Beruflich Dokumente
Kultur Dokumente
Network Security Lab
Hochgeladen von
Dayanand Gowda KrOriginaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Network Security Lab
Hochgeladen von
Dayanand Gowda KrCopyright:
Verfügbare Formate
Government of Karnataka
Department of Technical Education
Bengaluru
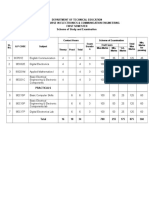
Course Title: Network Security Lab
Course Code:
Scheme (L:T:P) : 0:2:4 Total Contact Hours: 78
15CS65P
Type of Course: Tutorial and Credit :03 Core/ Elective:
Practical’s Core
CIE- 25 Marks SEE- 50 Marks
Prerequisites
Knowledge of Computer Network Softwares and Components.
Course Objectives
1. Installation of relevant softwares to Demonstrate Virtual box, port scanning, Finding
active machines and version of remote OS.
2. Demonstrate active and passive fingerprinting, sniffing the router traffic, use of
dumpsec.
3. Perform wireless audit of an access point, ARP poisioning, IPCop installation, study
of various crypto algorithms.
4. Demonstrate IDS, Rootkits, Open ssl command, setup and monitoring honeypot.
Course Outcome
On successful completion of the course, the students will be able to attain CO:
Experiment CL Linked Teaching
Course Outcome PO Hrs
linked
CO1
Install and demonstrate virtual box or 1, 2
any other equivalent software and A 1 to 10 09
Grabbing banner with telnet and netcat
CO2
Demonstrate port scanning, active 3,4 1 to 10
machines, version of remote OS using A 12
NMAP or any other software.
CO3
Experiment on active and passive 5 to 7 1 to 10
fingerprinting, sniffing the router traffic, A 15
use of dumpsec
CO4
Demonstrate wireless audit of an access 8 to 10 1 to 10
point, ARP poisoning, IPCop Firewall A 18
installation using relevant softwares.
CO5 Demostrate different cryptoalgorithms, 11 to 13 1 to 10 15
IDS, Rootkits using suitable softwares.
CO6 Demonstrate open ssl command, setup 14,15 1 to 10 09
A
and monitor honeypot on network.
Total sessions 78
Legends: R = Remember U= Understand; A= Apply and above levels (Bloom’s revised
taxonomy)
Directorate of Technical Education Karnataka State CS&E 15CS65P
Course-PO Attainment Matrix
Course Programme Outcomes
1 2 3 4 5 6 7 8 9 10
Network Security Lab 3 3 3 3 3 3 3 3 3 3
Level 3- Highly Addressed, Level 2-Moderately Addressed, Level 1-Low Addressed.
Method is to relate the level of PO with the number of hours devoted to the COs which address the given PO.
If >40% of classroom sessions addressing a particular PO, it is considered that PO is addressed at Level 3
If 25 to 40% of classroom sessions addressing a particular PO, it is considered that PO is addressed at Level 2
If 5 to 25% of classroom sessions addressing a particular PO, it is considered that PO is addressed at Level 1
If < 5% of classroom sessions addressing a particular PO, it is considered that PO is considered not-addressed.
List of Graded Practical Exercises
Sl.No Practical/Exercise
1 Learn to install Wine/Virtual Box/ or any other equivalent s/w on the host OS
2 Perform an experiment to grab a banner with telnet and perform the task using
Netcat
3 Perform an experiment for Port Scanning with nmap, superscan or any other
equivalent software
4 Using nmap 1)Find Open ports on a system 2) Find machines which are active
3)Find the version of remote OS on other systems 4)Find the version of s/w installed
on other system (using nmap or any othe software)
5 Perform an experiment on Active and Passive finger printing using XProbe2 and
nmap
6 Perform an experiment to demonstrate how to sniff for router traffic by using the
tool Cain and Abel / wireshark / tcpdump
7 Perform an experiment how to use DumpSec.
8 Perform an wireless audit of an access point / router and decrypt WEP and WPA
(softwares netstumbler or airsniff)
