ISC2 Cybersecurity Workforce Study 2023Dokument84 SeitenISC2 Cybersecurity Workforce Study 2023thecodehasbytesNoch keine Bewertungen
- Security Benchmark Report 2023Dokument66 SeitenSecurity Benchmark Report 2023Cary AgosNoch keine Bewertungen
- Dell Survey - NIST ResultsDokument11 SeitenDell Survey - NIST ResultsGreg OttoNoch keine Bewertungen
- Cybersecurity Jobs & Career Paths: Find Cybersecurity Jobs, #2Von EverandCybersecurity Jobs & Career Paths: Find Cybersecurity Jobs, #2Noch keine Bewertungen
- STH Security Awareness Report 2015Dokument23 SeitenSTH Security Awareness Report 2015Conrad LopezNoch keine Bewertungen
- What Is The Future of ITSM PDFDokument21 SeitenWhat Is The Future of ITSM PDFmariaNoch keine Bewertungen
- 2012 01 24 Larry Clinton Economics of Security Presentation at Opal Event in DCDokument36 Seiten2012 01 24 Larry Clinton Economics of Security Presentation at Opal Event in DCisallianceNoch keine Bewertungen
- Research Proposal: Under The Guidance of Dr. Hemalatha RDokument7 SeitenResearch Proposal: Under The Guidance of Dr. Hemalatha RJyothish JbNoch keine Bewertungen
- Task 1 / Task 2: Entrepreneurship (Ucx-249)Dokument42 SeitenTask 1 / Task 2: Entrepreneurship (Ucx-249)Ālok KrNoch keine Bewertungen
- Securing What's Now and What's Next: 20 Cybersecurity Considerations For 2020Dokument25 SeitenSecuring What's Now and What's Next: 20 Cybersecurity Considerations For 2020Lidia MefNoch keine Bewertungen
- A Best Practices Guide for Comprehensive Employee Awareness ProgramsVon EverandA Best Practices Guide for Comprehensive Employee Awareness ProgramsNoch keine Bewertungen
- 2011 12 02 Larry Clinton Cyber Risk and Data Breach Management Summit Presentation in NYC About PWC Study APTDokument31 Seiten2011 12 02 Larry Clinton Cyber Risk and Data Breach Management Summit Presentation in NYC About PWC Study APTisallianceNoch keine Bewertungen
- How To Minimize The Impact of The Cyber Security Skills Shortage TrustwaveDokument15 SeitenHow To Minimize The Impact of The Cyber Security Skills Shortage TrustwaveRezu JavNoch keine Bewertungen
- How To Build A Successful Career in CybersecurityDokument22 SeitenHow To Build A Successful Career in CybersecurityMiguel100% (3)
- HG and CV The Cybersecurity Jobs Report 2017Dokument5 SeitenHG and CV The Cybersecurity Jobs Report 2017vendetta82pgNoch keine Bewertungen
- The Future and Opportunities of Cybersecurity in the WorkforceVon EverandThe Future and Opportunities of Cybersecurity in the WorkforceBewertung: 3 von 5 Sternen3/5 (1)
- CompTIA CySA+ Certification The Ultimate Study Guide to Practice Questions With Answers and Master the Cybersecurity Analyst ExamVon EverandCompTIA CySA+ Certification The Ultimate Study Guide to Practice Questions With Answers and Master the Cybersecurity Analyst ExamNoch keine Bewertungen
- How To Become A Chief Information Security Officer (CISO) .Dokument18 SeitenHow To Become A Chief Information Security Officer (CISO) .James MsuyaNoch keine Bewertungen
- Ebook Enterprise Cybersecurity TrainingDokument20 SeitenEbook Enterprise Cybersecurity TrainingSandro Wallace PereiraNoch keine Bewertungen
- Project Report HRDokument58 SeitenProject Report HRkapahi89Noch keine Bewertungen
- Chapter IDokument12 SeitenChapter IromanNoch keine Bewertungen
- FTNT 2023 Security Awareness and Training BriefDokument15 SeitenFTNT 2023 Security Awareness and Training BriefAOSantanaNoch keine Bewertungen
- Offensive Security Warrior: Where It Comes From?Dokument2 SeitenOffensive Security Warrior: Where It Comes From?AyishasaddiquaNoch keine Bewertungen
- The Universal Language of IT: April 2020Dokument34 SeitenThe Universal Language of IT: April 2020prafullNoch keine Bewertungen
- Implementation of Insider Threat Program.Dokument6 SeitenImplementation of Insider Threat Program.cheropdeborah10Noch keine Bewertungen
- OIC-CERT Cyber Drill 2017, Post Event Report by PISA-CERT PakistanDokument8 SeitenOIC-CERT Cyber Drill 2017, Post Event Report by PISA-CERT PakistanAbbas AnsariNoch keine Bewertungen
- The Frictionless Enterprise: Special Research & Coverage SeriesDokument36 SeitenThe Frictionless Enterprise: Special Research & Coverage SeriesDerekBrownNoch keine Bewertungen
