Beruflich Dokumente
Kultur Dokumente
Electronics Assignment
Hochgeladen von
Mookie RichardOriginalbeschreibung:
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Electronics Assignment
Hochgeladen von
Mookie RichardCopyright:
Verfügbare Formate
Jahmal Richard Data Communication
Data Communication
1. Explaining the operations of simplex and duplex data communications
Simplex
Data in a simplex channel is always one way. Simplex channels are not often used because it is not possible to send back error or control signals to the transmit end. It's like a one way street. An example of simplex is Television, or Radio.
Half Duplex A half-duplex channel can send and receive, but not at the same time. It's like a one-lane bridge where two way traffic must give way in order to cross. Only one end transmits at a time, the other end receives. In addition, it is possible to perform error detection and request the sender to retransmit information that arrived corrupted. Another example of half-duplex is talk-back radio, and CB Radio (Citizens Band). You might have seen movies where truckies (drivers of very big trucks) communicate to each other, and when they want the other person to speak they say "over". This is because only one person can talk at a time. Full Duplex Data can travel in both directions simultaneously. There is no need to switch from transmit to receive mode like in half duplex. Its like a two lane bridge on a two-lane highway. Have you ever watched these television talk shows where the host has a number of people on the show, and they all try to talk at once. Well, that's full duplex! Of course, in the world of data communications, full duplex allows both way communication simultaneously. An example can be a consumer which uses a cable connection to not only receive TV channels, but also the same cable to support their phone and Internet surfing.
Jahmal Richard Data Communication
2. Explaining the operations of synchronous and asynchronous data communications
Asynchronous means "not synchronous". Synchronous means "agreed timing for the sending of ones and zeroes (bits)"--that is, the transmit and receive sides of the communications circuit have bothered to coordinate (synchronize) their signal and have agreed just what a digital bit encoded into the signal looks like. All communications paths have carrier signals, the signals have a frequency, and encoding bits into the signal involves spacing them out at regular intervals, and carving out just how long it takes to transmit a bit Asynchronous communication utilizes a transmitter, a receiver and a wire without coordination about the timing of individual bits. There is no coordination between the two end points on just how long the transmiter leaves the signal at a certain level to represent a single digital bit. Each device uses a clock to measure out the 'length' of abit. The transmitting device simply transmits. The receiving device has to look at the incoming signal and figure out what it is receiving and coordinate and retime its clock to match the incoming signal.
3. Explaining the use and importance of regenerators in digital systems 4. Explaining the concepts of mutual information and channel capacity Each time the source (transmitter) sends a symbol, it is said to use the channel.The channel capacity is the maximum average information that can be sent per channel use.By definition, channel capacity (C) is the
maximum data rate at which reliable transmission of information over the channel is possible. At rates R<C reliable transmission of information over the channel is possible and at rates R>C reliable transmission is not possible. Shannon formula states that : C=max_p(x) { I(x;y) } where I(x;y) denotes the mutual information between X (channel input) and Y (channel output) and the maximization is carried out over all input probability distributions of the channel ( p(x) ). the mutual information between to random variables X and Y is defined as I(x;y)=xy{ p(x)p(y|x)log[p(x,y)/( p(x)p(y) )] } where the mutual information is in bits and the logarithm is in base 2.
5. Explaining the basic operating principles of PCM and FSK, PSK and DPSK digital modulation techniques
If the modulating signal is digital, the modulation is termed amplitude-shift keying (ASK), frequencyshift keying (FSK), or phase-shift keying (PSK), since in this case the discrete amplitudes of the digital signal can be said to shift the parameter of the carrier signal between a finite number of values. For a modulating signal with only two amplitudes, binary is sometimes added before these terms.
