Beruflich Dokumente
Kultur Dokumente
Hipam Features
Hochgeladen von
HitachiIDCopyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Hipam Features
Hochgeladen von
HitachiIDCopyright:
Verfügbare Formate
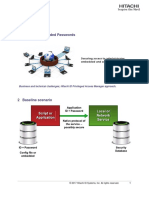
Hitachi ID Privileged Access Manager Features at a Glance
FEATURE: Infrastructure auto-discovery Description Privileged Access Manager periodically extracts a list of systems from a directory such as AD or from a source such as an IT inventory database. It then applies rules to decide which of these systems to manage. Managed systems are probed to nd accounts, groups and services on each one. Rules determine which of these accounts should be controlled by Privileged Access Manager. This process is normally run every 24 hours. Benet Auto-discovery is essential for deploying Privileged Access Manager in medium to large organizations, where there may be thousands of systems with accounts to secure and where hundreds of systems may be added, moved or retired daily.
FEATURE: Randomize passwords on privileged accounts Description Privileged Access Manager periodically randomizes passwords on every privileged account within its scope of authority. This is normally done daily. Benet Frequent password changes eliminate the possibility of password sharing or of access being retained by administrators after work is completed. Former IT staff lose access automatically.
FEATURE: Encrypted, replicated password vault Description Randomized passwords are encrypted and stored in a database. The database is replicated between at least two servers, installed in at least two physical locations. Benet Encryption and replication protects against inappropriate disclosure of sensitive passwords or loss of access to privileged accounts, even in the event of media theft, server crash or physical disaster at a data center.
FEATURE: Access control policies Description IT users sign into Privileged Access Manager to request access to privileged accounts. These requests are subject to access control rules, typically associating groups of users to groups of managed systems. Requests may also carry other data, such as incident numbers, which can be validated before access is granted. Benet Policies allow IT security to control who can sign into each system.
2011 Hitachi ID Systems, Inc. All rights reserved.
Privileged Access Manager Features at a Glance
FEATURE: One-time access request workow Description Users without pre-approved login rights can nonetheless request access to privileged accounts. These requests are subjected to a workow authorization process which may involve one or more approvers and which supports reminders, escalation, delegation, approval by multiple people and more. Benet Workow approvals supports a range of business processes, including production migration, a exible workforce and emergency access.
FEATURE: Single sign-on and other access disclosure methods Description Privileged Access Manager does not normally display passwords to privileged accounts from its vault. Instead, it may launch a login session automatically and inject credentials, or temporarily place a users AD domain account into a security group or create a temporary SSH trust relationship. Benet Users benet from single sign-on to privileged accounts while security is enhanced by avoiding password display and even knowledge of passwords by administrators.
FEATURE: Audit logs and reports Description Privileged Access Manager records every attempted, authorized and completed login to a privileged account. E-mail notications, incident management integration and built-in reports create accountability for access to privileged accounts. Benet Accountability motivates users to act appropriately and creates a forensic audit trail.
FEATURE: Session recording and forensic audits Description Privileged Access Manager can deploy an ActiveX control to an authorized users desktop to record login sessions to managed systems. These recordings include screen capture, web cam video, keyboard events and more. Recordings are archived indenitely and can be searched and played back, subject to access controls and workow approvals. Benet Session recording is useful both for knowledge sharing and forensic audits.
2011 Hitachi ID Systems, Inc. All rights reserved.
Privileged Access Manager Features at a Glance
FEATURE: Integration with Windows service accounts Description Privileged Access Manager can periodically change the passwords on Windows service accounts. It then noties Windows OS components including SCM, IIS, Scheduler and DCOM of the new password values. Benet This feature eliminates static passwords on Windows services, which often run with signicant privileges.
FEATURE: API to eliminate embedded application passwords Description Privileged Access Manager can frequently scramble and vault the passwords on accounts used by one application to connect to another. Applications can then be modied to call the Privileged Access Manager API to fetch current password values, eliminating passwords stored in scripts and conguration les. Benet Plaintext passwords stored in scripts and conguration les are a major security risk. Eliminating them signicantly improves the security posture of an organization.
