Beruflich Dokumente
Kultur Dokumente
Dos N Ddos
Hochgeladen von
singh_manpreet8080Originalbeschreibung:
Originaltitel
Copyright
Verfügbare Formate
Dieses Dokument teilen
Dokument teilen oder einbetten
Stufen Sie dieses Dokument als nützlich ein?
Sind diese Inhalte unangemessen?
Dieses Dokument meldenCopyright:
Verfügbare Formate
Dos N Ddos
Hochgeladen von
singh_manpreet8080Copyright:
Verfügbare Formate
DOS AND DDOS ATTACKS
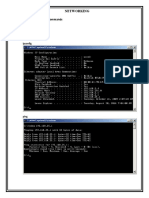
DOS ATTACKS:Denial of Service (DoS) attack is an attack against any system component that attempts to force that system component to limit, or even halt, normal services. Only one person and one server is involved in DoS attack. In easy language, DoS is the continous attempt or receiving a packet of data from a particular websites, it may be done intentionally or unintenionally. TYPES OF DoS ATTACKS:1.Bandwidth attacks 2.Protocol attacks 3.Logic attacks TECHNIQUES USED IN DoS ATTACKS:1.COMMAND PROMPT METHOD:It is a technique which uses command prompt. Just open the cmd and write the following there: Ping (i.p.of the victim) t(e.g ping 192.168.25.1 t),then a victims site will be busy in replying us like shown below. So victims site can be shutdown using this method i.But it can take some time.
2.USING RDoS TOOL:This is a website DOS attacking technique done by a tool called rDOS. It is build to attack a website having open vulnerable port. In this you have to enter the victims ip and a particular port for dos attack.
3.USING CRAZY PINGER:Crazy pinger is an network IP DoS attack application help you to flood a reuired IP with lots of packets and making it busy in replying and at last performing denial of services attack .Using this we can achieve a fastest dos attck because using this software we can open lots of pinging windows, which will individually attack the victim.
DDOS ATTACKS:Distributed Denial of Service (DDoS) attack is a DoS attack that occurs from more than one source, and/or from more than one location, at the same time.In DDoS more than one person and one server is involved. Often, the DDoS attackers are not aware that they are engaging in a DoS attack against a site, and are duped into joining the attack by a third party. e.g.:- When P.T.U. results are out, we open the website to see result,but most of that particular time a rush appears to that site, so a deadlock is appeared, so it is a kind of DDoS attack but done in a unintensional way. TOOL FOR DDoS:Tool used for DDoS is low orbit ion cannon. It is very easy to use, you just have to enter the URL or IP and lock it. Then select the attack option and then all DoS n DDoS work will do this software.It is preferred for DDoS because it can flood the server with both tcp and udp packets.
REAL LIFE EXAMPLE OF DDoS:DDoS attack used by Anonymous group(known for DDoS attacks) take down the master card and visa card websites. So due to this master card loses a number of crore rupees in a single day. So it can be very dangerous. DDOS COUNTER MEASURE:1. Insist on traffic charts directly by the datacenter. If you have taken hosting from a reseller, get the traffic charts and contact the datacenter directly to confirm. 2. If at any point in time your hosting provider / reseller is providing obstructions in validating the DDoS attack and its size, etc. Go direct. It is your right to ask and verify. 3. Never believe what your host provider tells you, until and unless it has been validated by the datacenter.
4. Try to contact the datacenter (you will have to be a little persistent) but try to talk to some senior Network Engineer and get more on the type of DDoS attack that is happening. Try to get some captured packets of the attack. Anything and everything you can get out of them is a plus. 5. Be VERY meticulous. Write everything down. 6. Take notes. All of it write it down. 7. Ask for names and designations. 8. Note down the time and date when you call someone. 9. Make a timeline of events, when the attack started, when were you informed, etc. Why? Because DDoS (be it recipient) can/could become messy, legally/lawfully speaking. 10. If you have noted everything down. You save your own a...
