Beruflich Dokumente
Kultur Dokumente
MQ SSL
Hochgeladen von
AirtelOriginalbeschreibung:
Originaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
MQ SSL
Hochgeladen von
AirtelCopyright:
Verfügbare Formate
1.
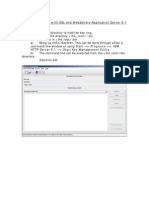
The sequence is : 1. (a) On the queue manager machine, open a Windows command prompt and enter strmqikm. This starts the IBM Key Management (iKeyman) GUI. 2. (a) Create a key repository for the queue manager : Select Key Database File -> New. Select "Key database type" := "CMS" ; "File Name" := "key.kdb" ; "Location" := "<MQdir>\Qmgrs\SSLQM\ssl" ; Select a password for this key repository. The password is encrypted and saved into file key.sth. 3. (b) click "New Self-Signed Certificate" (bottom-right corner) 4. (b) fill in the certificate attributes (Key Label must be ibmwebspheremq followed by the queue manager name in lowercase) Now the queue manager has a certificate. The queue manager presents this certificate to the WebSphere MQ client when the client connects. To validate the queue manager's certificate, the client needs the certification authority (CA) certificate. 5. (c) to extract the CA certificate, click Extract Certificate (bottom-right corner), and enter filename (sslqm.arm) and directory. This creates a file called sslqm.arm in C:\<MQDir>\Qmgrs\SSLQM\ssl\. You now must transfer the CA Certificate file to the client's key repository. 6. (c) Create c:\MQCLIENT\ if it does not exist, and copy (or FTP ASCII) the CA certificate file (sslqm.arm). 7. (c) on the client machine, run strmqikm
8.
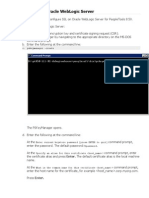
(c) create a key repository for the client : select Key Database File -> New Select "Key database type" := "CMS" ; "File Name" := "key.kdb" ; "Location" := "C:\MQCLIENT" ; Select a password for this key repository. Click Add (top-right corner) Select "Certificate file name" := "sslqm.arm" ; "Location" := "C:\MQCLIENT\" ; We created a certificate store for the MQ client in C:\MQCLIENT, but we have not told the client where to find it. To do this, set the MQSSLKEYR environment variable set mqsslkeyr=C:\MQCLIENT\key 9. SSL : (d) Change the client connection and server connection channel definitions for
echo al te r chl (SSL.CL IENTS) chl type(svrconn) sslc iph( t r i p l e _des_sha_us) ss lcauth(opt iona l ) runmqsc SSLQM
The change to the client connection channel updates the channel table (file AMQCLCHL.TAB) in your queue manager's @ipcc directory. Copy the channel table (or FTP binary) to the client directory (C:\MQCLIENT) in the client machine. 10. 11. 12. 13. 14. 15. 16. (d) Verify connection works : set mq mqchl l i b=C: \MQCLIENT mqchltab=AMQCLCHL.TAB mqsslkeyr=C:\MQCLIENT\key amqsputc Q1 SSLQM amqsgetc Q1 SSLQM
If the programs run successfully, it means that the client channel works with SSL. 2. Convert the SSL connection to two-way
SSL client authentication means that the client has a certificate assigned, which it presents to the server when the channel starts. To set up client authentication, we need to perform the following steps: o o o o a. Create a self-signed certificate for the client. b. Add the certification authority certificate to the queue manager. c. Change the server connection channel to request client authentication. d. Re-test.
The sequence is :
1.
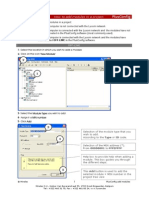
(a) to create a self-signed certificate for the client, on the client machine, run strmqikm This is the same as creating a self-signed certificate for the queue manager. The only difference is that we run it from the client machine. 2. (a) click the Open icon (or select Key Database File -> Open). 3. (a) provide the following values : "Key database type" := "CMS" ; "File Name" := "key.kdb" ; "Location" := "C:\MQCLIENT" ; enter the password. 4. (a) viewing Personal Certificates, click New Self-Signed Certificate (bottom-right corner). 5. (a) fill in the certificate attributes, as "Key Label" := "ibmwebspheremq" followed by the lowercase user ID. In our case: ibmwebspheremqemir Now the MQ client has a certificate, which it presents to the queue manager when the client connects. To validate the client's certificate, the queue manager needs the certification authority (CA) certificate.