FEATURE: Support for laptop passwords Description A laptop service can be deployed to Windows and Linux laptops. This service periodically contacts the central Privileged Access Manager server cluster, requesting a new password for local administrator accounts. Benet This process makes it possible to secure privileged passwords on mobile devices, which would otherwise be unreachable because they are powered down, disconnected from the network, protected by rewalls and assigned different IP addresses.
FEATURE: Identity management features included Description In a typical deployment, user rights to access privileged accounts depend on user membership in AD or LDAP groups. Privileged Access Manager includes workow processes to request such group membership, to apply segregation of duties policies to these groups, to detect unauthorized changes to these groups and to periodically invite group owners to review their membership. Benet Effective group membership management ensures that security policies are based on reliable data. This is especially helpful for organizations that have not deployed effective identity management process to manage ne-grained security entitlements.
2011 Hitachi ID Systems, Inc. All rights reserved.
Privileged Access Manager Features at a Glance
FEATURE: Many included integrations Description Privileged Access Manager includes connectors for over 100 systems and applications, plus exible agents designed to integrate new ones. Benet Including connectors in the base price and providing a rich set of connectors lowers both the initial and ongoing cost of the system.
FEATURE: Multi-master, replicated architecture Description Privileged Access Manager includes a data replication layer and can be deployed to multiple servers, at multiple locations, at no extra cost. Benet Built-in support for high-availability and fault-tolerance make Privileged Access Manager suitable for enterprise deployments.
FEATURE: Multi-lingual user interface Description Privileged Access Manager ships with multiple user interface languages and additional ones can be added easily, both by Hitachi ID Systems and customers. Benet A multi-lingual user interface makes Privileged Access Manager suitable for international organizations.
500, 1401 - 1 Street SE, Calgary AB Canada T2G 2J3 Tel: 1.403.233.0740 Fax: 1.403.233.0725 E-Mail: sales@Hitachi-ID.com
File: /pub/wp/documents/features/hipam/hipam-features-short-5.tex Date: 2011-05-05
www.Hitachi-ID.com
Das könnte Ihnen auch gefallen
- An Executive Guide to Identity Access Management - 2nd EditionVon EverandAn Executive Guide to Identity Access Management - 2nd EditionBewertung: 4 von 5 Sternen4/5 (3)
- Hardening Microsoft Active DirectoryDokument14 SeitenHardening Microsoft Active DirectoryMarquete NavarroNoch keine Bewertungen
- Best Practices For Securing Active DirectoryDokument123 SeitenBest Practices For Securing Active DirectoryFede VillanuevaNoch keine Bewertungen
- A Random-Walk-Down-Wall-Street-Malkiel-En-2834 PDFDokument5 SeitenA Random-Walk-Down-Wall-Street-Malkiel-En-2834 PDFTim100% (1)
- Hitachi ID Privileged Access Manager: Randomize and Control Disclosure of Privileged PasswordsDokument14 SeitenHitachi ID Privileged Access Manager: Randomize and Control Disclosure of Privileged PasswordsHitachiID100% (2)
- Privileged Identity Management Best Practices PDFDokument6 SeitenPrivileged Identity Management Best Practices PDFPrasad KshirsagarNoch keine Bewertungen
- WS-011 Windows Server 2019 AdministrationDokument54 SeitenWS-011 Windows Server 2019 AdministrationANoch keine Bewertungen
