Beruflich Dokumente
Kultur Dokumente
AEM Application SR - No Findings Severity Observation: Medium
Hochgeladen von
Seema Pal0 Bewertungen0% fanden dieses Dokument nützlich (0 Abstimmungen)
24 Ansichten2 SeitenThe summary identifies 4 medium to low severity issues found in an AEM application including: 1) Direct URL access allows downloading of user policy details, 2) Use of a vulnerable jQuery version, 3) Disclosure of server version information, and 4) Enabling of the HTTP OPTIONS method. Recommendations are provided to address each issue and their current status is marked as open.
Originalbeschreibung:
Originaltitel
Findings
Copyright
© © All Rights Reserved
Verfügbare Formate
XLSX, PDF, TXT oder online auf Scribd lesen
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenThe summary identifies 4 medium to low severity issues found in an AEM application including: 1) Direct URL access allows downloading of user policy details, 2) Use of a vulnerable jQuery version, 3) Disclosure of server version information, and 4) Enabling of the HTTP OPTIONS method. Recommendations are provided to address each issue and their current status is marked as open.
Copyright:
© All Rights Reserved
Verfügbare Formate
Als XLSX, PDF, TXT herunterladen oder online auf Scribd lesen
0 Bewertungen0% fanden dieses Dokument nützlich (0 Abstimmungen)
24 Ansichten2 SeitenAEM Application SR - No Findings Severity Observation: Medium
Hochgeladen von
Seema PalThe summary identifies 4 medium to low severity issues found in an AEM application including: 1) Direct URL access allows downloading of user policy details, 2) Use of a vulnerable jQuery version, 3) Disclosure of server version information, and 4) Enabling of the HTTP OPTIONS method. Recommendations are provided to address each issue and their current status is marked as open.
Copyright:
© All Rights Reserved
Verfügbare Formate
Als XLSX, PDF, TXT herunterladen oder online auf Scribd lesen
Sie sind auf Seite 1von 2
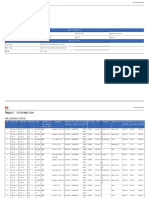
AEM Application
Sr.no Findings Severity Observation
It is observer that appication plans pdf
download directly, In which the user
1 Direct URL Access Medium
policy details and plan money are also
detected.
It is observed that application is using
2 Using known vulnerability LOW
vulnerable jQuery version
This information might help an attacker
gain a greater understanding of the
3 Server version disclosed LOW systems in use and potentially develop
further attacks targeted at the specific
version of AkamaiGhost.
It is observed that application allowed
the options method.Which provides a list
4 HTTP method enabled LOW
of methods that are supported by web
server.
EM Application
Instance Recommendation Status
you can use appropriate
permissions or ACLs to
disallow anonymous reading.
PRODUCTION Also, do not allow OPEN
anonymous web visitors user
read permissions to any
sensitive data files.
PRODUCTION Update to latest version OPEN
Configure your web server to
prevent information leakage
PRODUCTION OPEN
from the server header of its
HTTP response.