Das könnte Ihnen auch gefallen
- MPLS-Enabled Applications: Emerging Developments and New TechnologiesVon EverandMPLS-Enabled Applications: Emerging Developments and New TechnologiesBewertung: 4 von 5 Sternen4/5 (4)
- Implementation of DDoSDokument11 SeitenImplementation of DDoSUzma ZakiNoch keine Bewertungen
- DDoS Attack Detection Using Deep LearningDokument7 SeitenDDoS Attack Detection Using Deep LearningIAES IJAINoch keine Bewertungen
- LAB 02 - Installation of FTP ServerDokument3 SeitenLAB 02 - Installation of FTP ServerMadhukar WakadeNoch keine Bewertungen
- Risk Management: "Once We Know Our Weaknesses, They Cease To Do Us Any Harm"Dokument61 SeitenRisk Management: "Once We Know Our Weaknesses, They Cease To Do Us Any Harm"Paolo LegaspiNoch keine Bewertungen
- 03-MAC Address PDFDokument12 Seiten03-MAC Address PDFsuresh1776job80% (5)
- ITNE3006 Design Network Infrastructure: AssignmentDokument12 SeitenITNE3006 Design Network Infrastructure: Assignmentqwerty100% (1)
- Experiment No 1Dokument3 SeitenExperiment No 1dangi.bharat4100% (1)
- PT Simulation 1 - Intro To Cisco Packet TracerDokument6 SeitenPT Simulation 1 - Intro To Cisco Packet TracerRaymond NocheteNoch keine Bewertungen
- Config Basica Router SwitchDokument4 SeitenConfig Basica Router SwitchRogelio Tello100% (1)
- Linux Firewalls PPT 4205Dokument80 SeitenLinux Firewalls PPT 4205Mukul JhaNoch keine Bewertungen
- How To Configure A Peer To Peer NetworkDokument64 SeitenHow To Configure A Peer To Peer NetworkMean LymengNoch keine Bewertungen
- Assignment 4.1Dokument6 SeitenAssignment 4.1Navneet kumarNoch keine Bewertungen
- DHCP QuestionDokument9 SeitenDHCP QuestionLalit KaushikNoch keine Bewertungen
- Project Synopsis On LAN ConnectionDokument15 SeitenProject Synopsis On LAN ConnectionডৰাজবংশীNoch keine Bewertungen
- Network Digram DocumentDokument1 SeiteNetwork Digram Documentcarlk2004Noch keine Bewertungen
- Internet Access MethodsDokument4 SeitenInternet Access Methodsdrgnarayanan100% (1)
- Boader Gateway Protocol PresentationDokument31 SeitenBoader Gateway Protocol PresentationedwardNoch keine Bewertungen
- Mikrotik Router SetupDokument14 SeitenMikrotik Router SetupAlisya GunawanNoch keine Bewertungen
- CS432 - Cisco Packet Tracer PDFDokument6 SeitenCS432 - Cisco Packet Tracer PDFOburu David KatandiNoch keine Bewertungen
- Compile Software From Source Code - WIREDDokument6 SeitenCompile Software From Source Code - WIREDMartín LehoczkyNoch keine Bewertungen
- 14.3.5 Packet Tracer - Basic Router Configuration ReviewDokument5 Seiten14.3.5 Packet Tracer - Basic Router Configuration ReviewHạnh100% (1)
- Mplement Ontent Iltering: Lay Minh (Makito)Dokument27 SeitenMplement Ontent Iltering: Lay Minh (Makito)NaingWinOoNoch keine Bewertungen
- 5135-Ethical HackingDokument12 Seiten5135-Ethical HackingAslam RecoveryNoch keine Bewertungen
- Lab Sheet 3Dokument8 SeitenLab Sheet 3api-241418009Noch keine Bewertungen
- DragonOS - Focal DownloadDokument5 SeitenDragonOS - Focal DownloadEkaterina HoffmannNoch keine Bewertungen
- Cisco Ipsec Static DynamicDokument9 SeitenCisco Ipsec Static DynamichsitadmNoch keine Bewertungen
- Windows Networking CommandsDokument4 SeitenWindows Networking CommandsSulltana ShaqiriNoch keine Bewertungen
- Lab ManualDokument16 SeitenLab Manualsro1990Noch keine Bewertungen
- 5.0.1.2 DR and BDR Elections Instructions IG PDFDokument2 Seiten5.0.1.2 DR and BDR Elections Instructions IG PDFMaksim KorsakovNoch keine Bewertungen
- Ccna I Exploration Lab 2 - Intro To Packet Tracer Lab Required Materials - Data File Lsg01-Ptskills1.PkaDokument4 SeitenCcna I Exploration Lab 2 - Intro To Packet Tracer Lab Required Materials - Data File Lsg01-Ptskills1.PkaElizabeth NewmanNoch keine Bewertungen