9 Perform an experiment to sniff traffic using ARP poisoning
10 Install IPCop on a linux system and learn all the function available on the software.
11 Install JCrypt tool (or any other equivalent) and demonstrate Asymmetric,
Symmetric crypto algorithm, Hash and Digital/PKI signatures studied in theory
Network Security and Management
12 Demonstrate Intrusion Detection System (IDS) using any tool eg. Snort or any other
s/w
13 Install RootKits and study variety of opt
14 Generate minimum 10 passwords of length 12 characters using open ssl command
15 Setup a honey pot and monitor the honey pot on network
Reference
Build Your Own Security Lab: A field guide for network Testing, Michael Gregg, Wiley
India edition, ISBN: 9788126516919.
Suggested list of student activities
Note: the following activities or similar activities for assessing CIE (IA) for 5 marks (Any one)
Directorate of Technical Education Karnataka State CS&E 15CS65P
1. Each individual student should do any one of the following type activity or any other
similar activity related to the course and before conduction, get it approved from
concerned course co-ordinator and programme co-ordinator.
2. Each student should conduct different activity and no repeating should occur.
1. Demonstration of various software’s used for port scanning.
2. Report on result of various crypto algorithms by using equivalent software.
3. Prepare a report on firewall along with its uses and functions.
Course Delivery
The course will be delivered through Demonstration and Practices
Course Assessment and Evaluation Scheme
When/Where
To (Frequency Max Evidence Course
Method What
whom in the Marks collected outcomes
course)
IA Students Two tests 10 Blue books 1,2,3,4,5,6
(average of
two tests)
CIE Record 10 Record 1,2,3,4,5,6
Direct Assessment
(Continuous
Internal Student 05
Evaluation) activity. Report.
Total 25
SEE End End of the 50 Answer scripts 1,2,3,4,5,6
(Semester Exam course at BTE
End
Examination)
Student Feedback on Students Middle of the Feedback 1,2,3
course course forms Delivery of
course
Indirect Assessment
End of Course End of the Questionnaires 1,2,3,4,5,6
Survey course Effectiveness
of Delivery
of
instructions
&
Assessment
Methods
*CIE – Continuous Internal Evaluation *SEE – Semester End Examination
Note:
1. I.A. test shall be conducted as per SEE scheme of valuation. However obtained marks
shall be reduced to 10 marks. Average marks of two tests shall be rounded off to the next
higher digit.
2. Rubrics to be devised appropriately by the concerned faculty to assess Student
activities.
Directorate of Technical Education Karnataka State CS&E 15CS65P
Questions for CIE and SEE will be designed to evaluate the various educational
components (Bloom’s taxonomy) such as:
Sl. No Bloom’s Category %
1 Remembrance 10
2 Understanding 20
3 Application 70
Note to IA verifier: The following documents to be verified by CIE verifier at the end of
semester
1. Blue books (10 marks)
2. Record (10 marks)
3. Student suggested activities report for 5 marks
4. Student feedback on course regarding Effectiveness of Delivery of instructions &
Assessment Methods.
Format for Student Activity Assessment
DIMENSION Unsatisfactory Developing Satisfactory Good Exemplary Score
1 2 3 4 5
Collection of Does not Collects Collects CollectsCollects a 3
data collect any very limited some basic relevantgreat deal of
information information; information; information;
information;
relating to the some relate refer to the concerned
all refer to
topic to the topic topic to the topic
the topic
Fulfill team’s Does not Performs Performs Performs all
Performs all 4
roles & duties perform any very little nearly all duties duties of
duties assigned duties duties assigned
to the team team roles
role with
presentation
Shares work Always relies Rarely does Usually Does the Always 3
equally on others to do the assigned does the assigned job does the
the work work; often assigned without assigned
needs work; rarely having to be work
reminding needs reminded. without
reminding having to be
reminded
and on
given time
frame
Listen to Is always Usually Listens, but Listens and Listens and 3
other Team talking; never does most sometimes contributes contributes
mates allows anyone of the talk too to the precisely to
else to speak talking; much relevant the relevant
rarely topic topic and
allows exhibit
others to leadership
speak qualities
TOTAL 13/4=3.25=4
Note: This is only an example. Appropriate rubrics/criteria may be devised by the
Directorate of Technical Education Karnataka State CS&E 15CS65P
concerned Course Coordinator for assessing the given activity
Scheme of Valuation for End Examination
SN Particulars Marks
1 Record 05
2 Installation of tool (Any two) 15
3 Conduction and Demonstration 20
4 Viva Voce 10
Total 50
**Evaluation should be based on the screen output only. No hard copy required.
**Change of question is allowed only once. Marks of 05 should be deducted in the given
question.