6.
(b) click Provide "File Name" "C:\MQCLIENT\" ;
:=
Extract Certificate (bottom-right corner). <user ID>.arm, in our case: emir.arm; "Location" :=
Now, you must transfer the CA Certificate file to the queue manager's key repository. 7. (b) copy (or FTP ASCII) the CA certificate file (.arm) from the client's C:\MQCLIENT directory to the queue manager's ssl directory. This is <MQdir>\Qmgrs\SSLQM\ssl. 8. (b) on the queue manager machine, run strmqikm 9. (b) click the Open icon (or select Key Database File -> Open). Open the key.kdb file in <MQdir>\Qmgrs\SSLQM\ssl. Switch to viewing Signer Certificates. Click Add (top-right corner). Select "Certificate file name" := <user ID>.arm; "Location" := <MQdir>\Qmgrs\SSLQM\ssl\ ; Enter a label for the certificate, as the client's user ID ("emir"). 10. (c) to enable client authentication, the server connection channel must specify SSLCAUTH(REQUIRED). echo al te r chl (SSL.CL IENTS) chl type(svrconn) sslcauth( requi red) | runmqsc SSLQM 11. 12. 13. 14. 15. (d) run set mq mqchl l i b=C: \MQCLIENT mqchltab=AMQCLCHL.TAB mqsslkeyr=C:\MQCLIENT\key
16. 17.
amqsputc Q1 SSLQM amqsgetc Q1 SSLQM
If amqsputc fails with MQCONN ended with reason code 2393 or MQCONN ended with reason code 2059, stop and start the queue manager
Das könnte Ihnen auch gefallen
- Deploying Certificates Cisco Meeting Server: Design your certificates for CMS services and integrate with Cisco UCM Expressway and TMSVon EverandDeploying Certificates Cisco Meeting Server: Design your certificates for CMS services and integrate with Cisco UCM Expressway and TMSNoch keine Bewertungen
- SSL Interception On Proxy SG - 02 PDFDokument15 SeitenSSL Interception On Proxy SG - 02 PDFGsk SkNoch keine Bewertungen
- Creation and Installation of SSL Certificate For Key Tool NewDokument47 SeitenCreation and Installation of SSL Certificate For Key Tool NewT PrasadNoch keine Bewertungen
- Mastering C++ Network Automation: Run Automation across Configuration Management, Container Orchestration, Kubernetes, and Cloud NetworkingVon EverandMastering C++ Network Automation: Run Automation across Configuration Management, Container Orchestration, Kubernetes, and Cloud NetworkingNoch keine Bewertungen
- Kim TSM SSL Win PfadeDokument4 SeitenKim TSM SSL Win Pfadeasma merzNoch keine Bewertungen
- Weblogic 3Dokument12 SeitenWeblogic 3lava4242Noch keine Bewertungen
- NPrinting SSLDokument2 SeitenNPrinting SSLManuel Gomez FredesNoch keine Bewertungen
- MPESA SSL Guide PDFDokument7 SeitenMPESA SSL Guide PDFkikweteNoch keine Bewertungen
- SSL Connection in Managed MQ .NET (MQ v8)Dokument3 SeitenSSL Connection in Managed MQ .NET (MQ v8)Марфутин АнтонNoch keine Bewertungen
- SSL GuideDokument9 SeitenSSL Guidehelgebaly65Noch keine Bewertungen
- Now Open The Client - Ks File Using The " " Tool and Enter The PasswordDokument3 SeitenNow Open The Client - Ks File Using The " " Tool and Enter The Passwordniladri podderNoch keine Bewertungen
- How To Setup and Configure Commerce Data Exchange Real-Time ServiceDokument12 SeitenHow To Setup and Configure Commerce Data Exchange Real-Time ServiceIslam SultanNoch keine Bewertungen
- Using GSKit Tool and IHS-WebSphere Certification ProcessDokument8 SeitenUsing GSKit Tool and IHS-WebSphere Certification ProcessvaraNoch keine Bewertungen
- SSL Certificate Download ProcessDokument2 SeitenSSL Certificate Download Processkrishna mNoch keine Bewertungen
- Client To Box Certificate Auth VPNDokument9 SeitenClient To Box Certificate Auth VPNMihai MihutzNoch keine Bewertungen
