Beruflich Dokumente
Kultur Dokumente
Implications On Mobility PDF
Hochgeladen von
Nabila0 Bewertungen0% fanden dieses Dokument nützlich (0 Abstimmungen)
38 Ansichten4 SeitenOriginaltitel
IMPLICATIONS ON MOBILITY.pdf
Copyright
© © All Rights Reserved
Verfügbare Formate
PDF, TXT oder online auf Scribd lesen
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
© All Rights Reserved
Verfügbare Formate
Als PDF, TXT herunterladen oder online auf Scribd lesen
0 Bewertungen0% fanden dieses Dokument nützlich (0 Abstimmungen)
38 Ansichten4 SeitenImplications On Mobility PDF
Hochgeladen von
NabilaCopyright:
© All Rights Reserved
Verfügbare Formate
Als PDF, TXT herunterladen oder online auf Scribd lesen
Sie sind auf Seite 1von 4
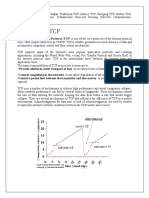
IMPLICATIONS ON MOBILITY - TCP: -
➢ While slow start is one of most useful mechanism in a
fixed network, it drastically reduces the efficiency of
the TCP if used in a mobile receiver or sender.
➢ The reason for this is that slow start mechanism may
be initiated for wrong reasons. Missing ACK in case of
mobile nodes is very common which may be due to
mobility or due to any interruption.
➢ Also, error rates, packet loss on wireless links are
order of magnitude and cannot be always
compensated by retransmissions or error correction
mechanisms.
➢ Mobility itself can cause packet loss. There are many
situations when a soft handover is not possible for
mobile end system. This results in loss of packet that
are in transit to the old foreign agent while the nodes
move to the new foreign agent. This loss is nothing to
do with wireless access but it is a rerouting problem.
➢ As already brought out, receipt of the three or more
ACK for the same packet is identified as loss of a single
packet and appropriate action is taken and loss of ACK
for a time that is much more than RTT is identified as
congestion and slow start mechanism is invoked. Both
these cannot be applied for the Mobile devices as
more often, loss of packet can take place for reason
other than these as well.
➢ Also, for the sake of mobile devices, on cannot change
the TCP protocol that encompasses the inter globe.
Hence new methods were devised that are discussed
below:
Classical TCP
i) Indirect TCP (I-TCP):
This method has been developed based on two
premises.
1. TCP performs poorly together with wireless
links
2. TCP within the fixed network cannot be
changed.
➢ I-TCP segments a TCP connection to a mobile device
into a fixed part and a wireless part. As shown below.
In this, the standard TCP is connected between fixed
host and the foreign agent (Access Point). Whereas the
‘Wireless TCP’ is connected between the Access point
and the Mobile host.
➢ IN this the access point acts as a proxy for both fixed
and mobile nodes. In case of fixed nodes, it is the
mobile node proxy and in case of mobile host, it is the
fixed node proxy. Foreign agent (access point) is
selected as proxy as it controls the mobility of the most
host. However, one can identify the TCP connection
separation at a special server at the entry point to a
mobile network (e.g. IWF - Inter Working Function in
GSM, GGSN in GPRS etc)
➢ The foreign acts as proxy and relays all data in both
directions. What is important to note in this case is
that the foreign agent itself responds to the receipt of
data from either hosts and send ACKs by itself. In case
the packet is lost in the wireless medium, the fixed
(correspondent) node will not notice this as the ACK is
already sent by the foreign agent. However, the
foreign agent tries to retransmit this packet locally to
maintain reliable data transport. Similarly, while the
mobile node sends data to foreign agent, if it is lost, the
mobile nodes identifies this much faster as the RTT up
to proxy is very much smaller and it retransmits the lost
packet.
➢ IN case of mobility of a mobile to a new access point,
this is intimated to the old access point and the data
are cached. This data is rerouted to new access point
along with the current TCP state such as sequence
number, address, ports etc.
➢ There are several advantages of this methods. these
are:
i) I-TCP does not require any change in the
existing TCP.
ii) Transmission in the wireless link like lost
packets, cannot propagate into the fixed
network.
iii) With I-TCP, new mechanism can be
introduced in the fixed network.
iv) Partitioning into two connections also allows
the use of different transport layer protocol
between the foreign agent and mobile host.
➢ Some of the disadvantages of the systems are listed
below;
i) End to end semantics of TCP is lost. The
correspondent always assumes that the receiver
has received the packet once it receives the ACKs
which always may not be case.
ii) Increased handover latency may be more
problematic. The old foreign agent needs to
buffer the packet that are destined for the mobile
node till it receives any information regarding its
current position. This may strain the resources of
the foreign agent.