Resource requirements for Network Security Lab
(For an Intake of 60 Students [3 Batches])
1) For all experiments the student must and should install software’s. After the demonstrate
the same be uninstalled. Each batch has to learn to install and use the tools. You can use any
other equivalent software’s other then the mentioned one.
2) The lab should have structured network with 10 mbps internet line. Using Virutal Box, two
OS can be installed on one machine, where in one OS acts as a client and other acts a server.
MODEL QUESTION BANK
1 Learn to install Wine/Virtual Box/ or any other equivalent s/w on the host OS
2 Perform an experiment to grab a banner with telnet and perform the task using Netcat
3 Perform an experiment for Port Scanning with nmap, superscan or any other equivalent
software
4 Using nmap 1)Find Open ports on a system 2) Find machines which are active 3)Find
the version of remote OS on other systems 4)Find the version of s/w installed on other
system (using nmap or any othe software)
5 Perform an experiment on Active and Passive finger printing using XProbe2 and nmap
6 Perform an experiment to demonstrate how to sniff for router traffic by using the tool
Cain and Abel / wireshark / tcpdump
7 Perform an experiment how to use DumpSec.
8 Perform an wireless audit of an access point / router and decrypt WEP and WPA
(softwares netstumbler or airsniff)
9 Perform an experiment to sniff traffic using ARP poisoning
10 Install IPCop on a linux system and learn all the function available on the software.
11 Install JCrypt tool (or any other equivalent) and demonstrate Asymmetric, Symmetric
crypto algorithm, Hash and Digital/PKI signatures studied in theory Network Security
and Management
12 Demonstrate Intrusion Detection System (IDS) using any tool eg. Snort or any other s/w
13 Install RootKits and study variety of opt
14 Generate minimum 10 passwords of length 12 characters using open ssl command
15 Setup a honey pot and monitor the honey pot on network
Directorate of Technical Education Karnataka State CS&E 15CS65P
Das könnte Ihnen auch gefallen
- CISSP Exam Prep Questions, Answers & ExplanationsDokument564 SeitenCISSP Exam Prep Questions, Answers & Explanationssiu manman100% (20)
- CYBER SECURITY PLAYBOOK ONE – TIER ZERODokument19 SeitenCYBER SECURITY PLAYBOOK ONE – TIER ZEROa1amarpatelNoch keine Bewertungen
- Boot Menu: Operating System PostDokument4 SeitenBoot Menu: Operating System Postjames paulNoch keine Bewertungen
- Cyber Threat IntelligenceDokument44 SeitenCyber Threat IntelligenceRushikaNoch keine Bewertungen
- Ad Psychology2Dokument46 SeitenAd Psychology2متابع بصمتNoch keine Bewertungen
- IC Digital Marketing Plan Template 10598Dokument2 SeitenIC Digital Marketing Plan Template 10598Wilder TrochezNoch keine Bewertungen
- NSC Exam Mark Scheme Autumn 2018Dokument13 SeitenNSC Exam Mark Scheme Autumn 2018Nixon Maharzan0% (1)
- 1076a-Proposal For Job Portal Development - MS - Technost IT Solutions WLLDokument6 Seiten1076a-Proposal For Job Portal Development - MS - Technost IT Solutions WLLTechnost IT Solutions SPCNoch keine Bewertungen
- What Is PPC? Learn Everything About PPC AdvertisingDokument6 SeitenWhat Is PPC? Learn Everything About PPC AdvertisingAddicted 2 PPCNoch keine Bewertungen
