Beruflich Dokumente
Kultur Dokumente
Openssh RDP VNC
Hochgeladen von
dennisbgOriginalbeschreibung:
Originaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Openssh RDP VNC
Hochgeladen von
dennisbgCopyright:
Verfügbare Formate
Connecting to Windows Machines via OpenSSH / Cygwin
Simon Baker UCL Computer Security Team 11/28/06
Introduction Recently, several problems have come to light with remote access solutions. Two of the most popular solutions are VNC and Microsoft Remote Desktop Protocol, known as RDP or rdesktop, and these have both had quite serious flaws, which could lead to a system compromise. However, by contrast, the OpenSSH software implementation has been reviewed by multiple competent people, and had very few vulnerabilities recently. In this paper, we will look at how to install OpenSSH onto a windows system, and effectively `wrap' access to RDP or VNC servers via a much more secure protocol.
Installing OpenSSH (Server) First, install Cygwin from http://www.cygwin.com/ The installation instructions for this task are available at http://www.cygwin.com/cygwin-ug-net/setup-net.html Ensure that you install the OpenSSH package, which appears under the Net category, or select the Full view mode.
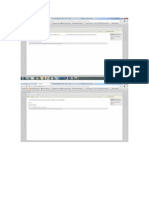
Once the installation is complete, we need to edit and add some environment variables. Open control panel, select System. Once this has loaded, select the Advanced tab, as shown below, and further select Environment Variables :
Under the System Variables section, click New - a New System Variable window should load. Enter the information as shown below:
Then click OK. ntsec is an environment variable to instruct cygwin to use Windows' security rules for controlling users' access to files and other operating system facilities. For more information on this setting, please see http://cygwin.com/cygwin-ug-net/ntsec.html Next, select the Path variable and click Edit. Append ;c:/cygwin/bin to this variable as shown below:
Then close all the open windows. The variables should be set correctly.
We can now start Cygwin - Start it via Start->Programs->Cygwin->Cygwin Bash Shell. You should then be presented with a console box. Run the ssh-host-config script, as shown in the screen shot below. Use the same answers as shown:
Once this has completed, you can start the actual SSH daemon. This can be achieved by one of three ways. Firstly, you can run net start sshd within the Cygwin prompt, or you can run cygrunsrv.exe -S sshd. The third way is to simply reboot. You may however see the following error message if you are using certain security templates: simonb@fricked ~ $ net start sshd The CYGWIN sshd service is starting. The CYGWIN sshd service could not be started. The service did not report an error. More help is available by typing NET HELPMSG 3534. simonb@fricked ~ $ cygrunsrv.exe -S sshd cygrunsrv: Error starting a service: QueryServiceStatus: Win32 error 1062: The service has not been started. This is due to permission setting problems with the Cygwin directory. This thread has some helpful advice: http://erdelynet.com/archive/ssh-l/2001-09/0068.html You can check to see if SSH is running, by running netstat -a in a cmd.exe or from a Cygwin shell, or use TCPView from http://sysinternals.com
Installation of TightVNC The TightVNC projects homepage is available at http://www.tightvnc.com/ At time of writing, the current installer is available from: http://heanet.dl.sourceforge.net/sourceforge/vnc-tight/tightvnc-1.3.8-setup.exe Download and run the installer, and under Additional Tasks ensure you enable the following options:
You will then be presented with the actual Setup screen. Firstly, enter two distinctly different passwords in the Primary and View-Only screen, as shown below:
If you want to install TightVNC on a number of computers, and do not want to repeatedly enter the same password on each machine, install TightVNC once and set the password, then copy the registry settings under HKEY_CURRENT_USER\Software\ORL\WinVNC3 to other machines. The next step is to enable connections via SSH only. Click the Administration tab, and enable the Allow loopback connections and Allow only loopback connections. Note that under Windows XP connections will already be firewalled by the inbuilt XP firewall (or whatever other solution you are using, e.g. F-Secure firewall). We will discuss enabling access to ssh later via the firewall.
Once this has been completed, click Apply then OK. The service should be configured and running.