- SPNEGO Based Single Sign-On Using Secure Login Server X.509 Client CertificatesDokument26 SeitenSPNEGO Based Single Sign-On Using Secure Login Server X.509 Client CertificatesJason CraigNoch keine Bewertungen
- Simple CADokument12 SeitenSimple CARameshChNoch keine Bewertungen
- A.5. Creating Your Own CertificatesDokument7 SeitenA.5. Creating Your Own CertificatesMaher Saad MechiNoch keine Bewertungen
- SSL For SharingDokument4 SeitenSSL For Sharingshivraj zambareNoch keine Bewertungen
- Implementing OAuth 2.0 With AWS API Gateway, Lambda, DynamoDB, and KMS - Part 2 - by Bilal Ashfaq - MediumDokument34 SeitenImplementing OAuth 2.0 With AWS API Gateway, Lambda, DynamoDB, and KMS - Part 2 - by Bilal Ashfaq - MediumProf SilvaNoch keine Bewertungen
- APACHE Web Server and SSL AuthenticationDokument8 SeitenAPACHE Web Server and SSL AuthenticationDJ JAMNoch keine Bewertungen
- PD25035Dokument8 SeitenPD25035Lam Khê PhạmNoch keine Bewertungen
- Updating The Network Controller Server CertificateDokument4 SeitenUpdating The Network Controller Server CertificateNavneetMishraNoch keine Bewertungen
- Environment Setup For FTPS: 1. Creation of Server CertificateDokument21 SeitenEnvironment Setup For FTPS: 1. Creation of Server Certificatescribd_renjithNoch keine Bewertungen
- Windows Openssl Ca Toolkit: Installation and ConfigurationDokument8 SeitenWindows Openssl Ca Toolkit: Installation and Configurationsantoshg83Noch keine Bewertungen
- Deploying Scom Gateway ServerDokument10 SeitenDeploying Scom Gateway Servernaveednezam2686Noch keine Bewertungen
- Faq Tomcat Soap SSLDokument9 SeitenFaq Tomcat Soap SSLhelixneuNoch keine Bewertungen
- Spnego Single Sign-On Using Secure Login Server X.509 Client CertificatesDokument25 SeitenSpnego Single Sign-On Using Secure Login Server X.509 Client CertificatesRodrigo XavierNoch keine Bewertungen
- SSL Config Was61 IhsDokument17 SeitenSSL Config Was61 IhsEsteban Adrian Lopez FajardoNoch keine Bewertungen
- SSLDokument2 SeitenSSLsurithearmyNoch keine Bewertungen
- Setting Up SSL On Oracle WebLogic Server (Configuración de Certificado SSL en PeopleSoft)Dokument17 SeitenSetting Up SSL On Oracle WebLogic Server (Configuración de Certificado SSL en PeopleSoft)Jesús ArredondoNoch keine Bewertungen
- SSL Over WebSphereDokument16 SeitenSSL Over WebSphereAnkit PoddarNoch keine Bewertungen
- Generating and Installing Domain Controller CertificateDokument2 SeitenGenerating and Installing Domain Controller CertificateGabriel Morales AngaritaNoch keine Bewertungen
- MB SSLDokument33 SeitenMB SSLRajesh0% (1)
- Pki OpensslDokument11 SeitenPki OpensslgdeepthiNoch keine Bewertungen
- SSL (Secure Socket Layer) : Steps To Configure SSL Certificate: For Web ServerDokument3 SeitenSSL (Secure Socket Layer) : Steps To Configure SSL Certificate: For Web ServerShailesh ChiliveriNoch keine Bewertungen
- Create Windows CA Certificate Templates For CUCMDokument32 SeitenCreate Windows CA Certificate Templates For CUCMDavid Van HerckNoch keine Bewertungen
- Manual de Creación de Entidad Certificadora LocalDokument7 SeitenManual de Creación de Entidad Certificadora LocalMelvin Alvaro Sorto MembreñoNoch keine Bewertungen
- Peap Configuration Guide v1.20: Self-Signing Certificates SectionDokument15 SeitenPeap Configuration Guide v1.20: Self-Signing Certificates SectionvladusgeniusNoch keine Bewertungen
- How To Configure SAP MII 12.0.3 Build 107 For HTTPSDokument9 SeitenHow To Configure SAP MII 12.0.3 Build 107 For HTTPSJesufrancis LinovazNoch keine Bewertungen
