Beruflich Dokumente
Kultur Dokumente
Lab 7
Hochgeladen von
Tomas Rodriguez RamirezOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Lab 7
Hochgeladen von
Tomas Rodriguez RamirezCopyright:
Verfügbare Formate
Lab ID: 10.1116A260.DHI2.
Extended ACL Practice Lab 1
Objective
Learn to configure access control lists (ACLs). Verify the ACLs by using show commands and network
connectivity tests.
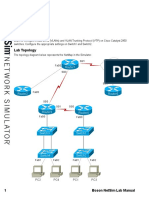
Lab Topology
The topology diagram below represents the NetMap in the Simulator.
Command Summary
Command Description
access-list access-list-number {deny | permit} defines an extended IP ACL for the traffic type
protocol source source-wildcard [operator [port]] specified by the protocol parameter
destination destination-wildcard [operator [port]] [log]
configure terminal enters global configuration mode from privileged
EXEC mode
enable enters privileged EXEC mode
end ends and exits configuration mode
exit exits one level in the menu structure
interface type number changes from global configuration mode to
interface configuration mode
ip access-group {access-list-number | access-list- controls access to an interface
name} {in | out}
1 Boson NetSim Lab Manual
Command Description
ping ip-address sends an Internet Control Message Protocol
(ICMP) echo request to the specified address
show access-lists [access-list-number | access-list- displays the contents of current ACLs
name]
show ip interface {type number} displays IP information for an interface
show ip interface brief displays a brief summary of interface status and
configuration
show running-config displays the active configuration file
telnet ip-address starts the terminal emulation program from a PC,
router, or switch; permits you to access devices
remotely over the network
The IP addresses and subnet masks used in this lab are shown in the tables below:
IP Addresses
Device Interface IP Address Subnet Mask
Router1 Serial 0/0 192.168.1.1 255.255.255.252
FastEthernet 0/0 10.10.1.1 255.255.255.0
Router2 Serial 0/0 192.168.1.2 255.255.255.252
FastEthernet 0/0 10.10.2.1 255.255.255.0
FastEthernet 0/1 192.168.1.5 255.255.255.252
Router3 FastEthernet 0/0 192.168.1.6 255.255.255.252
FastEthernet 0/1 10.10.3.1 255.255.255.0
Device IP Address Subnet Mask Default Gateway
PC1 10.10.1.3 255.255.255.0 10.10.1.1
PC2 10.10.1.4 255.255.255.0 10.10.1.1
PC3 10.10.2.3 255.255.255.0 10.10.2.1
PC4 10.10.3.3 255.255.255.0 10.10.3.1
PC5 10.10.3.4 255.255.255.0 10.10.3.1
PC6 10.10.3.5 255.255.255.0 10.10.3.1
2 Boson NetSim Lab Manual
Lab Tasks
Task 1: Verify Network Configuration
In this task, you will issue the commands necessary to review the current network configuration.
1. Verify the IP address and state of each interface. The line and protocol state of each of the
configured interfaces on each router and switch should be up/up.
2. Allow time for the network to converge. On PC1, issue a ping to verify connectivity with PC3
(10.10.2.3) and PC6 (10.10.3.5). All pings should be successful.
Task 2: Review ACL Configuration
1. What is an advantage of extended ACLs? _____________________________________________
______________________________________________________________________________
2. On which interface should you apply extended ACLs? ___________________________________
3. What is an acceptable value for the access-list-number parameter in an extended ACL? ________
Task 3: Configure an Extended ACL to Control LAN A Telnet Traffic
In this task, you will configure an ACL to control the flow of Telnet traffic from LAN A to Router2 and
Router3.
1. What type of transport protocol is Telnet? _____________________________________________
2. Create ACL 101, and apply it to the appropriate device and interface and in the appropriate direction;
ACL 101 should permit only Telnet traffic from the LAN A subnets to the WAN subnets on Router2
and Router3 (192.168.1.x).
3. Add statements to ACL 101 that will prevent Telnet traffic from the LAN A subnet to the LAN C
subnet and will allow all other traffic.
Task 4: Configure an Extended ACL to Control LAN C Telnet Traffic
In this task, you will configure an ACL to control the flow of Telnet traffic from LAN C.