https://hostadvice.com/how-
to/how-to-disable-the-
PRODUCTION OPEN
vulnerability-of-options-
method-in-iis-and-apache/
Das könnte Ihnen auch gefallen
- Confining The Apache Web Server With Security-Enhanced LinuxDokument12 SeitenConfining The Apache Web Server With Security-Enhanced LinuxI srcNoch keine Bewertungen
- Report For Foophones: by Utkarsh MunraDokument37 SeitenReport For Foophones: by Utkarsh Munrasuraj fbNoch keine Bewertungen
- Detailed Scan ReportDokument23 SeitenDetailed Scan ReportAnas YogieNoch keine Bewertungen
- Web Application (Muthoot - Com) - Pentesting - Revalidation - Report - 26-4-2023Dokument148 SeitenWeb Application (Muthoot - Com) - Pentesting - Revalidation - Report - 26-4-202390harish87Noch keine Bewertungen
- Web Application Pentest 101Dokument121 SeitenWeb Application Pentest 101Azlan YatimNoch keine Bewertungen
- Website Vulnscan Sample ReportDokument6 SeitenWebsite Vulnscan Sample Reportबी० के० शर्माNoch keine Bewertungen
- Ridho Abdul MajidDokument24 SeitenRidho Abdul MajidRidho Abdul MajidNoch keine Bewertungen
- Web Application Development Dos and DontsDokument18 SeitenWeb Application Development Dos and DontsvietictNoch keine Bewertungen
- S G A - SDokument8 SeitenS G A - SsubhadipbhadraNoch keine Bewertungen
- A Framework For Spyware AssessmentDokument7 SeitenA Framework For Spyware AssessmentNamrata PaudelNoch keine Bewertungen
- KUBERA: A Security Model For Web Applications: Qiang Wang, Zhiguang QinDokument4 SeitenKUBERA: A Security Model For Web Applications: Qiang Wang, Zhiguang QinHaritha ChowdaryNoch keine Bewertungen
- Documento1 2Dokument4 SeitenDocumento1 2hajodocumentoNoch keine Bewertungen
- Building Secure High-Performance Web Services With OKWS: Maxwell Krohn, MIT Computer Science and AI LaboratoryDokument14 SeitenBuilding Secure High-Performance Web Services With OKWS: Maxwell Krohn, MIT Computer Science and AI LaboratoryalkalacidNoch keine Bewertungen
- API-Gateway Maven VulnerabilitiesDokument8 SeitenAPI-Gateway Maven VulnerabilitiesNiculescu AndreiNoch keine Bewertungen
- Linuxsec3e PPT ch06Dokument25 SeitenLinuxsec3e PPT ch06Pham Hung Thinh (K17 DN)Noch keine Bewertungen
- Pentest-Report Fdroid PDFDokument17 SeitenPentest-Report Fdroid PDFSheloqNoch keine Bewertungen
- Report On OWASP What Is OWASP?: Deep Nandu BED-C-48Dokument4 SeitenReport On OWASP What Is OWASP?: Deep Nandu BED-C-48deep nanduNoch keine Bewertungen
- Proxy FirewallDokument109 SeitenProxy Firewallapi-3725866Noch keine Bewertungen
- Fortipentest - User GuideDokument23 SeitenFortipentest - User GuideCarlos Arturo Castro GarciaNoch keine Bewertungen
- Ismlabda 4Dokument19 SeitenIsmlabda 4ARYA DUBEY 20BCE0908Noch keine Bewertungen
- Application Whitelisting Using SRPDokument19 SeitenApplication Whitelisting Using SRPMigor IgorNoch keine Bewertungen
- Web Application Development Dos and DontsDokument18 SeitenWeb Application Development Dos and DontsRavi BhushanNoch keine Bewertungen
- Project Title: Web Application Security Website:: Technologies UsedDokument12 SeitenProject Title: Web Application Security Website:: Technologies UsedzimgurNoch keine Bewertungen
- Web Server Vulnerabilities And Security Measures: Members: Vũ Hoàng Đinh Hoàng Phi Instructor: Msc Nguyễn DuyDokument23 SeitenWeb Server Vulnerabilities And Security Measures: Members: Vũ Hoàng Đinh Hoàng Phi Instructor: Msc Nguyễn Duynewlife439Noch keine Bewertungen
- Id Vul Id Description LinkDokument3 SeitenId Vul Id Description LinkIytzaz BarkatNoch keine Bewertungen