Frequency-shift keying (FSK) is a frequency modulation scheme in which digital information is transmitted through discrete frequency changes of a carrier wave. The simplest FSK is binary FSK (BFSK). BFSK uses a pair of discrete frequencies to transmit binary (0s and 1s)
Jahmal Richard Data Communication
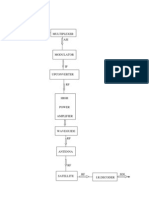
information. With this scheme, the "1" is called the mark frequency and the "0" is called the space frequency. The time domain of an FSK modulated carrier is illustrated in the figures to the right Pulse-code modulation (PCM) is a method used to digitally represent sampled analog signals. It is the standard form for digital audio in computers and various Blu-ray, DVD and Compact Disc formats, as well as other uses such as digital telephone systems. A PCM stream is a digital representation of an analog signal, in which the magnitude of the analog signal is sampled regularly at uniform intervals, with each sample being quantized to the nearest value within a range of digital steps Differential phase shift keying (DPSK) Differential phase shift keying (DPSK), a common form of phase modulation conveys data by changing the phase of carrier wave. In Phase shift keying, High state contains only one cycle but DPSK contains one and half cycle.
Phase-shift keying (PSK) is a digital modulation scheme that conveys data by changing, or modulating, the phase of a reference signal (the carrier wave).
6. Stating the basic principles of error detection and correction, including CRC and Hamming Codes
Error detection and correction or error control are techniques that enable reliable delivery of digital
data over unreliable communication channels. Many communication channels are subject to channel noise, and thus errors may be introduced during transmission from the source to a receiver. Error detection techniques allow detecting such errors, while error correction enables reconstruction of the original data. A cyclic redundancy check (CRC) is an error detecting code commonly used in digital networks and storage devices to detect accidental changes to raw data. Blocks of data entering these systems get a short check value attached, based on the remainder of a polynomial division of their contents; on retrieval the calculation is repeated, and corrective action can be taken against presumed data corruption if the check values do not match. CRCs are so called because the check (data verification) value is a redundancy (it adds no information to the message) and the algorithm is based on cyclic codes. CRCs are popular because they are simple to implement in binary hardware, easy to analyze mathematically, and particularly good at detecting common errors caused by noise in transmission channels. Because the check value has a fixed length, the function that generates it is occasionally used as a hash function Hamming codes are a family of linear error-correcting codes. Hamming codes can detect up to two and correct up to one bit errors. By contrast, the simple parity code cannot correct errors, and can detect only an odd number of errors. Hamming codes are special in that they are perfect codes, that is, they achieve the highest possible rate for codes with their block length and minimum distance.
7. Stating the basic principles of Intercomputer Communications- UART and USART
UART - Universal Asyncronous Receiver Transmitter USART - Universal Syncronous Asyncronous Receiver Transmitter
Jahmal Richard Data Communication
UART is a type of "asynchronous receiver/transmitter", a piece of computer hardware that translates data between parallel and serial forms. UARTs are commonly used in conjunction with communication standards such as EIA, RS-232, RS-422 or RS-485. The universal designation indicates that the data format and transmission speeds are configurable and that the actual electric signaling levels and methods (such as differential signaling etc.) typically are handled by a special driver circuit external to the UART. a UART that can also communicate synchronously; these devices are called USARTs (universal synchronous/asynchronous receiver/transmitter).
8. Describing the commonly used demodulation techniques
Demodulation is the act of extracting the original information-bearing signal from a modulated carrier wave. A demodulator is an electronic circuit (or computer program in a software-defined radio) that is [1] used to recover the information content from the modulated carrier wave. These terms are traditionally used in connection with radio receivers, but many other systems use many kinds of demodulators. Another common one is in a modem, which is a contraction of the terms modulator/demodulator.
9. Describing Ring, Star and Bus computer networking topologies
A network topology describes a network's layout and arrangement, the way in which the computers and hardware (printers, scanners, etc), known as nodes, are all linked together. There are 3 key network topologies each of which have their own advantages and disadvantages. Bus topology The type of network topology is where all the nodes of the network are connected to a central line. All data transmitted between nodes goes through the central cable.
Jahmal Richard Data Communication
Advantages
Easy to add and remove nodes Requires small amount of cable compared to other topologies so is less expensive and easier to setup and troubleshoot.
Disadvantages
A failure in the central line means the whole network will go down. Only one route for data to take so will performance will decrease as more data is transmitted.
Ring topology In a ring topology all the nodes are connected together in a loop. Data is transmitted from node to node in a single direction.
Jahmal Richard Data Communication
Advantages
As all the data can only travel in one direction the transmission of messages is simple and high rates can be achieved.
There is no dependence or need of a central computer or mainframe.
Disadvantages
If on node or line fails then data cannot continue to be transmitted between all the rest of the nodes in the network.