1. On Router3, create ACL 102 to allow only Telnet traffic from the LAN C subnet to any other network.
2. To which interface should extended ACLs typically be applied? ____________________________
3. On Router3, apply the ACL to the appropriate interface and in the appropriate direction.
4. On Router3, add a rule to ACL 102 to permit ICMP traffic from the LAN connected to Router3 to any
other network.
3 Boson NetSim Lab Manual
Task 5: Verify Extended ACLs
This task involves verifying that the extended ACLs created in the previous task are configured correctly.
1. On Router1, verify that ACL 101 has been applied to the correct interface.
2. On Router1, display the ACLs configured on the router.
3. Issue pings from LAN A PCs to all IP addresses configured in the topology. Attempt to telnet to all
IP addresses configured on the routers; the Telnet password is set to B0$0n. Which attempts are
successful, and which fail? _________________________________________________________
4. On Router3, verify that ACL 102 has been applied to the correct interface.
5. On Router3, display the ACLs configured on the router.
6. Issue pings from LAN C PCs to all IP addresses configured in the topology. Attempt to telnet to all
IP addresses configured on the routers; the Telnet password is set to B0$0n. Which attempts are
successful, and which fail? _________________________________________________________
7. On Router1 and Router3, display the ACLs configured on the router. How many times has each ACL
statement been implemented? ______________________________________________________
Once you have completed this lab, be sure to check your work by using the grading function.
You can do so by clicking the Grade Lab icon ( ) in the toolbar or by pressing Ctrl+G.
4 Boson NetSim Lab Manual
Lab Solutions
Task 1: Verify Network Configuration
1. Verify the IP address and state of each interface by using the following command. The line and
protocol state of each of the configured interfaces on each router and switch should be up/up. The
following is sample output from Router1:
Router1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
Serial0/0 192.168.1.1 YES unset up up
Serial0/1 unassigned YES unset administratively down down
FastEthernet0/0 10.10.1.1 YES unset up up
FastEthernet0/1 unassigned YES unset administratively down down
2. Allow time for the network to converge. On PC1, issue a ping to verify connectivity with PC3
(10.10.2.3) and PC6 (10.10.3.5). All pings should be successful.
C:>ping 10.10.2.3
C:>ping 10.10.3.5
Task 2: Review ACL Configuration
1. An advantage of extended ACLs is that they can be configured to permit or deny packets based on
source IP address, destination IP address, protocol, and port.
2. You should apply extended ACLs to the interface that is as close to the source as possible. This
prevents unnecessary traffic from traversing the network and consuming bandwidth and router
resources.
Extended ACLs can identify traffic based on source and destination IP addresses as well as traffic
type, as is required in this lab. Multiple ACLs are not required to accomplish multiple tasks on the
same interface. ACLs can consist of multiple access list statements. Packets are compared to each
statement in sequence until a match is found. The permit and deny keywords are used to indicate
whether matching packets should be forwarded or dropped, respectively. If the packet does not
match any of the access list statements, the packet is dropped. This is called the implicit deny rule;
all traffic is dropped unless it matches one of the access list statements that is configured with the
permit keyword.
3. You can use any number from 100 through 199 or from 2000 through 2699 as the access-list-
number parameter in an extended ACL.
Task 3: Configure an Extended ACL to Control LAN A Telnet Traffic
1. Telnet is a Transmission Control Protocol (TCP) transport protocol. Telnet is typically used for
bidirectional communication and can be used to configure a Cisco device via a virtual terminal
connection.
5 Boson NetSim Lab Manual
2. On Router1, issue the following commands to create a single ACL statement using ACL number
101 to allow Telnet traffic from the LAN A subnet to the WAN subnets on Router2 and Router3
(192.168.1.x). ACL 101 should be applied to Router1’s FastEthernet 0/0 interface in the inbound
direction.