Enabling SSH access via XP Firewall Open control panel, then select Windows Firewall. Once this has loaded, click the Exceptions tab, and then click New. Enter the appropriate information for the exception, in our case port 22.
While you are editing the firewall rules, you may as well disable the Remote Desktop checkbox, if enabled, as you can now SSH portforward the protocol over SSH. RDP uses port 3389 by default.
SSH'ing in from a UNIX Client One of the benefits of VNC is that the software will also run on a UNIX system, which means you can actually control and administer Windows machines from a UNIX client. If you are using the command line SSH, the following shows an example of how to connect:
From there, you simply load up a VNC client on your machine, and tell it to connect to localhost or 127.0.0.1. The connection will automatically be routed down the SSH tunnel to the remote server. For example, from another Terminal you could run vncviewer: simonb@tuxed ~ $ vncviewer --help TightVNC viewer version 1.2.9 Usage: vncviewer [<OPTIONS>] [<HOST>][:<DISPLAY#>] vncviewer [<OPTIONS>] [<HOST>][::<PORT#>] vncviewer [<OPTIONS>] -listen [<DISPLAY#>] vncviewer -help Again, simply use localhost as the HOST setting, e.g. vncviewer localhost will connect you to the remote host via the SSH tunnel. However, please bear in mind you can only connect to one host at a time, unless you increment the ssh command line, e.g.: use -L5901:localhost:5900 for example, and then connect your local client to that port.
SSH'ing in from a Windows Client You can use the UNIX method described above from a windows host, assuming it has cygwin installed on it, or there are several other SSH clients available, both commercial and freeware. One of the most popular is called PuTTY, and available from http://www.chiark.greenend.org.uk/%7esgtatham/putty/ It is quite easy to configure. On the client machine, download and install PuTTY (you can use either putty.exe, or the actual installer), and run putty. You will then see a configuration screen ; enter the hostname, and optionally the data fields shown in [1] and [2], and click Save :
Then, click Tunnels in the left pane, and enter the appropriate information. In the example below, we are forwarding VNC traffic (Port 5900), though this can be anything you like (for example, rdesktop is 3389)
Once you have configured PuTTY, you can then connect to the host in question. Then, you can simply use the VNC client or Rdesktop client installed locally to connect to localhost / 127.0.0.1 .
Problem Solving If you get User already logged on error messages, you need to read: http://support.microsoft.com/default.aspx?scid=kb;%5BLN%5D;884020
References http://www.microsoft.com/technet/prodtechnol/winxppro/reskit/c08621675.mspx
Das könnte Ihnen auch gefallen
- Hiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessVon EverandHiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessNoch keine Bewertungen
- VncserverDokument39 SeitenVncserverpensamemuchoNoch keine Bewertungen
- How To Set Up EASY NLC VNCDokument3 SeitenHow To Set Up EASY NLC VNCBlue ScreenNoch keine Bewertungen
- CSEC630 Lab2 - IDS Revised 20110614Dokument18 SeitenCSEC630 Lab2 - IDS Revised 20110614acg49100% (1)
- Setup of a Graphical User Interface Desktop for Linux Virtual Machine on Cloud PlatformsVon EverandSetup of a Graphical User Interface Desktop for Linux Virtual Machine on Cloud PlatformsNoch keine Bewertungen