➢ The foreign agent is to be a trusted agent. If the user
applies end to end encryption, the foreign
Das könnte Ihnen auch gefallen
- CCNA Interview Questions You'll Most Likely Be AskedVon EverandCCNA Interview Questions You'll Most Likely Be AskedNoch keine Bewertungen
- Introduction to Internet & Web Technology: Internet & Web TechnologyVon EverandIntroduction to Internet & Web Technology: Internet & Web TechnologyNoch keine Bewertungen
- Unit 5 Final NotesDokument20 SeitenUnit 5 Final Notesappsectesting3Noch keine Bewertungen
- 4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDokument16 Seiten4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDr. Sashi Kanth Reddy ANoch keine Bewertungen
- Unit-4: Indirect TCPDokument22 SeitenUnit-4: Indirect TCPSri Tulasi100% (1)
- Mobile TCPDokument7 SeitenMobile TCPTUSHARNoch keine Bewertungen
- Cs601 Unit VDokument20 SeitenCs601 Unit VRekha RahangdaleNoch keine Bewertungen
- Directorate of Technical Education, Tamilnadu: Thanthai Periyar Government Institute of Technology, Vellore-632002Dokument22 SeitenDirectorate of Technical Education, Tamilnadu: Thanthai Periyar Government Institute of Technology, Vellore-632002Karthick RaajNoch keine Bewertungen
- Snooping TCP As A Transparent TCP ExtensionDokument2 SeitenSnooping TCP As A Transparent TCP ExtensionKrishanu ModakNoch keine Bewertungen
- Unit Iii MC Mobile Transport Layer Part 4Dokument7 SeitenUnit Iii MC Mobile Transport Layer Part 4SLDFLAGNoch keine Bewertungen
- TCPFor WirelessDokument16 SeitenTCPFor WirelessZack StormNoch keine Bewertungen
- Chapte Rwise Content DocxDokument18 SeitenChapte Rwise Content DocxwexidaNoch keine Bewertungen
- DCN Unit-3saqDokument6 SeitenDCN Unit-3saqsravan kumarNoch keine Bewertungen
- Unit 5Dokument26 SeitenUnit 5ashwani tyagiNoch keine Bewertungen
- MC Unit 4Dokument28 SeitenMC Unit 4Naveenkumar TariNoch keine Bewertungen
- Unit Iii: Transport LayerDokument47 SeitenUnit Iii: Transport Layerg ezhilNoch keine Bewertungen
- Indirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerDokument12 SeitenIndirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerMukesh91% (220)
- TCP Over Wireless: Dr. RitikaDokument53 SeitenTCP Over Wireless: Dr. RitikamonumunduriNoch keine Bewertungen
- TCP For Wireless NetworksDokument16 SeitenTCP For Wireless NetworksAnbarasan TRNoch keine Bewertungen
- Mobile & Wireless NetworkingDokument38 SeitenMobile & Wireless NetworkingaishwaryaNoch keine Bewertungen
- Unit IV Mobile Transport LayerDokument10 SeitenUnit IV Mobile Transport LayerShradha PandeyNoch keine Bewertungen
- Transport Layer ProtocolDokument28 SeitenTransport Layer ProtocolShivanisAccountNoch keine Bewertungen
- Part 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersDokument6 SeitenPart 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersKani MozhiNoch keine Bewertungen
- Mobile Transport ProtocolsDokument15 SeitenMobile Transport ProtocolsAditya SinghNoch keine Bewertungen
- Rejinpaul MC UNIT4Dokument27 SeitenRejinpaul MC UNIT4SENTHIL VNoch keine Bewertungen
- A Comparison of Techniques For Improving TCP Performance Over Wireless LinksDokument4 SeitenA Comparison of Techniques For Improving TCP Performance Over Wireless LinksMuthu Vijay DeepakNoch keine Bewertungen
- A Solution For Improving TCP Performance Over Wireless LinksDokument12 SeitenA Solution For Improving TCP Performance Over Wireless LinksBirsh EndawkieNoch keine Bewertungen
- Rejinpaul MC UNIT4Dokument28 SeitenRejinpaul MC UNIT4Ganesh KumarNoch keine Bewertungen