- Hitachi ID Password ManagerDokument27 SeitenHitachi ID Password ManagerHitachiIDNoch keine Bewertungen
- WS-011 Windows Server 2019 AdministrationDokument68 SeitenWS-011 Windows Server 2019 AdministrationAlbert Jeremy100% (1)
- Q1) What Are The Primary Functions of Cyberark?Dokument8 SeitenQ1) What Are The Primary Functions of Cyberark?santoshs2002848Noch keine Bewertungen
- Cyber Ark Questions and AnswersDokument93 SeitenCyber Ark Questions and AnswersYayathi AmpoluNoch keine Bewertungen
- WS-011 Windows Server 2019/2022 AdministrationDokument50 SeitenWS-011 Windows Server 2019/2022 AdministrationSyed Amir Iqbal100% (1)
- CyberArk Security Fundamentals For Privileged Account SecurityDokument6 SeitenCyberArk Security Fundamentals For Privileged Account SecurityLeandro LomibaoNoch keine Bewertungen
- Ignition 21 CFR Part 11 Compliance - Panacea TechnologiesDokument7 SeitenIgnition 21 CFR Part 11 Compliance - Panacea TechnologiesglmazNoch keine Bewertungen
- Privileged Access Manager Faq GenericDokument8 SeitenPrivileged Access Manager Faq GenericHitachiIDNoch keine Bewertungen
- AZURE AZ 500 STUDY GUIDE-1: Microsoft Certified Associate Azure Security Engineer: Exam-AZ 500Von EverandAZURE AZ 500 STUDY GUIDE-1: Microsoft Certified Associate Azure Security Engineer: Exam-AZ 500Noch keine Bewertungen
- Hitachi Id Privileged Access ManagerDokument2 SeitenHitachi Id Privileged Access ManagerHitachiIDNoch keine Bewertungen
- Developing An IAM Business CaseDokument9 SeitenDeveloping An IAM Business CaseHitachiIDNoch keine Bewertungen
- Hiim FeaturesDokument3 SeitenHiim FeaturesHitachiIDNoch keine Bewertungen
- Privileged Access Workstation: Credential Hygiene and PAWDokument2 SeitenPrivileged Access Workstation: Credential Hygiene and PAWYohanna MonsalvezNoch keine Bewertungen
- Integrating Mtech Idm Suite With MiisDokument13 SeitenIntegrating Mtech Idm Suite With MiisHitachiIDNoch keine Bewertungen
- How Do You Understand The Segregation of Duties?Dokument3 SeitenHow Do You Understand The Segregation of Duties?Michal MachowskiNoch keine Bewertungen
- 10) Lecture10Dokument8 Seiten10) Lecture10byurabekova05Noch keine Bewertungen
- Defender Datasheet 69032Dokument2 SeitenDefender Datasheet 69032Santhanamariyan TNoch keine Bewertungen
- Password Manager Faq Network ArchitectsDokument9 SeitenPassword Manager Faq Network ArchitectsHitachiIDNoch keine Bewertungen
- PIM Brochure Low ResDokument4 SeitenPIM Brochure Low Resn_neethu11Noch keine Bewertungen
- Symantec Privileged Access Management: Product BriefDokument3 SeitenSymantec Privileged Access Management: Product BriefKo Ko AungNoch keine Bewertungen
- Monitor Employee Activity with Ekran SystemDokument148 SeitenMonitor Employee Activity with Ekran SystemSainiRahulNoch keine Bewertungen
- Password Manager: Detailed Presentation.Dokument27 SeitenPassword Manager: Detailed Presentation.HitachiIDNoch keine Bewertungen
- Cisco Identity Services Engine 1333230959Dokument5 SeitenCisco Identity Services Engine 1333230959Vanessa Arias IzaNoch keine Bewertungen
- Password Manager Pro - Security SpecificationsDokument15 SeitenPassword Manager Pro - Security Specificationsunicycle1234Noch keine Bewertungen
- AAA Administration for Clouds Unit 4Dokument35 SeitenAAA Administration for Clouds Unit 4sambangialekhya846Noch keine Bewertungen
- Chapter 16 IT Controls Part II Security and AccessDokument41 SeitenChapter 16 IT Controls Part II Security and AccessGazelem Zeryne AgootNoch keine Bewertungen
- Unit 4Dokument45 SeitenUnit 4AasmiNoch keine Bewertungen
- Implementing SSO with Shared CredentialsDokument8 SeitenImplementing SSO with Shared CredentialsPrasad KshirsagarNoch keine Bewertungen