Harder to add new nodes into the system, requires the network to be disrupted.
Star topology In the star network topology each node is connected directly to a central computer or mainframe.
Jahmal Richard Data Communication
Advantages
More secure connection as data is sent directly between nodes (unlike ring networks) A failure of the cable will only affect one node, hence faults are easier to pinpoint. Easy to add new nodes without any disruption
Disadvantages
Requires and is dependant upon a central computer. Requires more cable and is therefore more expensive to setup.
Sources http://uva.ulb.ac.be/cit_courseware/datacomm/dc_014.htm http://en.wikipedia.org/wiki/Hamming_code http://en.wikipedia.org/wiki/Demodulation http://en.wikipedia.org/wiki/Universal_asynchronous_receiver/transmitter ..
Das könnte Ihnen auch gefallen
- Error-Correction on Non-Standard Communication ChannelsVon EverandError-Correction on Non-Standard Communication ChannelsNoch keine Bewertungen
- Data Communication Basics: What Is Data CommunicationsDokument14 SeitenData Communication Basics: What Is Data CommunicationsKigenzaNoch keine Bewertungen
- GSM NotesDokument3 SeitenGSM NotesRamakant BhardwajNoch keine Bewertungen
- Signal Integrity: From High-Speed to Radiofrequency ApplicationsVon EverandSignal Integrity: From High-Speed to Radiofrequency ApplicationsNoch keine Bewertungen
- Chapter V FinalDokument16 SeitenChapter V FinalhariNoch keine Bewertungen
- Software Radio: Sampling Rate Selection, Design and SynchronizationVon EverandSoftware Radio: Sampling Rate Selection, Design and SynchronizationNoch keine Bewertungen
- Pulse-Code Modulation (PCM) Is A Method Used ToDokument8 SeitenPulse-Code Modulation (PCM) Is A Method Used ToMwesigye KennethNoch keine Bewertungen
- Data Communication EssentialsDokument13 SeitenData Communication EssentialsAADIKHANNoch keine Bewertungen
- Data Comm. & NetworkDokument139 SeitenData Comm. & NetworkAkash SachanNoch keine Bewertungen
- Communications 2: Modulation and Coding TechniquesDokument9 SeitenCommunications 2: Modulation and Coding Techniquesbecy welbaNoch keine Bewertungen
- Unit-V Communication InterfaceDokument16 SeitenUnit-V Communication Interfacesreekantha2013Noch keine Bewertungen
- DCN Chapter 1 - Part 1Dokument45 SeitenDCN Chapter 1 - Part 1Esta AmeNoch keine Bewertungen
- Data Communications - A.K MhazoDokument158 SeitenData Communications - A.K MhazoGloria Matope100% (1)
- Basic Telecommunications Networking TermsDokument4 SeitenBasic Telecommunications Networking Termstariq500Noch keine Bewertungen
- Chapter One: Data Communication BasicsDokument46 SeitenChapter One: Data Communication BasicsWiki EthiopiaNoch keine Bewertungen
- Concepts of Digital CommunicationsDokument88 SeitenConcepts of Digital CommunicationsMANASA P (RA2011004010071)Noch keine Bewertungen
- FoN - Chapter OneDokument36 SeitenFoN - Chapter OneNasis DerejeNoch keine Bewertungen
- HF TXDokument15 SeitenHF TXMuhammad Sharif JanjuaNoch keine Bewertungen
- 8251 Material PDFDokument31 Seiten8251 Material PDFskarthikpriyaNoch keine Bewertungen
- Starz University: Presentation: Switching Engineering in Comma Widimongar W. Jarque Id: 2774Dokument9 SeitenStarz University: Presentation: Switching Engineering in Comma Widimongar W. Jarque Id: 2774Widimongar W. JarqueNoch keine Bewertungen
- Wireless Technology Viva Questions and Answer Mca Sem5Dokument12 SeitenWireless Technology Viva Questions and Answer Mca Sem5Unknown100% (4)
- S Cada ModemDokument15 SeitenS Cada ModemRobin TiolieNoch keine Bewertungen
- Internet Technologies (IT)Dokument167 SeitenInternet Technologies (IT)Pramod GedamNoch keine Bewertungen
- Computer NetworksDokument15 SeitenComputer NetworksTrevor ChinguwoNoch keine Bewertungen