- Cybersecurity: Powerpoint TemplateDokument69 SeitenCybersecurity: Powerpoint TemplateJorge AlmeidaNoch keine Bewertungen
- Drugs Generic and Trade Names According to TerminologyDokument9 SeitenDrugs Generic and Trade Names According to TerminologyTahir MehmoodNoch keine Bewertungen
- List of Experiments: S. No Name of The Experiment Any Eight Experiments Should Be ConductedDokument100 SeitenList of Experiments: S. No Name of The Experiment Any Eight Experiments Should Be ConductedGangula Praneeth ReddyNoch keine Bewertungen
- Wifi Networking Guide WaspmoteDokument49 SeitenWifi Networking Guide WaspmoteAlejandro Martinez GarciaNoch keine Bewertungen
- Car ParkingDokument478 SeitenCar Parkingmohan890Noch keine Bewertungen
- Automatic Speed Control of VehiclesDokument3 SeitenAutomatic Speed Control of VehiclesVenky Venkat NuthakkiNoch keine Bewertungen
- Bs en 1011 Part 5Dokument14 SeitenBs en 1011 Part 5Asger14Noch keine Bewertungen
- Fishing in India MasemariDokument5 SeitenFishing in India MasemariRahul JadhavNoch keine Bewertungen
- Networking and Internet: by Chuck EasttomDokument42 SeitenNetworking and Internet: by Chuck EasttomAndi AuuNoch keine Bewertungen
- Hatsun Agro KarvyDokument13 SeitenHatsun Agro Karvyarif420_999Noch keine Bewertungen
- Web B Ased Learning (WBL)Dokument8 SeitenWeb B Ased Learning (WBL)Jahidul HaqueNoch keine Bewertungen
- Disclosure To Promote The Right To InformationDokument19 SeitenDisclosure To Promote The Right To Informationarindam_chowdhu1926Noch keine Bewertungen
- Decentralized Mobile Cloud ComputingDokument5 SeitenDecentralized Mobile Cloud ComputinggayathriNoch keine Bewertungen
- InternetDokument11 SeitenInternetenuNoch keine Bewertungen
- Make PVC Fishing JugsDokument2 SeitenMake PVC Fishing JugsHardii Fitrah Fadlan100% (1)
- Hi Tron Two Days IoT Internet of Things Professional Training BrochureDokument18 SeitenHi Tron Two Days IoT Internet of Things Professional Training BrochureomkardashetwarNoch keine Bewertungen
- Research On Consumer Behaviour in MobilesDokument19 SeitenResearch On Consumer Behaviour in MobilesDiwasNoch keine Bewertungen
- Sheheryar Naseer - SEO Expert - CVDokument1 SeiteSheheryar Naseer - SEO Expert - CVM. Sheheryar NaseerNoch keine Bewertungen
- 2019 Generic Pharmaceuticals Pricing Antitrust LitigationDokument524 Seiten2019 Generic Pharmaceuticals Pricing Antitrust LitigationAdam ForgieNoch keine Bewertungen
- How To Choose The Right Types of Fishing Rods PDFDokument2 SeitenHow To Choose The Right Types of Fishing Rods PDFFishing Gear GuideNoch keine Bewertungen
- .A Link Earning SheetDokument109 Seiten.A Link Earning SheetAnuj BhattNoch keine Bewertungen
- Most Read AloudDokument5 SeitenMost Read AloudabulfaiziqbalNoch keine Bewertungen
- Hybrid Electric VehiclesDokument16 SeitenHybrid Electric Vehiclestapas_kbNoch keine Bewertungen
- M.Tech Application LetterDokument2 SeitenM.Tech Application LetterSagar AryalNoch keine Bewertungen
- The Environment in BritainDokument2 SeitenThe Environment in BritainMercedes Jimenez RomanNoch keine Bewertungen
- Insight Mining: Most Important Step Creative DevelopmentDokument46 SeitenInsight Mining: Most Important Step Creative DevelopmentNesma Gamal100% (1)