- VNCDokument10 SeitenVNCatif_khanNoch keine Bewertungen
- A Short Walk-Through of Mininet and POX: Part 1: The Mininet Network Emulation EnvironmentDokument12 SeitenA Short Walk-Through of Mininet and POX: Part 1: The Mininet Network Emulation Environmentanilth12Noch keine Bewertungen
- How To Install and Configure VNC Remote Access For The GNOME Desktop On CentOS 7Dokument28 SeitenHow To Install and Configure VNC Remote Access For The GNOME Desktop On CentOS 7usama1571Noch keine Bewertungen
- Seismic Unix Installation Under CygwinDokument8 SeitenSeismic Unix Installation Under CygwinamrymokoNoch keine Bewertungen
- OpenVPN Easy and Secure Setup GuideDokument10 SeitenOpenVPN Easy and Secure Setup GuideYoussef AddiNoch keine Bewertungen
- X11 Forwarding Using SSHDokument11 SeitenX11 Forwarding Using SSHipgengNoch keine Bewertungen
- Final Project 5Dokument49 SeitenFinal Project 5Atika C'hNoch keine Bewertungen
- How To Set Up A Matlab Connection Via The Internet On Your Own ComputerDokument2 SeitenHow To Set Up A Matlab Connection Via The Internet On Your Own ComputerAmita Rathee DahiyaNoch keine Bewertungen
- Nodehowto 1Dokument4 SeitenNodehowto 1rachid moslehNoch keine Bewertungen
- Build SoftEther VPN For UNIXDokument3 SeitenBuild SoftEther VPN For UNIXMFM AhmedNoch keine Bewertungen
- Install and Configure a Remote Desktop on Ubuntu with xRDP and XFCEDokument13 SeitenInstall and Configure a Remote Desktop on Ubuntu with xRDP and XFCEbharath_mv7-1Noch keine Bewertungen
- How To Tunnel Remote Desktop Using SSH (Cygwin) For Windows XP (SP2)Dokument10 SeitenHow To Tunnel Remote Desktop Using SSH (Cygwin) For Windows XP (SP2)dheerajpantNoch keine Bewertungen
- 08 Basic AddrDokument6 Seiten08 Basic Addrmmihir82Noch keine Bewertungen
- Set Up VNC on RHEL 4Dokument10 SeitenSet Up VNC on RHEL 4Azwar Arsyad S SiNoch keine Bewertungen
- VMKnoppix x86 20080213eDokument6 SeitenVMKnoppix x86 20080213eswellowlNoch keine Bewertungen
- Windows 7 TU Delft VPN Connection GuideDokument3 SeitenWindows 7 TU Delft VPN Connection GuideDevristoNoch keine Bewertungen
- GNS3 On CentOS 7.X in The CloudDokument15 SeitenGNS3 On CentOS 7.X in The CloudJesus Rodriguez ArguelleNoch keine Bewertungen
- VNCK - 4.7.4.0 - Installation - Instructions - EngDokument6 SeitenVNCK - 4.7.4.0 - Installation - Instructions - EngNhatQuangNguyenNoch keine Bewertungen
- Mininet VM: Kernel, Switch and Application Code, On A Single Machine (VM, Cloud or Native), in SecondsDokument5 SeitenMininet VM: Kernel, Switch and Application Code, On A Single Machine (VM, Cloud or Native), in SecondsAlbergica AldoNoch keine Bewertungen
- Setup Mininet Virtual Network EnvironmentDokument8 SeitenSetup Mininet Virtual Network EnvironmentVivek0% (1)
- Cygwin X FaqDokument37 SeitenCygwin X FaqSáng tạo mỗi ngàyNoch keine Bewertungen
- ITEC 625 9042 Computer Systems ArchitectureDokument11 SeitenITEC 625 9042 Computer Systems ArchitectureAnas ToufeeqNoch keine Bewertungen
- Cygwin Install XampleDokument14 SeitenCygwin Install XampleDiini RätsepsoNoch keine Bewertungen
- Cloud Computing LABDokument73 SeitenCloud Computing LABDr ASKNoch keine Bewertungen
- Openvpn HowtoDokument24 SeitenOpenvpn HowtoMark ReevesNoch keine Bewertungen