- SDI ASI Encoder MultiplexerDokument41 SeitenSDI ASI Encoder MultiplexerChristie MillerNoch keine Bewertungen
- Unit 10 Assignment 2 Etinosa Enomayo 1.1Dokument8 SeitenUnit 10 Assignment 2 Etinosa Enomayo 1.1eet1nosa15Noch keine Bewertungen
- Data Comm and Comp Networking Lecture NoteDokument35 SeitenData Comm and Comp Networking Lecture NoteMikiyas GetasewNoch keine Bewertungen
- Data CommunicationDokument12 SeitenData CommunicationUmar shahryarNoch keine Bewertungen
- Unit 6 MCDokument44 SeitenUnit 6 MCkaustubhNoch keine Bewertungen
- Underwater Acoustic Modem: Midpoint ReportDokument10 SeitenUnderwater Acoustic Modem: Midpoint ReportRamesh KumarNoch keine Bewertungen
- Report On Cdma TechDokument47 SeitenReport On Cdma TechSubhalaxmi NayakNoch keine Bewertungen
- Digital Communication Chapter 11Dokument5 SeitenDigital Communication Chapter 11MIsh GomezNoch keine Bewertungen
- Interfaces in GSM002Dokument11 SeitenInterfaces in GSM002kkmNoch keine Bewertungen
- ELEC 382 Notes 13 Wired Digital CommunicationDokument9 SeitenELEC 382 Notes 13 Wired Digital CommunicationKenan BaltaciNoch keine Bewertungen
- Data Communication and Networking Prelims ExamDokument7 SeitenData Communication and Networking Prelims ExamSagarAnchalkarNoch keine Bewertungen
- 7 Telephone NetworksDokument7 Seiten7 Telephone NetworksKuldeep KumarNoch keine Bewertungen
- 7 Telephone NetworksDokument7 Seiten7 Telephone NetworksKuldeep KumarNoch keine Bewertungen
- 7 Telephone NetworksDokument7 Seiten7 Telephone NetworksKuldeep KumarNoch keine Bewertungen
- Unit 2 Mobile Telecommunication Systems Medium Access Control (MAC) Address Is A Hardware Address Use To Uniquely Identify EachDokument43 SeitenUnit 2 Mobile Telecommunication Systems Medium Access Control (MAC) Address Is A Hardware Address Use To Uniquely Identify EachVani BaskaranNoch keine Bewertungen
- Cdma EnggDokument59 SeitenCdma EnggMakarand DereNoch keine Bewertungen
- CDMA OverviewDokument65 SeitenCDMA OverviewRaghavLambaNoch keine Bewertungen
- RF QuestionsDokument31 SeitenRF QuestionsShashank PrajapatiNoch keine Bewertungen
- TSN QN BankDokument14 SeitenTSN QN BankbeslinNoch keine Bewertungen
- GR 12 ICT2 TNotes 2Dokument23 SeitenGR 12 ICT2 TNotes 2Nuha RiyadNoch keine Bewertungen
- Analysis of Iterative Decoding For Turbo Codes Using Maximum A Posteriori AlgorithmDokument100 SeitenAnalysis of Iterative Decoding For Turbo Codes Using Maximum A Posteriori AlgorithmWilliam Paul MacherlaNoch keine Bewertungen
- Fpga Implementation of Direct Sequence Spread SpectrumDokument29 SeitenFpga Implementation of Direct Sequence Spread SpectrumThirumal ArunNoch keine Bewertungen
- Electronic Communication: Recap and Way ForwardDokument45 SeitenElectronic Communication: Recap and Way ForwardShawn MoyoNoch keine Bewertungen
- Data Communication and NetworkingDokument19 SeitenData Communication and NetworkingSandeep Shrestha100% (1)
- Overview Coding TheoryDokument2 SeitenOverview Coding TheoryManal SaadNoch keine Bewertungen
- Data CommunicationsDokument231 SeitenData CommunicationsGia AbongNoch keine Bewertungen
- Chapter IDokument60 SeitenChapter IOumer HussenNoch keine Bewertungen
- Networking CHAPTER 1Dokument8 SeitenNetworking CHAPTER 1Aiko GerongNoch keine Bewertungen
- Introduction To Digital CommunicationsDokument12 SeitenIntroduction To Digital CommunicationsYashwanthReddyNoch keine Bewertungen
- Code Division Multiple Access (CDMA) Is ADokument20 SeitenCode Division Multiple Access (CDMA) Is AShrini JonnalagaddaNoch keine Bewertungen
- 2 CDMA Basic Priniple - 24Dokument24 Seiten2 CDMA Basic Priniple - 24David JohnsNoch keine Bewertungen
- ECE 443 - Lecture 1Dokument17 SeitenECE 443 - Lecture 1chigbu chiamakaNoch keine Bewertungen