- Ibm Practical File 20222Dokument46 SeitenIbm Practical File 20222Aman KhubaniNoch keine Bewertungen
- Generating A Self Sign Certificate OpensslDokument5 SeitenGenerating A Self Sign Certificate Opensslpavan.sai2916889Noch keine Bewertungen
- Notas de ZimbraDokument37 SeitenNotas de Zimbrabonilla03Noch keine Bewertungen
- Free SSLDokument43 SeitenFree SSLBianca PisanniNoch keine Bewertungen
- Project Name: IBM MQ Configuring SSL DocumentDokument11 SeitenProject Name: IBM MQ Configuring SSL Documentchiranjeevi kvNoch keine Bewertungen
- Rsa Netwitness Platform: Blue Coat Proxysg SgosDokument14 SeitenRsa Netwitness Platform: Blue Coat Proxysg SgosShirley Diossana GarayNoch keine Bewertungen
- HowTo-100-CA Signed PxGridClient Selfsigned PxGridISEnodeDokument22 SeitenHowTo-100-CA Signed PxGridClient Selfsigned PxGridISEnodeToua LorNoch keine Bewertungen
- Common Errors in BW Related To SSLDokument24 SeitenCommon Errors in BW Related To SSLKrishna Chaitanya SunkavalliNoch keine Bewertungen
- Configuring Websphere App Server7 Secure Sockets Layer Client Certificate Authentication Sas9 3 Ebi ServerDokument28 SeitenConfiguring Websphere App Server7 Secure Sockets Layer Client Certificate Authentication Sas9 3 Ebi ServerAshokNoch keine Bewertungen
- Administration Console and CLI Certificate Tools - Zimbra - Tech CenterDokument17 SeitenAdministration Console and CLI Certificate Tools - Zimbra - Tech CenterfacundopaganiNoch keine Bewertungen
- WS Security Implementation Using Apache CXF and WSS4JDokument11 SeitenWS Security Implementation Using Apache CXF and WSS4JYogeshwar VajraveluNoch keine Bewertungen
- 3 ADFS Installation and ConfigurationDokument14 Seiten3 ADFS Installation and ConfigurationIngrid CardenasNoch keine Bewertungen
- ADS SSL Configuration ABAP To JAVADokument3 SeitenADS SSL Configuration ABAP To JAVASumeet SharmaNoch keine Bewertungen
- Self Signed SSLCertificateDokument2 SeitenSelf Signed SSLCertificateharikrishna242424100% (1)
- MQTT Secure Connection Over TLSDokument8 SeitenMQTT Secure Connection Over TLSMohamed Yassine GaraliNoch keine Bewertungen
- Keybrigding Certificates: SSL - Client - Ca - DirectoryDokument4 SeitenKeybrigding Certificates: SSL - Client - Ca - DirectorySignia DiseñoNoch keine Bewertungen
- Configuring CISCO ACS Server As Radius For Intel AMT 802.1x Clients With Windows DB Rev 3Dokument30 SeitenConfiguring CISCO ACS Server As Radius For Intel AMT 802.1x Clients With Windows DB Rev 3Angel AlarasNoch keine Bewertungen
- SSL Insight Certificate Installation GuideDokument15 SeitenSSL Insight Certificate Installation GuideluisNoch keine Bewertungen
- CRM On Demand Web Service LoginDokument19 SeitenCRM On Demand Web Service LoginSankalp DameleNoch keine Bewertungen
- Tableau Developer ResumeDokument3 SeitenTableau Developer ResumeGanapathiraju SravaniNoch keine Bewertungen
- Laudon Ess6 ch09Dokument41 SeitenLaudon Ess6 ch09MarkolineNoch keine Bewertungen
- Introduction To Excels Basic FeaturesDokument38 SeitenIntroduction To Excels Basic FeaturesBikram92Noch keine Bewertungen
- Queen's Medical Center v. Kaiser Foundation Health PlanDokument34 SeitenQueen's Medical Center v. Kaiser Foundation Health PlanAlex KacikNoch keine Bewertungen
- REST APIs Part 2 - Making REST API Calls With Postman PDFDokument29 SeitenREST APIs Part 2 - Making REST API Calls With Postman PDFmohamedNoch keine Bewertungen
- Using LDAP To Manage Users DocumentDokument57 SeitenUsing LDAP To Manage Users DocumentDilip Musunuru100% (1)
