Beruflich Dokumente
Kultur Dokumente
Firewall Rules
Hochgeladen von
roy_txOriginalbeschreibung:
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Firewall Rules
Hochgeladen von
roy_txCopyright:
Verfügbare Formate
A P P E N D I X
Firewall and NAT Rules
Firewall Rules, page D-1 NAT Rules, page D-3
Firewall Rules
This section describes firewall rules used for the simplest and most typical firewall configuration. Table D-1 presents general firewall rules that comply with the guidelines described in Firewall Configuration Guidelines, page 3-12.
Table D-1 General Firewall Rules Protocol
Action Pass
Source LAN networks
Port Any
Destination DMZ net, outside networks
Port Any
Description Allowing any kind of traffic from the private network to the DMZ or outside networks (for example, the Internet). Blocking any kind of traffic to the protected networks (DMZ and internal network). Blocking any kind of traffic from the DMZ to the private network.
Any
Block Block
Any Any
Outside networks DMZ network
Any Any
LAN networks, Any DMZ network LAN networks Any
Table D-2 describes rules that you must add to enable connectivity between the internal gatekeeper located in the DMZ and the MCU components located on the internal network.
Table D-2 Gatekeeper-to-MCU/EMP Traffic Firewall Rules Protocol
Action Pass
Source Gatekeeper IP address as it appears in the DMZ Gatekeeper IP address as it appears in the DMZ
Port Any
Destination Port MCU IP address 1025 65535
Description TCP High ports from Gatekeeper to MCU on the LAN. Enables H.245 control signaling channels to be opened. H.323 signaling to MCU on the LAN. Enables call setup signaling between the Internal Gatekeeper and the MCUs.
TCP
Pass
TCP
Any
MCU IP address
2720
Design Guide for the Cisco Unified Videoconferencing Solution Using Desktop Component Release 5.5 OL-16113-01
D-1
Appendix D Firewall Rules
Firewall and NAT Rules
Table D-3 describes rules that you must add to enable connectivity between the internal Cisco Unified Videoconferencing Manager located on the DMZ and the Cisco Unified Videoconferencing 3500 Series MCU located on the internal network.
Table D-3 Cisco Unified Videoconferencing Manager-to-MCU Traffic Firewall Rules
Action Protocol Pass TCP
Source
Port
Destination
Port
Description Login (XML) to MCU on the LAN. Enables XML management interface connectivity between the Cisco Unified Videoconferencing Manager and the Cisco Unified Videoconferencing 3500 Series MCU components. SNMP from Cisco Unified Videoconferencing Manager to Cisco Unified Videoconferencing 3500 Series MCU on the LAN. Enables SNMP management interface connectivity between the Cisco Unified Videoconferencing Manager and the Cisco Unified Videoconferencing 3500 Series MCU components.
Any Cisco Unified Videoconferencing Manager IP address as it appears on the DMZ
3336 Cisco Unified Videoconferencing 3500 Series MCU IP address
Pass
UDP
Any Cisco Unified Videoconferencing Manager IP address as it appears on the DMZ
161 Cisco Unified Videoconferencing 3500 Series MCU IP address
Table D-4 describes a rule that you must add to enable connectivity between the internal gatekeeper located on the DMZ and Cisco Unified Videoconferencing 3500 Series Gateway components located on the private network.
Table D-4 Cisco IOS H.323 Gatekeeper-to-gateway Traffic Firewall Rules
Action Protocol Pass TCP
Source Gatekeeper IP address as it appears on the DMZ
Port Any
Destination
Port
Description TCP High ports from Gatekeeper to GW320 on the LAN. Enables H.245 control signaling channels to be opened.
1025 Cisco Unified Videoconferencing 65535 3500 Series Gateway IP address
Table D-5 describes rules that you must add to enable a Desktop Server Client to invite a room system located on the private network.
Table D-5 Gatekeeper-to-endpoint Traffic Firewall Rules
Action Protocol Source Pass TCP
Port
Destination
Port
Description H.323 signaling to a room system on the LAN. Enables call setup signaling between the Internal Gatekeeper and room systems. TCP High ports from Gatekeeper to room system on the LAN. Enables H.245 control signaling channels to be opened.