- Lesson 3 PDFDokument8 SeitenLesson 3 PDFJacob Satorious ExcaliburNoch keine Bewertungen
- Drive Change From Within: Gear Your Workplace For MoreDokument62 SeitenDrive Change From Within: Gear Your Workplace For MoreShah MuradNoch keine Bewertungen
- Isc2 Cyberedge 2020 CDR Report v10 - 641567Dokument58 SeitenIsc2 Cyberedge 2020 CDR Report v10 - 641567Forense OrlandoNoch keine Bewertungen
- RPT Cybersecurity Workforce ShortageDokument24 SeitenRPT Cybersecurity Workforce ShortageGustavo SánchezNoch keine Bewertungen
- TR EB Cybersec Career2Dokument10 SeitenTR EB Cybersec Career2RothNoch keine Bewertungen
- Quotes On StressDokument5 SeitenQuotes On StressgretchhhNoch keine Bewertungen
- Todentj 9 250 PDFDokument7 SeitenTodentj 9 250 PDFRSU DUTA MULYANoch keine Bewertungen
- Arihant DRX Ascend Case Study PDFDokument2 SeitenArihant DRX Ascend Case Study PDFsaurav.martNoch keine Bewertungen
- BrochureDokument6 SeitenBrochureRahul ShettyNoch keine Bewertungen
- 50 Maternal and Child NCLEX QuestionsDokument14 Seiten50 Maternal and Child NCLEX QuestionsShengxy Ferrer100% (2)
- Budget Equity ToolDokument22 SeitenBudget Equity ToolEd PraetorianNoch keine Bewertungen
- 23 Medicinal Plants The Native Americans Used On A Daily Basis - MSYCDokument15 Seiten23 Medicinal Plants The Native Americans Used On A Daily Basis - MSYCLeandro RodriguesNoch keine Bewertungen
- INTEGRATED CASE STUDY: Cold Supply Chains and The COVID-19 VaccineDokument3 SeitenINTEGRATED CASE STUDY: Cold Supply Chains and The COVID-19 VaccineKatia Katherine LUZON CURONoch keine Bewertungen
- Standards For Accreditation-Schools - 2010Dokument43 SeitenStandards For Accreditation-Schools - 2010Nayda Jiménez Pérez100% (1)
- Common Core Principles and Competences For Social Care and Health Workers Working With Adults at The End of LifeDokument20 SeitenCommon Core Principles and Competences For Social Care and Health Workers Working With Adults at The End of LifeEng Stephen ArendeNoch keine Bewertungen
- Avocado Production in The PhilippinesDokument20 SeitenAvocado Production in The Philippinescutieaiko100% (1)
- DLL - Mapeh 6 - Q4 - W6Dokument4 SeitenDLL - Mapeh 6 - Q4 - W6Bernard Martin100% (1)
- Action Plan GPPDokument3 SeitenAction Plan GPPMa Rk AntonioNoch keine Bewertungen
- 1PE 4 Q3 Answer Sheet March 2024Dokument3 Seiten1PE 4 Q3 Answer Sheet March 2024Chid CabanesasNoch keine Bewertungen
- Vstep Tests B1 B2 C1 Full KeyDokument162 SeitenVstep Tests B1 B2 C1 Full KeyLe Hoang LinhNoch keine Bewertungen
- Drug Study - MidazolamDokument8 SeitenDrug Study - MidazolamKian HerreraNoch keine Bewertungen
- Pitbull StatementDokument4 SeitenPitbull StatementThe Citizen NewspaperNoch keine Bewertungen
- Baby Led-WeaningDokument7 SeitenBaby Led-WeaningsophieNoch keine Bewertungen
- Form 1 ADokument2 SeitenForm 1 ARohit Jain100% (2)
- ACLS Pretest Exam AnnotatedDokument21 SeitenACLS Pretest Exam AnnotatedMOLLYNoch keine Bewertungen
- BNMHGDokument34 SeitenBNMHGAnonymous lt2LFZHNoch keine Bewertungen
- Antimicrobial ResistanceDokument46 SeitenAntimicrobial ResistanceEmil CotenescuNoch keine Bewertungen
- Docet CPD Resources - Competencies and Cet PointsDokument1 SeiteDocet CPD Resources - Competencies and Cet PointsWEDHNoch keine Bewertungen
- BUPA Medical Service Providers Lebanon Updated-April 2013Dokument3 SeitenBUPA Medical Service Providers Lebanon Updated-April 2013gchaoul87Noch keine Bewertungen
- AM LOVE School Form 8 SF8 Learner Basic Health and Nutrition ReportDokument4 SeitenAM LOVE School Form 8 SF8 Learner Basic Health and Nutrition ReportLornaNirzaEnriquezNoch keine Bewertungen
- R4 HealthfacilitiesDokument332 SeitenR4 HealthfacilitiesCarl Joseph BarcenasNoch keine Bewertungen
- Public Opinion On Idea of Digitalising Rural CommunityDokument11 SeitenPublic Opinion On Idea of Digitalising Rural CommunityINSTITUTE OF LEGAL EDUCATIONNoch keine Bewertungen
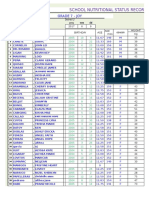
- School Nutritional Status Record: Grade 7 - JoyDokument4 SeitenSchool Nutritional Status Record: Grade 7 - JoySidNoch keine Bewertungen
- 1053-Article Text-2175-1-10-20230227Dokument8 Seiten1053-Article Text-2175-1-10-20230227inNoch keine Bewertungen
- JPNC 02 00096Dokument9 SeitenJPNC 02 00096Catalina StoicescuNoch keine Bewertungen