- 5 Common Web Application VulnerabilitiesDokument4 Seiten5 Common Web Application VulnerabilitiesAnonymous Fhs3ufkCNoch keine Bewertungen
- N' Talk UCO-529035 Sanchit Srivastava: PA 168: Post Graduate Seminar On IT Security and CryptographyDokument19 SeitenN' Talk UCO-529035 Sanchit Srivastava: PA 168: Post Graduate Seminar On IT Security and CryptographySanchit SrivastavaNoch keine Bewertungen
- System HardeningDokument36 SeitenSystem HardeningHarshithNoch keine Bewertungen
- Vastrzone Application Security Assessment Report DATE: 01 JUNE 2022Dokument17 SeitenVastrzone Application Security Assessment Report DATE: 01 JUNE 2022MAJ. VIKAS TYAGI DGR Batch 08Noch keine Bewertungen
- An Evaluation of The Google Chrome Extension SecurDokument16 SeitenAn Evaluation of The Google Chrome Extension SecurHaiNoch keine Bewertungen
- ATLASSIAN - Network and Connectivity Troubleshooting GuideDokument10 SeitenATLASSIAN - Network and Connectivity Troubleshooting GuidevishalrajkumarNoch keine Bewertungen
- SB04 133Dokument55 SeitenSB04 133eliasnumira6284Noch keine Bewertungen
- Audit Report: Audited On December 02 2011Dokument76 SeitenAudit Report: Audited On December 02 2011jhonhackodigeNoch keine Bewertungen
- OKWSDokument14 SeitenOKWSor2jdi8lNoch keine Bewertungen
- Cert-In Open Proxy Servers: IndexDokument7 SeitenCert-In Open Proxy Servers: IndexAmitesh AgarwalNoch keine Bewertungen
- ReportDokument22 SeitenReportappu12245Noch keine Bewertungen
- Sub BrowserDokument8 SeitenSub BrowserpostscriptNoch keine Bewertungen
- Web Application Vapt Cybersapiens United LLP: Report OnDokument19 SeitenWeb Application Vapt Cybersapiens United LLP: Report OnPavan Kumar Chinta100% (1)
- 8 Steps To Zero TrustDokument2 Seiten8 Steps To Zero Trust세인Noch keine Bewertungen
- #1 API Risk - Mitigation StrategyDokument10 Seiten#1 API Risk - Mitigation StrategyLucrécio Ricco AlmeidaNoch keine Bewertungen
- Log4Shell Exploit Report 1639388282Dokument7 SeitenLog4Shell Exploit Report 1639388282Julio SousaNoch keine Bewertungen
- DVWA v1.3Dokument16 SeitenDVWA v1.3sbeuhNoch keine Bewertungen
- Jaas in Action Chapter01 05Dokument13 SeitenJaas in Action Chapter01 05farrdy20Noch keine Bewertungen
- ReportDokument17 SeitenReportJay SoniNoch keine Bewertungen
- 20 - Web Application Security Testing Using Burp Suite (Compatibility Mode) PDFDokument35 Seiten20 - Web Application Security Testing Using Burp Suite (Compatibility Mode) PDFsamsNoch keine Bewertungen
- Vulnerability ReportDokument9 SeitenVulnerability ReportXc CristiNoch keine Bewertungen
- Information Disclosure VulnerabilityDokument8 SeitenInformation Disclosure Vulnerabilitysetyahangga3Noch keine Bewertungen
- Ai Web Report 1 1Dokument25 SeitenAi Web Report 1 1Suraj TheekshanaNoch keine Bewertungen
- Qulalys Sample ReportDokument6 SeitenQulalys Sample Reporteagleboy007Noch keine Bewertungen
- Log4Shell Report: Vulnerability Assessment and MitigationDokument7 SeitenLog4Shell Report: Vulnerability Assessment and MitigationEduardoNoch keine Bewertungen
- Web Application Security Standard PDFDokument5 SeitenWeb Application Security Standard PDFyshprasdNoch keine Bewertungen
- Cryptolocker Update RevDDokument4 SeitenCryptolocker Update RevDNomNoch keine Bewertungen
- Lapse Plus TutorialDokument11 SeitenLapse Plus TutorialadivishNoch keine Bewertungen
- API Security Best PracticesDokument4 SeitenAPI Security Best PracticesJknoxvilNoch keine Bewertungen
- FULL DOC of Hiding SensitiveDokument62 SeitenFULL DOC of Hiding SensitiveAnusha ReddyNoch keine Bewertungen