Gatekeeper IP address Any as it appears on the DMZ Gatekeeper IP address Any as it appears on the DMZ
1720 Room system IP address as it appears on the private network 1025 Room system IP address as it appears 65535 on the private network
Pass
TCP
Design Guide for the Cisco Unified Videoconferencing Solution Using Desktop Component Release 5.5
D-2
OL-16113-01
Appendix D
Firewall and NAT Rules NAT Rules
Table D-6 describes rules that you must add to enable connectivity between the internal Cisco Unified Videoconferencing Manager located on the DMZ and Cisco Unified Videoconferencing 3500 Series Gateway components located on the internal network.
Table D-6 Cisco Unified Videoconferencing Manager-to-gateway Traffic Firewall Rules Protocol
Action Pass
Source
Port
Destination GW IP address
Port 1820
Description H.323 Signaling from Gatekeeper to GW320 on the LAN. Enables call setup signaling between the Internal Gatekeeper and the Cisco Unified Videoconferencing 3500 Series Gateways. SNMP from Cisco Unified Videoconferencing Manager to gateway on the LAN. Enables SNMP management interface connectivity between the Cisco Unified Videoconferencing Manager and the gateway components.
TCP
Any Cisco Unified Videoconferencing Manager IP address as it appears on the DMZ
Pass
UDP
Any Cisco Unified Videoconferencing Manager IP address as it appears on the DMZ
GW IP address
161
NAT Rules
Table D-7 describes static NAT entries in the firewall WAN interface that you must configure to enable connectivity between the Desktop Server Clients located on the external networks and the Desktop Servers located in the DMZ.
Table D-7 NAT Rules defining traffic from Desktop Clients to Web Services External Port Range
Protocol TCP
NAT IP
Internal Port Range
Description For external Desktop Server Client web access. Alternatively you can configure the Desktop Server Clients to connect via TCP port 443. For more information about configuring TCP port 443, see Configuring Desktop Server for HTTPS section on page A-1. Control connection between Desktop Server and Desktop Server Client (mandatory). For external Desktop Server Client web access to a virtual room configuration. Enables Desktop Server Client access to Cisco Unified Videoconferencing Manager virtual room settings.
80 (HTTP)
Desktop Server IP address 80 (HTTP) as it appears on the DMZ
TCP TCP
443 (HTTPS) Desktop Server IP address 443 as is appears on the DMZ (HTTPS) 8080 8080 Cisco Unified Videoconferencing Manager Desktop Server IP address as is appears on the DMZ
Table D-8 on page D-4 describes a static NAT entry in the firewall WAN interface that you must add to enable connectivity between the Desktop Server Web Cast clients located on the external networks and the Cisco Unified Videoconferencing Streaming Server located on the DMZ.
Design Guide for the Cisco Unified Videoconferencing Solution Using Desktop Component Release 5.5 OL-16113-01
D-3
Appendix D NAT Rules
Firewall and NAT Rules
Table D-8
NAT Rules defining traffic from Desktop Webcast Clients to the Cisco Unified Videoconferencing Streaming Server External Port Range
Protocol TCP
NAT IP Cisco Unified Videoconferencing Streaming Server IP as appears on the DMZ
Internal Port Range 7070
Description Streaming tunneling connection enables the Web Cast client to access the streamed conference.
7070
Design Guide for the Cisco Unified Videoconferencing Solution Using Desktop Component Release 5.5
D-4
OL-16113-01
Das könnte Ihnen auch gefallen
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationVon EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNoch keine Bewertungen
- Unified Border Element (CUBE) With Cisco Unified Communications Manager (CUCM) Configuration ExampleDokument12 SeitenUnified Border Element (CUBE) With Cisco Unified Communications Manager (CUCM) Configuration ExampleJuan GarciaNoch keine Bewertungen