Router1(config)#access-list 101 permit tcp 10.10.1.0 0.0.0.255 192.168.1.0 0.0.0.7 eq telnet
Router1(config)#interface fastethernet 0/0
Router1(config-if)#ip access-group 101 in
3. On Router1, issue the following commands to prevent Telnet traffic from the LAN A subnet to the
LAN C subnet and to allow all other traffic:
Router1(config)#access-list 101 deny tcp any 10.10.3.0 0.0.0.255 eq telnet
Router1(config)#access-list 101 permit ip any any
Task 4: Configure an Extended ACL to Control LAN C Telnet Traffic
1. On Router3, issue the following command to create ACL 102 to allow Telnet traffic from LAN C to
any other network:
Router3(config)#access-list 102 permit tcp 10.10.3.0 0.0.0.255 any eq telnet
2. Extended ACLs should be applied as close to the source of the traffic as possible. Because the LAN
whose traffic you want to regulate is connected to Router3’s FastEthernet 0/1 interface, you should
apply ACL 102 to that interface.
3. On Router3, issue the following commands to assign ACL 102 to the appropriate interface and in the
appropriate direction:
Router3(config)#interface fastethernet 0/1
Router3(config-if)#ip access-group 102 in
4. On Router3, issue the following commands to create ACL 102 statements that will prevent ICMP
traffic from LAN C to any IP address on Router WAN (192.168.1.x) interfaces and that will allow all
other traffic:
Router3(config)#access-list 102 deny icmp 10.10.3.0 0.0.0.255 192.168.1.0 0.0.0.7
Router3(config)#access-list 102 permit ip any any
6 Boson NetSim Lab Manual
Task 5: Verify Extended ACLs
1. On Router1, issue the following command to verify that ACL 101 has been applied to Router1’s
FastEthernet 0/0 interface:
Router1#show ip interface fastethernet 0/0
FastEthernet0/0 is up, line protocol is up
Internet address is 10.10.1.1/24
Broadcast address is 255.255.255.255
MTU 1500 bytes,
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is 101
<output omitted>
2. On Router1, issue the following command to display the configured ACLs:
Router1#show access-lists
Extended IP access list 101
10 permit tcp 10.10.1.0 0.0.0.255 192.168.1.0 0.0.0.7 eq telnet (0 matches)
20 deny tcp any 10.10.3.0 0.0.0.255 eq telnet (0 matches)
30 permit ip any any (0 matches)
3. You should be able to ping from the LAN A PCs to all IP addresses configured in the simulated
network. You should test Telnet connectivity between LAN A PCs and the routers; the Telnet
password is set to B0$0n. The Telnet connectivity to the WAN and LAN interfaces on the routers
should be successful, with the exception of a Telnet session to Router3’s LAN interface, which
should fail. The following is sample output from PC1 to Router1:
C:>ping 10.10.1.1
C:>telnet 10.10.1.1
Password:B0$0n
Router1>exit
[Connection to 10.10.1.1 closed by foreign host]
C:>telnet 10.10.3.1
Trying 10.10.3.1 ...
% Destination unreachable; gateway or host down
C:>telnet 192.168.1.1
Password:B0$0n
Router1>exit
[Connection to 192.168.1.1 closed by foreign host]
4. On Rout
7 Boson NetSim Lab Manual
er3, issue the following command to verify that ACL 102 has been applied to Router3’s FastEthernet 0/1
interface:
Router3#show ip interface fastethernet 0/1
FastEthernet0/1 is up, line protocol is up
Internet address is 10.10.3.1/24
Broadcast address is 255.255.255.255
MTU 1500 bytes,
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is 102
<output omitted>
5. On Router3, issue the following command to display the configured ACLs:
Router3#show access-lists
Extended IP access list 102
10 permit tcp 10.10.3.0 0.0.0.255 any eq telnet (0 matches)
20 deny icmp 10.10.3.0 0.0.0.255 192.168.1.0 0.0.0.7 (0 matches)
30 permit ip any any (4 matches)
6. From LAN C PCs, you should be able to telnet to any of the router interfaces and ping any IP
address in any LAN subnet; the Telnet password is set to B0$0n. However, you should not be able
to ping any WAN IP address configured on the routers. The following is sample output from PC6:
C:>telnet 10.10.1.1
Password:B0$0n
Router1>exit
[Connection to 10.10.1.1 closed by foreign host]
C:>ping 10.10.1.1 (succeeds)
C:>ping 192.168.1.1 (fails)
7. By issuing the following command on Router1 and Router3, you can determine the number of times
each statement has been applied:
Router1#show access-lists
Extended IP access list 101
10 permit tcp 10.10.1.0 0.0.0.255 192.168.1.0 0.0.0.7 eq telnet (1 matches)
20 deny tcp any 10.10.3.0 0.0.0.255 eq telnet (1 matches)
30 permit ip any any (2 matches)
Router3#show access-lists
Extended IP access list 102
10 permit tcp 10.10.3.0 0.0.0.255 any eq telnet (1 matches)
20 deny icmp 10.10.3.0 0.0.0.255 192.168.1.0 0.0.0.7 (5 matches)
30 permit ip any any (1 matches)
8 Boson NetSim Lab Manual
Sample Configuration Scripts
Router1
Router1#show running-config
Building configuration...