- Target Marketing of BMW & Mithsubishi Electric VehiclesDokument2 SeitenTarget Marketing of BMW & Mithsubishi Electric VehiclessandarulewisNoch keine Bewertungen
- M.N.N. Appaji: M.SC (IT), M.B.A. (Finance), MCTS, MCP, CEHDokument44 SeitenM.N.N. Appaji: M.SC (IT), M.B.A. (Finance), MCTS, MCP, CEHM N N AppajiNoch keine Bewertungen
- How To Get 10K Real YouTube Views in A WeekDokument25 SeitenHow To Get 10K Real YouTube Views in A WeekNikhil Rao0% (1)
- Types of Business Entities in IndiaDokument13 SeitenTypes of Business Entities in IndiaDipali MahalleNoch keine Bewertungen
- Braking of Road VehiclesDokument2 SeitenBraking of Road VehiclesWietsche Clement William PennyNoch keine Bewertungen
- Gas Inventory Management System SDLCDokument29 SeitenGas Inventory Management System SDLCmax mishraNoch keine Bewertungen
- Digitaltrend in Download Vivek Bindra All Courses For FreeDokument7 SeitenDigitaltrend in Download Vivek Bindra All Courses For FreeMD MOINNoch keine Bewertungen
- Internet SecureDokument227 SeitenInternet Securemoizm53Noch keine Bewertungen
- Digital Marketing Course BrochureDokument18 SeitenDigital Marketing Course Brochureprem yadavNoch keine Bewertungen
- SAP Dictionary German EnglishDokument171 SeitenSAP Dictionary German EnglishlucascocsNoch keine Bewertungen
- Free SEO Audit ReportDokument8 SeitenFree SEO Audit ReportKiyan RoyNoch keine Bewertungen
- CV For PH.D AdmissionDokument2 SeitenCV For PH.D AdmissionIbrahimAkkiNoch keine Bewertungen
- Hatsun Agro ProductsDokument2 SeitenHatsun Agro ProductsUDDIPANA DIHINGIANoch keine Bewertungen
- Network Administration Lab Syllabus For Diploma 3rd Sem CSDokument6 SeitenNetwork Administration Lab Syllabus For Diploma 3rd Sem CSVishal Raj.VNoch keine Bewertungen
- STLABDokument5 SeitenSTLABKrishna RajbharNoch keine Bewertungen
- EE 353 Computer Networks-Fall 2022Dokument81 SeitenEE 353 Computer Networks-Fall 2022Muhammad TalhaNoch keine Bewertungen
- COmputer LabDokument9 SeitenCOmputer LabpnkjinamdarNoch keine Bewertungen
- DLP Lab ManualDokument72 SeitenDLP Lab ManualPoorna chand Evuru100% (1)
- CSL332 - KQB KtuQbankDokument6 SeitenCSL332 - KQB KtuQbankgjajNoch keine Bewertungen
- Digital Logic Lab Manual: KL University (2019-20Dokument38 SeitenDigital Logic Lab Manual: KL University (2019-20PAILA HEMANTHNoch keine Bewertungen
- 6ECE - CN Lab ManualDokument159 Seiten6ECE - CN Lab ManualDiya SharmaNoch keine Bewertungen
- Basics of Information Security Course Code: 4360702Dokument8 SeitenBasics of Information Security Course Code: 4360702BJAYG2005Noch keine Bewertungen
- Prepared By: Computer Network Lab ManualDokument47 SeitenPrepared By: Computer Network Lab ManualMadihaNoch keine Bewertungen
- Practical's Core: Course Outcome Experiment CL LinkedDokument5 SeitenPractical's Core: Course Outcome Experiment CL Linkedmanasa nagarajNoch keine Bewertungen
- Data Science Lab Python CourseDokument5 SeitenData Science Lab Python CourseNAJIYA NAZRIN P NNoch keine Bewertungen
- Lab Manual of Computer Networks Lab ETCS 354Dokument61 SeitenLab Manual of Computer Networks Lab ETCS 354vaibhav kashyapNoch keine Bewertungen