- Cisco PIX 515E Firewall Quick Start Guide, Version 6.3Dokument36 SeitenCisco PIX 515E Firewall Quick Start Guide, Version 6.3vmilano1Noch keine Bewertungen
- 1.1.4.6 CiscoDokument11 Seiten1.1.4.6 CiscoZeratul322100% (2)
- 11.2.4.5 Lab - Accessing Network Devices With SSHDokument11 Seiten11.2.4.5 Lab - Accessing Network Devices With SSHDragan Filipovic50% (2)
- SIC Practical5 by STUD - TalksDokument7 SeitenSIC Practical5 by STUD - TalksPradeep PrajapatiNoch keine Bewertungen
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkVon EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNoch keine Bewertungen
- RequirementsDokument15 SeitenRequirementsVinu McNoch keine Bewertungen
- PIX/ASA: Establish and Troubleshoot Connectivity Through The Cisco Security ApplianceDokument7 SeitenPIX/ASA: Establish and Troubleshoot Connectivity Through The Cisco Security AppliancetsibiNoch keine Bewertungen
- Integration Into NetworksDokument3 SeitenIntegration Into NetworksmaikpopescuNoch keine Bewertungen
- EBW100-LAN Deltalogic24 (En)Dokument10 SeitenEBW100-LAN Deltalogic24 (En)Jorge_Andril_5370Noch keine Bewertungen
- CCNASv1 1 Chp08 Lab B RMT Acc VPN Instructor PDFDokument33 SeitenCCNASv1 1 Chp08 Lab B RMT Acc VPN Instructor PDFAhmadHijaziNoch keine Bewertungen
- 11.2.4.6 Lab - Accessing Network Devices With SSHDokument6 Seiten11.2.4.6 Lab - Accessing Network Devices With SSHParthPatel0% (3)
- CCNP Packet Tracer - Configuring A Zone-Based Policy Firewall (ZPF)Dokument4 SeitenCCNP Packet Tracer - Configuring A Zone-Based Policy Firewall (ZPF)lgainz01Noch keine Bewertungen
- CCNA Security PT Practice SBA 1Dokument4 SeitenCCNA Security PT Practice SBA 1Oscar Patricio Morales RuedaNoch keine Bewertungen
- Configuring Frame Relay Cisco RoutersDokument52 SeitenConfiguring Frame Relay Cisco RouterswarrhalkNoch keine Bewertungen
- Integration Into Networks: 4.1 Network ParametersDokument2 SeitenIntegration Into Networks: 4.1 Network ParametersMihai PopescuNoch keine Bewertungen
- Collaboration Meeting Rooms (CMR) Cloud Enterprise Deployment Guide (WBS31)Dokument46 SeitenCollaboration Meeting Rooms (CMR) Cloud Enterprise Deployment Guide (WBS31)Cark86Noch keine Bewertungen
- 6.5.1.2 Lab - Building A Switch and Router NetworkDokument8 Seiten6.5.1.2 Lab - Building A Switch and Router NetworkParthPatel100% (8)
- 4.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIDokument10 Seiten4.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIAhmadHijaziNoch keine Bewertungen
- Integration Into Networks: 4.1 Network ParametersDokument2 SeitenIntegration Into Networks: 4.1 Network ParametersMihai PopescuNoch keine Bewertungen
- NeffDokument16 SeitenNeffAliAbdulKarimNoch keine Bewertungen
- Ccnasv1.1 Chp10 Lab-C Asa-ssl-VPN Instructor 8.25.37 Am 8.25.57 AmDokument50 SeitenCcnasv1.1 Chp10 Lab-C Asa-ssl-VPN Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (3)
- EWR-Modem Deltalogic24 (En)Dokument12 SeitenEWR-Modem Deltalogic24 (En)Jorge_Andril_5370Noch keine Bewertungen
- DES-3500 CLI Manual R4 - UpdateDokument238 SeitenDES-3500 CLI Manual R4 - UpdateeentwineNoch keine Bewertungen
- How To Protect Your MikroTik RouterOSDokument13 SeitenHow To Protect Your MikroTik RouterOSRuben DarioNoch keine Bewertungen
- Ccnasecurity Sba FinalDokument12 SeitenCcnasecurity Sba FinalBilly Zomg100% (2)
- 4.4.1.1 Packet Tracer - Configuring A Zone-Based Policy Firewall (ZPF)Dokument5 Seiten4.4.1.1 Packet Tracer - Configuring A Zone-Based Policy Firewall (ZPF)LizSocaZevallos100% (1)
- 9.4.2.7 Lab - Troubleshooting ACL Configuration and PlacementDokument8 Seiten9.4.2.7 Lab - Troubleshooting ACL Configuration and PlacementEdward Octaviano III0% (5)