- Chapter 1 LAN DesignDokument22 SeitenChapter 1 LAN DesignFatah Nur AlamNoch keine Bewertungen
- How To Protect Your MikroTik RouterOSDokument13 SeitenHow To Protect Your MikroTik RouterOSRuben DarioNoch keine Bewertungen
- Network CommandsDokument21 SeitenNetwork Commandsivica77Noch keine Bewertungen
- Exercises Netflow NfsenDokument9 SeitenExercises Netflow NfsenDeepak KandaNoch keine Bewertungen
- Monitoring Netflow With NfSenDokument5 SeitenMonitoring Netflow With NfSenThanhNN0312Noch keine Bewertungen
- OpenVas Scanner in KaliDokument6 SeitenOpenVas Scanner in KaliminingdbNoch keine Bewertungen
- IP VPN OverviewDokument34 SeitenIP VPN OverviewJanek PodwalaNoch keine Bewertungen
- Network Forensic ReportDokument3 SeitenNetwork Forensic Reportchauhan_vinay12Noch keine Bewertungen
- 10 Useful Windows Networking CommandsDokument6 Seiten10 Useful Windows Networking CommandsLeon KityamwiNoch keine Bewertungen
- OSCP Survival GuideDokument63 SeitenOSCP Survival Guidesetyahangga3Noch keine Bewertungen
- Command DescriptionDokument2 SeitenCommand DescriptionGiova RossiNoch keine Bewertungen
- CCNA 1 Exploration ENetwork Final Exam Form1 V 4.0Dokument19 SeitenCCNA 1 Exploration ENetwork Final Exam Form1 V 4.0sEcZxNoch keine Bewertungen
- Ettercap TutorialDokument35 SeitenEttercap TutorialAnonymous OCDJg17ZNoch keine Bewertungen
- Forensics Tutorial 12 - Network Forensics With WiresharkDokument20 SeitenForensics Tutorial 12 - Network Forensics With WiresharkMary Amirtha Sagayee. GNoch keine Bewertungen
- Anatomy of A Remote Kernel Exploit: Dan RosenbergDokument80 SeitenAnatomy of A Remote Kernel Exploit: Dan RosenbergrodrigoduocNoch keine Bewertungen
- Router Security Configuration GuideDokument291 SeitenRouter Security Configuration GuideghaniNoch keine Bewertungen
- 4.6.6.5 Lab - Using Wireshark To Examine HTTP and HTTPS TrafficDokument7 Seiten4.6.6.5 Lab - Using Wireshark To Examine HTTP and HTTPS Trafficc583706Noch keine Bewertungen
- CT Article Two Cable Modem Registration ProcessDokument5 SeitenCT Article Two Cable Modem Registration Processnoisi80Noch keine Bewertungen
- 15 DHCP Protocol Principles PDFDokument17 Seiten15 DHCP Protocol Principles PDFMuhammadSarmadMahmoodMalikNoch keine Bewertungen
- Networking: Ipconfig Ping FC CHKDSK Net AccountsDokument27 SeitenNetworking: Ipconfig Ping FC CHKDSK Net Accountsshivsharma330Noch keine Bewertungen
- Lesson 1 Introducing Basic Network ConceptsDokument48 SeitenLesson 1 Introducing Basic Network ConceptsJay Carlo SalcedoNoch keine Bewertungen
- Howto Close Open Port UbuntuDokument2 SeitenHowto Close Open Port Ubuntufibbo2012Noch keine Bewertungen
- 5.2.2.5 Packet Tracer - Configuring Dynamic NAT Instructions IG PDFDokument2 Seiten5.2.2.5 Packet Tracer - Configuring Dynamic NAT Instructions IG PDFblado1Noch keine Bewertungen
- Connect Mikrotik Routerboard 751u To Radiusdesk BasicDokument7 SeitenConnect Mikrotik Routerboard 751u To Radiusdesk BasicOneRobNoch keine Bewertungen
- 10 Things NetshDokument5 Seiten10 Things NetshhpgeraldNoch keine Bewertungen
- Answer:: Networking Interview QuestionsDokument10 SeitenAnswer:: Networking Interview QuestionsramNoch keine Bewertungen
- Network Address Translation (NAT)Dokument49 SeitenNetwork Address Translation (NAT)Kero MaalosaNoch keine Bewertungen
- DDOS Attack ReportDokument5 SeitenDDOS Attack ReportFaiz AhmedNoch keine Bewertungen
- GRAMMARIAN CHECKED-CS Research Project InnocentGirls-1Dokument85 SeitenGRAMMARIAN CHECKED-CS Research Project InnocentGirls-1Zejkeara ImperialNoch keine Bewertungen