- TCP IP Over Satellite - Yi ZhangDokument8 SeitenTCP IP Over Satellite - Yi ZhangAhmadHambaliNoch keine Bewertungen
- Mobile Communications Chapter 9: Mobile Transport Layer: Motivation TCP-mechanisms Classical ApproachesDokument18 SeitenMobile Communications Chapter 9: Mobile Transport Layer: Motivation TCP-mechanisms Classical Approacheschandra100% (1)
- Mobile Communications Chapter 9: Mobile Transport Layer: Motivation TCP-mechanisms Classical ApproachesDokument18 SeitenMobile Communications Chapter 9: Mobile Transport Layer: Motivation TCP-mechanisms Classical ApproachesArulNoch keine Bewertungen
- CN Unit IIIDokument40 SeitenCN Unit IIIVIJAY KARTHICK X CSE studentNoch keine Bewertungen
- Unit 4Dokument14 SeitenUnit 4126 Kavya sriNoch keine Bewertungen
- LTE Telkomsel Partner Development (1) Datacom & LTE Transport Architecture Overview PDFDokument22 SeitenLTE Telkomsel Partner Development (1) Datacom & LTE Transport Architecture Overview PDFAlif CalligoNoch keine Bewertungen
- Unit IiDokument9 SeitenUnit Iimoneeranaaz11Noch keine Bewertungen
- Mobile Transport Layer Implications On MobilityDokument4 SeitenMobile Transport Layer Implications On MobilityrosmyNoch keine Bewertungen
- Unit Iv: Mobile TCP and WapDokument70 SeitenUnit Iv: Mobile TCP and WapIliyas AhamedNoch keine Bewertungen
- Assign3 SolutionDokument8 SeitenAssign3 SolutionBintang Mandala PutraNoch keine Bewertungen
- 1 Compare I-TCP, S-TCP and M-TCP 2 Understand CO3: Assignment # 2Dokument8 Seiten1 Compare I-TCP, S-TCP and M-TCP 2 Understand CO3: Assignment # 2wexidaNoch keine Bewertungen
- Full Form and Their UsesDokument4 SeitenFull Form and Their UsesAchyutDashputeNoch keine Bewertungen
- Mod. 3.3 Indirect TCP, Snooping TCP, Mobile TCPDokument18 SeitenMod. 3.3 Indirect TCP, Snooping TCP, Mobile TCPkhanvilkarshruti6Noch keine Bewertungen
- C08 Transport ProtocolsDokument19 SeitenC08 Transport ProtocolsraghuippiliNoch keine Bewertungen
- MC CH-3Dokument25 SeitenMC CH-3faayaoromoo14Noch keine Bewertungen
- 2010 MC1633 (1) MTLDokument32 Seiten2010 MC1633 (1) MTLjavednjavedNoch keine Bewertungen
- Mobile Communications Chapter 9: Mobile Transport Layer: Additional OptimizationsDokument23 SeitenMobile Communications Chapter 9: Mobile Transport Layer: Additional OptimizationsVidya ANoch keine Bewertungen
- Assignment # 01: Wireless and Mobile ComputingDokument4 SeitenAssignment # 01: Wireless and Mobile ComputingHamza TararNoch keine Bewertungen
- Mobile Communications Mobile Transport LayerDokument18 SeitenMobile Communications Mobile Transport LayerChaudhary AdnanNoch keine Bewertungen
- Unit-3 Mobile Transport LayerDokument34 SeitenUnit-3 Mobile Transport LayerMprabha KaranNoch keine Bewertungen
- Unit 5Dokument10 SeitenUnit 5Dhanashri DevalapurkarNoch keine Bewertungen
- Cn-Unit 3Dokument59 SeitenCn-Unit 3b.nandhu2810Noch keine Bewertungen
- Mid Term Subjective Cs610Dokument5 SeitenMid Term Subjective Cs610Rashid MehmoodNoch keine Bewertungen
- PAPER Jan 2019Dokument5 SeitenPAPER Jan 2019RheaNoch keine Bewertungen
- CN Ass 3 SolnDokument10 SeitenCN Ass 3 SolnNoobs RageNoch keine Bewertungen
- CN Model PaperDokument5 SeitenCN Model PaperPavithraNoch keine Bewertungen
- Mobile Transport Layer: Presented by - Nilesh JadavDokument27 SeitenMobile Transport Layer: Presented by - Nilesh JadavMfleh MflehNoch keine Bewertungen
- C09 Transport ProtocolsDokument18 SeitenC09 Transport ProtocolsSenthil RNoch keine Bewertungen
- Mobile Communications Chapter 9: Mobile Transport LayerDokument13 SeitenMobile Communications Chapter 9: Mobile Transport Layernero neroNoch keine Bewertungen