- Twido Modbus TCP Ip 1Dokument7 SeitenTwido Modbus TCP Ip 1Ivan Agreda SalvadorNoch keine Bewertungen
- 880 Basic Router ConfigDokument22 Seiten880 Basic Router ConfigHoratiu PetrescuNoch keine Bewertungen
- 2.3.3.5 Lab - Configuring A Switch Management Address NewportDokument4 Seiten2.3.3.5 Lab - Configuring A Switch Management Address Newportgerardo1028Noch keine Bewertungen
- Configuring Mikrotik Router With 3CX: Presented byDokument15 SeitenConfiguring Mikrotik Router With 3CX: Presented bymauricioagoNoch keine Bewertungen
- PppoenatDokument10 SeitenPppoenatbunlimNoch keine Bewertungen
- 6.3.1.1 Lab - Securing Layer 2 SwitchesDokument22 Seiten6.3.1.1 Lab - Securing Layer 2 SwitchesJson CañedaNoch keine Bewertungen
- How To Configure Cisco PIX Firewall Part II: The Simple Network DiagramDokument4 SeitenHow To Configure Cisco PIX Firewall Part II: The Simple Network Diagramabbass512Noch keine Bewertungen
- Weekly ReportDokument3 SeitenWeekly ReportNirav DsouzaNoch keine Bewertungen
- Wireless Router enDokument12 SeitenWireless Router ensupynsNoch keine Bewertungen
- How To Protect Your MikroTik RouterOSDokument16 SeitenHow To Protect Your MikroTik RouterOScozack12Noch keine Bewertungen
- Ports IP OfficeDokument3 SeitenPorts IP OfficeJesús CHuy Jiménez RuizNoch keine Bewertungen
- Cisco Pix 515E Firewall ConfigurationDokument7 SeitenCisco Pix 515E Firewall Configurationmicorina100% (2)
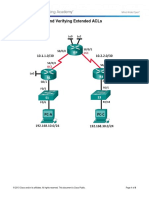
- 9.3.2.13 Lab - Configuring and Verifying Extended ACLsDokument8 Seiten9.3.2.13 Lab - Configuring and Verifying Extended ACLsAnonymous cW6o4f886% (14)
- T BOX ManualDokument26 SeitenT BOX ManualVlady TeoNoch keine Bewertungen
- Gwgk20lg - GK RC ModifiedDokument107 SeitenGwgk20lg - GK RC ModifiedGilles de PaimpolNoch keine Bewertungen
- 6.5.1.1 Lab - Securing Layer 2 SwitchesDokument29 Seiten6.5.1.1 Lab - Securing Layer 2 Switchesxmaryta0% (2)
- 8.7.1.2 Lab - Configuring A Remote Access VPN Server and Client - InstructorDokument37 Seiten8.7.1.2 Lab - Configuring A Remote Access VPN Server and Client - InstructorSalem TrabelsiNoch keine Bewertungen
- Lab - Configuring and Verifying VTY RestrictionsDokument6 SeitenLab - Configuring and Verifying VTY Restrictionsdaniel ramirezNoch keine Bewertungen
- 9.3.2.13 Lab - Configuring and Verifying Extended ACLsDokument8 Seiten9.3.2.13 Lab - Configuring and Verifying Extended ACLsSupinder SekhonNoch keine Bewertungen
- ARP L3-4 ToIP-Aplicacion v1.0 20140703Dokument44 SeitenARP L3-4 ToIP-Aplicacion v1.0 20140703AnghelloReyesZegarraNoch keine Bewertungen
- DVR Network Setting1-TronikaDokument10 SeitenDVR Network Setting1-TronikadanangsalimNoch keine Bewertungen
- Cisco Router Monitoring and Configuration Utilities User ManualDokument6 SeitenCisco Router Monitoring and Configuration Utilities User ManualYogesh KhollamNoch keine Bewertungen
- Pass4test: Certification IT Garanti, The Easy Way!Dokument20 SeitenPass4test: Certification IT Garanti, The Easy Way!Kenza LazrakNoch keine Bewertungen
- SCG 880 SeriesDokument92 SeitenSCG 880 Seriesshamanu8Noch keine Bewertungen
- 2.3.3.4 Lab - Configuring A Switch Management AddressDokument8 Seiten2.3.3.4 Lab - Configuring A Switch Management AddressDaisy Galvan0% (1)
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksVon EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNoch keine Bewertungen
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityVon EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNoch keine Bewertungen
- IP Telephony: Deploying VoIP Protocols and IMS InfrastructureVon EverandIP Telephony: Deploying VoIP Protocols and IMS InfrastructureNoch keine Bewertungen
- Manual Panel SimplexDokument10 SeitenManual Panel Simplexprofesional7002Noch keine Bewertungen