- Step One:: Autoconf Automake Binutils Bison Flex GCC Gcc-CoreDokument3 SeitenStep One:: Autoconf Automake Binutils Bison Flex GCC Gcc-CoreMohammad Noor AlamNoch keine Bewertungen
- Moshell InstallationDokument15 SeitenMoshell InstallationSilviu DiaconuNoch keine Bewertungen
- BLCN532 Lab 1 Set Up Your Development EnvironmentDokument9 SeitenBLCN532 Lab 1 Set Up Your Development EnvironmentAVINNNNASHNoch keine Bewertungen
- Instructions On How To Use The Virtual Machine Files PDFDokument8 SeitenInstructions On How To Use The Virtual Machine Files PDFhoadiNoch keine Bewertungen
- NetSentinel Security ServerDokument9 SeitenNetSentinel Security ServerKiran DasNoch keine Bewertungen
- 02 Create Install LAMP On Virtual Machine UbunDokument20 Seiten02 Create Install LAMP On Virtual Machine UbunscribdNoch keine Bewertungen
- UltraVNC GuideDokument28 SeitenUltraVNC GuideDiego OrtelladoNoch keine Bewertungen
- Touchwin SCADA ManualDokument28 SeitenTouchwin SCADA ManualMarko AntonioNoch keine Bewertungen
- Configuring A VNC Server in Linux BobpeersDokument5 SeitenConfiguring A VNC Server in Linux BobpeersGavinda LakmalNoch keine Bewertungen
- Professional Node.js: Building Javascript Based Scalable SoftwareVon EverandProfessional Node.js: Building Javascript Based Scalable SoftwareNoch keine Bewertungen
- Green Networks: Introduction To MininetDokument6 SeitenGreen Networks: Introduction To MininetnshivegowdaNoch keine Bewertungen
- Deephi DNNDK Tutorial For Ultra96 - LogicTronix - June - 2019Dokument13 SeitenDeephi DNNDK Tutorial For Ultra96 - LogicTronix - June - 2019Kiên Lê HữuNoch keine Bewertungen
- Centos 6 Easy OpenVPN 1.2 Install GuideDokument11 SeitenCentos 6 Easy OpenVPN 1.2 Install Guideworld1capitalNoch keine Bewertungen
- DockerSetup Win10Dokument11 SeitenDockerSetup Win10Göktuğ BağcıNoch keine Bewertungen
- Installation of The Digitalsystemsvm Virtual MachineDokument16 SeitenInstallation of The Digitalsystemsvm Virtual Machinerenzo m cuevaNoch keine Bewertungen
- WinProxy Quick Start GuideDokument16 SeitenWinProxy Quick Start GuideRichard BarjaNoch keine Bewertungen
- Openvpn Client Server With ShorewallDokument5 SeitenOpenvpn Client Server With ShorewallansaarNoch keine Bewertungen
- Open VSwitch Getting StartedDokument6 SeitenOpen VSwitch Getting StartedYogesh PalkarNoch keine Bewertungen
- Evaluation of Some Intrusion Detection and Vulnerability Assessment ToolsVon EverandEvaluation of Some Intrusion Detection and Vulnerability Assessment ToolsNoch keine Bewertungen
- VNC Failed To Connect To ServerDokument3 SeitenVNC Failed To Connect To ServerMarcos Avelino VasconcelosNoch keine Bewertungen
- Banner GrabDokument2 SeitenBanner Grabnandanmg7_382713560Noch keine Bewertungen
- Vcloud Director Installation Part 1 - Database: This Is Part 1 of The VCD 9.0 Installation GuideDokument15 SeitenVcloud Director Installation Part 1 - Database: This Is Part 1 of The VCD 9.0 Installation GuideprakashNoch keine Bewertungen
- VPN Uni - Lu v1 2Dokument23 SeitenVPN Uni - Lu v1 2Katherine Hernandez0% (1)
- Configure A Squid Proxy Server Through WebminDokument20 SeitenConfigure A Squid Proxy Server Through WebminceeropyNoch keine Bewertungen
- Install and Configure SUSE Linux and SAP NetWeaverDokument49 SeitenInstall and Configure SUSE Linux and SAP NetWeaverrajesh98765Noch keine Bewertungen
- DDWRT OpenVPN Server Setup Guide v2.01Dokument35 SeitenDDWRT OpenVPN Server Setup Guide v2.01kickflip900Noch keine Bewertungen