- 0417 w11 QP 3Dokument8 Seiten0417 w11 QP 3Safa AslamNoch keine Bewertungen
- TriggersDokument4 SeitenTriggerssanjay.gupta8194Noch keine Bewertungen
- iOS To Windows How To Copy and Paste Text Between Your Iphone and PC PCMagDokument16 SeiteniOS To Windows How To Copy and Paste Text Between Your Iphone and PC PCMagendickhkNoch keine Bewertungen
- NIthin ResumeDokument2 SeitenNIthin ResumeNithinNoch keine Bewertungen
- SmartConnector Quick Reference v1.5Dokument1 SeiteSmartConnector Quick Reference v1.5seifadiazNoch keine Bewertungen
- IQ 16.0 SAP Sybase IQ Error Messages Sybase IncDokument1.138 SeitenIQ 16.0 SAP Sybase IQ Error Messages Sybase Inccesar19800Noch keine Bewertungen
- MadhuDokument5 SeitenMadhusravan1006Noch keine Bewertungen
- IN 951 AdministratorGuide en PDFDokument649 SeitenIN 951 AdministratorGuide en PDFVenkatesh NarisettyNoch keine Bewertungen
- CIS 7500 - Online Barcode Verification SystemDokument2 SeitenCIS 7500 - Online Barcode Verification SystemComplete Inspection Systems, Inc.Noch keine Bewertungen
- Zero To Blogger in 30 Days! - Sarah Arrow - 2014 PDFDokument171 SeitenZero To Blogger in 30 Days! - Sarah Arrow - 2014 PDFKoustubh GuptaNoch keine Bewertungen
- READMEDokument11 SeitenREADMEm0st1tedNoch keine Bewertungen
- Bank of Baroda Ascrom Cell BCC FAQ For Troubleshooting:-: "Syntax Is Not Proper 1 or Else"Dokument9 SeitenBank of Baroda Ascrom Cell BCC FAQ For Troubleshooting:-: "Syntax Is Not Proper 1 or Else"binalamitNoch keine Bewertungen
- Ardrone Simulink Development Kit: RequirementsDokument3 SeitenArdrone Simulink Development Kit: RequirementsAndree Gutierrez SucllaNoch keine Bewertungen
- Jepretan Layar 2020-01-15 Pada 10.41.58 PDFDokument1 SeiteJepretan Layar 2020-01-15 Pada 10.41.58 PDFFahira AnwarNoch keine Bewertungen
- iDRAC8 With Lifecycle Controller Version 2.75.75.75: Release NotesDokument17 SeiteniDRAC8 With Lifecycle Controller Version 2.75.75.75: Release NotesANthonyNoch keine Bewertungen
- Corey ChandlerDokument2 SeitenCorey ChandleryerocNoch keine Bewertungen
- 50 Servlet Interview Questions and Answers - JournalDev PDFDokument49 Seiten50 Servlet Interview Questions and Answers - JournalDev PDFKanahaiya GuptaNoch keine Bewertungen
- Netbackup 5220 and Symantec Storage Shelf Technote - Additional Configuration and Troubleshooting GuideDokument59 SeitenNetbackup 5220 and Symantec Storage Shelf Technote - Additional Configuration and Troubleshooting GuideRichard ReaNoch keine Bewertungen
- Excel Practice 3 - Practice With Functions and Conditional FormattingDokument2 SeitenExcel Practice 3 - Practice With Functions and Conditional FormattingJair LPZNoch keine Bewertungen
- SuiteScript Developer and Reference Guide 15.2 PDFDokument1.275 SeitenSuiteScript Developer and Reference Guide 15.2 PDFShashi Bhushan Kumar0% (1)
- Setup TDA Step by Step GuideDokument14 SeitenSetup TDA Step by Step GuideMuhammad AyoubNoch keine Bewertungen
- Websphere V5.0Dokument562 SeitenWebsphere V5.0Robert Pérez MartinezNoch keine Bewertungen
- DELMIA-Human Task AnalysisDokument83 SeitenDELMIA-Human Task AnalysisRushikesh Harkal50% (2)
- Boolean StringsDokument14 SeitenBoolean StringsAbiram RNoch keine Bewertungen
- Universe Cicp2100Dokument2 SeitenUniverse Cicp2100lidosmarkers0aNoch keine Bewertungen
- Getting Started With OneDrive PDFDokument9 SeitenGetting Started With OneDrive PDFKwon Min RaNoch keine Bewertungen
- GlassmorphismDokument7 SeitenGlassmorphismEscorcia Montaño IsaacNoch keine Bewertungen
- Vision PlusDokument12 SeitenVision PlusShashank Shukla67% (6)
- PKM Method and StyleDokument22 SeitenPKM Method and StyleAlessio Sperlinga100% (4)