Current configuration : 1185 bytes
!
Version 15.b
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname Router1
!
ip subnet-zero
!
ip cef
no ip domain-lookup
!
interface Serial0/0
description Link to Router2
ip address 192.168.1.1 255.255.255.252
no ip directed-broadcast
clock rate 64000
!
interface Serial0/1
description Unused port
no ip address
no ip directed-broadcast
shutdown
!
interface FastEthernet0/0
description Link to Switch1
ip address 10.10.1.1 255.255.255.0
no ip directed-broadcast
ip access-group 101 in
!
interface FastEthernet0/1
description Unused port
no ip address
no ip directed-broadcast
shutdown
!
router ospf 1
log-adjacency-changes
network 10.10.1.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.3 area 0
!
ip classless
no ip http server
!
access-list 101 permit tcp 10.10.1.0 0.0.0.255 192.168.1.0 0.0.0.7 eq telnet
access-list 101 deny tcp any 10.10.3.0 0.0.0.255 eq telnet
access-list 101 permit ip any any
!
line con 0
line aux 0
line vty 0 4
login
password B0$0n
!
no scheduler allocate
end
9 Boson NetSim Lab Manual
Router3
Router3#show running-config
Building configuration...
Current configuration : 1157 bytes
!
Version 15.b
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname Router3
!
ip subnet-zero
!
ip cef
no ip domain-lookup
!
interface Serial0/0
description Unused Port
no ip address
no ip directed-broadcast
shutdown
!
interface Serial0/1
description Unused Port
no ip address
no ip directed-broadcast
shutdown
!
interface FastEthernet0/0
description Link to Router2
ip address 192.168.1.6 255.255.255.252
no ip directed-broadcast
!
interface FastEthernet0/1
description Link to Switch3
ip address 10.10.3.1 255.255.255.0
no ip directed-broadcast
ip access-group 102 in
!
router ospf 1
log-adjacency-changes
network 10.10.3.0 0.0.0.255 area 0
network 192.168.1.4 0.0.0.3 area 0
!
ip classless
no ip http server
!
access-list 102 permit tcp 10.10.3.0 0.0.0.255 any eq telnet
access-list 102 deny icmp 10.10.3.0 0.0.0.255 192.168.1.0 0.0.0.7
access-list 102 permit ip any any
!
line con 0
line aux 0
line vty 0 4
login
password B0$0n
!
no scheduler allocate
end
Copyright © 1996–2017 Boson Software, LLC. All rights reserved. NetSim software and documentation are protected by copyright law.