- AssignmentDokument22 SeitenAssignmentHaris ChaudhryNoch keine Bewertungen
- Hitachi Id Group ManagerDokument2 SeitenHitachi Id Group ManagerHitachiIDNoch keine Bewertungen
- CSCF_Password PolicyDokument4 SeitenCSCF_Password Policyge.alehegnNoch keine Bewertungen
- T S C S: 1.1 OverviewDokument56 SeitenT S C S: 1.1 OverviewSamdani TajNoch keine Bewertungen
- Hotel Management SystemDokument3 SeitenHotel Management SystemSubash_SaradhaNoch keine Bewertungen
- IBM Privileged Identity ManagerDokument6 SeitenIBM Privileged Identity ManagerMuhittin KetelogluNoch keine Bewertungen
- Priority_FDA_CFR_11_Compliance (1)Dokument7 SeitenPriority_FDA_CFR_11_Compliance (1)allforspamandspamforall1Noch keine Bewertungen
- Cyber Security That’s Good for Your People and Your BusinessDokument2 SeitenCyber Security That’s Good for Your People and Your BusinessSyed MoizNoch keine Bewertungen
- 5 Operational RequirementsDokument2 Seiten5 Operational RequirementsHakimuddin AttarwalaNoch keine Bewertungen
- Microsafe HP Networking Jf388a Imc User Access Management Module With 200-User 2024Dokument4 SeitenMicrosafe HP Networking Jf388a Imc User Access Management Module With 200-User 2024rsrosabrNoch keine Bewertungen
- Project SynopsisDokument4 SeitenProject Synopsisramandubey69Noch keine Bewertungen
- Enhanced Security Admin Environment Solution Datasheet (En)Dokument2 SeitenEnhanced Security Admin Environment Solution Datasheet (En)Mohammed MojoNoch keine Bewertungen
- PwC Due Diligence Portal SoftwareDokument4 SeitenPwC Due Diligence Portal SoftwarerakehjNoch keine Bewertungen
- Privileged Access Management: SecurityDokument13 SeitenPrivileged Access Management: SecurityMohamedNoch keine Bewertungen
- Toaz - Info Stock Management System PRDokument20 SeitenToaz - Info Stock Management System PRVattikuti SathwikNoch keine Bewertungen
- Windows ServicesDokument38 SeitenWindows ServicesAnimeshNandyNoch keine Bewertungen
- Client Management Suite 7 1 DatasheetDokument6 SeitenClient Management Suite 7 1 DatasheetShahid Wahab NawabNoch keine Bewertungen
- PAM DocumentationDokument8 SeitenPAM DocumentationsidNoch keine Bewertungen
- 2012-3 WP SecurIT TrustBuilder Two-Factor Authentication IBM ISAM - 1Dokument6 Seiten2012-3 WP SecurIT TrustBuilder Two-Factor Authentication IBM ISAM - 1aliNoch keine Bewertungen
- Hitachi ID Access CertifierDokument7 SeitenHitachi ID Access CertifierHitachiIDNoch keine Bewertungen
- Deep Identity Solution Overview - CC 14apr2016Dokument66 SeitenDeep Identity Solution Overview - CC 14apr2016Christer CruzNoch keine Bewertungen
- SCCMDokument3 SeitenSCCManujsharmaitproNoch keine Bewertungen
- Centrify DirectAudit Datasheet PDFDokument2 SeitenCentrify DirectAudit Datasheet PDFLucasFerreiraNoch keine Bewertungen
- The IT Director's Guide To Passwords and Cyber EssentialsDokument21 SeitenThe IT Director's Guide To Passwords and Cyber EssentialsAlejandro AlmaguerNoch keine Bewertungen
- Cisco Identity Services EngineDokument8 SeitenCisco Identity Services EngineZakarieya AbdurahmanNoch keine Bewertungen
- IBM SAM For Enterprise SSO DataSheetDokument8 SeitenIBM SAM For Enterprise SSO DataSheetbakh777196Noch keine Bewertungen
- Black Orange Dark Simple Digital Financial Technology (Fintech) Technology PresentationDokument6 SeitenBlack Orange Dark Simple Digital Financial Technology (Fintech) Technology PresentationRohit SinghNoch keine Bewertungen
- Hitachi ID Password ManagerDokument5 SeitenHitachi ID Password ManagerHitachiIDNoch keine Bewertungen
- Identity and Access Lifecycle AutomationDokument14 SeitenIdentity and Access Lifecycle AutomationHitachiIDNoch keine Bewertungen