- Tutorial Mininet POXDokument8 SeitenTutorial Mininet POXPaolo FrankoneriNoch keine Bewertungen
- Continuous Integration (CI) :: Classic Diagram Is Available To Explain These Terms in Below AWS WebsiteDokument9 SeitenContinuous Integration (CI) :: Classic Diagram Is Available To Explain These Terms in Below AWS WebsiteBala SubramanyamNoch keine Bewertungen
- Kako Instalirati Omni OS Na VMWARE ESXIDokument14 SeitenKako Instalirati Omni OS Na VMWARE ESXIZeljko PekicNoch keine Bewertungen
- Wi-Fi Extender FAQ v1 1209Dokument7 SeitenWi-Fi Extender FAQ v1 1209dennisbgNoch keine Bewertungen
- t6 Training Guidebook enDokument39 Seitent6 Training Guidebook enMiguel ZuzaNoch keine Bewertungen
- 819 3805 11 PDFDokument12 Seiten819 3805 11 PDFdennisbgNoch keine Bewertungen
- PCTV 400e PCTV Sat Pro Usb PCTV HDTV Sat Pro Usb HardwareDokument13 SeitenPCTV 400e PCTV Sat Pro Usb PCTV HDTV Sat Pro Usb HardwaredennisbgNoch keine Bewertungen
- Manuals from Manualslib.com Search EngineDokument24 SeitenManuals from Manualslib.com Search EnginedennisbgNoch keine Bewertungen
- Ingres 10.2: Security GuideDokument105 SeitenIngres 10.2: Security GuidedennisbgNoch keine Bewertungen
- 1.InputOutput Group 20, IOG 20Dokument204 Seiten1.InputOutput Group 20, IOG 20KStf1Noch keine Bewertungen
- Suunto Training Guidebook EN PDFDokument21 SeitenSuunto Training Guidebook EN PDFdennisbgNoch keine Bewertungen
- Owner'S Manual Mode D'Emploi Manual de InstruccionesDokument64 SeitenOwner'S Manual Mode D'Emploi Manual de InstruccionesdennisbgNoch keine Bewertungen
- d3 Raspored KanalaDokument2 Seitend3 Raspored KanaladennisbgNoch keine Bewertungen
- Gardena: Mastercontrol Solar Art. 1866Dokument22 SeitenGardena: Mastercontrol Solar Art. 1866dennisbgNoch keine Bewertungen
- GUI Method Via Netowork Manager (Ubuntu 14.04, 16.04) : Disconnects-In-11-10Dokument7 SeitenGUI Method Via Netowork Manager (Ubuntu 14.04, 16.04) : Disconnects-In-11-10dennisbgNoch keine Bewertungen
- Change The MTUDokument1 SeiteChange The MTUdennisbgNoch keine Bewertungen
- NetBackup Troubleshoot GuideDokument348 SeitenNetBackup Troubleshoot GuidedennisbgNoch keine Bewertungen
- Suunto Training Guidebook / Guía Entrenamiento Suunto.Dokument21 SeitenSuunto Training Guidebook / Guía Entrenamiento Suunto.Mayayo: Carrerasdemontana.comNoch keine Bewertungen
- Cum Sa Construiesti Un IazDokument0 SeitenCum Sa Construiesti Un IazrecutuNoch keine Bewertungen
- Wi-Fi Extender FAQ v1 1209Dokument7 SeitenWi-Fi Extender FAQ v1 1209dennisbgNoch keine Bewertungen
- ExtremeWareXOSCommandRef11 3Dokument1.712 SeitenExtremeWareXOSCommandRef11 3jarguetaoNoch keine Bewertungen
- Garmin Etrex Vista C Manual enDokument0 SeitenGarmin Etrex Vista C Manual enJohn G.Noch keine Bewertungen
- Cisco One-Year Limited Hardware WarrantyDokument33 SeitenCisco One-Year Limited Hardware WarrantydennisbgNoch keine Bewertungen
- Office Email IphoneDokument8 SeitenOffice Email IphonedennisbgNoch keine Bewertungen
- ATN 910&910I&910B&950B V200R003C10 Configuration Guide 01 (CLI) PDFDokument4.653 SeitenATN 910&910I&910B&950B V200R003C10 Configuration Guide 01 (CLI) PDFgooblin100% (2)
- Sample Code: DecisionDokument16 SeitenSample Code: Decisionhisuman100Noch keine Bewertungen
- Norma ISO6722 - Cableado en VehiculosDokument13 SeitenNorma ISO6722 - Cableado en VehiculosMaxwell MazariegosNoch keine Bewertungen