- Visvesvaraya Technological University: Gaayana R (1GA19CS049) Jayanth R G (1GA19CS065)Dokument46 SeitenVisvesvaraya Technological University: Gaayana R (1GA19CS049) Jayanth R G (1GA19CS065)Jeevan ShettyNoch keine Bewertungen
- Sky Network TV LTD V My Box NZ LTD Dist Sheet 25.10.18Dokument70 SeitenSky Network TV LTD V My Box NZ LTD Dist Sheet 25.10.18Stuff NewsroomNoch keine Bewertungen
- Unit 1, Lesson 9 - Lossless CompressionDokument18 SeitenUnit 1, Lesson 9 - Lossless CompressionAalaa MadyNoch keine Bewertungen
- Standards and Guidelines For Electronic Medical Record Systems in KenyaDokument115 SeitenStandards and Guidelines For Electronic Medical Record Systems in KenyaI-TECH KenyaNoch keine Bewertungen
- Aut ProcedureDokument30 SeitenAut ProcedureAnupam Das100% (4)
- BINUS UniversityDokument22 SeitenBINUS Universityjenifir marchNoch keine Bewertungen
- Lec7 - CS787 - Advanced AlgorithmsDokument7 SeitenLec7 - CS787 - Advanced AlgorithmsSérgio Luiz PiresNoch keine Bewertungen
- Auth API DocumentationDokument6 SeitenAuth API DocumentationMarcelo Pereira RodriguesNoch keine Bewertungen
- Blueprint Start PagesDokument13 SeitenBlueprint Start PageskenindiNoch keine Bewertungen
- EEP-Arc Flash Hazard Calculation in 9 Steps Using IEEE 1584-AAADokument6 SeitenEEP-Arc Flash Hazard Calculation in 9 Steps Using IEEE 1584-AAAJOSE LUIS FALCON CHAVEZNoch keine Bewertungen
- Review On Design and Development of Mobile App For FarmersDokument4 SeitenReview On Design and Development of Mobile App For FarmersEditor IJTSRD0% (1)
- Title IdDokument144 SeitenTitle IdCristianOria97Noch keine Bewertungen
- README Withered Arm V 1.33.7Dokument2 SeitenREADME Withered Arm V 1.33.7august1929Noch keine Bewertungen
- IBM Lotus Symphony Developer's GuideDokument150 SeitenIBM Lotus Symphony Developer's GuideRakesh KumarNoch keine Bewertungen
- CPU AffinityDokument4 SeitenCPU Affinityvivek_ibmNoch keine Bewertungen
- SLOOP: A European Project Focused On The Realization of A Shared Repository of Free Learning ObjectsDokument7 SeitenSLOOP: A European Project Focused On The Realization of A Shared Repository of Free Learning ObjectsPierfranco Ravotto100% (1)
- Data StreamsDokument44 SeitenData StreamsSharon LavigneNoch keine Bewertungen
- Deploying PHP App On HerokuDokument23 SeitenDeploying PHP App On HerokuZuhadMahmoodNoch keine Bewertungen
- DBMS 6-11Dokument43 SeitenDBMS 6-11Shubham ThakurNoch keine Bewertungen
- CF Lecture 06-File System and OSDokument43 SeitenCF Lecture 06-File System and OSFaisal ShahzadNoch keine Bewertungen
- As01 Vs As91Dokument6 SeitenAs01 Vs As91Manas Kumar SahooNoch keine Bewertungen
- Main Functions of An Operating System: 2017 Me 302 M. Usama Bin ManzoorDokument4 SeitenMain Functions of An Operating System: 2017 Me 302 M. Usama Bin Manzoorusama manzoorNoch keine Bewertungen
- Glass Panel CalculationsDokument12 SeitenGlass Panel CalculationsAshaNoch keine Bewertungen
- Cisco IOS XR Getting Started Guide For The Cisco CRS RouterDokument220 SeitenCisco IOS XR Getting Started Guide For The Cisco CRS Routerab_laaroussiNoch keine Bewertungen
- Configuration of Gateway and Proxy Devices OI 06 enDokument268 SeitenConfiguration of Gateway and Proxy Devices OI 06 enOSunTzuONoch keine Bewertungen
- UI Design Report ExampleDokument3 SeitenUI Design Report ExampleWei LeeNoch keine Bewertungen
- HiPath 3000 Data Sheet PDFDokument10 SeitenHiPath 3000 Data Sheet PDFStoica AlexandruNoch keine Bewertungen
- Lanelet2: A High-Definition Map Framework For The Future of Automated DrivingDokument8 SeitenLanelet2: A High-Definition Map Framework For The Future of Automated DrivingJEICK HINCAPIE BARRERANoch keine Bewertungen
- UML Diagrams For Online Video Database Management System Like YDokument16 SeitenUML Diagrams For Online Video Database Management System Like YHawera SolomonNoch keine Bewertungen