- NP Lab Manual v10 MMDokument79 SeitenNP Lab Manual v10 MMRajatNoch keine Bewertungen
- Ail411 DL Lab SyllubusDokument4 SeitenAil411 DL Lab SyllubusReemaNoch keine Bewertungen
- Government of Karnataka's Analog and Digital Lab CourseDokument12 SeitenGovernment of Karnataka's Analog and Digital Lab CourseHanduNoch keine Bewertungen
- Final - IT8761 Security Lab ManualDokument55 SeitenFinal - IT8761 Security Lab ManualShiek TiwariNoch keine Bewertungen
- EC1258 - Digital Electronics Laboratory Manual (REC)Dokument94 SeitenEC1258 - Digital Electronics Laboratory Manual (REC)jeyaganesh100% (8)
- 1 & 2 Sem Scheme of StudiesDokument2 Seiten1 & 2 Sem Scheme of StudiesDayanand Gowda KrNoch keine Bewertungen
- Oct2014Dokument2 SeitenOct2014Dayanand Gowda KrNoch keine Bewertungen
- Iv Eee I Sem MPMC Lab Manual (Ee432) PDFDokument50 SeitenIv Eee I Sem MPMC Lab Manual (Ee432) PDFjitendra jhaNoch keine Bewertungen
- Registers and Counters for Digital Logic DesignDokument42 SeitenRegisters and Counters for Digital Logic DesignDayanand Gowda KrNoch keine Bewertungen
- Network Security Mgmt.Dokument9 SeitenNetwork Security Mgmt.Dayanand Gowda Kr0% (1)
- Switch LevelDokument19 SeitenSwitch LevelDayanand Gowda KrNoch keine Bewertungen
- Outline of A Resistor - Electronics Basics - ROHMDokument5 SeitenOutline of A Resistor - Electronics Basics - ROHMDayanand Gowda KrNoch keine Bewertungen
- Introduction of Data CommunicationDokument19 SeitenIntroduction of Data CommunicationDayanand Gowda KrNoch keine Bewertungen
- KicadDokument19 SeitenKicadeusuntombunNoch keine Bewertungen
- Verilog Tutorial - and Gate With Test Bench - ElectroSoftsDokument4 SeitenVerilog Tutorial - and Gate With Test Bench - ElectroSoftsDayanand Gowda KrNoch keine Bewertungen
- Data Communication and NetworkDokument32 SeitenData Communication and NetworkDayanand Gowda KrNoch keine Bewertungen
- Using Telephone and Cable Networks For Data TransmissionDokument52 SeitenUsing Telephone and Cable Networks For Data TransmissionDayanand Gowda KrNoch keine Bewertungen
- WWW - Swarthmore.edu NatSci Echeeve1 Class E72 E72L1 Lab1 (Schem)Dokument7 SeitenWWW - Swarthmore.edu NatSci Echeeve1 Class E72 E72L1 Lab1 (Schem)Dayanand Gowda KrNoch keine Bewertungen
- Mat Lab NewDokument19 SeitenMat Lab NewDayanand Gowda KrNoch keine Bewertungen
- EMI 3unitDokument18 SeitenEMI 3unitDayanand Gowda KrNoch keine Bewertungen
- Data NetworksDokument26 SeitenData Networksanon_395780178Noch keine Bewertungen
- Resistors: Classification and characteristics guideDokument6 SeitenResistors: Classification and characteristics guideDayanand Gowda Kr100% (1)
- Basics of Data Communication and Computer Networking (262 KB)Dokument19 SeitenBasics of Data Communication and Computer Networking (262 KB)m_kanwar8652Noch keine Bewertungen
- Data Communication and Computer NetworksDokument23 SeitenData Communication and Computer NetworksPedro CostaNoch keine Bewertungen
- Logic Design Lab ManualDokument22 SeitenLogic Design Lab ManualAzarkhan Mokashi100% (1)
- Logic Design Lab ManualDokument22 SeitenLogic Design Lab ManualAzarkhan Mokashi100% (1)
- NetworkingDokument16 SeitenNetworkingIsha KapoorNoch keine Bewertungen
- Electronics Symbols PDFDokument8 SeitenElectronics Symbols PDFDayanand Gowda KrNoch keine Bewertungen