- Hitachi ID Password ManagerDokument17 SeitenHitachi ID Password ManagerHitachiIDNoch keine Bewertungen
- Hitachi ID Identity and Access Management SuiteDokument10 SeitenHitachi ID Identity and Access Management SuiteHitachiIDNoch keine Bewertungen
- Hitachi ID Group ManagerDokument2 SeitenHitachi ID Group ManagerHitachiIDNoch keine Bewertungen
- An Overview of Business Drivers and Technology SolutionsDokument6 SeitenAn Overview of Business Drivers and Technology SolutionsHitachiIDNoch keine Bewertungen
- Maximizing User Adoption With Hitachi ID Password ManagerDokument8 SeitenMaximizing User Adoption With Hitachi ID Password ManagerHitachiIDNoch keine Bewertungen
- Authentication ManagementDokument6 SeitenAuthentication ManagementHitachiIDNoch keine Bewertungen
- Hitachi ID Identity ManagerDokument17 SeitenHitachi ID Identity ManagerHitachiIDNoch keine Bewertungen
- Hitachi ID Access CertifierDokument2 SeitenHitachi ID Access CertifierHitachiIDNoch keine Bewertungen
- Building An Identity Management Business CaseDokument11 SeitenBuilding An Identity Management Business CaseHitachiIDNoch keine Bewertungen
- Hitachi ID Access CertifierDokument7 SeitenHitachi ID Access CertifierHitachiIDNoch keine Bewertungen
- Hitachi ID Group ManagerDokument7 SeitenHitachi ID Group ManagerHitachiIDNoch keine Bewertungen
- Hitachi ID Identity ManagerDokument4 SeitenHitachi ID Identity ManagerHitachiIDNoch keine Bewertungen
- Hitachi ID Identity ManagerDokument20 SeitenHitachi ID Identity ManagerHitachiIDNoch keine Bewertungen
- Securing Embedded PasswordsDokument7 SeitenSecuring Embedded PasswordsHitachiIDNoch keine Bewertungen
- Hitachi ID Identity and Access Management SuiteDokument16 SeitenHitachi ID Identity and Access Management SuiteHitachiIDNoch keine Bewertungen
- Hitachi ID Privileged Access Manager BrochureDokument2 SeitenHitachi ID Privileged Access Manager BrochureHitachiIDNoch keine Bewertungen
- 2015 Privileged Access Management StudyDokument26 Seiten2015 Privileged Access Management StudyHitachiIDNoch keine Bewertungen
- Privileged Access ManagementDokument3 SeitenPrivileged Access ManagementHitachiIDNoch keine Bewertungen
- Privileged Access ManagementDokument15 SeitenPrivileged Access ManagementHitachiIDNoch keine Bewertungen
- Hitachi ID Access CertifierDokument7 SeitenHitachi ID Access CertifierHitachiIDNoch keine Bewertungen
- Hitachi ID Identity Manager BrochureDokument2 SeitenHitachi ID Identity Manager BrochureHitachiIDNoch keine Bewertungen
- Hitachi ID Management Suite BrochureDokument2 SeitenHitachi ID Management Suite BrochureHitachiIDNoch keine Bewertungen
- Hitachi ID Password Manager BrochureDokument2 SeitenHitachi ID Password Manager BrochureHitachiIDNoch keine Bewertungen
- Hitachi ID Identity Express™ - Corporate Edition BrochureDokument2 SeitenHitachi ID Identity Express™ - Corporate Edition BrochureHitachiIDNoch keine Bewertungen
- Simplifying Lotus Notes Id and Password ManagementDokument2 SeitenSimplifying Lotus Notes Id and Password ManagementHitachiIDNoch keine Bewertungen
- NCR Corporation - Identity and Access Management - A Case StudyDokument2 SeitenNCR Corporation - Identity and Access Management - A Case StudyHitachiIDNoch keine Bewertungen
- GLB - Gramm-Leach-Bliley ActDokument2 SeitenGLB - Gramm-Leach-Bliley ActHitachiIDNoch keine Bewertungen
- Condicional Perfecto Continuo interrogativo guíaDokument2 SeitenCondicional Perfecto Continuo interrogativo guíaMaxi RamirezNoch keine Bewertungen
- Sahar NSC FixDokument45 SeitenSahar NSC FixSahar AndhikaNoch keine Bewertungen
- PCC ConfigDokument345 SeitenPCC ConfigVamsi SuriNoch keine Bewertungen