- Web Shells, Backdoor Trojans and Rats: Version: 2013-0011Dokument35 SeitenWeb Shells, Backdoor Trojans and Rats: Version: 2013-0011Auro AurelioNoch keine Bewertungen
- HTML IntroductionDokument36 SeitenHTML IntroductionKHAN_EROSNoch keine Bewertungen
- Unit 1 Introduction To Web TechnologiesDokument12 SeitenUnit 1 Introduction To Web TechnologiesME16 Krunal DeshmukhNoch keine Bewertungen
- Navigating The Internet (WWW) by Mr. N.P. Ravi KumarDokument25 SeitenNavigating The Internet (WWW) by Mr. N.P. Ravi Kumarsudheer babu arumbakaNoch keine Bewertungen
- HTMLDokument10 SeitenHTMLsreeni50% (2)
- API Hacking RESTful API 1Dokument4 SeitenAPI Hacking RESTful API 1mogogotNoch keine Bewertungen
- Native Web or Hybrid Mobile App DevelopmentDokument36 SeitenNative Web or Hybrid Mobile App DevelopmentShahar Kaminitz100% (6)
- 2.2 Day12-Locators PDFDokument27 Seiten2.2 Day12-Locators PDFQutab Kumar PatnaikNoch keine Bewertungen
- Question and Answers Part A (2 Marks) 1. Define The Term InternetDokument24 SeitenQuestion and Answers Part A (2 Marks) 1. Define The Term InternetNivi NivethaNoch keine Bewertungen
- Bug Bounty Hunting - Complete Guide To An Innovative Earning ProcessDokument4 SeitenBug Bounty Hunting - Complete Guide To An Innovative Earning ProcessHarsh ParasiyaNoch keine Bewertungen
- Ossec Web Ui 0 8 Site Searchp Cross Site Scripting PDFDokument4 SeitenOssec Web Ui 0 8 Site Searchp Cross Site Scripting PDFsavsabien972Noch keine Bewertungen
- Silabus WordpressDokument1 SeiteSilabus Wordpressarif wicaksonoNoch keine Bewertungen
- Building Your First Laravel ApplicationDokument38 SeitenBuilding Your First Laravel ApplicationFrancesco MartinoNoch keine Bewertungen
- C4C CertificateDokument2 SeitenC4C CertificateYogeshNoch keine Bewertungen
- Web Servers - Apache - UbuntuDokument13 SeitenWeb Servers - Apache - UbuntuLaVermineNoch keine Bewertungen
- Dynamic Rendering As A Workaround - Google Search Central - Documentation - Google For DevelopersDokument7 SeitenDynamic Rendering As A Workaround - Google Search Central - Documentation - Google For Developersrouleau.jasonNoch keine Bewertungen
- 09 JSP IntroDokument32 Seiten09 JSP IntroHercules LeNoch keine Bewertungen
- Web TechnologyDokument46 SeitenWeb TechnologyniraliNoch keine Bewertungen
- Automated QueriesDokument5 SeitenAutomated QueriestpspaceNoch keine Bewertungen
- Blood Bank Management SystemDokument3 SeitenBlood Bank Management Systemshruti sawalkarNoch keine Bewertungen
- Google Analytics: Beginners NotesDokument5 SeitenGoogle Analytics: Beginners NotesAavish GuptaNoch keine Bewertungen
- StageDokument14 SeitenStageRached TRNoch keine Bewertungen
- Computer Engineering Syllabus Sem V Mumbai UniversityDokument7 SeitenComputer Engineering Syllabus Sem V Mumbai UniversityVarunNoch keine Bewertungen
- Bootstrap 3 CSS Classes Desk ReferenceDokument8 SeitenBootstrap 3 CSS Classes Desk ReferenceBootstrap Creative100% (2)
- Soap PDFDokument49 SeitenSoap PDFmed_beNoch keine Bewertungen
- My Learnings in Java CourseDokument41 SeitenMy Learnings in Java CoursePREMOTH ANIRUTH T GNoch keine Bewertungen
- Advance Java First PresentationDokument8 SeitenAdvance Java First Presentationroy MuslimNoch keine Bewertungen
- Method Three: Greasemonkey Scripts: This SiteDokument2 SeitenMethod Three: Greasemonkey Scripts: This SiteScribdNoch keine Bewertungen
- CHR Online 20230921132430Dokument196 SeitenCHR Online 20230921132430intoisrNoch keine Bewertungen
- Social WebDokument192 SeitenSocial WebAshrin KumarNoch keine Bewertungen
- Postman 4Dokument80 SeitenPostman 4George MeloNoch keine Bewertungen