- SEP Sizing and Scalability Best Practices - v2.2Dokument25 SeitenSEP Sizing and Scalability Best Practices - v2.2thiagodolabellaNoch keine Bewertungen
- MaxEye DVB Test SolutionDokument25 SeitenMaxEye DVB Test Solutiondan r.Noch keine Bewertungen
- Guide For Interpreting Life Cycle Assessment ResultDokument60 SeitenGuide For Interpreting Life Cycle Assessment ResultSharah Yunihar SaputraNoch keine Bewertungen
- Infra ReportDokument3 SeitenInfra ReportjuniorarkeeNoch keine Bewertungen
- Performance PresentationDokument51 SeitenPerformance PresentationSridhar ChandrashekarNoch keine Bewertungen
- PF0009-SLB-ST-DWG-0001 Rev - CDokument1 SeitePF0009-SLB-ST-DWG-0001 Rev - Cbmanojkumar16Noch keine Bewertungen
- Crompton Greaves Leading Manufacturer of Power EquipmentDokument12 SeitenCrompton Greaves Leading Manufacturer of Power Equipmentcarlos vidal100% (1)
- FOX Running Manual: Legal NoticeDokument14 SeitenFOX Running Manual: Legal NoticeDaniel NavarroNoch keine Bewertungen
- ISO 19100 Geographic Information StandardsDokument12 SeitenISO 19100 Geographic Information StandardsHermenegildo LuisNoch keine Bewertungen
- The Mysterious Outlook Outbox - The Whole StoryDokument19 SeitenThe Mysterious Outlook Outbox - The Whole StoryAlessandro VNoch keine Bewertungen
- Din 17100Dokument7 SeitenDin 17100Marco Antônio Deitos FilhoNoch keine Bewertungen
- Parliamentary Procedure in A MeetingDokument2 SeitenParliamentary Procedure in A MeetingGiordann MadejaNoch keine Bewertungen
- Construction Project ManagementDokument51 SeitenConstruction Project Managementocduran42004100% (5)
- Thrush S2R R-1340 Maintenence ManualDokument227 SeitenThrush S2R R-1340 Maintenence Manualarizonaflyer1_732976100% (1)
- Block Diagram: PowerDokument96 SeitenBlock Diagram: PowerBrennan GriffinNoch keine Bewertungen
- 07 - Vee BoDokument68 Seiten07 - Vee BochinnaNoch keine Bewertungen
- Is 650Dokument11 SeitenIs 650Sougata DasNoch keine Bewertungen
- Boiler Safety and Pressure Vessel HazardsDokument72 SeitenBoiler Safety and Pressure Vessel HazardsKabiNoch keine Bewertungen
- Proces Wp023 en PDokument56 SeitenProces Wp023 en PLessing Cárdenas DíazNoch keine Bewertungen
- DDF KroneDokument31 SeitenDDF KroneyusufNoch keine Bewertungen
- Owner's Manual Manuel D'utilisation BedienungsanleitungDokument35 SeitenOwner's Manual Manuel D'utilisation Bedienungsanleitungcostelo63Noch keine Bewertungen
- CA44 and CA44S Carbon Steel Air and Gas Traps Flanged DN15 To DN25Dokument5 SeitenCA44 and CA44S Carbon Steel Air and Gas Traps Flanged DN15 To DN25nnaemeka omekeNoch keine Bewertungen
- 6.c. ISO-10079-1-2022 - Electrically Powered Suction ApparatusDokument7 Seiten6.c. ISO-10079-1-2022 - Electrically Powered Suction Apparatusqvc.regulatory 2Noch keine Bewertungen
- Examen Dell Networking Series Switches V PDFDokument30 SeitenExamen Dell Networking Series Switches V PDFJulio Cesar Agudelo BenitezNoch keine Bewertungen
- Definitions of Each of The 20 Tools of Process ControlDokument2 SeitenDefinitions of Each of The 20 Tools of Process Control88No1FanNoch keine Bewertungen
- TKM Engineering Project Evaluation RubricDokument6 SeitenTKM Engineering Project Evaluation RubricAbhiram DonNoch keine Bewertungen
- ElectromagneticShakersF3 F4 F5B F10Dokument16 SeitenElectromagneticShakersF3 F4 F5B F10Valentin PredaNoch keine Bewertungen