- Entrepreneurship - Quarter 2 - Week 1-3 - 4 M's of Production and - Business ModelDokument6 SeitenEntrepreneurship - Quarter 2 - Week 1-3 - 4 M's of Production and - Business ModelJude Del RosarioNoch keine Bewertungen
- Portfolio HistoryDokument8 SeitenPortfolio Historyshubham singhNoch keine Bewertungen
- HiaceDokument1 SeiteHiaceburjmalabarautoNoch keine Bewertungen
- Sarina Dimaggio Teaching Resume 5Dokument1 SeiteSarina Dimaggio Teaching Resume 5api-660205517Noch keine Bewertungen
- Mobile Services Tax Invoice for Dr Reddys LaboratoriesDokument3 SeitenMobile Services Tax Invoice for Dr Reddys LaboratoriesK Sree RamNoch keine Bewertungen
- Bakhtar University: Graduate School of Business AdministrationDokument3 SeitenBakhtar University: Graduate School of Business AdministrationIhsanulhaqnooriNoch keine Bewertungen
- Module 1 in Contemporary Arts First MonthDokument12 SeitenModule 1 in Contemporary Arts First MonthMiles Bugtong CagalpinNoch keine Bewertungen
- Analysis of Cocoyam Utilisation by Rural Households in Owerri West Local Government Area of Imo StateDokument11 SeitenAnalysis of Cocoyam Utilisation by Rural Households in Owerri West Local Government Area of Imo StatePORI ENTERPRISESNoch keine Bewertungen
- Land Securities Group (A)Dokument13 SeitenLand Securities Group (A)Piyush SamalNoch keine Bewertungen
- Terrestrial EcosystemDokument13 SeitenTerrestrial Ecosystemailene burceNoch keine Bewertungen
- Lantern October 2012Dokument36 SeitenLantern October 2012Jovel JosephNoch keine Bewertungen
- PERDEV - Lesson 3 ReadingsDokument6 SeitenPERDEV - Lesson 3 ReadingsSofiaNoch keine Bewertungen
- Court of Appeals: DecisionDokument11 SeitenCourt of Appeals: DecisionBrian del MundoNoch keine Bewertungen
- OutliningDokument17 SeitenOutliningJohn Mark TabbadNoch keine Bewertungen
- The Apostolic Church, Ghana English Assembly - Koforidua District Topic: Equipping The Saints For The MinistryDokument2 SeitenThe Apostolic Church, Ghana English Assembly - Koforidua District Topic: Equipping The Saints For The MinistryOfosu AnimNoch keine Bewertungen
- Salzer Panel Accessories Price List - 01st January 2019Dokument40 SeitenSalzer Panel Accessories Price List - 01st January 2019Chandra SekaranNoch keine Bewertungen
- Traditional Knowledge - The Changing Scenario in India PDFDokument9 SeitenTraditional Knowledge - The Changing Scenario in India PDFashutosh srivastavaNoch keine Bewertungen
- Basic Unix Commands: Cat - List A FileDokument3 SeitenBasic Unix Commands: Cat - List A Filekathir_tkNoch keine Bewertungen
- Final Project On Employee EngagementDokument48 SeitenFinal Project On Employee Engagementanuja_solanki8903100% (1)
- EDUC 5240 - Creating Positive Classroom EnvironmentsDokument5 SeitenEDUC 5240 - Creating Positive Classroom EnvironmentsMay Phyo ThuNoch keine Bewertungen
- Work, Energy and Power: Checkpoint 1 (p.194)Dokument12 SeitenWork, Energy and Power: Checkpoint 1 (p.194)U KILLED MY DOGNoch keine Bewertungen
- AGIL KENYA For Web - tcm141-76354Dokument4 SeitenAGIL KENYA For Web - tcm141-76354Leah KimuhuNoch keine Bewertungen
- 6-Modul - PTI412 - IoT-1-2020Dokument17 Seiten6-Modul - PTI412 - IoT-1-202020200801015 Joko SulistyoNoch keine Bewertungen
- Explore the rules and history of American football and basketballDokument2 SeitenExplore the rules and history of American football and basketballAndrei IoneanuNoch keine Bewertungen
- Ferret Fiasco: Archie Carr IIIDokument8 SeitenFerret Fiasco: Archie Carr IIIArchie Carr III100% (1)
- The Man of Sorrows Wednesday of Holy Week Divine IntimacyDokument5 SeitenThe Man of Sorrows Wednesday of Holy Week Divine IntimacyTerri ThomasNoch keine Bewertungen