- Inductor SDokument2 SeitenInductor SDayanand Gowda KrNoch keine Bewertungen
- FilterDokument4 SeitenFilterJohny AugustNoch keine Bewertungen
- Resistors: Classification and characteristics guideDokument6 SeitenResistors: Classification and characteristics guideDayanand Gowda Kr100% (1)
- FilterDokument4 SeitenFilterJohny AugustNoch keine Bewertungen
- Innovative Techniques For Data Security - Version - Part 2Dokument44 SeitenInnovative Techniques For Data Security - Version - Part 2Miruna FloroiuNoch keine Bewertungen
- Cyberlaws and SecurityDokument1 SeiteCyberlaws and Security17001009023 HINGULA BHATNoch keine Bewertungen
- Chapter 5 - Basic CryptographyDokument59 SeitenChapter 5 - Basic CryptographymaryaNoch keine Bewertungen
- SPYWARE Vs ADWAREDokument3 SeitenSPYWARE Vs ADWARESiddhi ChavanNoch keine Bewertungen
- CIS Cisco Firewall Benchmark v4.0.0Dokument174 SeitenCIS Cisco Firewall Benchmark v4.0.0sobi_zubi0Noch keine Bewertungen
- CS-166 Project ProposalDokument3 SeitenCS-166 Project ProposalSanyami BhavsarNoch keine Bewertungen
- Virus ToolsDokument10 SeitenVirus ToolsHeetNoch keine Bewertungen
- Cryptography and Network Security 922887376Dokument2 SeitenCryptography and Network Security 922887376Shailendra Yadav25% (4)
- Owp Security Advanced Security 11gr 133411Dokument12 SeitenOwp Security Advanced Security 11gr 133411Dinesh KumarNoch keine Bewertungen
- Digital Signature ForuzanDokument47 SeitenDigital Signature ForuzanSagar Lodhiya0% (1)
- Nilesh ChouibisaDokument15 SeitenNilesh ChouibisaDhruv KanthaliyaNoch keine Bewertungen
- Information Security AssignmentDokument2 SeitenInformation Security AssignmentKashif UllahNoch keine Bewertungen
- Navigating PCI DSS v4.0Dokument24 SeitenNavigating PCI DSS v4.0Ivan DoriNoch keine Bewertungen
- TVL Empowerment Technologies Q3 M3Dokument8 SeitenTVL Empowerment Technologies Q3 M3DarkApostlesNoch keine Bewertungen
- Top 10 digital safety rulesDokument4 SeitenTop 10 digital safety rulesDanloyd QuijanoNoch keine Bewertungen
- MIS Threads and RisksDokument10 SeitenMIS Threads and RisksMidhun MadhavNoch keine Bewertungen
- Saas Provider Security Checklist: Watch This VideoDokument1 SeiteSaas Provider Security Checklist: Watch This VideomanishNoch keine Bewertungen
- Cracking Wi-Fi Using PythonDokument6 SeitenCracking Wi-Fi Using PythonInternational Journal of Innovative Science and Research TechnologyNoch keine Bewertungen
- Crime TheoryDokument9 SeitenCrime TheoryHillary OmondiNoch keine Bewertungen
- Chapter 1 - Controls On SecurityDokument15 SeitenChapter 1 - Controls On SecurityMohammad Rafsun IslamNoch keine Bewertungen
- Elliptic Curve Cryptography An Enhanced SecurityDokument6 SeitenElliptic Curve Cryptography An Enhanced SecuritysathyaNoch keine Bewertungen
- Top Hacker TED Talk Teaches Cybersecurity LessonsDokument1 SeiteTop Hacker TED Talk Teaches Cybersecurity LessonsFikri Prayogi ArdiansyahNoch keine Bewertungen
- Internet SecurityDokument12 SeitenInternet SecurityBogdan DanNoch keine Bewertungen
- Api SecurityDokument5 SeitenApi SecurityNaNoch keine Bewertungen
- Information SecurityDokument2 SeitenInformation Security3qtrtymNoch keine Bewertungen