10 Boson NetSim Lab Manual
Das könnte Ihnen auch gefallen
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeVon EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeBewertung: 4 von 5 Sternen4/5 (5794)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreVon EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreBewertung: 4 von 5 Sternen4/5 (1090)
- Never Split the Difference: Negotiating As If Your Life Depended On ItVon EverandNever Split the Difference: Negotiating As If Your Life Depended On ItBewertung: 4.5 von 5 Sternen4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceVon EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceBewertung: 4 von 5 Sternen4/5 (895)
- Grit: The Power of Passion and PerseveranceVon EverandGrit: The Power of Passion and PerseveranceBewertung: 4 von 5 Sternen4/5 (588)
- Shoe Dog: A Memoir by the Creator of NikeVon EverandShoe Dog: A Memoir by the Creator of NikeBewertung: 4.5 von 5 Sternen4.5/5 (537)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersVon EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersBewertung: 4.5 von 5 Sternen4.5/5 (345)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureVon EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureBewertung: 4.5 von 5 Sternen4.5/5 (474)
- Her Body and Other Parties: StoriesVon EverandHer Body and Other Parties: StoriesBewertung: 4 von 5 Sternen4/5 (821)
- The Emperor of All Maladies: A Biography of CancerVon EverandThe Emperor of All Maladies: A Biography of CancerBewertung: 4.5 von 5 Sternen4.5/5 (271)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Von EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Bewertung: 4.5 von 5 Sternen4.5/5 (121)
- The Little Book of Hygge: Danish Secrets to Happy LivingVon EverandThe Little Book of Hygge: Danish Secrets to Happy LivingBewertung: 3.5 von 5 Sternen3.5/5 (400)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyVon EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyBewertung: 3.5 von 5 Sternen3.5/5 (2259)
- The Yellow House: A Memoir (2019 National Book Award Winner)Von EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Bewertung: 4 von 5 Sternen4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaVon EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaBewertung: 4.5 von 5 Sternen4.5/5 (266)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryVon EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryBewertung: 3.5 von 5 Sternen3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnVon EverandTeam of Rivals: The Political Genius of Abraham LincolnBewertung: 4.5 von 5 Sternen4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealVon EverandOn Fire: The (Burning) Case for a Green New DealBewertung: 4 von 5 Sternen4/5 (74)
- The Unwinding: An Inner History of the New AmericaVon EverandThe Unwinding: An Inner History of the New AmericaBewertung: 4 von 5 Sternen4/5 (45)
- Web Services TutorialDokument4 SeitenWeb Services Tutorialapi-19921804Noch keine Bewertungen
- 4.5raw Layer7Dokument24 Seiten4.5raw Layer7Haris ErnandhaniNoch keine Bewertungen
- MikroTik Routers and Wireless - Products - hAP Ac Lite TCDokument7 SeitenMikroTik Routers and Wireless - Products - hAP Ac Lite TCTomas Rodriguez RamirezNoch keine Bewertungen
- Lab 5Dokument12 SeitenLab 5Tomas Rodriguez RamirezNoch keine Bewertungen
- Lab 9Dokument16 SeitenLab 9Tomas Rodriguez RamirezNoch keine Bewertungen
- Lab 2Dokument13 SeitenLab 2Tomas Rodriguez RamirezNoch keine Bewertungen
- Lab 4Dokument6 SeitenLab 4Tomas Rodriguez RamirezNoch keine Bewertungen
- OSPF Authentication II: Objective Lab TopologyDokument9 SeitenOSPF Authentication II: Objective Lab TopologyTomas Rodriguez RamirezNoch keine Bewertungen
- Lab 1Dokument10 SeitenLab 1Tomas Rodriguez RamirezNoch keine Bewertungen
- IP Access Lists: Objective Lab TopologyDokument5 SeitenIP Access Lists: Objective Lab TopologyTomas Rodriguez RamirezNoch keine Bewertungen
- Lab 2Dokument9 SeitenLab 2Tomas Rodriguez RamirezNoch keine Bewertungen
- Lab 3Dokument16 SeitenLab 3Tomas Rodriguez RamirezNoch keine Bewertungen