- Data Communication Refers To The Transmission of This Digital Data Between Two or More Computers.aDokument33 SeitenData Communication Refers To The Transmission of This Digital Data Between Two or More Computers.aAnil KumarNoch keine Bewertungen
- IntroductionDokument31 SeitenIntroductionKent Ian ClaridadNoch keine Bewertungen
- Digital ModulationDokument9 SeitenDigital ModulationAdel AdelNoch keine Bewertungen
- Paul Meader & Robin Nolan - The Gypsy Jazz Songbook - 2Dokument42 SeitenPaul Meader & Robin Nolan - The Gypsy Jazz Songbook - 2Roman Gorodeckij86% (7)
- 公主日记英文剧本Dokument21 Seiten公主日记英文剧本shannonhu519Noch keine Bewertungen
- Keith Jarrett-I Remember Clifford PDFDokument3 SeitenKeith Jarrett-I Remember Clifford PDFJuan Carlos Flores100% (3)
- Listening: Pre-Intermediate Progress Test Units 1-3ADokument4 SeitenListening: Pre-Intermediate Progress Test Units 1-3AМаргарита СтанковаNoch keine Bewertungen
- Tda 7438Dokument18 SeitenTda 7438sontuyet82Noch keine Bewertungen
- Celine Dion - The Colour of My LoveDokument20 SeitenCeline Dion - The Colour of My LoveMagdalena Campos VelezNoch keine Bewertungen
- Clearwater TribuneDokument8 SeitenClearwater TribunewestribNoch keine Bewertungen
- Telecommunication HandbookDokument288 SeitenTelecommunication Handbookapi-374053080% (5)
- Wibree DocumentationDokument15 SeitenWibree DocumentationVasim Akram0% (2)
- Abchinese School: Certificate of AppreciationDokument15 SeitenAbchinese School: Certificate of AppreciationCham LaverintoNoch keine Bewertungen
- Mini FM Transmitter PDFDokument16 SeitenMini FM Transmitter PDFAreeba NasirNoch keine Bewertungen
- Unit 1 - Grammar 1. Avoiding RepetitionDokument2 SeitenUnit 1 - Grammar 1. Avoiding RepetitionVeasna Chann100% (1)
- Lesson 1 Media and Information LiteracyDokument9 SeitenLesson 1 Media and Information LiteracyGabriel PatronNoch keine Bewertungen
- Blue Wind - Yui Romaji Lyrics: Yui Music: CozziDokument7 SeitenBlue Wind - Yui Romaji Lyrics: Yui Music: CozziNikodemus PrajnadibyaNoch keine Bewertungen
- The Sound of Silence Accordi Simon Garfunkel Accordi&TestoDokument4 SeitenThe Sound of Silence Accordi Simon Garfunkel Accordi&TestomarcoNoch keine Bewertungen
- Best 100 InstrumentalDokument3 SeitenBest 100 InstrumentalMohd Shahlan Sidi AhmadNoch keine Bewertungen
- GoldenBookofSong1923 PDFDokument124 SeitenGoldenBookofSong1923 PDFJohn Gibbins86% (7)
- WiFi Frequency SpectrumDokument9 SeitenWiFi Frequency SpectrumAlberto NakagawaNoch keine Bewertungen
- Beginner Lesson To Cello For SectionalDokument11 SeitenBeginner Lesson To Cello For Sectionalapi-513093583Noch keine Bewertungen
- Types of Antennas and Techniques Used in Antenna DesigningDokument3 SeitenTypes of Antennas and Techniques Used in Antenna Designing1760Simran PrasadNoch keine Bewertungen
- Dwnload Full Basic Environmental Technology Water Supply Waste Management and Pollution Control 6th Edition Nathanson Test Bank PDFDokument36 SeitenDwnload Full Basic Environmental Technology Water Supply Waste Management and Pollution Control 6th Edition Nathanson Test Bank PDFeamdsumberr100% (15)
- Antony Reimagining - David WesselDokument4 SeitenAntony Reimagining - David Wesselmcain93Noch keine Bewertungen
- Cannonball Adderley - Mercy Mercy MercyDokument1 SeiteCannonball Adderley - Mercy Mercy MercyDan H100% (2)
- Lee-Konitz-10-Step-Method All The ThingsDokument3 SeitenLee-Konitz-10-Step-Method All The ThingsAnders Haraldsson100% (7)
- Manual - QualiPoc Android 12.0.0Dokument32 SeitenManual - QualiPoc Android 12.0.0djnava88Noch keine Bewertungen
- Classification of Radio WavesDokument4 SeitenClassification of Radio WavesmayankfirstNoch keine Bewertungen