- Linux Kernel SlidesDokument477 SeitenLinux Kernel SlidesManuel GonzalezNoch keine Bewertungen
- File squid-3.HEAD-20130412-r12755.tar - GZ Dengan Cara Sebagai BerikutDokument4 SeitenFile squid-3.HEAD-20130412-r12755.tar - GZ Dengan Cara Sebagai BerikutYudi PermanaNoch keine Bewertungen
- A Guide To Site Disaster Recovery OptionsDokument8 SeitenA Guide To Site Disaster Recovery Optionslyax1365100% (1)
- Aamir Resume (Pune Address)Dokument3 SeitenAamir Resume (Pune Address)AamirNoch keine Bewertungen
- RadioDJ - Frequently Asked Questions - RadioDJ - Free Radio Automation SoftwareDokument2 SeitenRadioDJ - Frequently Asked Questions - RadioDJ - Free Radio Automation SoftwarePatito FeoNoch keine Bewertungen
- Self Service Portal Draft User Guide: Commercial Bank of EthiopiaDokument13 SeitenSelf Service Portal Draft User Guide: Commercial Bank of Ethiopiaዝምታ ተሻለNoch keine Bewertungen
- EN - Ebook-Google-Analytics-App-WebDokument77 SeitenEN - Ebook-Google-Analytics-App-WebTommi PohjolaNoch keine Bewertungen
- Youtube Planner: Company DetailsDokument5 SeitenYoutube Planner: Company DetailsDiana Siachoque0% (2)
- Laravel HelpDokument181 SeitenLaravel HelpSandip PhuseNoch keine Bewertungen
- Silk TestDokument2 SeitenSilk Testapi-3700829100% (1)
- CVDokument4 SeitenCVAyman BadawiNoch keine Bewertungen
- Loc JPDokument73 SeitenLoc JPThe KnightNoch keine Bewertungen
- How To Add ModulesDokument7 SeitenHow To Add ModulesAnkit GuptaNoch keine Bewertungen
- Whatfix Deployment Document - GroupPolicyDokument12 SeitenWhatfix Deployment Document - GroupPolicythiagoomNoch keine Bewertungen
- MSDN Library Visual Studio 6.0 - Read MeDokument8 SeitenMSDN Library Visual Studio 6.0 - Read MeEtty Aryati Priyanto100% (1)
- Chapter One Lab-2.1 - Navigate The IOSDokument4 SeitenChapter One Lab-2.1 - Navigate The IOSFedasa BoteNoch keine Bewertungen
- GNX4 Operating System Update Procedure (Via USB)Dokument1 SeiteGNX4 Operating System Update Procedure (Via USB)Tom GrossNoch keine Bewertungen
- Offline Interactive PDF Form Using DownloadDokument13 SeitenOffline Interactive PDF Form Using DownloadFede LeverNoch keine Bewertungen
- Top Free Sites To Download Books - Google SearchDokument1 SeiteTop Free Sites To Download Books - Google Searchrony chidiacNoch keine Bewertungen
- Is It A TV? or Something Better?: FeaturesDokument2 SeitenIs It A TV? or Something Better?: FeaturesCsr GraficaNoch keine Bewertungen
- Multiple RDP (Remote Desktop) Sessions in Windows 10Dokument1 SeiteMultiple RDP (Remote Desktop) Sessions in Windows 10neycrochaNoch keine Bewertungen
- Endpoint Security Via Application Sandboxing and Virtualization: Past, Present, FutureDokument27 SeitenEndpoint Security Via Application Sandboxing and Virtualization: Past, Present, FutureAnubha KabraNoch keine Bewertungen
- Ruby On Rails Guides v2 - Ruby On RailsDokument1.649 SeitenRuby On Rails Guides v2 - Ruby On RailsManmeet Dhaliwal100% (1)
- Faktor-Faktor Lingkungan Kerja Dan Kaitannya Dengan k3 - YouTubeDokument5 SeitenFaktor-Faktor Lingkungan Kerja Dan Kaitannya Dengan k3 - YouTubeNashrllahNoch keine Bewertungen
- The Dark Net: Inside the Digital UnderworldVon EverandThe Dark Net: Inside the Digital UnderworldBewertung: 3.5 von 5 Sternen3.5/5 (104)
- Defensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityVon EverandDefensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityBewertung: 5 von 5 Sternen5/5 (1)
- The Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellVon EverandThe Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellBewertung: 5 von 5 Sternen5/5 (6)