- Mobile Transport LayerDokument18 SeitenMobile Transport LayervalansterNoch keine Bewertungen
- C09-Transport ProtocolsDokument18 SeitenC09-Transport ProtocolsArul JothiNoch keine Bewertungen
- La Naval Drug Co Vs CA G R No 103200Dokument2 SeitenLa Naval Drug Co Vs CA G R No 103200UE LawNoch keine Bewertungen
- Inv69116728 45926324Dokument1 SeiteInv69116728 45926324dany.cantaragiuNoch keine Bewertungen
- Section 12-22, Art. 3, 1987 Philippine ConstitutionDokument3 SeitenSection 12-22, Art. 3, 1987 Philippine ConstitutionKaren LabogNoch keine Bewertungen
- Braided Composites ModellingDokument33 SeitenBraided Composites ModellingaamirmubNoch keine Bewertungen
- Product Information DIGSI 5 V07.50Dokument56 SeitenProduct Information DIGSI 5 V07.50g-bearNoch keine Bewertungen
- BSNL Project MBA NitishDokument92 SeitenBSNL Project MBA NitishAnkitSingh0% (2)
- Lich King Chorus PDFDokument21 SeitenLich King Chorus PDFMacgy YeungNoch keine Bewertungen
- Consolidated Companies ListDokument31 SeitenConsolidated Companies ListSamir OberoiNoch keine Bewertungen
- Valery 1178Dokument22 SeitenValery 1178valerybikobo588Noch keine Bewertungen
- Point of View Task CardsDokument7 SeitenPoint of View Task Cardsapi-660227300Noch keine Bewertungen
- LEBV4830Dokument371 SeitenLEBV4830anton100% (1)
- Schema Elctrica Placa Baza Toshiba A500-13wDokument49 SeitenSchema Elctrica Placa Baza Toshiba A500-13wnicmaxxusNoch keine Bewertungen
- Financial Analysis of OGDCLDokument16 SeitenFinancial Analysis of OGDCLsehrish_sadaqat7873100% (1)
- Lecture Notes (Financial Economics)Dokument136 SeitenLecture Notes (Financial Economics)americus_smile7474100% (2)
- PLLV Client Consent FormDokument4 SeitenPLLV Client Consent Formapi-237715517Noch keine Bewertungen
- Safe and Gentle Ventilation For Little Patients Easy - Light - SmartDokument4 SeitenSafe and Gentle Ventilation For Little Patients Easy - Light - SmartSteven BrownNoch keine Bewertungen
- Revised Estimate Draft 24-12-2021Dokument100 SeitenRevised Estimate Draft 24-12-2021Reenu CherianNoch keine Bewertungen
- KEC International Limited: Pile FoundationDokument49 SeitenKEC International Limited: Pile FoundationDinesh Kumar100% (1)
- Consolidated Digests - Part 2Dokument314 SeitenConsolidated Digests - Part 2Neil Patrick Pepito ErmacNoch keine Bewertungen
- Juegos PPCDokument8 SeitenJuegos PPCikro995Noch keine Bewertungen
- ETA-1 Service PDFDokument44 SeitenETA-1 Service PDFgansolNoch keine Bewertungen
- The Truth About Customer ExperienceDokument11 SeitenThe Truth About Customer Experienceaksr27Noch keine Bewertungen
- MF 660Dokument7 SeitenMF 660Sebastian Vasquez OsorioNoch keine Bewertungen
- What Is SAP PS (Project Systems) ModuleDokument3 SeitenWhat Is SAP PS (Project Systems) ModuleahmerNoch keine Bewertungen
- Project of Consumer BehaviourDokument28 SeitenProject of Consumer BehaviourNaveed JuttNoch keine Bewertungen
- High-Definition Multimedia Interface SpecificationDokument51 SeitenHigh-Definition Multimedia Interface SpecificationwadrNoch keine Bewertungen
- Audi Navigation System Plus - MMI Operating ManualDokument100 SeitenAudi Navigation System Plus - MMI Operating ManualchillipaneerNoch keine Bewertungen
- HANA Heroes 1 - EWM Lessons Learned (V2)Dokument40 SeitenHANA Heroes 1 - EWM Lessons Learned (V2)Larissa MaiaNoch keine Bewertungen
- Low Cost CompaniesDokument9 SeitenLow Cost CompaniesIvan RodriguezNoch keine Bewertungen
- DSP Unit V ObjectiveDokument4 SeitenDSP Unit V Objectiveshashi dharNoch keine Bewertungen