- Grade 5 Theory Music VocabularyDokument5 SeitenGrade 5 Theory Music VocabularyChow Tsz HinNoch keine Bewertungen
- GFW8 WM CompareDokument2 SeitenGFW8 WM ComparelsueyinNoch keine Bewertungen
- GSM - The Network Switching Subsystem (NSS) : The Switching System Includes The Following Functional ElementsDokument3 SeitenGSM - The Network Switching Subsystem (NSS) : The Switching System Includes The Following Functional ElementsnuurNoch keine Bewertungen
- India CCTV Market Outlook 2016Dokument4 SeitenIndia CCTV Market Outlook 2016Neeraj ChawlaNoch keine Bewertungen
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsVon EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsBewertung: 5 von 5 Sternen5/5 (1)
- Hacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxVon EverandHacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxBewertung: 4.5 von 5 Sternen4.5/5 (67)
- Microsoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsVon EverandMicrosoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsNoch keine Bewertungen
- Microsoft Certified Azure Fundamentals Study Guide: Exam AZ-900Von EverandMicrosoft Certified Azure Fundamentals Study Guide: Exam AZ-900Noch keine Bewertungen
- Cybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringVon EverandCybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringBewertung: 5 von 5 Sternen5/5 (40)
- AWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamVon EverandAWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamNoch keine Bewertungen
- Cybersecurity: The Beginner's Guide: A comprehensive guide to getting started in cybersecurityVon EverandCybersecurity: The Beginner's Guide: A comprehensive guide to getting started in cybersecurityBewertung: 5 von 5 Sternen5/5 (2)
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNVon EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNBewertung: 5 von 5 Sternen5/5 (1)
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionVon EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionBewertung: 5 von 5 Sternen5/5 (4)
- Alcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast ExamsVon EverandAlcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast ExamsNoch keine Bewertungen
- Networking Fundamentals: Develop the networking skills required to pass the Microsoft MTA Networking Fundamentals Exam 98-366Von EverandNetworking Fundamentals: Develop the networking skills required to pass the Microsoft MTA Networking Fundamentals Exam 98-366Noch keine Bewertungen
- Azure Networking: Command Line Mastery From Beginner To ArchitectVon EverandAzure Networking: Command Line Mastery From Beginner To ArchitectNoch keine Bewertungen
- ITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationVon EverandITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationBewertung: 5 von 5 Sternen5/5 (2)
- Concise Guide to OTN optical transport networksVon EverandConcise Guide to OTN optical transport networksBewertung: 4 von 5 Sternen4/5 (2)
- AWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamVon EverandAWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamBewertung: 5 von 5 Sternen5/5 (1)
- Computer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)Von EverandComputer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)Noch keine Bewertungen
- Computer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityVon EverandComputer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityBewertung: 4.5 von 5 Sternen4.5/5 (13)
- Internet of Things: Principles and ParadigmsVon EverandInternet of Things: Principles and ParadigmsBewertung: 4.5 von 5 Sternen4.5/5 (6)
- Open Radio Access Network (O-RAN) Systems Architecture and DesignVon EverandOpen Radio Access Network (O-RAN) Systems Architecture and DesignNoch keine Bewertungen