- How to Do Nothing: Resisting the Attention EconomyVon EverandHow to Do Nothing: Resisting the Attention EconomyBewertung: 4 von 5 Sternen4/5 (421)
- More Porn - Faster!: 50 Tips & Tools for Faster and More Efficient Porn BrowsingVon EverandMore Porn - Faster!: 50 Tips & Tools for Faster and More Efficient Porn BrowsingBewertung: 3.5 von 5 Sternen3.5/5 (23)
- The Wires of War: Technology and the Global Struggle for PowerVon EverandThe Wires of War: Technology and the Global Struggle for PowerBewertung: 4 von 5 Sternen4/5 (34)
- The Internet Con: How to Seize the Means of ComputationVon EverandThe Internet Con: How to Seize the Means of ComputationBewertung: 5 von 5 Sternen5/5 (6)
- CISM Certified Information Security Manager Study GuideVon EverandCISM Certified Information Security Manager Study GuideNoch keine Bewertungen
- Nine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's ComputersVon EverandNine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's ComputersBewertung: 5 von 5 Sternen5/5 (7)
- React.js Design Patterns: Learn how to build scalable React apps with ease (English Edition)Von EverandReact.js Design Patterns: Learn how to build scalable React apps with ease (English Edition)Noch keine Bewertungen
- So You Want to Start a Podcast: Finding Your Voice, Telling Your Story, and Building a Community That Will ListenVon EverandSo You Want to Start a Podcast: Finding Your Voice, Telling Your Story, and Building a Community That Will ListenBewertung: 3.5 von 5 Sternen3.5/5 (24)
- Grokking Algorithms: An illustrated guide for programmers and other curious peopleVon EverandGrokking Algorithms: An illustrated guide for programmers and other curious peopleBewertung: 4 von 5 Sternen4/5 (16)
- Practical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTVon EverandPractical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTNoch keine Bewertungen
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsVon EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsBewertung: 5 von 5 Sternen5/5 (1)
- An Internet in Your Head: A New Paradigm for How the Brain WorksVon EverandAn Internet in Your Head: A New Paradigm for How the Brain WorksNoch keine Bewertungen
- Python for Beginners: The 1 Day Crash Course For Python Programming In The Real WorldVon EverandPython for Beginners: The 1 Day Crash Course For Python Programming In The Real WorldNoch keine Bewertungen
- How to Start a Blog with WordPress: Beginner's Guide to Make Money by Writing OnlineVon EverandHow to Start a Blog with WordPress: Beginner's Guide to Make Money by Writing OnlineBewertung: 3.5 von 5 Sternen3.5/5 (2)
- Web Copy That Sells: The Revolutionary Formula for Creating Killer Copy That Grabs Their Attention and Compels Them to BuyVon EverandWeb Copy That Sells: The Revolutionary Formula for Creating Killer Copy That Grabs Their Attention and Compels Them to BuyBewertung: 4 von 5 Sternen4/5 (13)
- Ten Arguments for Deleting Your Social Media Accounts Right NowVon EverandTen Arguments for Deleting Your Social Media Accounts Right NowBewertung: 4 von 5 Sternen4/5 (388)
- HTML5 and CSS3 Masterclass: In-depth Web Design Training with Geolocation, the HTML5 Canvas, 2D and 3D CSS Transformations, Flexbox, CSS Grid, and More (English Edition)Von EverandHTML5 and CSS3 Masterclass: In-depth Web Design Training with Geolocation, the HTML5 Canvas, 2D and 3D CSS Transformations, Flexbox, CSS Grid, and More (English Edition)Noch keine Bewertungen