- Lab 4Dokument14 SeitenLab 4Tomas Rodriguez RamirezNoch keine Bewertungen
- Lab 5Dokument13 SeitenLab 5Tomas Rodriguez RamirezNoch keine Bewertungen
- ACLDokument69 SeitenACLr00t32Noch keine Bewertungen
- Practica de LaboratorioDokument10 SeitenPractica de LaboratorioTomas Rodriguez RamirezNoch keine Bewertungen
- Lab 1Dokument11 SeitenLab 1Tomas Rodriguez RamirezNoch keine Bewertungen
- Microsoft Certification Exam Voucher PricesDokument12 SeitenMicrosoft Certification Exam Voucher PricesTomas Rodriguez RamirezNoch keine Bewertungen
- Huawei GPon Data Sheet PDFDokument2 SeitenHuawei GPon Data Sheet PDFKaye Chris AbalosNoch keine Bewertungen
- Assignment AJPDokument3 SeitenAssignment AJPSomesh ShewalkarNoch keine Bewertungen
- Tutorial 4Dokument4 SeitenTutorial 4HEMANILASHINII A P R THARMALINGAMNoch keine Bewertungen
- What Is OSI ModelDokument3 SeitenWhat Is OSI ModelAhmad Raza100% (1)
- 3.4.2.6 LabDokument17 Seiten3.4.2.6 LabJeanly JalandoniNoch keine Bewertungen
- 802.11 AMPDU and AMSDU Performance 2007Dokument5 Seiten802.11 AMPDU and AMSDU Performance 2007Fabian TrumperNoch keine Bewertungen
- Huawei NE20E-S Router Product BrochureDokument8 SeitenHuawei NE20E-S Router Product BrochureFernando Huanca AlaviNoch keine Bewertungen
- ODR002013 Configure QoS On NE Series Routers ISSUE1.02 PDFDokument128 SeitenODR002013 Configure QoS On NE Series Routers ISSUE1.02 PDFbetofranco530Noch keine Bewertungen
- SM 25xx ETA2 DB ENG PDFDokument24 SeitenSM 25xx ETA2 DB ENG PDFCristian CastellanosNoch keine Bewertungen
- HCNP-R&S-IERS Implementing Enterprise Routing and Switching Network Training V2.0Dokument480 SeitenHCNP-R&S-IERS Implementing Enterprise Routing and Switching Network Training V2.0Teferi BarantoNoch keine Bewertungen
- Computer Network MCQDokument118 SeitenComputer Network MCQMohammad Mizanur Rahman Nayan100% (4)
- Ruckus Icx Family Sales GuideDokument2 SeitenRuckus Icx Family Sales GuideRenataEMJNoch keine Bewertungen
- Wcb/Mcgraw-Hill The Mcgraw-Hill Companies, Inc., 1998Dokument16 SeitenWcb/Mcgraw-Hill The Mcgraw-Hill Companies, Inc., 1998Vinay MadhavNoch keine Bewertungen
- Brand Model Interface Form Factor CapacitiesDokument44 SeitenBrand Model Interface Form Factor CapacitiesICT Dosq28Noch keine Bewertungen
- New Gotocert 200-150 Dumps PDF - DCICN Introducing Cisco Data Center NetworkingDokument7 SeitenNew Gotocert 200-150 Dumps PDF - DCICN Introducing Cisco Data Center NetworkingKathrine E. LindleyNoch keine Bewertungen
- Isp Readiness - KJ Teoh NTT MSCDokument14 SeitenIsp Readiness - KJ Teoh NTT MSCmsyukorNoch keine Bewertungen
- Cisco Networking Academy Program. CCNA 3 and 4 Companion GuideDokument752 SeitenCisco Networking Academy Program. CCNA 3 and 4 Companion GuideKatamba RogersNoch keine Bewertungen
- FinalDokument25 SeitenFinalsachin prajapatiNoch keine Bewertungen
- CCN Practical No.7Dokument7 SeitenCCN Practical No.7Gaurang GawasNoch keine Bewertungen
- BPG N PlatformDokument50 SeitenBPG N PlatformHitesh RahangdaleNoch keine Bewertungen
- Part 1: Getting Started: CSE342 - Lab 4: Packet Sniffing With WiresharkDokument16 SeitenPart 1: Getting Started: CSE342 - Lab 4: Packet Sniffing With WiresharkAjay Pratap SinghNoch keine Bewertungen
- OSI Model: Functions of Physical LayerDokument13 SeitenOSI Model: Functions of Physical LayerMuhammad FayazNoch keine Bewertungen
- Latihan Soal MTCRE 2019 (Buat Ujian)Dokument9 SeitenLatihan Soal MTCRE 2019 (Buat Ujian)tugas simdigNoch keine Bewertungen
- Using Using Using Using Using Using Using Namespace Public Partial Class PublicDokument4 SeitenUsing Using Using Using Using Using Using Namespace Public Partial Class PublicAndrei BotnariNoch keine Bewertungen
- MA29Dokument1 SeiteMA29Kwun Hok ChongNoch keine Bewertungen
- Mobile IpDokument7 SeitenMobile IpAlejandro VasquezNoch keine Bewertungen
- SIP Tutorial - A Guide To Session Initiation Protocol (SIP)Dokument45 SeitenSIP Tutorial - A Guide To Session Initiation Protocol (SIP)PT50% (4)
- Huawei Optical Product Line Summary JuneDokument9 SeitenHuawei Optical Product Line Summary JuneMKEBRENoch keine Bewertungen